
Setting up a security operations center (SOC) requires a lot of involvement and collaboration. From defining objectives to implementing effective processes, every step can feel arduous and daunting. Especially while manually sifting through logs, delaying incident responses, and decoding scalability issues. And this is why you need SOC tools.
SOC tools leverage automation to streamline the processes needed to strengthen the organization’s security posture and enable a strong monitoring mechanism.
Read on to learn more about SOC software and how to choose the right one for building a strong security operations center.
What is a SOC tool?
A SOC tool is a software solution that helps security teams identify, monitor, manage, and mitigate security risks within an organization. SOC tools encompass a range of functionalities like data collection and analysis, security incident management, vulnerability management, behavioral monitoring etc.
Here is a quick graphical view of the SOC concept of operations:
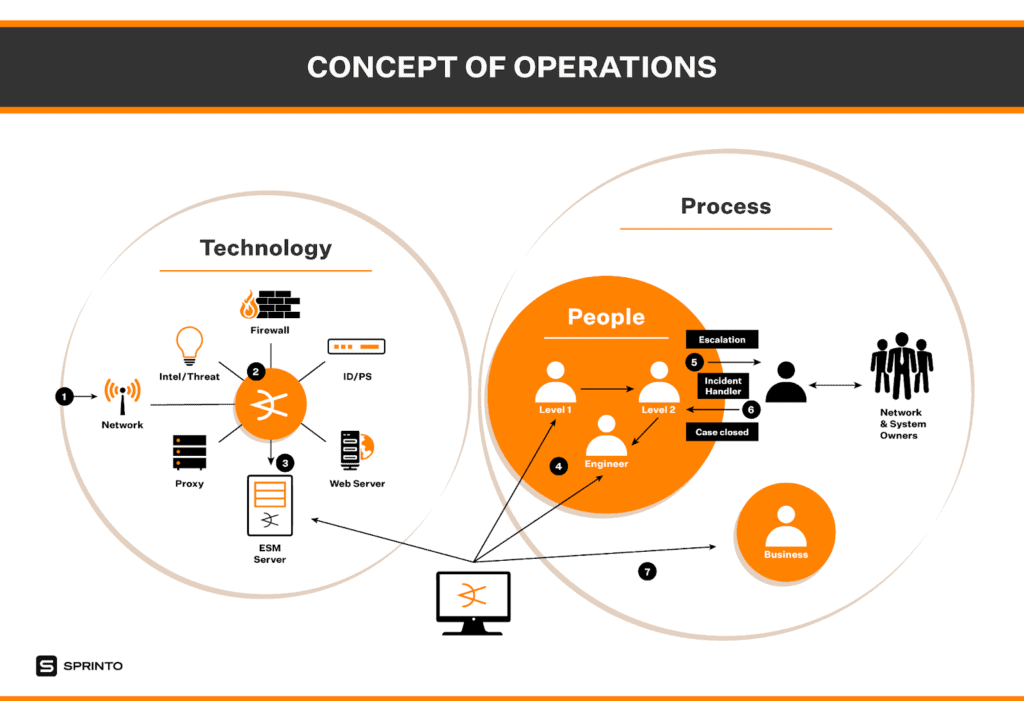
Best SOC Tools List in 2025
The market offers a range of SOC tool options each with its own unique capabilities. The choice of SOC software will however depend on a number of factors and we’ll talk more on the selection part later.
Here’s a detailed SOC tools list you must refer to:
1. Sprinto (Get Started)
When it comes to putting security operations on autopilot, Sprinto is a great collaborator for the SOC team.
It automates security compliance and provides enhanced features like integrated risk assessments, device monitoring, proactive alerting and seamless evidence collection.
Tasks, documentation, incident management and audits, everything is streamlined with Sprinto and there’s centralised visibility across the IT infrastructure and at exacting level.
Sprinto is suitable for all types of organizations from small to mid-sized and enterprises.
| Key Features | Pros | Deployments |
| Vulnerability & incident management Role-based access controls Tiered remediation Baked in MDM (mobile device management) | Scalable compliance programs 100+ integrations supported Audit-friendly Ready to use documents and policy templates | On-premise and cloud deployments |
Check out the review and rating on G2: Rating: 4.8/5
Sprinto is one of the best tool when it comes to SOC 2 compliance—experience by yourself.
2. Splunk
Splunk is a data collection, monitoring and analysis tool that supports the SOC operations of an organization with its automation capabilities.
Splunk streamlines data sourcing, tagging and alerts so as to enable the SOC team to derive powerful insights and take well-informed decisions. It leverages machine learning and AI capabilities for threat detection and incident response.
It is well-suited for enterprises handling large volumes of complex data and offers customised dashboards along with a wide array of integrations and add-ons.
| Key Features | Pros | Deployments |
| Advanced threat detection Incident investigation and forensics Orchestration of security operations Log Management | Broad spectrum of use cases Leverages machine learning and AI capabilities Highly scalable platform Advanced analytics | On-premises, cloud, hybrid and fully managed Splunk cloud deployment |
G2 Rating: 4.3/5
3. LogRhythm
LogRhythm is a powerful NextGen SIEM platform with a comprehensive feature set to support the security operations of an organization.
It is an effective SOC tool helping the teams identify, understand and respond to incidents and manage workflows. With its centralized dashboard for logs, alerts and events, it helps in proactive threat detection.
It is suitable for medium to large organizations and also supports compliance functions.
| Key Features | Pros | Deployments |
| Cloud based SIEM security Network detection and response Threat intelligence service feeds User and entity behaviour analytics (UEBA) | Intuitive user interface 24×7 visibility across enterprise Flexible deployments Customizable dashboards & reporting | On-premise, cloud-based, virtual appliance and managed services deployment |
G2 Rating: 4.2/5
Implement custom controls with the help of Sprinto
4. CrowdStrike Falcon
CrowdStrike Falcon is a versatile SOC tool for dealing with security challenges and has advanced endpoint detection and response capabilities.
It helps protect against unknown malware with threat intelligence and real-time responses. Organizations can also investigate the root cause of incidents with forensic analysis and enjoy the benefits of managed hunting and expert support.
It is specially suitable for remote organizations because it is a fully cloud-based solution.
| Key Features | Pros | Deployments |
| Endpoint detection and response Next generation anti-virus Incident management Threat intelligence | Harnesses the power of AI Cloud native IT infrastructure Supports integration with SIEM, SOAR and other tools | On-premise, cloud, multi-cloud and hybrid deployments |
G2 Rating: 4.7/5
5. Palo Alto
Offering granular visibility and control, Palo Alto offers a range of security solutions that protect networks and cloud environments.
It is best known for its Next generation firewall that solves a number of modern BYOD (bring your own device) challenges and helps in advanced threat detection. Powered by automation and orchestration capabilities, Palo Alto helps manage security operations quickly and easy.
It is best suited for large enterprises.
| Key Features | Pros | Deployments |
| Next-Generation Firewall Digital forensics Malware analysis and reporting Threat hunting | Uses AI and machine learning Centralized management Automation & orchestration | On-premise, virtual, cloud, and hybrid deployments |
G2 Rating: 4.5/5
Types of SOC tools and technologies
SOC tools and technologies help in identifying, preventing and responding to cyber incidents and in streamlining of security operations. They become a part of an organization’s security ecosystem and facilitate prompt resolution of security events.
Here are the 7 types of SOC tools and technologies that you should know:

1. Vulnerability management tools
Vulnerability management is essentially the process of identification, evaluation, reporting, and resolution of cloud security weaknesses in systems and related software. It highlights tiny cracks that a cyber attacker can use to penetrate critical networks of any organization. The entire IT landscape is assessed for vulnerabilities which helps prioritize possible threats and minimize the attack surface.
2. Endpoint detection and response
Endpoint detection and response are SOC monitoring tools for detecting and responding to suspicious activities on endpoints like laptops, mobile devices and servers. EDR tools can detect sophisticated attacks that can bypass network-based threat prevention tools. These solutions give real-time visibility over endpoint devices thereby preventing exploitation of system vulnerabilities.
3. Intrusion detection systems
Intrusion Detection system is a monitoring system that watches over network traffic to alert the organization about potential security violations. It either detects deviations from usual network behaviour or uses a database of known attack patterns (signature attacks) to catch anomalies and notify the concerned authorities.
4. Access management tools
Access Management is a security tool to help organizations manage access rights and user permissions across the IT environment. These tools prevent unauthorized access to specific files, folders, applications and other data assets that contain sensitive information. They offer greater control to administrators and also automate provisioning and de-provisioning access to resources.
5. SIEM-Security information and event management
SIEM technology is used to collect data from different sources, convert them into data sets and correlate them with other security events for spotting any potential threats. It has the capabilities of analyzing heterogenous data from servers, network devices, firewalls etc. for compromise by converting it into a dataset. The SOC team is then notified for further investigation and action.
6. UEBA-User Entity and Behaviour Analytics
UEBA is a threat detection technology that proactively detects deviation from baseline behaviour patterns in the IT environment. Rather than looking for known attack patterns, UEBA focuses on user and entity behaviour and catches anomalies that may be missed by other security tools. This is done by creating models of normal user and entity behaviour and generating alerts in case the activity is beyond ‘normal’ range.
7. SOAR-Security Orchestration, Automation and Response
SOAR technology is used to automate incident response workflows to reduce response time and manage security breach risks more effectively. It comes with advanced analysis and reporting capabilities, pre-defined playbooks for guided responses and integration capabilities with other security tools. SOAR helps the SOC teams streamline security incident management processes.
Automate all your SOC 2 compliance requirements with Sprinto
How do you choose the right SOC tool?
An operation center retains the traditional command structure and roles despite integrating with development and ops departments. Empowered by new technologies, a SOC identifies and responds to critical security incidents, thus ensuring business continuity.
That is why choosing ideal Security Operations Center tools is essential — an automated system that covers all aspects of IT security. Here are some tips that’ll help you choose the right SOC tools and some mistakes that you must avoid:
Quick tips to choose a SOC tool
- Base the selection on the unique security needs and goals of the SOC team and the organization in general
- Look for integration capabilities to enable collaboration between the new and existing IT infrastructure
- Pick tools that offer scalable solutions: customization, automation, and the ability to handle large volumes of data.
- Ask about after-sales support. Responsive teams with technical knowledge can help avert downtime.
- Ask about how the tool enables changes in security frameworks and handles changes in requirements.
- Advanced analytics and comprehensive reporting capabilities are a must-have.
Mistakes to avoid
- A truly enterprise-level SOC tool costs money. When it comes to maintaining your organization’s information security measures, this is no place to skimp or to cut corners.
- In an attempt to spot every possible threat, many businesses procure multiple security platforms. These are often disconnected and do not possess the sophistication required to identify complicated threats. Move away from this silo mentality and choose a SOC tool that integrates well with your network operations and associated staffing.
- Think of the big picture. Getting excited with the latest technology is tempting. But if it does not fulfill your business requirements, is it even worth it? Finalize SOC analyst tools based on sound risk assessment and data security policies
Ditch spreadsheets—compliance can be done smarter
What constitutes a good SOC tool?
The plethora of tools available in the market to solve the issue, as mentioned above, often confuse founders and CTOs. Identifying the most suitable tool for the business is a challenge.
Check out these factors when qualifying a SOC tool as ‘good’:
Distinguishes high and low-fidelity alerts
A SOC tool must be able to distinguish between low and high-fidelity alerts and notify the team about an anomaly accordingly. A high-fidelity alert is reliable and accurate and requires immediate action.
Goes beyond traditional solutions
Traditional signature-based or endpoint detection solutions and firewalls cannot identify a new and unknown threat. A SOC tool must deploy advanced solutions like behavioral analytics to single out abnormalities in the system. This involves proactive analysis of user and device behaviour for reporting deviations.
Has Log Management and Security scanning capabilities
As a SOC aims to gather as much context as possible about the threat, a SOC monitoring tool must empower the SOC team with its capabilities. Log data from applications, devices, servers etc must be analyzed and filtered for security threats. Security scans should help detect any default passwords, missing security patches, malicious software etc.
Includes Machine learning capabilities
A robust and intuitive tool with ML capabilities can respond to advanced threats better in contrast to traditional systems. It can analyze large volumes of data, learn from historical events and automate a number of incident triage tasks. ML also helps in reducing alert fatigue for SOC teams by reducing the number of false positives.
Sprinto as a SOC tool can enhance your compliance management
Whether you outsource the majority of an organization’s SOC functionality, or staff an in-house team to set up and run a SOC, investing in the best SOC tools and security measures is worth the investment. Depending upon the business size and availability of resources in your budget, choose the best tools in the market that help you conveniently build a SOC
And to support the SOC team, you can always leverage Sprinto’s automation capabilities. Sprinto can help with policy management, implementing controls, incident management, evidence collection and audit-friendly reporting. We ensure that security compliance becomes the default state of the organization and it becomes confident in its resilience.
Build preventative and defensive level security with Sprinto. Book a personalised demo today.
FAQs
Are there any free SOC tools?
Yes, there are some free SOC tool options in the market. These are: OSSEC (for intrusion detection), Wazuh (Open -source security monitoring solution), TheHive (security incident management) etc. However, while these are good to begin your SOC supporting journey, the number of features may be limited as compared to paid versions.
What are the 5 major steps for developing a SOC?
The 5 steps for developing a SOC include Planning, designing, building, operating and reviewing a SOC. The planning phase involves identifying the SOC goals and developing a strategy while the designing phase requires technology selection. Once the SOC is built, the operating phase tests the implementation followed by the final review of SOC.
What are some emerging trends in SOC tools?
Some emerging trends in SOC tools are use of Artificial intelligence and machine learning for threat hunting and response, cloud-based security monitoring, use of automation and orchestration etc. All the threat complexity continues to grow, SOC tools are counting on new technological advancements for fighting cyber incidents.
Payal Wadhwa
Payal is your friendly neighborhood compliance whiz who is also ISC2 certified! She turns perplexing compliance lingo into actionable advice about keeping your digital business safe and savvy. When she isn’t saving virtual worlds, she’s penning down poetic musings or lighting up local open mics. Cyber savvy by day, poet by night!
Explore more SOC 2 articles
SOC 2 Compliance Overview
SOC 2 Preparation and Documentation
SOC 2 Audit and
Reporting
SOC 2 Differences and Similarities
SOC 2 Updates & Management
SOC 2 Industry-Specific Applications
research & insights curated to help you earn a seat at the table.







