
You are here because somewhere in your business improvement plan because your business prospects specifically asked you for your SOC 2 certification. For a cloud hosted company processing sensitive customer data, this is not uncommon and a major sales unblocker. But in order to be certified, you should understand the nitty gritties of the process.
This article explores it all – the certification journey entails in details – the myths, the best practices, the control selection process, the auditing requirements, and much more!
Let’s begin…
What is SOC 2 certification ?
SOC 2 certification is an attestation report issued by AICPA-approved auditors that certifies that a service organization has the right operational controls pertaining to security, availability, confidentiality, processing integrity, and privacy needed to protect customer data.
SOC 2 certification is a voluntary compliance standard for service organizations, developed by the American Institute of CPAs (AICPA), which specifies how organizations should manage customer data. The standard is based on the following Trust Services Principles.
The process of getting SOC 2 certification is a quick one and takes 1 to 2 months also depends on size of organisation. This process involves selecting the trust principles, defining the controls, assessing the security process, and receiving an attestation report from external auditors. The time taken to get certified depends on the nature of your organisation and the auditor’s time to evaluate.
Why is SOC 2 certification required?
SOC 2 certification is voluntary compliance for service organizations to showcase their ability to protect sensitive information for customers, enabling them to build trust and commitment. It attests that necessary security controls and processes are implemented to protect customer assets and data.
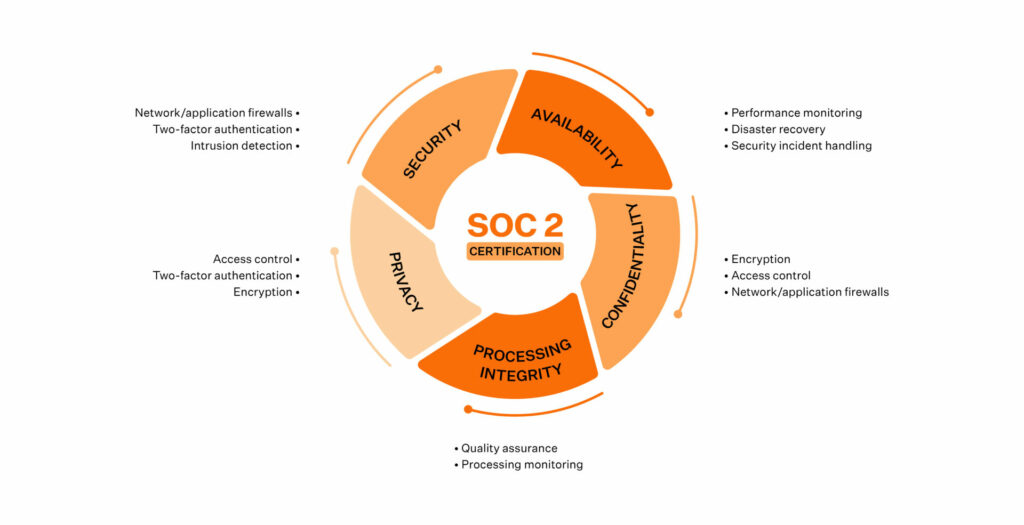
A SOC 2 certification is a report on your organization’s adherence to one or more of the 5 TSCs of SOC 2.
SOC 2 certification helps you attract and retain customers or business partners who are security conscious, giving you a competitive advantage over those who are not certified.
A SOC 2 certification also demonstrates your organization’s design and effectiveness of the administrative and technical controls and policies you have implemented for your information security systems.
Automate SOC 2 compliance effortlessly
5 Steps to Get SOC 2 Certification
Now that you’ve understood the role TSCs play in your SOC 2 certification journey let’s move on to the next steps.
But before we tell you everything you need to know about getting SOC 2 certification, let us first bust a popular myth. ‘There is no such thing as a SOC 2 certificate’. Instead, at the end of your SOC 2 journey, a certified SOC 2 auditor reviews your security systems and gives their ‘SOC 2 attestation‘ to your compliance posture.
Here are the 5 steps to get SOC 2 certified:
Step 1: Select The Trust Principles You Want to Get Audite
Among the five TSCs, Security is the compulsory one. So you need to add that to the cart. If you store customers’ personal data, add Privacy to your SOC 2 cart. And if you manage the financial information of customers, then add processing integrity to the cart. All SaaS firms typically add Availability – since they are on the cloud, it’s an apt TSC for them.
So the key is understanding and recognizing your business operations, mapping them with the TSC, and picking those that apply to your business.
It’s important to understand and remember that every criterion in the trust principles need not apply to your business.
In our experience, customers usually go for Security, Availability, and Confidentiality.
Step 2: Define the Controls
Once you’ve selected the TSC that applies to your business, define the controls that will help you achieve compliance when mapped against the SOC 2 requirements. You can either look for control templates online or hire an external consultant.
For ease of application, you can classify these control into two buckets:
- Administrative controls
- Technical security controls
Administrative Controls
These are the controls you will have to implement to demonstrate effectiveness in people management, physical security measures, documentation policies, policies for instances when a new person joins the team and when an existing member leaves the team, and more.
Technical Security Controls
Technical controls are those that you apply to ensure that your technical infrastructure is secure and built to protect customer data from internal and external threats. Examples of technical security controls include firewalls, access controls, multi-factor authentication (MFA), encryption methods, and more.
How to implement SOC 2 controls automatically?
Step 3: Performance test of selected controls
There is one more step to SOC 2 compliance. Though this is not a mandatory requirement, it is a best practice.
After implementing your controls, you must test them, find control gaps vis-a-vis SOC 2 requirements, and remediate them. Post remediation, check again to ensure that nothing slips through the cracks.
This stage is also called the readiness assessment stage. Once you’ve chosen the trust criteria and applied the controls, you now assess whether you are ready to be audited by an external auditor. You can either assess your compliance posture yourself or have an external consultant review it and give you an unbiased opinion on your current security posture.
This step is optional and is an added cost to your SOC 2 journey. But it is also one of the most widely implemented security practices. Talk to our experts to know if this is right for you.
Step 4: Get your SOC 2 certification report audited by a certified CPA
The last step is to get an external auditor to review your security systems and compliance posture. This process will have you submit evidence for various controls, procedures, and policies. Again, expect frequent back and forth between the auditor and you. You will be asked to share additional evidence, insights on a temporary or consistent lapse in control effectiveness, or something else that could come up. A typical audit goes for 4 to 6 weeks.
When you work with Sprinto, this process is significantly smoother because the evidence-collection process is automated and is designed to collect evidence periodically.
This evidence is stored in a way that is easy for the auditor to review and assess. Suppose the auditor wishes to check the historical data on the effectiveness of a specific control. In that case, all they have to do is click on a few links and voila, they have access to the historical data they need.
Step 5: Receive a SOC 2 attestation report
Depending on how all your policies and controls are performing, the auditor awards you a qualified SOC 2 attestation report or a (SOC 2 certificate). Or, you receive an unqualified or adverse report highlighting the flaws in your systems, in which case it’s best to fix the patches and undergo the audit again to obtain a report with no non-conformities.
Sprinto continuously monitors your cloud security posture to collect evidence for the SOC 2 controls you’ve implemented in an audit friendly manner. With Sprinto, you can:
✔ Comprehensively map all entities that directly or indirectly impact data your security
✔ Access a network of auditors to async audit and quickly gain certification
✔ Automate evidence collection for all compliance related actions in a single dashboard
Save 80% of man hours spent on SOC 2 with Sprinto
What is the difference between SOC 2 Type 1 and Type 2 certification?
There are two types of attestations you could go for in your SOC 2 Certification Journey. While these have some similarities, there are a few minor differences security certifications have.
- SOC 2 Type 1 attestations
- SOC 2 Type 2 attestations
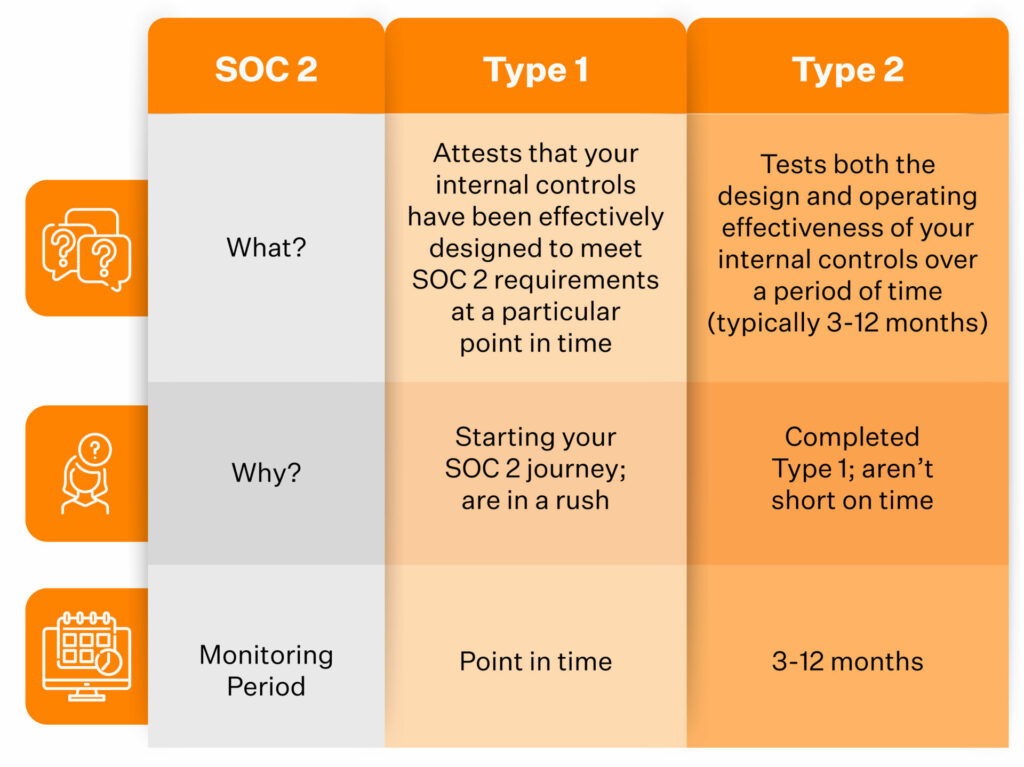
SOC 2 Type 1 attestation is the simpler one and costs relatively less. That’s because it is a snapshot of how well your organization has implemented its internal controls and policies at a point in time. A typical SOC 2 Type 1 process takes between 1 to 3 months. SOC 2 Type 1 evaluates how well the implemented controls and policies are designed and mapped against the requirements listed for the TSCs you’ve chosen over a period of time.
Sprinto seamlessly integrates with your cloud system to continuously map entities that impact data security directly or indirectly. Using an integrated risk assessment system, it verifies and automatically records your risk status in detail.
Check out this detailed video on the difference:
Find out which type of report would be best for you. Speak to our experts now
SOC 2 Type 2 is significantly more comprehensive when compared to Type 1. SOC 2 Type 2 evaluates how well the implemented controls and policies are working and are mapped against the requirements listed for the TSCs you’ve chosen. A SOC 2 Type 2 attestation process has a monitoring period that lasts between 3 to 12 months.
Both SOC 2 Type 1 and SOC 2 Type 2 require businesses to undergo a mandatory audit to get attested.
In our experience, when SOC 2 attestations are needed to unblock sales deals, often prospects are looking for a SOC 2 Type 2 report unless the prospects have specifically mentioned that even a SOC 2 Type 1 will do the job.
Get Our Practical SOC 2 Guide;
Yours at No Cost

How much does it cost to get a SOC 2 certification?
An average SOC 2 certification/attestation cost ranges between USD 20,000 – USD 50,000.
Your SOC 2 certification cost will depend on factors like employee size, the infrastructure used, the existing tech stack, add-on costs, and auditor fees.
Worried about your SOC 2 compliance efforts? Here’s a quick way to get a rough estimate on tech stack, automation, audit readiness, and more.
Here’s an infographic that walks you through the variables that affect the price.

How long does it take to become SOC 2 Certified?
You can get certified in months, not years. In just three simple steps, Sprinto helps you build entity level controls and run fully automated checks so you become compliant and pass compliance audits with breeze.
Realistically, the market standard timeline for SOC 2 Type 1 is 1 to 3 months, and for SOC 2 Type 2, it is 3 to 12 months.
Must check: SOC 2 Auditors and Service Providers [How to Choose One]
However, the following factors affect the total timeline:
1) It depends on the time taken by your organization to become SOC 2 audit-ready
2) The time taken by the auditor to complete the audit
What are trust services criteria? Why is it important for SOC 2 certification?

Trust Service Criteria is the epicentre of your SOC 2 journey. Security, Availability, Confidentiality, Privacy, and Processing Integrity are the five Trust Service Criteria of SOC 2.
Based on your business model, you will need to choose the criteria that apply to you and your processing activities. We’ve included a summary of the five trust service criteria and what they aim to achieve here.
You can choose the criteria that applies to your business based on the data you process. Note that off the five criteria, Security is a must-have, while the others are optional.
Before we dive in and learn more about the Trust Service Criteria, it is imperative to know that each of the five TSCs will apply to your organization’s Infrastructure, Software, People Policies, and other Procedures.
Security
As we mentioned earlier, Security is a must-have criterion and is also known as the common criterion.
Availability
This criterion will require your organization to demonstrate how they maintain uptime and meet global performance standards.
Confidentiality
This criterion requires your organization to demonstrate how customer data is secured right from when it enters your business environment until it is safely disposed of.
Privacy
This criterion details the guidelines for protecting Personal Identifiable Information (PII) and the controls and measures required to protect PII. This will have you share insights on the measures and policies in place to ensure that the data you process in your cloud assets is safe, reliable, and accurate.
For example, information on the use of encryption protocols, access control mechanisms, firewalls, and data loss prevention tools will be in the scope of this criterion.
Processing Integrity
Organizations in the fintech space and those who deal with payment processing are the ones who usually include this criterion in their SOC 2 Scope.
Find out How Sprinto can help companies become SOC 2 certified
Sprinto is purpose-built to help organizations become SOC 2 compliant in a seamless and cost-effective way. Our integrated dashboard gives you complete visibility of your compliance posture and gives you a real-time score to help you monitor your compliance progress and also identify areas in your business environment that need your attention.
In addition, Sprinto’s compliance automation engine relies on its automated evidence collection and continuous monitoring engine to ensure that the auditor receives all the evidence on controls, procedures, and policies from the time of a specific point in time.
How Sprinto helped Dassana launch a compliance program centered on visibility
That’s not all; our auditor-facing dashboard is custom-designed to meet the auditor’s requirements. All the evidence is presented to them in the format they choose to work with and in their order of preference. This ensures they have everything they need without asking our clients for more information. This reduces the audit time frames by weeks.
Did we tell you about the cost? Because we rely on automation, we don’t feel the need to charge our clients huge sums. As a result, the Sprinto pricing model will cost you a fraction of the average market price.
Does this sound too good to be true? Then, talk to our experts today to know what your SOC 2 journey with Sprinto would look like, and don’t shy away from asking them about the Price and completion timelines.
FAQ
How long does it take to get SOC 2 Type 1 certification?
A typical SOC 2 Type 1 process takes between 1 to 3 months. The time taken depends on various factors like the scope of your audit and the number of controls.
Is it necessary to be SOC 2 certified?
Being SOC 2 Certified is not mandatory. However, compliance with SOC 2 ensures that your organization has taken measures to protect sensitive information or intellectual property from unauthorized access and maintain top-notch security.
Who needs a SOC 2 Type 2 certification?
SOC 2 Type II reports are usually needed by businesses that seek IT service providers or third party vendors. This attestation is most useful and will provide comprehensive coverage within the Systems and Organization Controls protocol. It does not provide actual security but helps to gain the trust of potential customers.
How long does it take to get SOC 2 certified?
The timeline to get a SOC 2 report depends on the size of your organization and how fast the controls are implemented. For type 1, it takes about 2 to 3 weeks and for type 2, you can expect to get it in at least three months.
What are some of the common challenges to getting SOC 2 attestation?
Some common road bumps where companies fail to cater to SOC 2 compliance requirements are defining the audit scope of SOC 2 compliance framework correctly, aligning their business practices as per the framework requirements, documenting policies, finding the right auditor, conducting a risk assessment, finding a pen test partner, and collecting evidence manually.
Vimal Mohan
Vimal is a Content Lead at Sprinto who masterfully simplifies the world of compliance for every day folks. When not decoding complex framework requirements and compliance speak, you can find him at the local MMA dojo, exploring trails on his cycle, or hiking. He blends regulatory wisdom with an adventurous spirit, navigating both worlds with effortless expertise
Explore more SOC 2 articles
SOC 2 Compliance Overview
SOC 2 Preparation and Documentation
SOC 2 Audit and
Reporting
SOC 2 Differences and Similarities
SOC 2 Updates & Management
SOC 2 Industry-Specific Applications
research & insights curated to help you earn a seat at the table.








