With cloud-hosted applications becoming a mainstay in today’s world of IT, staying compliant with industry standards and benchmarks like SOC 2 is becoming a necessity for SaaS firms. Therefore, getting SOC 2 compliance isn’t a question of ‘why’ as much as it is a ‘when’. With that in mind, here’s a handy SOC 2 compliance checklist to help you plan and kickstart your compliance journey.
But before we get into the SOC 2 checklist, let’s understand the various nuances of the SOC 2 framework that will help you prepare better.
Getting audit-ready involves months of preparation, planning, and ticking things off on a rather lengthy checklist. Defining a scope, choosing the right trust service criteria, implementing internal risk, and assessing controls – these are just a few of your obligations before the reward – is certification. Let’s understand what each step under SOC 2 compliance checklist entails and also an easy shortcut at the end.
| TL;DR The SOC 2 compliance process involves defining objectives, choosing the report type, conducting internal risk assessments, performing gap analysis, contacting an auditor, and more. Automating SOC 2 compliance processes, from policy creation to evidence collection, saves time and resources. Using automation tools for SOC 2 compliance will save you time and reduce costs associated with manual processes and potential non-compliance issues. |
What is the SOC 2 compliance checklist?
The SOC 2 compliance checklist acts as a guide that helps organizations assess how customer data is collected, processed, stored, and accessed, thereby ensuring compliance with the Service Organization Control 2 (SOC 2) framework.
The SOC 2 checklist also reviews vulnerability management and risk mitigation. The checklist enables organizations to meet SOC 2 requirements, demonstrating effective controls over customer information security, availability, processing integrity, confidentiality, and privacy.
Why should you implement a SOC 2 checklist?
Implementing a SOC 2 checklist provides comprehensive coverage and simplifies the audit readiness process. It showcases your commitment to security, reassuring customers that their data is safeguarded. The SOC 2 audit prompts organizations to formalize and document policies, procedures, and controls.
Documenting these essential practices significantly diminishes business risks, enhances vendor management, and frequently streamlines operational efficiency.
SOC 2 requirements checklist
A well-designed SOC 2 requirements checklist will lay out actionable steps organizations can take to meet the extensive criteria of the framework across security, availability, processing integrity, confidentiality, and privacy. Based on our experience of helping hundreds of businesses become SOC 2 compliant.
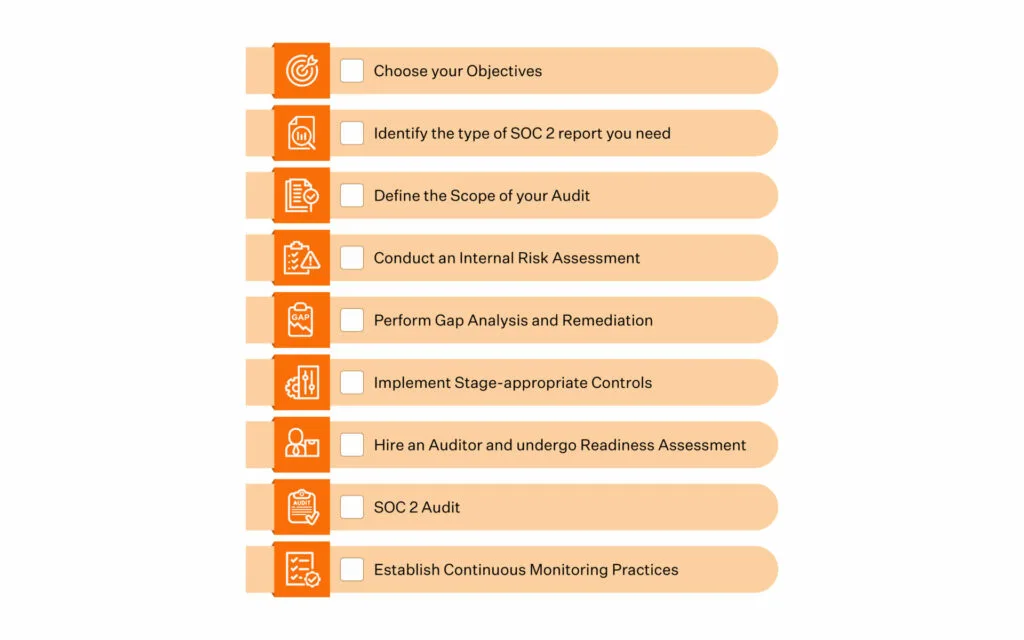
Here’s a 9-step SOC 2 checklist:
1. Choose your objectives
2. Identify the type of SOC 2 report you need
3. Define your SOC 2 scope
4. Conduct an internal risk assessment
5. Perform gap analysis and remediation
6. Implement relevant controls and test them
7. Undergo readiness assessment
8. Conduct the SOC 2 audit
1. Choose your objectives
The first action item of the SOC compliance checklist is to determine the purpose of the SOC 2 report. The specific answers to why SOC 2 compliance is important to you would serve as the end goals and objectives to be achieved in your compliance journey.
With a clear understanding of your objectives, you can ensure the SOC 2 process addresses your particular reasons for pursuing compliance. This clarity will help drive decision-making as you work through defining the scope, assembling a cross-functional team, evaluating controls, undergoing auditing, and taking necessary actions to remediate gaps.
Download your SOC 2 Compliance Checklist
Here are some examples:
- Your customers have asked for it
- You are entering a new geography, and SOC 2 compliance will add to your strength
- You want to bolster your organization’s security posture to avoid data breaches and the financial and reputation damage that comes with it
That said, not wanting SOC 2 compliance because customers aren’t asking for it or because none of your competitors has it isn’t advisable. It’s never too early to get compliant. And it’s always an advantage to be proactive about your information security.
Also read: How to make compliance your superpower
2. Identify the type of SOC 2 report you need
SOC 2 reports can be Type 1 or Type 2. You decide which one is appropriate based on your compliance goals.
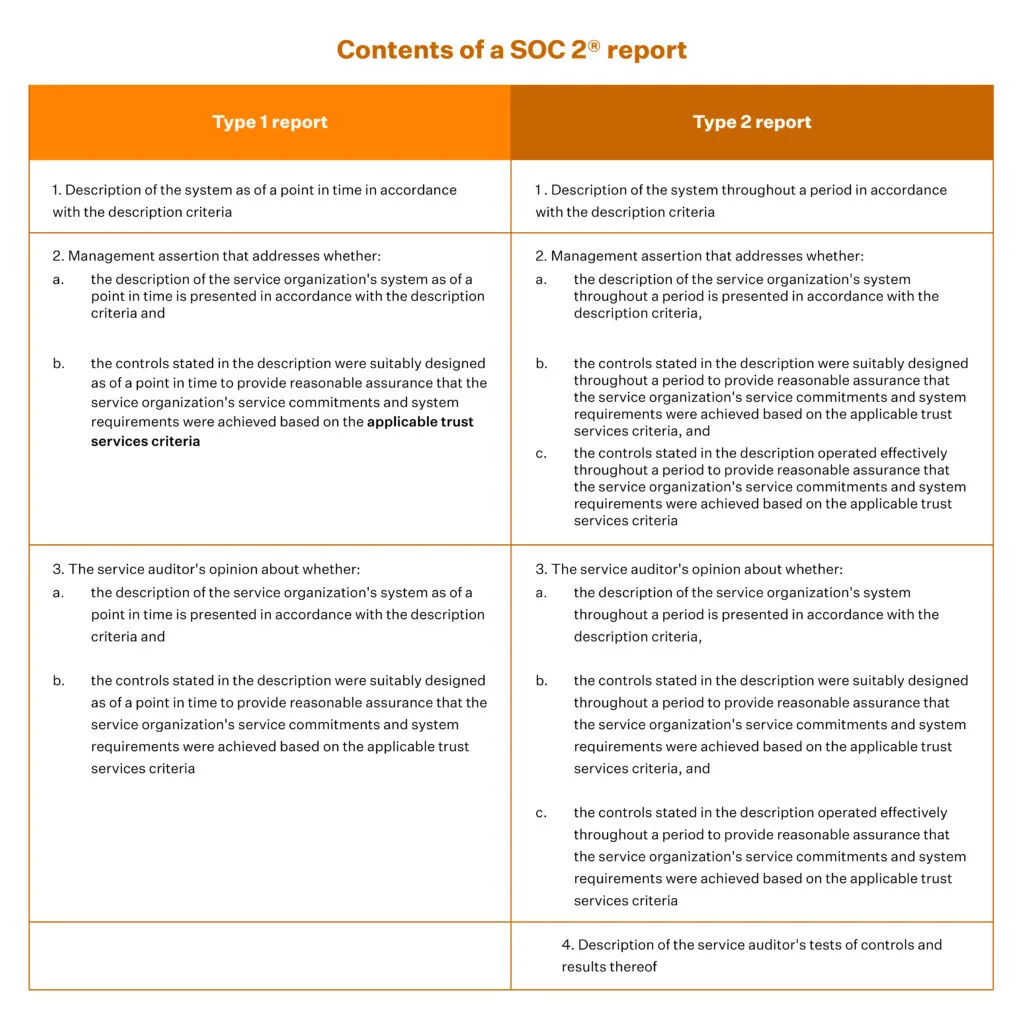
A Type 1 report is faster, but only reflects the performance of controls at a point in time and affirms that your internal controls are in place.
Type 2 confirms that the controls are working as expected when tracked over a period of time, and it is likely that you will be asked to produce a Type 2 audit report shortly after. It is comprehensive and demands a control monitoring period that can be as long as 6 months, but it produces a more vivid picture of the performance of your security controls.

Kickstart with our automated,
ready-to launch toolkit.
3. Define scope
Defining the scope of your audit is crucial as it will demonstrate to the auditor that you have a good understanding of your data security requirements as per SOC 2 compliance checklist. It will also help streamline the process by eliminating the criteria that don’t apply to you.
You must define the scope of your audit by selecting the TSC that applies to your business based on the type of data you store or transmit. Note that Security as a TSC is a must. Regulatory requirements will also have a bearing on your criteria selection. That said, in our experience, most SaaS businesses typically only need Security, Availability and Confidentiality (or their combination) as TSC in their SOC 2 journey.
Here are some examples:
- Choose Availability if your customers have concerns about downtime.
- Choose Confidentiality if you store sensitive information protected by non-disclosure agreements (NDAs) or if your customers have specific requirements about confidentiality.
- If you execute critical customer operations, such as financial processing, payroll services, and tax processing, you should include processing integrity.
- Include Privacy if your customers store PII (Personally Identifiable Information) such as healthcare data, birthdays, and social security numbers.
On that note, a bad example here would be leaving a relevant TSC out of your SOC 2 scope. Such oversight could significantly add to your cybersecurity risk and potentially snowball into substantial business risk.
A SOC 2 audit looks at your infrastructure, data, people, risk management policies, and software, to name a few items. So, at this stage, you must also determine who and what within categories will be subject to the audit. For instance, you can keep some of your non-production assets from the scope of the audit.
4. Conduct an internal risk assessment
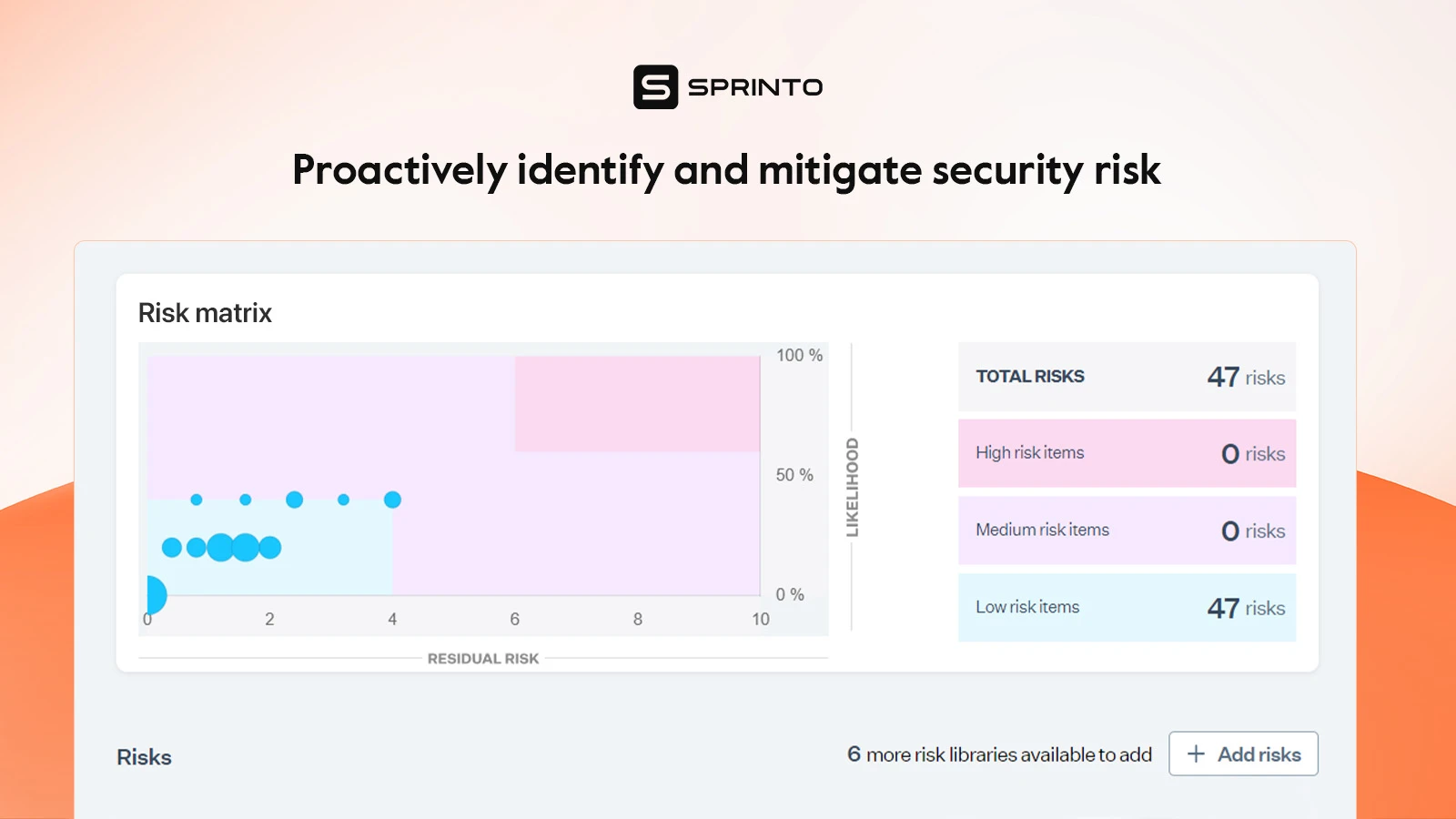
Risk assessment is crucial in your SOC 2 compliance journey. You must identify any risks and document the scope of those risks from identified threats and vulnerabilities.
Assign a likelihood and impact to each identified risk and then deploy measures (controls) to mitigate them as per the SOC 2 checklist.
Once you have identified the risks, score them based on its impact and likelihood of that risk scenario actually playing out. A common mistake organizations make in this stage is scoring risks based on guts rather than reality. A better, auditor approved way of scoring risks is by using industry grade benchmarks.
A compliance automation platform like Sprinto builds a true, up-to-date inventory of assets and gives you the tools and capabilities to define risks at an asset level. Using its comprehensive risk register, you can identify, risks associated with your assets.
Get SOC 2 compliant on a budget
5. Perform gap analysis and remediation
You must examine your current control status and security practices and compare their compliance posture with how they measure against SOC requirements.
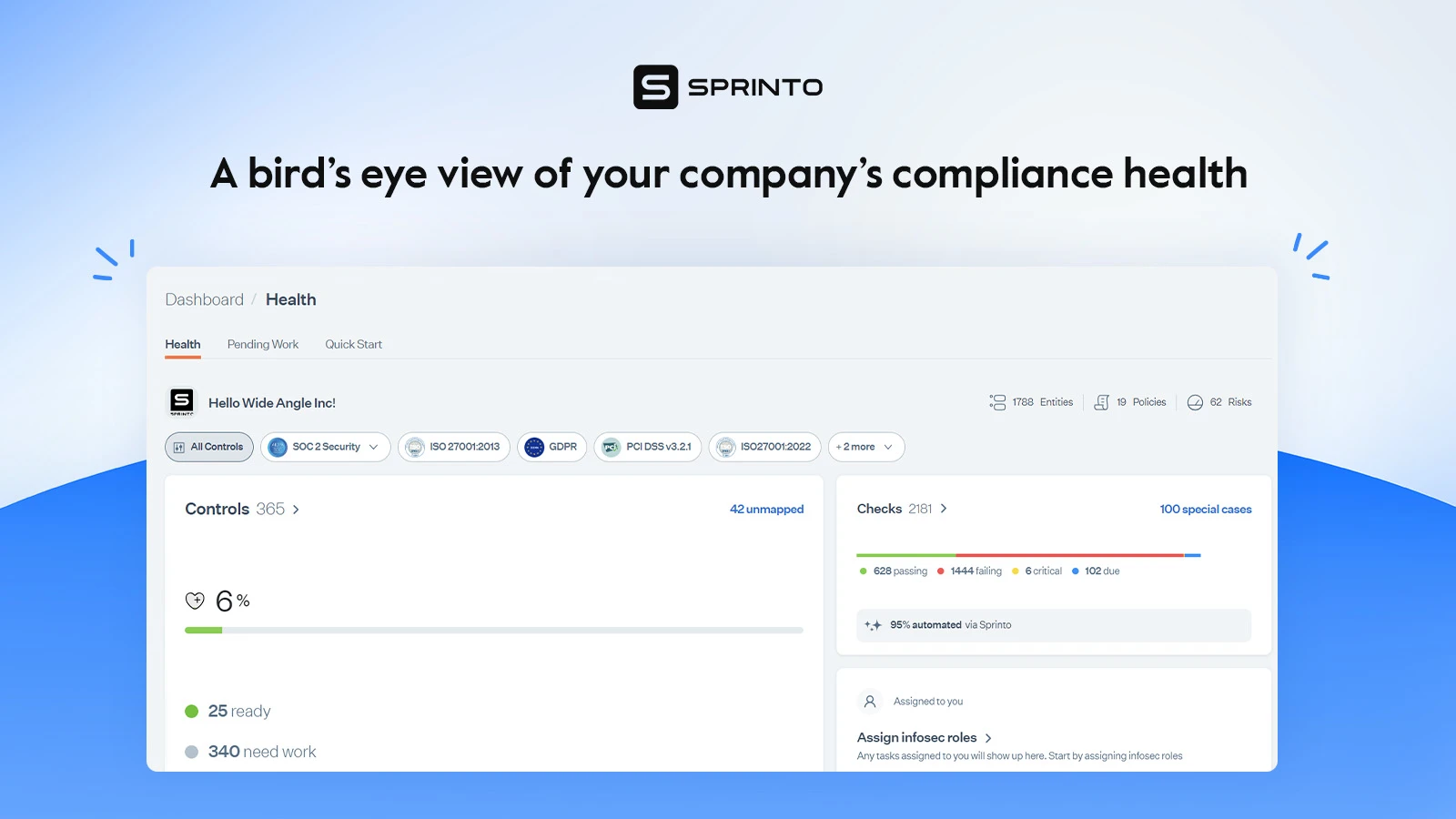
A compliance automation tool like Sprinto can make this process a lot easier by integrating with your applications and scanning the environment for control gaps and vulnerabilities. From a single dashboard, you can view the health of all controls, risks, and issues that require your attention. The auditor-friendly dashboard also allows you to automatically collect compliance evidence.
6. Implement relevant controls and test them
Following gap assessment, implement controls to meet compliance and keep asset security in check. These may include modifying security workflows, introducing employee training modules, and creating new process documentation, among others. The risk ratings (carried out earlier) will help you prioritize controls.
Once you have implemented the control, test them for its effectiveness. This is a critical part of SOC 2 Type 2 because here the auditor tests if the controls are working as they should.
Common issues you may face at this stage is not remediating or not getting alerted on failing controls on time and overlooking non-compliance issues which puts you at the risk of not meeting auditor expectations.
You can resolve these using a tool like Sprinto that automatically maps risks to compliance criteria and controls, launches automated checks to test controls, and monitors their health on a central dashboard.
When anomalies are detected, trigger alerts and remediation workflows to the appropriate risk owners. Context-rich, time-bound alerts ensure timely resolution throughout the risk lifecycle, preventing issues from escalating. Get a demo now to see Sprinto’s live control dashboard.
7. Undergo readiness assessment
Undertake a readiness assessment to see if you meet the minimum SOC compliance requirements to undergo a full audit.
Here are your focus areas for the assessment:
- Gap analysis – It aims to detect vulnerabilities and gaps and generate a list of specific recommendations and actions. It takes around 2-4 weeks from start to finish.
- Controls matrix – It lists the objectives map, internal controls identification, and control characteristics.
- Auditor documentation – It involves drafting the request list for auditors and testing procedures.
Based on the auditor’s findings, remediate the gaps by remapping some controls or implementing new ones. Even though technically, no business can ‘fail’ a SOC 2 audit, you must correct discrepancies to ensure you receive a good report.
Readiness assessment involves writing policies, linking checks to the right control, evaluating risks without leaving any gaps, and collecting evidence accurately. Doing these manually leaves a lot of room for error and derail the audit process.
Sprinto helps you add momentum to compliance activities by offering pre-built templates, pre-mapped controls, automated evidence collecting system, and dedicated auditor dashboard. Get SOC 2 compliant with ease. Talk to our experts today!
“We only need to spend 5-10 minutes a week on compliance now,” notes Rodney Olsen, VP of Engineering at Ripl.
Check out How Ripl achieved SOC 2 compliance while spending 1/3 of the expected effort with Sprinto.
8. SOC 2 audit
Authorize an independent certified auditor to complete your SOC 2 audit checklist and generate a report. While SOC 2 compliance costs can be a significant factor, choose an auditor with established credentials and experience auditing businesses like yours. In your Type 2 audit, you may expect a long-drawn exchange of information with the auditor as you answer their questions, provide evidence, review your internal samples, and discover non-conformities.
Typically, SOC 2 Type 2 audits may take between two weeks to six months, depending on the volume of corrections or questions the auditor raises. Type 2 has a mandatory monitoring period of three-six months. A Type 2 report, therefore, offers more significant insights into your organization’s controls and its effectiveness.
Here are some questions the auditor may ask:
- Can you share evidence to show that all your employees undergo background verification?
- Can you show proof of how you ensure that the changes in your code repositories are peer-reviewed before it is merged?
- Can you demonstrate with evidence that you remove access to emails and databases once an employee resigns from your organization?
- Can you show proof that you run background checks on all your employees?
- Can you share proof of how you maintain the endpoint security of all systems?
The audit for Type 1, in comparison, doesn’t require a monitoring period, is less intrusive, and requires you to give a snapshot (with evidence) of the various checks and systems (read as controls) you have put in place to meet the SOC compliance checklist requirements. Note that after you clear your SOC 2 Type 1 audit, you will need to go through an observation period of three-six months before you can apply for Type 2.
Get Our Practical SOC 2 Guide;
Yours at No Cost

9. Establish continuous monitoring practices
Getting your SOC 2 compliance report isn’t just a one-time event. The report is just a start as security and compliance are on-going efforts . It pays to establish a robust continuous compliance monitoring practice as SOC 2 audits must happen annually.
Continuous compliance makes future audits and scaling scope of compliance easy. when you operate with the assurance of compliant practices, you can add more frameworks without disrupting the practice or the org at large.
Your monitoring practices should be scalable to grow with your organization, simplify evidence collection, not hamper employee productivity, alert you of non-compliant activities, and paint an accurate picture of entity-level granular overview of your infosec health at any point in time.
Monitoring IT infrastructures manually, without the right tools creates gaps, eats up bandwidth, and results in last-minute surprises. Avoid these pitfalls and ensure audit success by continuously, automatically, and comprehensively monitoring your assets and controls for compliance with GRC automation tools like Sprinto. See Sprinto in action
Aligning Your Checklist with SOC 2 Trust Service Criteria
When going through a SOC 2 audit, your organization will be evaluated based on five Trust Service Criteria (TSC) defined by the AICPA. To properly prepare, you should review your internal controls and procedures to ensure they address each of these criteria.
Here are some tips for aligning your SOC 2 readiness checklist with the TSC:
1. Security
It must be in scope for every SOC 2 audit and is, therefore, referred to as the common criteria. It requires you to enable access control, network firewalls, and other operational/governance controls to protect your data and applications. Enable entity-level controls that establish baseline security policies.
2. Availability
Requires you to demonstrate that your systems meet operational uptime and performance standards. So, implement monitoring for system uptime and performance. Have disaster recovery and incident response processes ready as well.
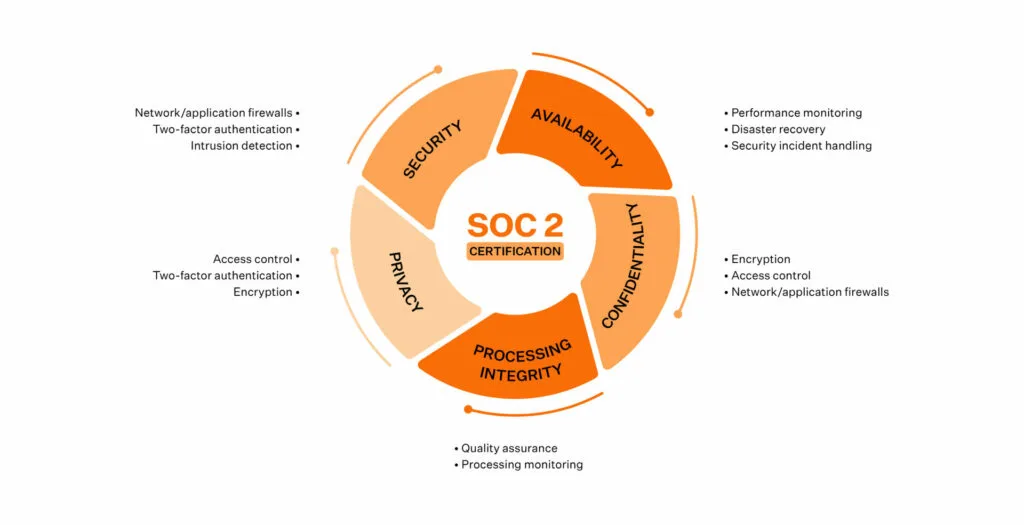
3. Confidentiality
Shows how you safeguard sensitive data throughout its lifecycle. Implement access controls so only authorized users can access data.
4. Processing Integrity
Have quality assurance checks to validate the accuracy and reliability of data processing. Monitor systems to ensure timely processing and intended outcomes. It includes quality assurance procedures and SOC tools to monitor data processing.
5. Privacy
Requires you to protect Personally Identifiable Information (PII) from breaches and unauthorized access through rigorous access controls, two-factor authentication, and encryption.
Challenges of implementing SOC 2 compliance
Achieving SOC 2 compliance is a major undertaking that comes with some substantial challenges. One hurdle is the time-intensive process of thoroughly documenting all controls, policies, and procedures to SOC 2 standards. You can expect this to take quite some time and effort. There will also likely be costs associated with making required updates to infrastructure or systems to meet compliance criteria.
Even after achieving compliance, the work doesn’t stop. Maintaining SOC 2 requires rigorous ongoing internal control audits. With strict standards to meet, the process of becoming compliant is far from easy. However, for organizations handling critical customer data, the effort is worthwhile to gain trust and demonstrate security commitments.
The Sprinto Advantage: With the help of the SOC 2 automation platform, you can streamline the whole process to eliminate manual repetitive tasks. Talk with Sprinto’s experts to know more about SOC 2 automation and beyond.
Also check the comparison between ISO 27001 and SOC 2, if you are also considering ISO.
Tips to help you prepare for a SOC 2 audit
Despite SOC 2’s many challenges, organizations achieve compliance in less than three to six months. The more innovative way forward is to use tools that help you navigate its security controls while keeping an eye on them constantly.
Here are four tips to keep in mind before a SOC 2 audit:
1. Automate evidence collection without fail: Evidence are one of the most important parts of audits, so automate wherever possible to remain audit-ready at all times.
2. Review your internal controls regularly: All security controls as per your SOC 2 scope must be reviewed periodically with internal stakeholders assigned with clear ownership.
3. Conduct multiple readiness assessments: It is better to find gaps internally before the audit than after getting the CPA firm involved.
4. Use a compliance automation tool: These tools drastically reduce audit timelines and help you avoid compliance fatigue. Before the actual audit, you’ll be able to use the tool to map controls, generate audit trails, and create documentation while it integrates with your existing tool stack.
Automate your SOC 2 compliance with Sprinto
The SOC 2 certification process involves extensive documentation, evidence gathering, testing, and control implementation. Manually, it can take hundreds of hours and remain error-prone. Automating the SOC 2 compliance checks removes the manual effort involved in infosec compliance by automating repeatable tasks.
With Sprinto, the entire process—from checklists to policy creation and implementation—is error-free and automated and can be tracked on a single dashboard. Smart workflows accelerate compliance, allowing you to obtain an SOC 2 certification in weeks. You can automate your SOC 2 check with Sprinto in the 3 easy steps listed below.
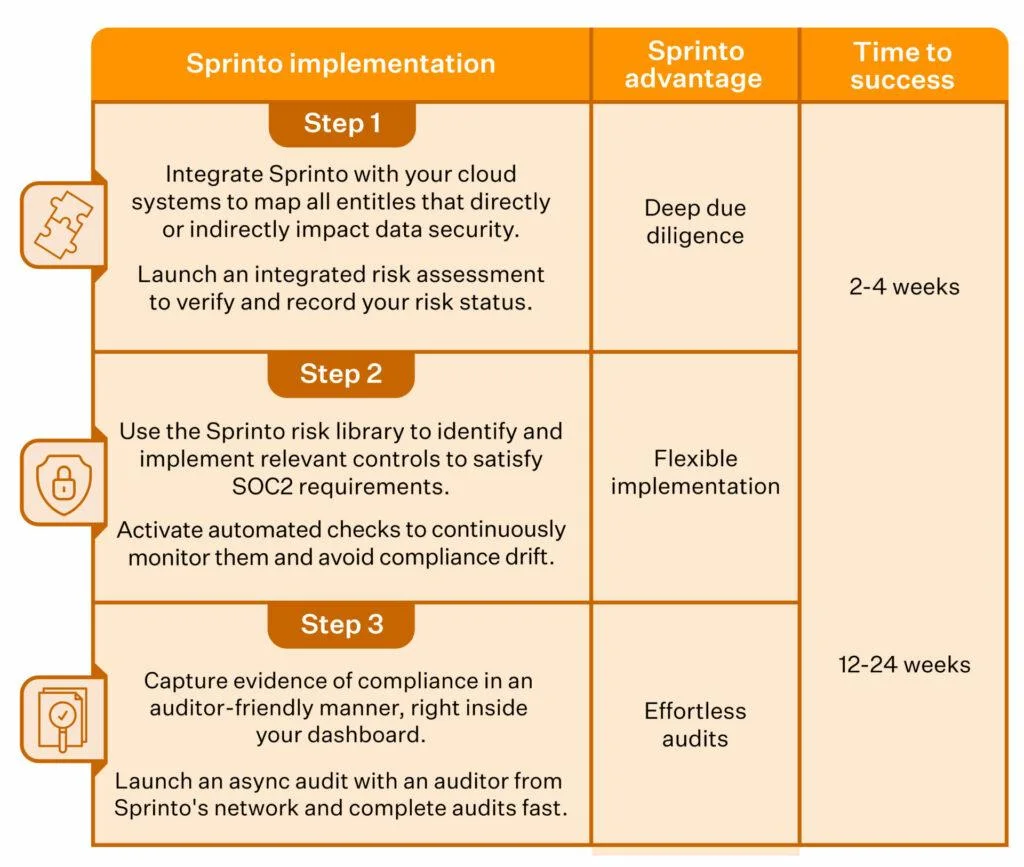
Read more: SOC 2 Automation: What Is It, and Why Do You Need It.
What’s more, you can now catalog all your evidence that demonstrates your SOC 2 compliance and present it to the auditors seamlessly, saving you a ton of time and resources.
Case in point: PreSkale completed its SOC 2 audit under 30 days while working with Sprinto.

Sprinto’s compliance platform also eliminates many additional costs. With Sprinto, you only pay the auditor and the pen testing vendor (not including company-specific incidentals).The result? You save hundreds of hours, fix issues quickly with continuous monitoring, and obtain a hassle-free SOC 2 report. Book a free demo here to see how Sprinto can help you successfully start and sail through your SOC 2 journey.
FAQs
SOC 2 is a voluntary information security compliance standard developed by the American Institute of CPAs (AICPA) for cloud-hosted organizations. The compliance framework is based on the Trust Services Criteria of security, availability, processing integrity, confidentiality, and privacy.
Tech companies that capture and/or handle sensitive customer information can consider getting SOC 2 compliant. This is because SOC 2 compliance demonstrates that you have a robust security posture and practice in place to keep data safe and secure. It helps to demonstrate that your organization provides customers and prospects a secure, available, confidential, and private solution.
The five basic trust principles or service criteria are security, processing integrity, availability, privacy, and confidentiality. Only security is compulsory for all organizations undergoing a SOC 2 audit, while the rest can be selected based on the type of data.
No, SOC 2 is not a mandatory framework. However, due to growing concerns over data privacy and security, organizations require their vendors to demonstrate if they handle data securely and ask for proof in the form a SOC 2 audit report
Like a compliance standard, SOC 2 compliance has its own nuances and complexities. It ultimately depends on how you approach it – manual approach can be error-prone, time-consuming, and half-baked. Using an automation tool, you can reach the audit finish line in weeks rather than months.
No, the AICPA did not release an official checklist for organizations to become SOC 2 compliant. This gives different auditing firms the flexibility to use a process they see fit. Compliance automation tools like Sprinto combine compliance workflows in one solution to offer an effective way of becoming compliant.
Anwita
Anwita is a cybersecurity enthusiast and veteran blogger all rolled into one. Her love for everything cybersecurity started her journey into the world compliance. With multiple certifications on cybersecurity under her belt, she aims to simplify complex security related topics for all audiences. She loves to read nonfiction, listen to progressive rock, and watches sitcoms on the weekends.
Explore more SOC 2 articles
SOC 2 Compliance Overview
SOC 2 Preparation and Documentation
SOC 2 Audit and
Reporting
SOC 2 Differences and Similarities
SOC 2 Updates & Management
SOC 2 Industry-Specific Applications
research & insights curated to help you earn a seat at the table.










