With attacks rising year after year, businesses are wary of partnerships unless you can prove you protect sensitive data. A SOC 2 Type 2 report is one way to offer that assurance.
This article clarifies whether you’re pursuing compliance because a client asked, competitors have it, or you’re strengthening your security posture. We’ll cover what SOC 2 Type 2 is, when to consider it, and how to prepare, including timelines, costs, and effort involved.
What is SOC 2 Type 2?
A SOC 2 Type 2 is an assessment resulting in a report that assesses the design and operating effectiveness of controls over an observation period of 3-12 months. The goal is to protect sensitive data and meet the selected trust service criteria (security, availability, processing integrity, confidentiality, and privacy).
In this regard:
There is no formal SOC 2 type 2 certification but the report serves as a recognition of implementation and examination of operating effectiveness of controls by an independent auditor.
SOC 2 requires businesses to undergo an audit by an external AICPA-accredited auditor. Depending on the depth of the audit and the audit monitoring period, SOC 2 reports come in two types: Type 1 and Type 2. But more on that later.
The importance of SOC 2 Type 2 compliance
SOC 2 Type 2 is a crucial requirement, especially for enterprise clients, because it signals security maturity of the vendors through an independent validation of control effectiveness. Organizations get better market access and revenue enablement while mitigating key risks and ensuring operational resilience.
Preparing for SOC 2 Type 2 helps expose gaps before they become high-risk areas and reduces chances of breaches. And finally, companies that are SOC 2 Type 2 compliant get insurance premium advantages where they are supposed to pay 15-30% lower premiums because of the credibility and assurance the framework provides.
Who needs a SOC 2 Type 2 report?
A SOC 2 Type 2 report is required by any cloud business that offers services and handles sensitive customer information. These businesses have strict security expectations and include SaaS companies, fintech, healthcare industries, data centers and vendors pitching to enterprise clients.
SOC 2 Type 2 is a table-stakes requirement to speed up deal cycles when working with clients that need high standards of security and operational integrity.
Why should companies consider becoming SOC 2 Type 2 compliant?
Soc 2 Type 2 reports are a great way to demonstrate organization security and unlock sales deals as it provides evidence that you have implemented the relevant controls and they function effectively.
Here are some reasons why you should consider becoming SOC 2 Type 2 compliant:
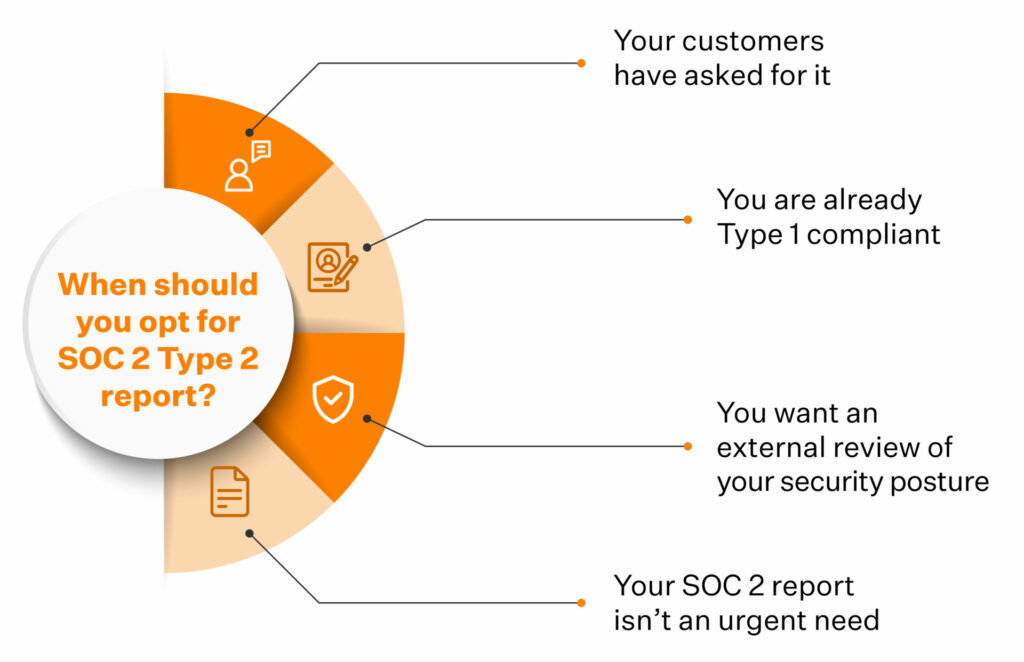
1. Your customers have asked for it
Enterprise customers prefer the more comprehensive Type 2 report for their vendor contracts. A Type 2 report gives them more assurance on your data security and internal controls.
2. You are already Type 1 compliant
The AICPA doesn’t prescribe any rules or hierarchy between Type 1 and Type 2 reports. Companies typically opt for a Type 2 report after receiving the Type 1 attestation.
3. You want an external review of your security posture
It’s one thing to follow the best security practices and another to have a third-party credible authority vouch for it. SOC 2 Type 2 stands testimony to your organization’s cyber security information best practices in keeping with the framework requirements.
4. Your SOC 2 report isn’t an urgent need
Your internal controls get monitored over 3-12 months, during which the auditor tests them for design and operating effectiveness per SOC 2 requirements. So, you must opt for a SOC 2 Type 2 only if you have time on your hands – SOC 2 Type 2 reports can take 5-12 months.
When working with Sprinto, a Type 2 report takes roughly five months to complete. Read how Sprinto helped businesses fast-track their SOC 2 process.
SOC 2 Type I Vs SOC 2 Type 2: Which is right for you?
As we mentioned earlier, the primary difference between the SOC 2 Type 1 and Type 2 is the extent of detail sought during the audit and monitoring period.
While a Type 1 report reviews the design of your internal controls at a ‘point in time’ as per SOC 2 requirements, the Type 2 report, in comparison, checks their design and operating effectiveness over 3-12 months.
Type 1 audits, to that extent, are easier – since your organization gets evaluated at a point in time. And therefore, the evidence requirements are fewer too.
| Aspect | SOC 2 Type I | SOC 2 Type 2 |
| Audit focus | To evaluate control design at a point in time | To evaluate the design+operating effectiveness of controls over a specific period |
| Timeframe | Snapshot assessment | Covers an observation period of 3-12 months |
| Depth | Light: includes policy review and control design | Rigorous: requires evidence of control effectiveness such as logs, reports, etc. |
| Audit preparation | Faster to complete- a few weeks | Can take months because of monitoring period |
| Assurance level | Basic assurance | High level of trust |
| Use case | Early stage startups and for readiness checks before Type 2 | Mature companies that require a high level of security and trust and assurance to pitch to enterprise clients. |
How to become SOC 2 Type 2 compliant?
To become SOC 2 Type 2 compliant, companies should understand the AICPA Trust Service Criteria, define compliance scope, implement controls with supporting evidence and engage an independent CPA to conduct audit.
That said, preparing for SOC 2 Type 2, especially if you are starting afresh, can seem daunting. But you can divide and conquer the SOC 2 behemoth by breaking it down into logical steps.
Get SOC 2 compliant without worrying about its complexities
Here are the 3 major steps to be SOC 2 type 2 compliant:
Define your SOC 2 Type 2 scope
SOC 2 compliance requires organizations to put in place controls in one or more of the five Trust Service Criteria (TSC): Security, Availability, Processing Integrity, Confidentiality, and Privacy. These controls get evaluated on an ongoing basis to ensure the protection of your data.
They were formerly known as Trust Service Principles.
While security is a mandatory SOC 2 need, the others aren’t. You can choose the TSC that’s relevant to your organization. Typically, the choice of TSC gets based on specific customer needs and the type of business.
For instance, while availability as a TSC is relevant for all cloud-hosted organizations, processing integrity makes greater sense for fintech or data processing organizations.
In our experience, most SaaS businesses choose Security, Availability, and Confidentiality as their scope.
Define your controls
Once you’ve picked the TSC that applies to your business, it’s time to implement controls that align with SOC 2 compliance. You can find control templates online or hire a consultant to help.
To make things easier, classify these controls into two categories:
- Administrative controls: These controls show how you manage people and physical security. They cover documentation policies, onboarding and offboarding procedures, and more.
- Technical security controls: These controls ensure your technical infrastructure is secure and protect customer data from internal and external threats.
Conduct a Gap Analysis
A SOC 2 gap analysis is a high-level review of your control environment to identify gaps between your current setup and SOC 2 criteria. Depending on the complexity of your environment, it typically involves 1 to 4 hours of evaluation with individuals who can review the controls at a high level.
This analysis covers relevant areas like HR, IT, and engineering. For instance, you might be asked, “Can you explain your process for vetting new hires? Does it include background checks?”
The output will be a report highlighting the gaps and the controls you need to implement to meet SOC 2 criteria. These recommendations can range from tasks like documenting an annual risk assessment to specific actions like establishing a monthly vulnerability scanning and remediation program in your production environment.
Will this guarantee a flawless audit? No, but a successful gap analysis will give you a clear picture of your situation before the external auditor performs the audit.
Sounds like a lot, doesn’t it? Don’t worry. We have you covered. Sprinto, a GRC automation software, helps you uncover compliance gaps and provide a detailed action plan. The platform runs automated checks, pinpoints improvement opportunities, and guides you toward a proactive, structured approach to compliance. See Sprinto in action.
Gather the evidence of the controls – Preparation stage
SOC 2 has a list of sub-criteria for every chosen TSC, and this step requires you to put in place those controls, test them, identify security control gaps, remediate, and test again.
It’s, of course, easier said than done. Any company going through an audit will typically need an Infosec Officer who can run this program. This role gets played by CTO if the company does not have a designated Infosec officer. The infosec office spends roughly about 300 hours identifying and fixing gaps.
Save upto 300+ hours with compliance automation
And for a Type 2, the time involved is longer as evidence collection will need to happen for the coverage period of the entire audit. Organizations that take the manual route to SOC 2 (DIY or work with a consultant) tend to tie themselves up in knots at this stage.
It requires them to implement and monitor many processes to ensure that evidence collection and process adherence gets done accurately.
You can make this step effortless and error-free by automating it. A bunch of tools in the market can automate your audit preparation and evidence collection and save you hundreds of hours.
We’ll tell you how and what to look for in these tools later in the article.
Before you get to the audit, you can conduct a SOC 2 readiness assessment to ensure you have all your ducks in a row. Trust us; you don’t want to enter the audit ill-prepared and risk a qualified opinion in your report.
In SOC 2 parlance, a qualified opinion translates to exceptions and deviations in your compliance. You need an unqualified report, meaning you pass with flying colors!
Automate your compliance: Achieve Always-on compliance!
Partner with for an auditor to certify your SOC 2 Type 2 report
Remember, your SOC 2 report is only as good as the auditor producing it. While it points to your organization’s security posture, at the end of the day, it’s getting reviewed by an auditor attesting to your security practices. So, your choice of a SOC 2 auditor is also very critical here.
You can choose from the Big4, a CPA firm or an individual CPA.
Aside from choosing one that fits your budget, here are some criteria that can help:
- Has the auditor previously worked with organizations like yours?
- What are the timelines the auditor works with? Does it match your requirement?
- Is the auditor open to suggestions and some back and forth with you? Are they rigid or flexible in terms of working style?
Sprinto’s adaptive automation helps you breeze through SOC2 compliance in 3 simple steps using entity-wide SOC2 controls and automated checks. First, we integrate with your cloud system to map all entities and verify your risk status by conducting an integrated risk assessment.
In the second step, use Sprinto’s risk library to identify and implement relevant SOC 2 controls and run automated checks. In the final step, it captures evidence automatically to the dashboard in an audit friendly manner to ensure quick and guaranteed audit success. Learn more.
What does a SOC 2 Type 2 report contain?
SOC 2 Type 2 report gives deep insights into an organization’s internal controls, governance, security processes, infrastructure, practices, and oversights.
A SOC report is an information mine on the audited entity. It comprises general information on the audited organization, the auditor’s opinion on assessing the organization’s controls, and the description of the tests involved.
Recommendations for improving security protocols where needed are also included in the report.
SOC 2 reports include:
Management Assertion: Summarises the organization’s services, products, structures, systems and controls.
Independent Service Auditor’s Report: Contains the auditor’s opinion on your audit performance.
System Description: Captures overview of services provided, system components, control activities, and more.
Applicable TSC and Related Controls, Tests of Controls, and Test Results: Details all the tests (and their results) performed during the audit and gives the insights that explain the auditor’s opinion detailed in section 2. A Type 2 report will also include the controls list, auditor’s tests, and the test results for each listed control vis-a-vis the selected Trust Service Principles (TSC).
Other information provided by the Management: Gives the management’s response to deviations or exceptions highlighted by the auditor in Section 4.
Check out this detailed video on SOC 2 Type 2 report:
How can you utilize SOC 2 Type 2 audit report?
There are several benefits to having a SOC 2 Type 2 audit. While you can flaunt your SOC 2 attestation on the company website and marketing materials, your SOC 2 audit report is for private consumption only.
You can share it with existing and potential customers after signing a non-disclosure agreement (NDA), as your report contains confidential information about your organization’s security posture and description of infrastructure.
Also check out: A detailed evaluation of the SOC 2 audit cost
How long does it take to get your SOC 2 Type ll report?
The time to obtain your Type 2 report can range from 4-12 months. However, it depends on several factors. For one, your route to SOC 2. If you choose a DIY approach or rope in an external consultant, you must set aside 3-6 months for audit preparation alone.
Add to that the audit monitoring period of 3-12 months, and the minimum time to procure the report is roughly six months! And that’s an optimistic bet.
Manual evidence collection and gap monitoring take time and effort and eat into your employee productivity.
The smart way to hasten the process while you improve its effectiveness is to automate it. After all, SOC 2 attestation is an annual affair, and you don’t want to spend precious work hours chasing compliance attestations when you have time-tested off-the-shelf solutions as a workaround.
Also, check out: Examples of SOC 2 reporting
How much does it cost to prepare for SOC 2 Type 2 audit?
The costs of preparing for a SOC 2 Type 2 audit range from $10000-$50000. This financial implication will depend on your organization’s size, complexity (of systems & controls) of operations, audit readiness and the type of auditor chosen.
Again, these are just ballpark estimates.
You can considerably reduce costs when you work with automation players like Sprinto. Not only is Sprinto’s platform cost competent, but it also packs in it many features that can help you reduce other costs overheads, such as readiness assessments, MDMs, staff security training, and more.
How long is a SOC 2 Type 2 report valid?
A SOC 2 Type 2 is typically valid for 12 months after the review period ends. The review period is usually 3-12 months after which the report is issued and organizations must undergo an annual audit to maintain continuous coverage.
Here’s an example, if the review period is March 2024 – December 2024 and the report is issued in February 2025, it will be valid till February 2026.
SOC 2 Type 2 Requirements
Businesses are evaluated on the basis of the five Trust Service Criteria (TSCs); security, availability, confidentiality, processing integrity, and privacy. Security is the most important and compulsory criteria; the rest depend on the type of data you process, the service, and industry.
Let’s understand the requirements for these trust criteria:
- Security – Concerned with protecting customer data throughout its lifecycle. It prevents unauthorized access or disclosure of information and damage to systems. The requirements are:
- Controls over physical and logical access.
- Use of firewalls, encryption, and intrusion detection systems.
- Access control policies, procedures, and authentication mechanisms.
- Monitoring systems and user activity.
- Incident response and recovery protocols.
- Availability – Refers to the information accessibility used by your business and its services. It focuses primarily on business continuity and disaster management. The requirements list includes:
- Disaster recovery plans and backups.
- Business continuity planning and testing.
- System monitoring for uptime, performance, and failures.
- Resource allocation and capacity management.
- Communication with customers regarding availability commitments.
- Processing integrity – Evaluates the timeliness, accuracy, validity, and permission of data hosted in your cloud. The requirements are:
- Input, processing, and output controls.
- Monitoring of data processing to ensure accuracy and completeness.
- Error detection and correction mechanisms.
- Controls to ensure authorized data processing.
- System validations and audit trails to verify integrity.
- Confidentiality – Deals with safeguarding confidential and sensitive information throughout its lifecycle by restricting access to unauthorized users. The requirements are:
- Encryption of data at rest and in transit.
- Confidentiality agreements with employees, customers, and third parties.
- Access restrictions based on business need.
- Monitoring and logging of access to confidential data.
- Data retention and disposal policies.
- Privacy – This principle lists the guidelines that protect PII (Personally identifiable Information) from unauthorized access and breaches. The requirements for the privacy principle are:
- Policies for collecting, storing, and sharing personal information.
- User consent for data collection and processing.
- Access and correction rights for individuals regarding their data.
- Safeguards to protect personal information from unauthorized access or disclosure.
- Data retention and disposal policies to limit unnecessary data retention.
How Phyllo cut through compliance complexity with Sprinto’s proven solution
Benefits of SOC 2 Type ll report
Most businesses get Type 2 reports because their customers asked for it. Reduce incidents: Security breaches don’t just result in financial losses but eat up human bandwidth as well. SOC 2 Type 2 helps you reduce the chances of an incident occurring by improving the operating effectiveness of your controls.
Competitive edge: With more customers becoming security conscious, you gain a competitive advantage when you demonstrate good security practices, helping you unlock more sales deals.
Scale easily: As security frameworks like ISO 27001 and NIST have overlapping control requirements, you can easily scale without putting a lot of effort by building on your existing controls.
Strengthen your posture: You can improve the robustness and effectiveness of your overall security posture using industry grade best practices.
Answer questionnaires: Whenever a customer requires you to answer security questions, you don’t have to start from scratch. Use the templates and pre-built questionnaires to gain customer trust.
Find out how Sprinto can help you become SOC 2 Type 2 compliant
Imagine walking into a SOC 2 audit knowing fully well that you are compliant in every possible way! Sprinto builds confidence in your security posture with its intuitive dashboard and control mapping. The dashboard gives you a bird’s eye and a granular overview of your compliance readiness.
Sprinto automates repeatable tasks and makes it easier to show SOC 2 compliance with evidence. Automated procedures for evidence collection and continuous monitoring ensure you have proof for every control and reduce the back and forth with the CPA.
The auditor dashboard ensures that the auditor gets all the information with relevant documentation they seek in the format they need!
And that’s scratching the surface. With Sprinto, you can conduct security training for staff and maintain logs of it. You can edit and release company-wide infosec policies using our editable policy templates. You can conduct risk assessments and map your compliance to an entity level!
Talk to us to know why Sprinto makes your perfect SOC 2 partner.
FAQs
Who needs to be SOC 2 Type 2 compliant?
SaaS businesses, firms that use the cloud to store sensitive customer information, and cloud service providers can get SOC 2 Type 2 compliance. While it isn’t a regulatory requirement, getting a Type 2 attestation instills confidence in your infosec practices.
Who should go through SOC 2 type ll compliance?
You should consider a Type 2 audit once you are already SOC 2 Type 1 compliant and your customers ask for proof that the applicable controls are working effectively as claimed or as they should.
How much does it cost to become SOC 2 Type 2 compliant?
The costs to prepare for a Type 2 audit depend on your organization’s size, complexity (of systems & controls) of operations, audit readiness, and the type of auditor chosen. And with readiness assessments (optional) and other overheads, you are roughly looking at about $20000-$50000. Again, these are just ballpark estimates.
You can reduce these costs significantly when you work with Sprinto.
What are the soc 2 type ll controls?
Soc 2 Type 2 controls include control environment, communication and information, risk assessment, monitoring activities, control activities, logical and physical access controls, system operations, change management, and risk mitigation.
For how long is a type 2 report valid?
A SOC 2 Type 2 report is valid for one year from the date of its issue. This means your organization should ensure continuous compliance of the relevant controls even after the certification.
Who should go through SOC 2 type 2 compliance?
You should consider a SOC 2 Type 2 audit once you are already SOC 2 Type 1 compliant and your customers ask for proof that the applicable controls are working effectively as claimed or as they should.
Anwita
Anwita is a cybersecurity enthusiast and veteran blogger all rolled into one. Her love for everything cybersecurity started her journey into the world compliance. With multiple certifications on cybersecurity under her belt, she aims to simplify complex security related topics for all audiences. She loves to read nonfiction, listen to progressive rock, and watches sitcoms on the weekends.
Explore more SOC 2 articles
SOC 2 Compliance Overview
SOC 2 Preparation and Documentation
SOC 2 Audit and
Reporting
SOC 2 Differences and Similarities
SOC 2 Updates & Management
SOC 2 Industry-Specific Applications
research & insights curated to help you earn a seat at the table.






