SOC 2 compliance is a thorough standard—auditors ask tough questions and expect verifiable proof such as policies, screenshots, logs, or attestations. If you miss these, you risk piling up audit exceptions, which can damage customer trust.
In this guide, we explain SOC 2, why it matters, and how to approach the compliance process strategically to strengthen credibility and drive growth.
- What it is: SOC 2 evaluates internal controls for data protection, system integrity, and privacy.
- Who needs it: Any company that stores or processes customer data in the cloud (especially B2B SaaS).
- SOC 2 Reports: Type 1 (snapshot of controls) vs. Type 2 (effectiveness of controls over time).
Steps to compliance:
- Undergo an audit by an independent CPA firm.
- Choose relevant TSCs based on your business and data use.
- Conduct internal risk assessments and gap analysis.
- Define and implement required policies and technical controls.
- Map controls to individual TSC criteria (61 in total).
- Automate continuous monitoring to stay audit-ready.
Basics of SOC 2 compliance
AICPA initially designed SOC to address financial reporting (SOC 1). Later, the framework expanded with SOC 2 to focus on broader principles. Let’s explore what SOC 2 compliance means, the structure of a SOC 2 report, the Trust Services Criteria that guide it, and how it differs from SOC 1 and SOC 3.
What is SOC 2 compliance?
SOC 2 compliance is a voluntary compliance standard developed by the American Institute of CPAs (AICPA) that specifies how organizations should manage customer data based on the Trust Services Criteria (TSC) of Security, Availability, Confidentiality, Processing Integrity, and Privacy.
In other words, SOC 2 is a compliance protocol that assesses whether your organization manages its customers’ data safely and effectively within the cloud. It provides evidence of the strength of your data protection and cloud security practices in the form of SOC reports. SOC 2 compliance isn’t a regulatory requirement but is a globally-accepted compliance benchmark.
What is a SOC 2 report (and what it contains)
A SOC 2 report is an independent audit report that evaluates how a service organization manages and protects customer data. It verifies whether the organization’s internal controls meet the Trust Services Criteria (TSC) — Security, Availability, Processing Integrity, Confidentiality, and Privacy.
The report contains details on how these controls are designed and operated to safeguard systems and ensure reliability. Each category is assessed to confirm that the organization’s processes are secure, consistent, and aligned with compliance requirements.
A SOC 2 report is issued and attested by an external auditor, making it a trusted way to demonstrate to customers and prospects that your systems are secure, available, confidential, and private.
Sprinto automates SOC 2 readiness—mapping controls, collecting evidence, and monitoring continuously so you stay audit-ready at all times.
👉 Book a free demo →
What are the SOC 2 Trust Services Criteria?
The SOC 2 Trust Services Criteria (formerly known as the Trust Principles) are the foundations on which businesses are evaluated during an SOC 2 audit.
Think of each criterion as a focus area for your infosec compliance program; each defines a set of SOC compliance objectives your business must adhere to with your defined controls.
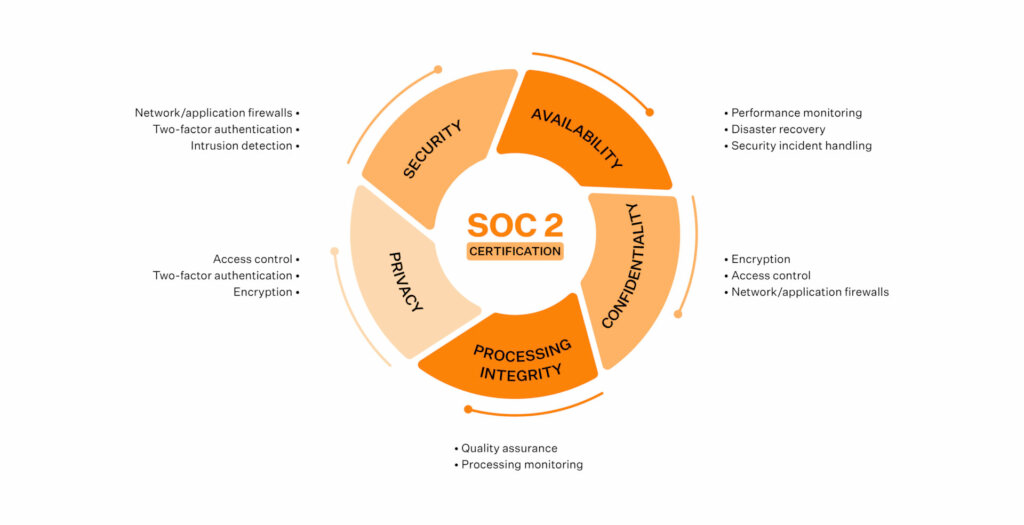
1. Security
It must be in scope for every SOC 2 audit and is, therefore, referred to as the common criteria. It requires you to enable access control, entity-level controls, firewalls, and other operational/governance controls to protect your data and applications. This TSC takes substantial effort and will require participation from your IT development, IT Infrastructure, HR, senior management, and operations teams.
2. Availability
This principle requires you to demonstrate that your systems meet operational uptime and performance standards and includes network performance monitoring, disaster recovery processes, and procedures for handling security incidents, among others. Business continuity, data recovery and backup plans are critical pieces here.
Choose Availability if your customers have concerns about downtime.
3. Confidentiality
This principle requires you to demonstrate your ability to safeguard confidential information throughout its lifecycle by establishing access control and proper privileges (to ensure that data can be viewed/used only by the authorized set of people or organizations). Confidential data includes financial information, intellectual property, and any other form of business-sensitive details specific to your contractual commitments with your customer.
Choose Confidentiality if you store sensitive information protected by non-disclosure agreements (NDAs) or if your customers have specific requirements about confidentiality.
4. Processing Integrity
This principle assesses whether your cloud data is processed accurately, reliably and on time, and if your systems achieve their purpose. It includes quality assurance procedures and SOC tools to monitor data processing.
Include Processing Integrity if you execute critical customer operations such as financial processing, payroll services, and tax processing, to name a few.
5. Privacy
It requires you to protect Personally Identifiable Information (PII) from breaches and unauthorized access through rigorous access controls, two-factor authentication, and encryption, among others.
Include Privacy if your customers store PII such as healthcare data, birthdays, and social security numbers.
What is the difference between SOC 1, SOC 2, and SOC 3?
SOC 1 focuses on financial reporting controls, SOC 2 covers operational controls around security and data protection, and SOC 3 is a simplified, public-facing version of SOC 2.
Here’s a table for the differences:
| Type | Focus Areas | Report Style |
| SOC 1 | Internal controls over financial transactions. | Detailed, technical; not public. |
| SOC 2 | Security, availability, processing integrity, confidentiality, privacy (Trust Services Criteria). | Detailed, technical; restricted sharing. |
| SOC 3 | Same Trust Services Criteria as SOC 2 but at a high level. | Simplified, easy-to-read; can be publicly shared. |
Who needs SOC 2 compliance?
Organizations handling sensitive customer data, such as SaaS companies, healthcare providers, financial services, or any business processing personal or financial information, often need SOC 2 compliance.
SOC 2 is required regardless of a company’s size, even if it’s a startup, as long as they want to have secure data management and build trust with clients.
Who needs to prepare for SOC 2 compliance?
The SOC 2 checklist is explicitly designed for businesses that store customer data in the cloud. So, in essence, it will apply to most SaaS companies and cloud vendors. Besides, the SOC compliance framework offers good security practices for data loss prevention, incident response, intrusion detection, unauthorized access, and other security incidents to ensure business continuity.

3 months of SOC 2 observation
and Engineering at Dassana
Which industries benefit most from SOC 2 compliance?
Industries that benefit most from SOC 2 compliance include:
- Technology and SaaS: Cloud service providers, software companies, and tech startups handling sensitive user data build trust and meet client security requirements.
- Healthcare: Organizations managing protected health information (PHI) under HIPAA, like telehealth platforms or medical tech firms, ensure data security and compliance.
- Financial Services: Banks, fintech companies, and payment processors handling financial data use SOC 2 to prove secure data handling and fraud prevention.
- E-commerce: Retailers and platforms processing customer payment information enhance credibility and protect against data breaches.
- Professional Services: Law firms, accounting firms, and consultancies managing confidential client data demonstrate robust security practices.
Is SOC 2 compliance mandatory?
SOC 2 compliance is not legally mandatory, but clients, partners, or industry standards often require it. It demonstrates adherence to strict security and privacy controls, making it essential for securing contracts.
The SOC 2 compliance journey
The SOC 2 compliance journey requires strategic planning. This section demystifies the process, from initial steps to certification, addressing timelines, costs, hurdles, and supportive tools, drawing on expert insights to guide you efficiently.
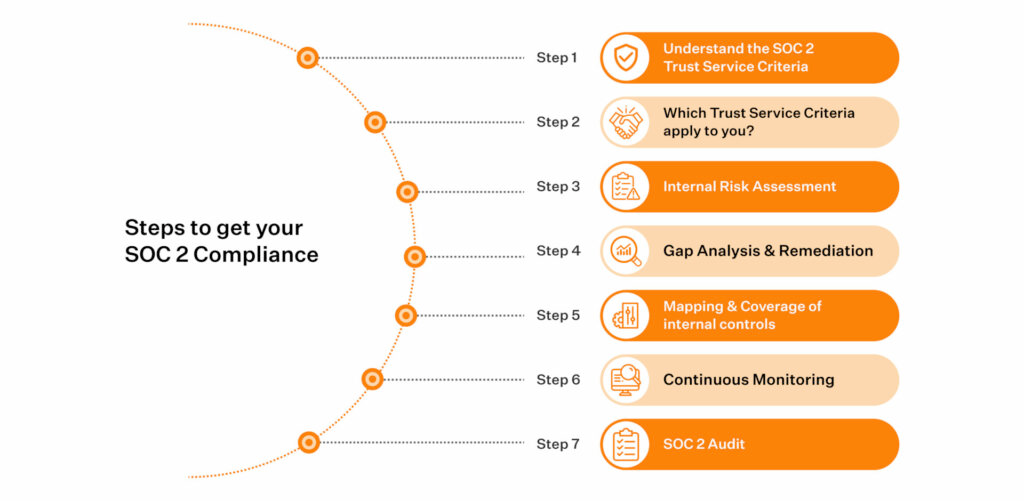
How do you get SOC 2 compliant?
To achieve compliance, you need to understand the many SOC 2 compliance requirements and interpret how they fit into your specific environment.
To do that, you will need to do the following:
Before diving into the five TSCs, it is essential to note that each of the five criteria will apply to – Infrastructure, Software, People, Data, and Procedures in your organization.
1. Choose the relevant Trust Service Criteria for your business
To begin with, evaluate your operating environment and scope out all the TSC before selecting which ones best fit your business model and the customer asks (based on the type of data you store or transmit). For instance, if you are a SaaS firm that stores personal data, Availability, and Privacy as TSC would be more relevant.
But if you manage customer financial transactions, processing integrity could become the critical criteria. To that extent, SOC 2 reports are unique to each business. Doing this will help you cut the flab in the audit process. And you won’t waste your business-critical time and resources chasing attestations and evidence that aren’t meaningful to your business and customers.
In our experience, most businesses only need Security, Availability, and Confidentiality (or their combination) as TSC in their SOC 2 journey. Select privacy and processing integrity if your business processes or holds PII or executes critical customer operations such as financial processing or data processing.
2. Conduct an Internal Risk Assessment
Risk mitigation and SOC 2 risk assessment are crucial in your SOC 2 compliance journey. You need to identify any risks associated with growth, location, or infosec best practices, and document the scope of risks from identified threats and vulnerabilities.
The exercise is subjective, and you will need to assess risks for your business such as from vendors and business partners, misuse of access to information, leadership changes, regulatory, economic and physical environment changes, and technology changes.
You then need to assign a likelihood and impact to each identified risk and then deploy measures (controls) to mitigate them. During the audit, you will be required to demonstrate how you monitor, identify, analyze and prevent losses that could come from those.

3. Analyze Gaps and Plan Remediation
It is crucial to do a gap analysis at this stage. This will help you understand which policies, procedures, and controls your business already has in place and operationalized and how they measure against the SOC 2 requirements.
For instance, SOC 2 requires your production databases to be encrypted at rest and automation tests to be set up for all code repositories that support the application and website. It also requires you to set up a process of at least one review before merging.
If you don’t meet these requirements, you can form a remediation plan to plug the gaps and implement those controls against the gaps. As a best practice, base the remediation plan on your current situation as well as how you want to grow vis-a-vis SOC 2 requirements.
4. Map & Cover All Internal Controls
Each of the five TSC in SOC 2 comes with a set of individual criteria (totaling 61). You will need to deploy internal controls for each of the individual criteria (under your selected TSC) through policies that establish what is expected and procedures that put your policies into action.
For instance, the confidentiality TSC has two individual criteria. So, your internal controls for Confidentiality will need to 1) demonstrate that you have procedures in place to identify and designate confidential information when it is received, determine the period over which the information will be retained, and 2) protect it from erasure or destruction.
You then need to carry out a mapping exercise to demonstrate how your organization meets the selected criteria by aligning your controls. For instance, you will need to map your internal controls to the 33 individual criteria under security (where relevant). While it is okay to repeat controls for some of the criteria, you need to ensure there is enough coverage for each TSC. And if there isn’t, close the gap by remapping some controls or implementing new ones.
Note that the criteria for each trust services category your organization addresses are considered complete only if all the individual criteria associated with that category are addressed. If any criterion is out of scope, you can keep it out of the audit purview with a suitable justification.
The entire process is intensive and time-consuming and can take a chunk of your CTO’s time (who already is swamped with new releases and meetings). But when you work with Sprinto, the process is streamlined, automated, and fast. Sprinto provides a template of 20+ editable security policies that make for an easy read. Did we say our policies’ templates are crafted with no legal jargon to throw you off your compliance game?
Sprinto’s approach to compliance is logical and goes from People, Policies, Infrastructure, Code Repos, Incident Management, and Access Control to Documentation – so you don’t miss out on any security measures. It ensures all the relevant controls under each of these buckets vis-a-vis your TSC are identified and set. Mapping is automated with Sprinto, saving you from hours of dreadful work. You can mark production and non-production assets and define the security criteria for each.
For instance, you can earmark some of your non-production assets from the purview of the audit or temporarily remove specific entities from the scope when an employee is away from work on maternity/paternity leave and can’t encrypt their laptops or update their operating systems.
Sprinto auto-maps 100+ SOC 2 controls to your systems, tracks real-time status, and collects audit-ready evidence — all in one dashboard.
👉 Book a demo →
5. Monitor Continuously
Continuous monitoring is perhaps the most critical step in your compliance journey; one that will help keep you SOC 2 ready always. It’s akin to a continuous loop that requires you to test your controls, remediate the gaps, test again, and continuously collect evidence of compliance.
Depending on the control, you will be able to do this by either taking screenshots, producing policy documents or tickets, showing emails, and pulling out reports from the various tools you work with, to name a few.
You need to create a continuous monitoring system such that it not only validates your compliance with proof, it also alerts you when something isn’t done or done incorrectly.
For instance, when an employee leaves, a workflow should get initiated to remove access. If this doesn’t happen, you should have a system in place to flag this failure so it can be corrected. Continuous monitoring will help you demonstrate with evidence the periodic and dynamic implementation of controls and checks.
With Sprinto, your audit prep is as intensive and exhaustive (sometimes even more) but is entirely automated! From giving you a dashboard overview of your SOC 2 compliance readiness to providing a granular view of, say, which employees haven’t gone through their security training, Sprinto helps you focus on the controls that need investigation on a real-time basis through continuous monitoring. helpful
The dashboard is designed to capture your audit preparedness (there is even a % marker that shows your preparedness) and flags off lapses, oversights, and vulnerabilities that need fixing. And since each control is aligned to its evidence in the platform, Sprinto makes evidence collection and continuous monitoring easy and error-free. You could even add custom controls, classify your entities and select the evidence you want to share.
Also, find out what the SOC 2 bridge letter is and how it is helpful.
6. Get SOC 2 Attestation
A SOC 2 compliance is as much about your security posture and best practices as it is about getting the attestation from the auditor. Your approach to SOC 2, therefore, should focus equally on the means as well as the end.
At this stage, you need to authorize an independent certified auditor to complete your SOC 2 audit and generate a report. While SOC 2 compliance costs can be a significant factor, choose an auditor with established credentials and experience auditing businesses like yours. Additionally, you will need to find a way to securely share all the documentation and evidence to meet the auditor’s request (through shared drives, for instance).
Typically, you can expect a long-drawn to and fro with the auditor as you answer their questions, provide evidence, and discover non-conformities. An established continuous monitoring practice can help you sail through the audit easily.
With Sprinto, evidence collection and cataloging are automated. You also get access to Sprinto’s network of independent third-party auditors. The auditors (trained in using Sprinto) get all the information they need on Sprinto’s custom Auditor’s Dashboard, making evidence sharing easy for both of you. And unlike most other tools in the market, Sprinto offers 100% case coverage and completely manages the auditor for you!
How long does it take to achieve SOC 2 compliance?
Achieving SOC 2 compliance involves preparation, readiness assessment, and auditing, with timelines varying by report type (Type 1 or Type 2), organization size, control complexity, and whether manual or automated processes are used.
Here’s a breakdown of SOC 2 timelines:
- Manual approach: Typically 3-4 months for preparation alone, extending to several months or up to a year for full certification due to manual evidence collection and remediation.
- Automated approach (e.g., with tools like Sprinto): Reduces preparation to 2-4 weeks, enabling audit readiness in as little as 30 days for smaller or well-prepared organizations.
| Report type | Duration | Nature of assessment |
| SOC 2 Type 1 | 1-3 months | Point-in-time assessment of control design; shorter as no monitoring period is required. |
| SOC 2 Type 2 | 3-12 months | Includes a 3-6 month observation period to test operational effectiveness; audit phase alone may take 4-6 weeks. |
What are the costs involved in SOC 2 compliance?
SOC 2 compliance costs vary by organization size, complexity, and report type. Here’s a breakdown including audit costs:
- Internal Effort: 100–200 hours, costing $5,000–$20,000 based on salaries.
- Tools: Automation platforms like Sprinto cost $5,000–$20,000/year; security tools add $2,000–$10,000.
- Remediation: $1,000–$10,000 for fixing control gaps.
- Audit Fees: $7,000–$20,000 (Type 1); $10,000–$50,000 (Type 2).
- Total: $10,000–$30,000 (Type 1) or $20,000–$70,000+ (Type 2) for small firms; higher for larger ones.
Sprinto reduces compliance effort by 80% through automation, helping you save time, money, and audit headaches.
👉 Calculate your savings →
What are the common challenges in becoming SOC 2 compliant?
Achieving SOC 2 compliance presents several hurdles (and myths), particularly for organizations new to the process. Here are the primary challenges of SOC 2:
- Complexity of scope definition: Selecting the right Trust Service Criteria (TSCs) and defining system boundaries is complex, often leading to over- or under-scoping, which delays preparation.
- Resource intensity: Manual evidence collection and control implementation require significant time (100–200 hours) and skilled personnel, straining small teams.
- Gap identification and remediation: Identifying and fixing control gaps (e.g., outdated security policies or tools) can be costly ($1,000–$10,000) and time-consuming.
- Maintaining continuous compliance: Ensuring ongoing adherence, especially for Type 2 reports, requires consistent monitoring and documentation, which is challenging without automation.
- Auditor coordination: Aligning with auditors and managing their requirements can be time-intensive, particularly if controls are poorly documented.
What tools or platforms can help with SOC 2 compliance readiness?
SOC 2 compliance readiness can be achieved by automating processes like evidence collection, control monitoring, and audit preparation with several automation tools and software. Here are some options:
- Automation tools: Compliance automation platforms like Sprinto, Vanta, Drata, or Secureframe map controls to SOC 2 requirements, automate evidence collection, and provide real-time monitoring.
- Supporting Security Tools:
- Endpoint management (e.g., Jamf, CrowdStrike) for device security compliance.
- Identity management (e.g., Okta, OneLogin) for access control monitoring.
- Monitoring tools (e.g., Datadog, Splunk) for real-time security and performance tracking.
Types of SOC 2 reports
SOC 2 reports are essential for demonstrating an organization’s commitment to data security and trust. Two main types of SOC 2 reports are Type 1 and Type 2. While both assess how well a company’s controls align with the Trust Services Criteria, they differ in scope and duration.
1. What’s the difference between SOC 2 Type 1 and Type 2?
While a SOC 2 Type 1 report affirms that controls are in place at that point in time, Type 2 confirms that the controls in place are actually working too over a period of time; the one we think you will need eventually.
If you decide to go for Type 1, here’s what it would mean:
- It shows your committed to data security
- It indicates you plan on eventually becoming fully SOC 2 compliant
- It’ll give you a ringside view of which organizational controls to include in the Type 2 report
- It’ll give you a practical understanding of the criteria auditors will want to test against in a Type 2 report
Even though a Type 1 report takes less time and makes for a great starting point, as your business grows, there’s a high likelihood that your vendors and prospects will ask for the more comprehensive Type 2 compliance before working with you. Here again, you ought to be aware that to obtain your Type 2 report, you must operate the SOC 2 controls over a period of time, about three-six months for the first audit and one year for subsequent audits.
Learn more about SOC 2 Type 1 and SOC 2 Type 2.
2. Why SOC 2 compliance matters (especially type 2)?
SOC 2 compliance demonstrates your organization’s commitment to protecting customer data and maintaining strong security controls. A type 2 compliance matters even more because it verifies the consistent, real-world effectiveness of these controls over time. It builds greater trust, meets enterprise security requirements, and gives your business a lasting competitive edge.
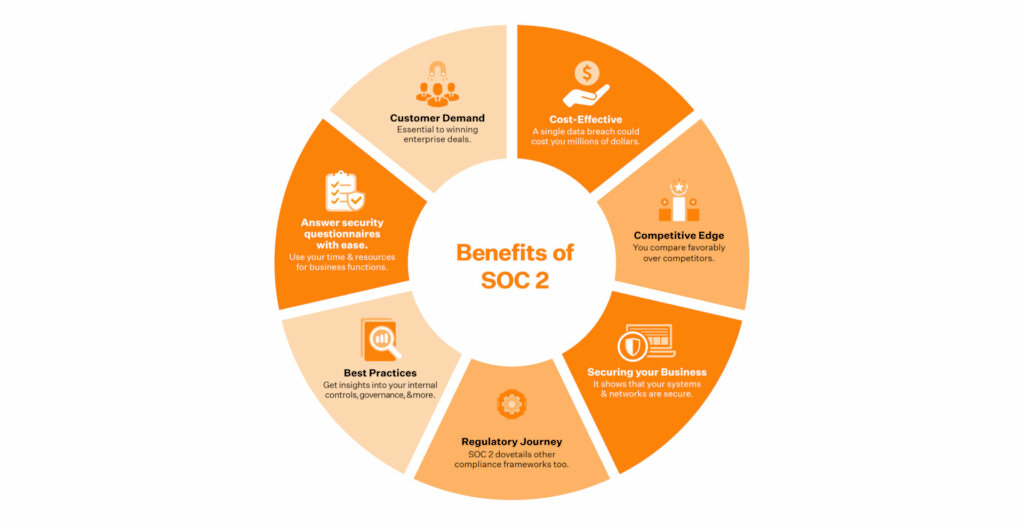
Sprinto can help you get both Type 1 and Type 2 ready. And if you aren’t sure which type of SOC 2 you need, our team will help you decide on what best fits your immediate requirements. Sprinto will also sift through the hundreds of compliance requirements and break them down into easy-to-understand and implementable action items for you.
3. How often should SOC 2 Audits be performed?
To obtain your Type 2 report, you must operate the SOC 2 controls over a period of time — about three to six months for the first audit and one year for subsequent audits. This ensures that your organization continuously maintains and demonstrates the effectiveness of its security and compliance controls over time.
SOC 2 Audit Process
The SOC 2 audit process is a structured evaluation that helps demonstrate how effectively your organization safeguards customer data and ensures compliance with the TSCs.
The audit process typically involves preparation, documentation, control implementation, testing, and final reporting.Learn more about the SOC 2 audit process here.
What happens during a SOC 2 Audit?
During a SOC 2 audit, an independent third-party auditor evaluates your organization’s controls and processes against the relevant trust principles — Security, Availability, Processing Integrity, Confidentiality, and Privacy. The auditor reviews whether your internal controls are properly designed (for Type 1) and operating effectively over time (for Type 2).
The audit involves in-depth testing of control effectiveness, review of documentation, and validation of how systems perform under real-world scenarios. The result is a formal SOC 2 audit report that reflects your organization’s compliance posture and provides assurance to customers and stakeholders.
Here’s everything you need to know about the SOC 2 attestation.
The SOC 2 Audit Report
Once you get the SOC 2 report, you can share it with your customers and prospects. You could also watermark it or request a signed NDA from your prospects before sharing it since the report contains sensitive information.
A SOC 2 audit report includes:
- An opinion letter
- Management assertion
- A detailed description of the system or service
- Details of the selected trust services categories
- Tests of controls and the results of testing
- Optional additional information
How should you prepare for a SOC 2 audit?
Preparation starts with defining the scope: identifying which systems, processes, and trust principles are relevant to your organization. Next, ensure that your policies, procedures, and evidence align with SOC 2 requirements.
Many organizations conduct a readiness assessment before their formal audit to identify and fix potential gaps in their controls. This proactive approach saves time and ensures a smoother audit experience.Here’s a detailed guide on how to prepare for a SOC 2 audit.
What documents and evidence are required for SOC 2 audits?
During the audit, you’ll need to provide documentation and evidence that supports your control environment. This includes security policies, access control records, incident response plans, risk assessments, employee training records, and system configurations.
The goal is to demonstrate that your security and compliance processes are not only well-documented but also consistently followed.
Evidence collection is another critical step. It involves gathering real-time data that verifies the implementation of security controls, for example, proof of access reviews, vulnerability scans, and encryption logs.
Who conducts SOC 2 audits?
SOC 2 audits are conducted by licensed CPA (Certified Public Accountant) firms that specialize in information security audits. These auditors are authorized under the American Institute of Certified Public Accountants (AICPA) and follow its defined audit standards.
The auditor’s role is to provide an independent opinion on whether your organization’s controls are appropriately designed and operating effectively over time. Partnering with an experienced auditor ensures credibility and smoother navigation through the process.
Sprinto makes it easier for you to do all this and much more by automating the changes to policies and procedures.
The smart way to become SOC 2 compliant
With Sprinto, your audit journey is a well-thought-out and detailed process during which we help define the controls and checks, and automate it all with our easy-to-use and intuitive platform. Sprinto replaces all the manual, error-prone, repetitive, and busy work with automation. Book a free demo here to see how Sprinto can help you successfully start and sail through your SOC 2 journey.
Why should you listen to us?
Sprinto was founded as a solution to the problems its founders faced when they needed to get a SOC 2 certification? While getting a certification for Recruiterbox, a B2B SaaS company they had co-founded earlier, the founders spent months, tens of thousands of dollars, and a ton of effort. During this time, their product development came to a grinding halt, and they landed up cannibalizing other projects!
As it turns out, this is a typical story with many companies. While the compliances by themselves aren’t unwieldy, the solutions to obtain them are all stuck in the past.
Sprinto ensures you don’t put your business growth on the back burner while working on getting security certifications to earn your customers’ trust. When done well, a SOC compliance can serve as a growth enabler and help swing those lucrative enterprise deals in your favor!
Sprinto helps you get audit-ready in weeks with automated control mapping, continuous monitoring, and expert support.
👉 Book a demo →
SOC 2 Compliance FAQs
SOC 2 audits are exclusively carried out by licensed CPA firms or agencies accredited by the AICPA. Also, the auditor or auditing firm must be an independent CPA, ensuring they have no affiliations or connections with the service organization being audited.
SOC 2 compliance is a voluntary standard established by the AICPA for service organizations. It outlines guidelines for effectively managing customer data. The SOC 2 standard is built upon the Trust Services Criteria, which includes the following key aspects: security, availability, processing integrity, confidentiality, and privacy.
SOC 2 compliance entails meeting specific criteria evaluated during an audit. In 2023, there are five essential TSCs that businesses need to adhere to. These criteria include Security, Availability, Confidentiality, Processing Integrity, and Privacy. Each TSC sets out your organization’s compliance requirements by implementing robust internal controls.
Yes. A SOC 2 report shows that you take data security seriously, which builds trust with customers. It helps you clear security reviews faster, avoid deal blockers, and move through procurement with less friction. Many buyers now expect it, especially in B2B and enterprise sales.
Without SOC 2, you may lose deals, especially with mid-market or enterprise customers who expect it during security reviews. It can also increase the risk of data gaps, audit issues, and lost trust. SOC 2 helps you stay competitive and build credibility.
Pritesh Vora
Pritesh is a founding team member and VP Growth & Marketing at Sprinto. He comes with over a decade of experience and is a data-driven dynamo in growth strategy, sales, and marketing! His strategies have crafted the success of not one, but two early-stage SaaS startups to 7-digit revenues within a year – he’s your go to guy for all things growth.
Explore more SOC 2 articles
SOC 2 Compliance Overview
SOC 2 Preparation and Documentation
SOC 2 Audit and
Reporting
SOC 2 Differences and Similarities
SOC 2 Updates & Management
SOC 2 Industry-Specific Applications
research & insights curated to help you earn a seat at the table.










