
Your organization’s data is perhaps your most valuable asset. Protecting its security, confidentiality, and integrity is key to keeping your organization safe. This need to preserve information gets even more pronounced when you work with the Department of Defense (DoD), the United States of America, which values Cybersecurity Maturity Model Certification (CMMC) Compliance.
The CMMC ensures adherence to DoD cybersecurity standards and helps DoD contractors implement necessary cybersecurity practices.
Your compliance with the CMMC program is key to demonstrating your ability to handle DoD data securely.
If you are a service provider for the DoD or a sub-contractor to one of the DoD’s prime contractors or are going to enter the Defense Industrial Base (DIB) sector, then CMMC certification will be a prerequisite. Here’s a lowdown on the CMMC compliance program, its asks, and the way to go about it.
- CMMC compliance has three levels: level 1 focuses on basic hygiene, level 2 on intermediate to advanced cyber practices, and level 3 on comprehensive security practices and controls.
- To get CMMC certified, understand your level, appoint an officer, track CUI, develope a plan, mitigate risk, and continuously monitor.
- CMMC 2.0 reduces from 5 levels to 3, aligns better with NIST, allows annual self-assessment for Level 1 and some Level 2, and reduces complexity and costs while maintaining robust cybersecurity requirements.
What is CMMC?
The Cybersecurity Maturity Model Certification, CMMC for short, is a unified cybersecurity framework developed by the Department of Defense, USA, to protect the Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) at every step across the DoD’s supply chain.

The CMMC program standardizes the asks for cybersecurity practices and helps the DoD determine the extent of cyber protection practices organizations have incorporated. CMMC compliance, therefore, provides the DoD assurance that its contractors and sub-contractors meet its cybersecurity requirements and have the wherewithal to protect sensitive DoD data.
It also helps organizations that constitute the DIB assess their current security posture, identify security gaps, optimize their processes, and maintain cyber hygiene per DoD’s requirements.
What is CMMC Compliance?
The CMMC compliance outlines essential cybersecurity practices that organizations must follow to safeguard sensitive information for the DoD.
Why is CMMC compliance important?
CMMC compliance is important because it helps contractors implement strong cybersecurity practices, reducing the risk of cyberattacks and data breaches.
Its primary goal is to protect sensitive government information, including FCI and CUI, while also strengthening the security of the defense supply chain.
Get CMMC compliant with ease
Who needs to comply with CMMC?
CMMC certification is for organizations that handle/work with DoD information. The compliance level will depend on the type of information the organizations are privy to. For instance, if the organization operates with non-classified DoD information, it may only need a Level 3 clearance or below. A Level 4 clearance or higher is needed if it handles high-value information. An interesting aside here – these classifications are project-based.
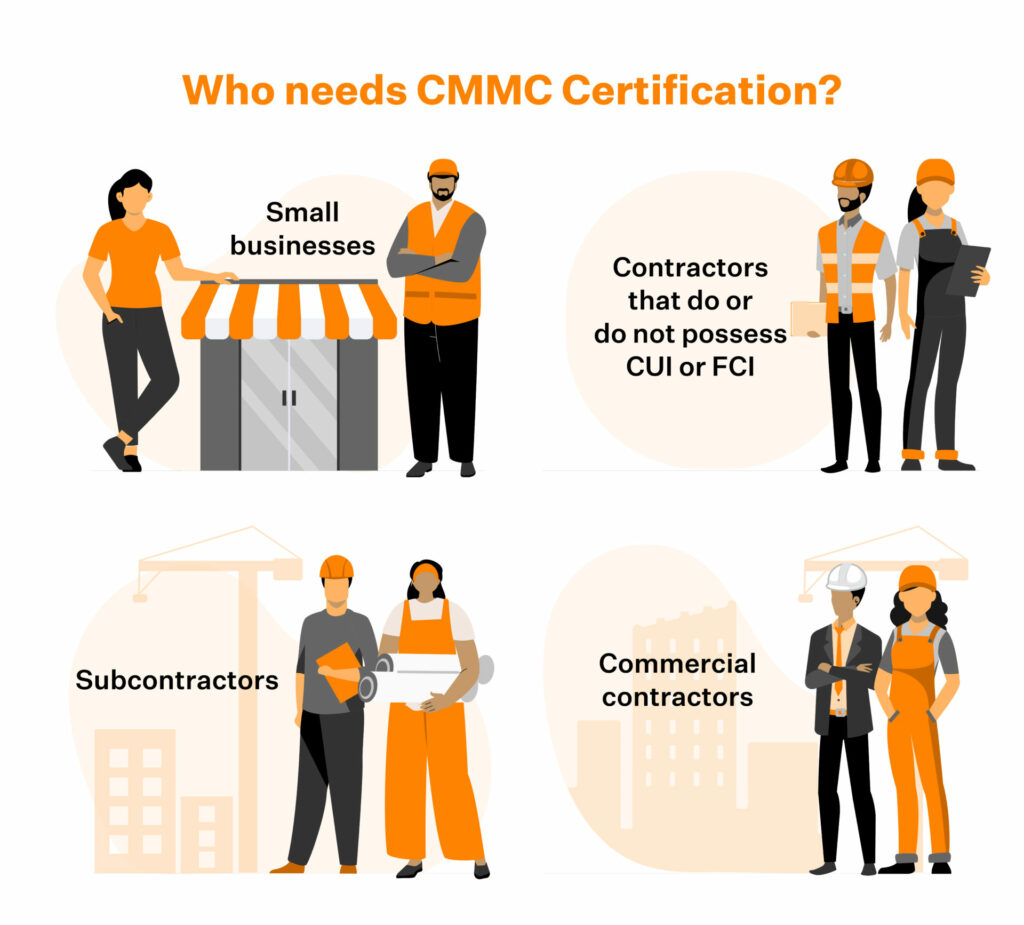
All defense contractors will be required to have a CMMC certification. This includes:
• Small businesses
• Contractors that do or do not possess CUI or FCI
• Subcontractors
• Commercial contractors
Note that CMMC applies only to DoD contracts, and not all US government contractors.
To become CMMC certified, companies must implement and pass an external CMMC assessment carried out by authorized and accredited CMMC Third-Party Assessment Organizations (C3PAOs). C3PAOs must be accredited by the Cyber AB (formerly CMMC Accreditation Body). Check their marketplace for a list of accredited C3PAOs.
During the assessment, organizations must produce documented evidence for the required processes and practices, and demonstrate the necessary capabilities.
Successful assessments result in the issuance of CMMC certificates to the DIB organization at an appropriate maturity level. Wondering what the levels of maturity are? We’ve covered that in the later section.
CMMC compliance requirements will appear in all contracts starting in the fiscal year 2026. This means DoD contractors will need to comply in order to bid on such work.
You may also like to read: PCI DSS certification
Domains, Practices, and Maturity Levels
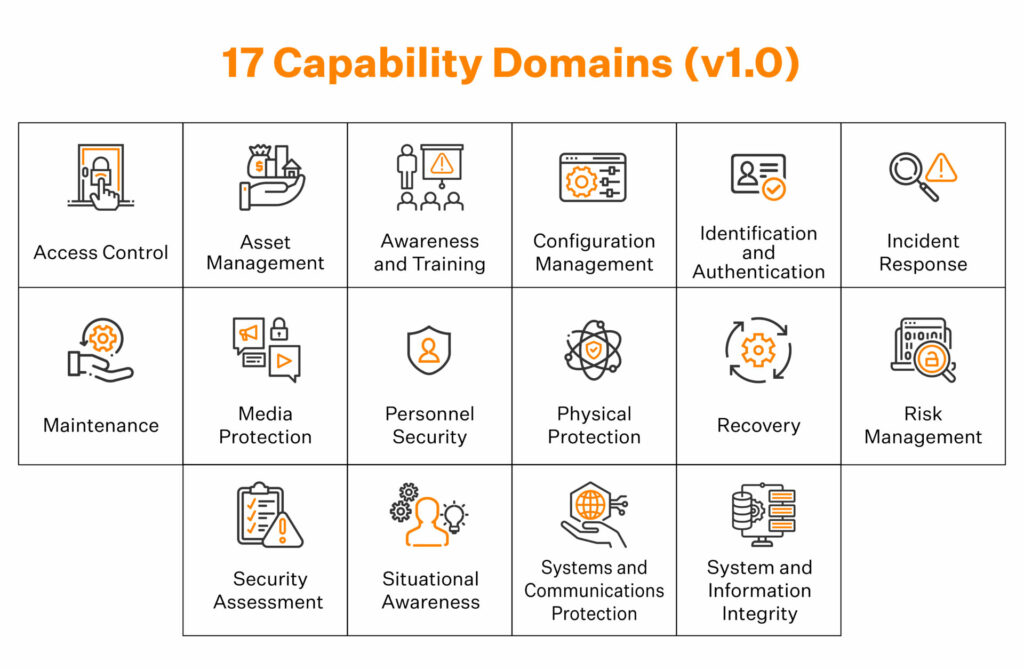
The CMMC model framework organizes processes and cybersecurity best practices into 17 domains. Each domain consists of processes that span five levels of cybersecurity maturity. Additionally, each domain contains one or more capabilities spanning the five levels. And, for any given capability, organizations must demonstrate one or more practices (171 in total).
Capability Domains
Each domain comprises processes and capabilities across the five levels of CMMC. The domains include:
Processes, Practices & Maturity Levels
Processes and practices in CMMC depend on the organization’s maturity levels in terms of the type of DoD information it handles.
Here’s a quick overview of the CMMC maturity level, processes, practices and focus.
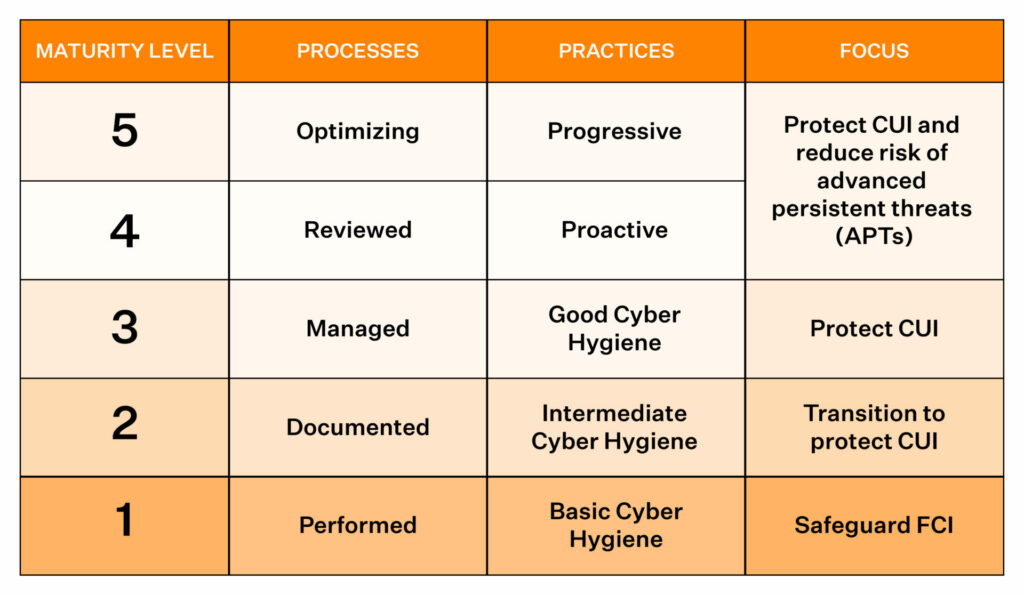
These aren’t mere checkboxes but should be seen as processes or activities ingrained in an organization’s operations. The following section details the CMMC maturity levels.
CMMC compliance levels
The framework has five different CMMC compliance levels against which DoD contractors and subcontractors are assessed to determine the extent and maturity of their information systems’ cybersecurity processes and practices.
Note: Please note that the CMMC has updated its structure, reducing the previous five levels to three. This change was announced in November 2023 as part of CMMC 2.0, which aimed at streamlining the certification process. The new levels are Level 1 (Foundational), Level 2 (Advanced), and Level 3 (Expert).
This breakdown makes it easier for organizations to achieve the minimum cybersecurity standards required per their risk profile (based on the type of sensitive information handled).
Here are the 5 CMMC certification levels:
Level 1: Basic Cyber Hygiene
Level 1 defines the minimum level of cyber hygiene required to protect FCI. It includes 17 practices derived from NIST standards, and requires a performance-only approach to cybersecurity. It is the easiest of the five levels to achieve, and there isn’t any CMMC requirement to document security processes at this level.
Practices, typically, can be defined as the specific technical activities that must be performed to showcase a specific level of cybersecurity maturity.
Level 2: Intermediate Cyber Hygiene
Level 2 is slightly more challenging than Level 1. It is, in essence, a mid-way transition point to managing CUI. It requires a total of 72 practices (55 additional along with the 17 from Level 1) to be demonstrated. Level 2 requires organizations to perform and document the processes, procedures, and cybersecurity policies.
Level 3: Good Cyber Hygiene
This level requires adherence to 130 practices to showcase the protection of CUI. This is the minimum level needed to use, share, or handle CUI. Level 3 requires organizations to demonstrate that their cybersecurity processes are managed and documented.
Level 4: Proactive Cyber Hygiene
Level 4 comprises 156 practices and indicates a reasonably advanced cybersecurity system. To achieve level 4 certifications, organizations must review and document activities as well as loop management into the entire process. The focus at Level 4 also shifts towards proactively defending against Advanced Persistent Threats (APTs) as against only protecting CUI in Level 3.
Level 5: Advanced & Progressive Cyber Hygiene
Level 5 includes 171 practices and is the highest level of CMMC compliance. Organizations with Level 5 certifications have an advanced and progressive cybersecurity system in place to protect CUI from APTs. A CMMC level 5 certification indicates that organizations can assess APTs and that their cybersecurity defenses are optimized and reviewed to thwart them.
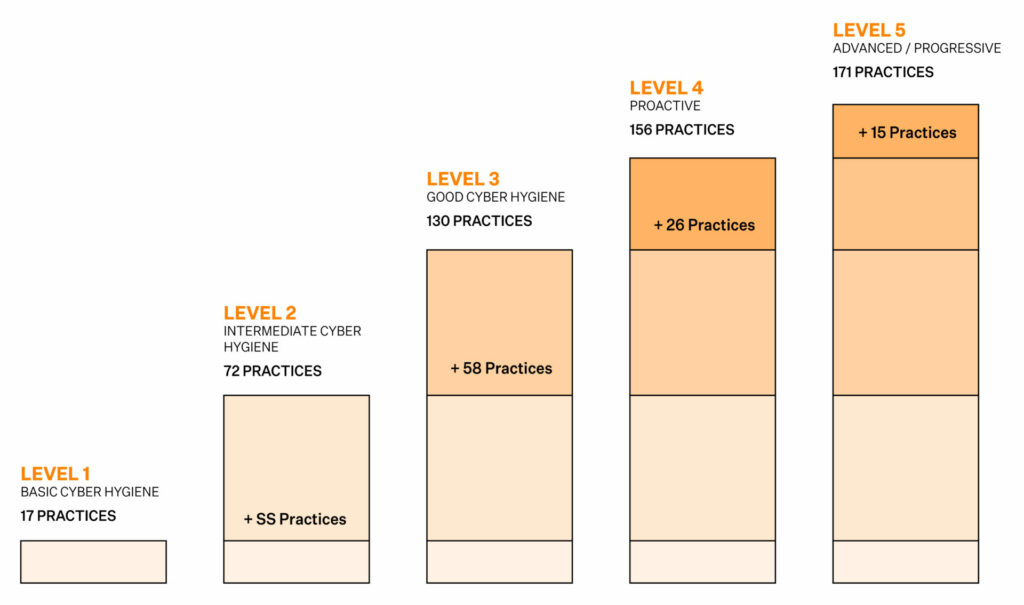
Note that these practices are not new, but rather are derived from Federal Acquisition Regulation (FAR) 48 CFR 52.204-21 and NIST SP 800-171 r1 and Draft NIST SP 800-171B. Besides, each level builds off the levels before. So, a Level 5 CMMC organization will also comply with all lower levels.
CMMC Compliance requirements
To comply with the CMMC framework, you have to implement a number of security practices based on your level. Level 1 includes 17 practices under six domains. To comply with level 2, you have to implement 110 practices grouped under 14 domains.
All domains are listed below:
- Access Control (AC)
- Incident Response (IR)
- Risk Management (RM)
- Access Management (AM)
- Maintenance (MA)
- Security Assessment (CA)
- Awareness and Training (AT)
- Media Protection (MP)
- Audit and Accountability (AU)
- Personnel Security (PS)
- System and Communications (SC)
- Configuration Management (CM)
- Physical Protection (PE)
- System and Information Integrity (SI)
- Identification and Authentication (IA)
- Recovery (RE)
- Situation Awareness (SA)
All DoD suppliers will have to be certified to the appropriate CMMC level in order to continue doing business with DoD under the mandated CMMC requirements. NSF-ISR was named one of the first C3PAO candidates to participate in the CMMC program.
Giles suggests that organizations start the CMMC process with a basic question: Does my organization have controlled unclassified information? This is information created or owned by the government that needs to be safeguarded and released only under proper, legal and regulated controls, such as parts for a new defense aircraft or specifications for military uniforms.
How do I get CMMC compliant?
Getting CMMC compliant starts with determining your requirement level, appointing a compliance manager, and ending with continuous compliance monitoring. The end-to-end process requires time, effort, expertise, and dedication.
We spoke to our in-house auditors to summarize the CMMC compliance checklist to help you get started.
Step 1: Determine your requirement level
The controls applicable to your business depend on your organization’s maturity level. Each level builds on the previous one, so knowing the right one is critical.
Step 2: Appoint a compliance manager
Select someone to oversee the CCMC compliance activities. This person will be responsible for collaborating with external stakeholders, developing the right policies to meet the organization’s objectives, ensuring that all activities align with the CMMC checklist, and developing a timeline for each activity.
Step 3: Collaborate, communicate, and document
Understand the people, process, and technologies in your infrastructure. Know who is responsible for handling which sensitive system, the systems that are in place to protect them, and coordinate with all functions to develop a unified channel to communicate compliance efforts. Document the roles of contractors and third party stakeholders.
Step 4: Track the CUI flow within your systems
To protect CUI, you should know where and how it flows within your IT environment. Once identified, reduce its storage across endpoints to the fewest devices.
Reducing the CUI footprint means you have fewer endpoints to protect, which in turn helps you achieve compliance faster and reduce the cost. Once reduced, identify all systems and data that process CUI and create an inventory. Develop a network diagram to visualize data flow within and outside your organization’s perimeter.
Step 5: Develop a SSP and PoA&M
An SSP or a system security plan documents the policies, processes, and measures you have adopted. Review and update the roadmap as and when you change a process, implement a new policy, or adopt a new technology. It should include the selected controls and security practices you plan to implement.
Develop a Plan of Actions & Milestones (POA&M), a document to track the progress of your CMMC compliance checklist. It should include gaps found during the audit, corrective actions, and timelines for completing the action items.
Step 6: Conduct an internal assessment
Conduct a self-assessment to evaluate the progress and effectiveness of the implemented controls using the CMMC self-assessment guide. Develop a SAR (security assessment report) to document your findings and include suggested actions for improvement.
Step 7: Submit your documents to the SPRS
The Supplier Performance Risk System (SPRS) is a central repository of all CMMC documents. Submit your SSP, SAR, and POA&M to the SPRS. Also, be sure to share your self-assessment score to help the Department of Defense evaluate your posture and progress.
Step 8: Address and remediate existing risks
Use your self-assessment result to close existing gaps. Use the POA&M as a guide to implement the remaining controls and measures. Once you have remediated the risks, submit the SSP, SAR, and POA&M to the SPRS again. Now you have an updated score.
Step 9: CMMC certification
Connect with a CMMC 3rd Party Assessment Organization (C3PAO) to communicate your status and set a timeline. The C3PAO will evaluate your current progress and create a detailed report of their findings.
Once the report is verified by the CMMC Assessment Process (CAP), it will be uploaded to the CMMC Enterprise Mission Assurance Support Service (EMASS) for further review by the DoD.
Step 10: Continuous monitoring
Your CMMC framework implementation does not end at certification. To maintain your certification, you must regularly update your training materials, review policies, update documents, and ensure that all controls and measures function as intended.
Apart from monitoring, you must conduct internal assessments and update the results to the SPRS to ensure compliance.
How much does implementing CMMC compliance cost?
The cost of implementing CMMC compliance varies by maturity level: Level 1 costs $1,000 annually, Level 2 costs $25,000, and Level 3 costs around $50,000.
Here is a breakdown of CMMC costs.
| Category | Details/Range |
| Gap assessment | $3.5k to $20k |
| Remediation | $35,000 to $115,000 |
| Audit | $20,000 to $40,000 |
| Consulting | $250 to $400 per hour |
| CUI enclave | $300 to $4,000 per month per user |
For more information, take a look at our compliance cost calculator and compliance effort calculator.
What’s changed in CMMC 2.0?
CMMC 2.0 is the most recent iteration (released in November 2021) of the cybersecurity maturity model by the DoD. Instead of the five levels in CMMC 1.0, it has streamlined requirements to three levels of cybersecurity – Foundational, Advanced, and Expert.
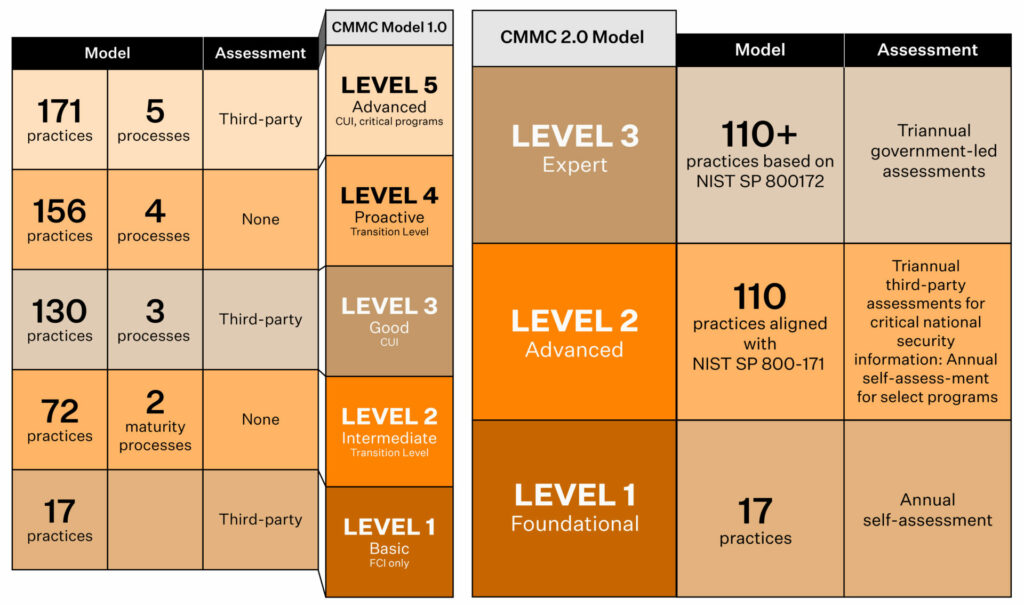
CMMC Level 1 (Foundational)
This level remains applicable to organizations with FCI only, and requires them to incorporate the same 17 basic safeguarding practices. Level 1 organizations don’t process and transmit CUI, and will have to self-certify that they comply with the 17 practices annually. The CMMC self-assessment should be completed using the CMMC Assessment Guide for the appropriate CMMC level.
Falsely certifying under Level 1 could result in fraud claims under the False Claims Act.
CMMC Level 2 (Advanced)
This level is applicable to companies that handle CUI and FCI. It is the same as Level 3 of CMMC 1.0 but with a reduced number of practices. It now includes 110 practices from NIST SP 800-171r2, and will require most organizations to undergo third-party assessments every three years. Some organizations, depending on the type of information, may need to demonstrate compliance through self-assessments.
Also, CMMC 2.0 will allow organizations to receive contract awards with a time-bound Plan of Actions and Milestones (POA&M) in place to complete CMMC requirements.
CMMC Level 3 (Expert)
This level combines the former CMMC 1.0 Levels 4 and 5, and is applicable for organizations that handle the highest priority programs with CUI. Similar to Level 2, organizations at Level 3 will also need to pass an assessment every three years.
The DoD has expressed that it does not intend to approve the inclusion of a CMMC requirement in any contract prior to the completion of the CMMC 2.0 rulemaking process. Once CMMC 2.0 is codified through rulemaking, the DoD will require companies to adhere to the revised CMMC 2.0 framework. The DoD’s estimate for completing that process is 9-24 months from November 2021.
Preparing for CMMC with Sprinto
While there isn’t much clarity on the timelines (expected to be May 2023), it isn’t reason enough to pause the preparations. Instead, it is time to streamline your organization’s processes and controls to achieve CMMC.
Sprinto is built to intelligently automate your cybersecurity compliance requirements. With its in-app integrated risk assessment and gap analysis, your journey with Sprinto needn’t end with completing the certification process. Sprinto offers a real-time continuous monitoring feature that can free up your engineering leadership’s time to pursue the more productive growth needs of the organization, a must-have for your CMMC certification.
You can add more cybersecurity frameworks such as SOC 2, PCI DSS, GDPR, ISO 27001 as your organization grows and build off the already-implemented security controls.
Talk to us today to get the proper assistance in achieving CMMC compliance.
FAQs
Is the NIST standard the same as CMMC?
Not exactly. NIST 800-171 is a set of standards created by the National Institute of Standards and Technology (NIST), while CMMC is the process organizations go through to meet those standards. The differences get more detailed when you dive into the federal guidelines, but that’s the basic distinction.
What’s the difference between CMMC Level 2 and Level 3?
CMMC 2.0 Level 2 is pretty much the same as CMMC 1.02 Level 3, based on NIST SP 800-171. It includes all 14 domains and 110 security controls from CMMC 1.02 but removes the 20 unique Level 3 practices and processes specific to CMMC 1.02.
How much does CMMC certification cost?
CMMC certification costs vary based on the organization’s size and level of certification needed. Costs range typically from $3,000 to $60,000 and include factors like assessment fees, preparation, and potential remediation.
What is the difference between CMMC and NIST?
CMMC certifies DoD contractors with specific cybersecurity maturity levels, focuses on certifying compliance, and requires third-party assessments. NIST provides comprehensive cybersecurity guidelines, best practices, standards, and frameworks for various sectors but generally relies on self-assessment.
How long does a CMMC assessment take?
A CMMC assessment typically takes several weeks, depending on the organization’s size and complexity. Preparation, documentation review, and the actual audit process contribute to the timeline. The assessment duration can range from a few weeks to a couple of months.
Anwita
Anwita is a cybersecurity enthusiast and veteran blogger all rolled into one. Her love for everything cybersecurity started her journey into the world compliance. With multiple certifications on cybersecurity under her belt, she aims to simplify complex security related topics for all audiences. She loves to read nonfiction, listen to progressive rock, and watches sitcoms on the weekends.
Explore more
research & insights curated to help you earn a seat at the table.
















