
Cloud-hosted businesses today are cognizant of the profound impact security has on customer perception. Ensuring the security of customer data as well as maintaining vendor compliance is an important objective. SOC 2, in this context, is a globally-accepted way to secure data, build trust, and unlock growth opportunities.
But what exactly does a SOC 2 report contain? This article breaks down the key components of these essential documents and offers business owners a practical guide to understanding and leveraging SOC 2 reports.
TL;DR
| SOC 2 reports are comprehensive assessments of an organization’s security controls, typically containing five main sections: Management Assertion, Independent Auditor’s Report, System Description, Trust Services Criteria and Test Results, and Other Information. |
| The Independent Auditor’s Report section is crucial, providing an opinion on compliance (unqualified, qualified, adverse, or disclaimer), while the System Description offers detailed insights into the organization’s security practices. |
| SOC 2 Type 1 reports assess control design at a point in time, while Type 2 reports include control testing results over a period, making them more comprehensive for evaluating ongoing security effectiveness. |
What is a SOC 2 Report?
A SOC 2 report is a detailed description of your SOC 2 audit. It is an evaluation by an independent certified auditor of whether your business provides a secure, available, confidential, and private solution to your customers. The auditor releases the report after examining your organization’s control over one or more of the Trust Services Criteria (that you have chosen).
The SOC 2 report contains the auditor’s detailed opinion on the design and operating effectiveness of your internal controls. It is, in essence, a testimony to the strength of your infosec practices. It is meant to enable the report users (your customers and customer’s customer) to assess and address the risks that arise from their relationship with your organization.
“If you are handling sensitive customer data or looking at Enterprise-Scale customers, especially in the US, SOC 2 becomes a table-stakes requirement for a sales engagement.”
Devika Anil: Lead Auditor at Sprinto
Subscribe to get top-tier insights straight to your inbox!
What does a SOC 2 report contain?
A SOC 2 report is a comprehensive document that provides insight into an organization’s security controls and their effectiveness. Here’s what you should look for in each section:
- Independent auditor’s report
- Audit scope and timeframe
- Auditor’s responsibilities
- Management’s responsibilities
- Limitations of the audit
- Auditor’s opinion (e.g., unqualified, qualified, adverse, or disclaimer)
- Management’s assertion
- Overview of the system
- Statement on the suitability of control design
- Assertion of control effectiveness
- System description
- System boundaries and components
- Infrastructure and software details
- Personnel roles and responsibilities
- Data flow and processing procedures
- Relevant aspects of the control environment
- Trust service criteria and related controls
- Breakdown by criteria (Security, Availability, Processing Integrity, Confidentiality, Privacy)
- Description of controls for each criterion
- Explanation of how controls address the criteria
- Tests of Controls
- Control objectives
- Description of controls
- Test procedures performed
- Results of testing
- Any exceptions or deviations noted
When reviewing a SOC 2 report, pay close attention to the auditor’s opinion, any exceptions noted in the tests of controls, and how the organization plans to address any identified issues.
Re-prioritize growth. Leave the complexities of compliance to us.
SOC 2 Report Example
The crux of the SOC 2 report lies in understanding whether a particular organization meets its audit criteria or not. The SOC report, therefore, provides detailed information about the audit, management perspectives, system description, tests of controls, and other relevant information. While all this can make the report quite intimidating, what with its reams of information in legal-speak, here’s a ready reckoner on the various sections of the report and what to look for in each of them.
A SOC 2 report example helps to evaluate whether your business provides a secure, confidential, and private solution to your customers.
Every SOC 2 report should have the 5 sections:
- Management Assertion
- Independent Service Auditor’s Report
- System Description
- Trust Services Criteria, controls, and test Results
- Other information
In most SOC 2 reports, you will find four sections and an optional fifth section.
Here’s a SOC 2 report example that showcases what each section includes:

Source: AICPA’s Illustrative Type 2 SOC 2 Report with the Criteria in the Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM)
Sections of SOC 2 Report
The SOC 2 report is an information mine about the audited entity. It includes (but is not limited to) general information on the audited organization, the auditor’s opinion on the compliance assessment of the organization’s controls, and the description of the tests involved. The report also includes recommendations for improving security protocols when needed.
Here’s a lowdown on each section and what it contains:
Section 1: Management Assertion
This section provides assertions, statements and facts as given by the audited organization and relates to their system(s) under audit. It’s written by the organization and is essentially the management acknowledging that the information provided is accurate and relevant. The section summarises the organization’s services, products, structures, systems and controls. It, however, doesn’t contain technical details.
Here’s a gist of what this section contains:
- Types of services provided
- Components of systems – Infrastructure, System, People, Procedures and Data
- Aspects of systems
- How the systems capture and address significant events and conditions
- Processes used to prepare and deliver reports
- Any applicable Trust Service Criteria that are not being met by controls, with reasons as to why
Section 2: Independent Service Auditor’s Report
This section is much like your university grade card as it captures your auditor’s rating on your compliance. It shows whether or not you passed the assessment. It is, therefore, one of the most read and important sections of the report.
In this section, the auditor shares their opinion on your SOC 2 audit readiness. It also includes a description of the scope of the audit, the organization’s responsibilities, the auditor’s responsibility and inherent limitations in the assessment, such as human error and circumvention of controls, to name a few.
Here are the four types of auditor opinions and what they mean:
- Unqualified – You pass with flying colours!
An unqualified opinion means that the auditor did not find any issues during the audit. Every control tested was designed appropriately (Type 1 report) and operated effectively (Type 2 report).
- Qualified – Close, but not quite.
The auditor has some reservations as some areas require attention. But how bad is a qualified report? Well, it depends on the controls in question that failed and how they impact the report users.
- Adverse – You failed.
An adverse opinion indicates that the organization materially failed one or more of the standards, and its controls and system isn’t reliable.
- Disclaimer of Opinion – No comments!
This technically isn’t an opinion. It essentially means that the information provided wasn’t enough for the auditor to form an opinion. It happens when the auditors do not have access to the information they need or are unable to complete it neutrally.
Note that this section gives the overall status of the assessment alone. You won’t find details beyond that here.
Here’s a SOC 2 audit report example that highlights the auditor’s opinion.
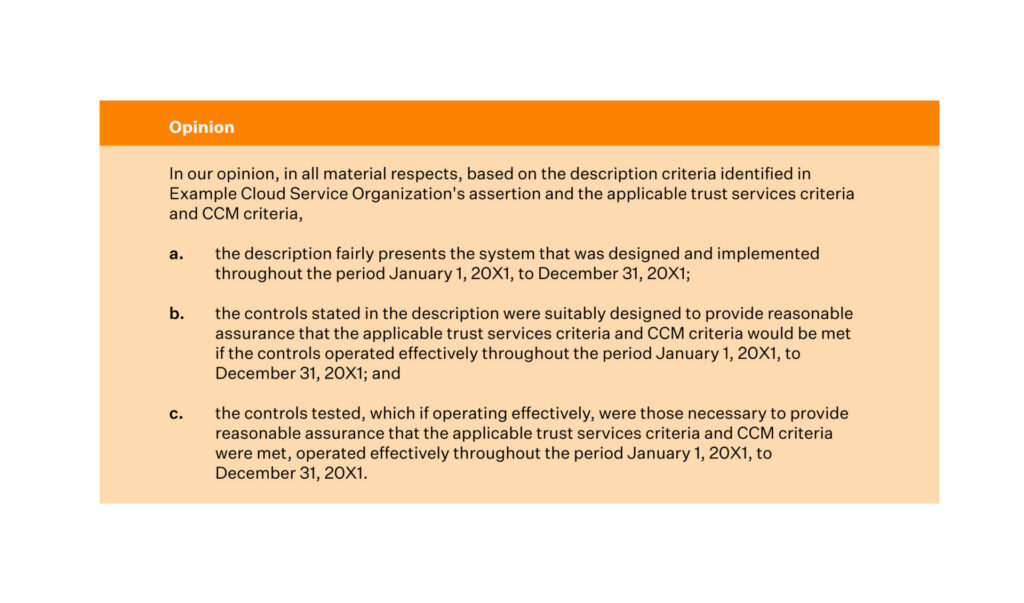
Source: AICPA’s Illustrative Type 2 SOC 2 Report with the Criteria in the Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM)
Section 3: System Description
If management assertion was a brief overview of the organization’s system description, this section is a detailed deep dive. It’s a must-read section and covers the system(s), scope & requirements, components, controls, sub-service organizations and other systems information.
It includes details of the human resources, roles and responsibilities and also features the list of system components and controls grouped with the relevant common criteria.
This section covers a detailed account of the control environment, control activities (policies and procedures), information and communication system, monitoring (to assess the quality of internal control performance through penetration testing and vulnerability scans), and risk assessment (the organization’s assessment of relevant risks and its management).
Some of the items in the system description would be:
Overview of services provided: It contains a brief overview of the services offered by the organization. Your customers will read here to ensure that the services they seek from you are covered in the compliance scope. You will also find service commitments and system requirements here.
System components: You will find technical details such as where the organization (or its application) is hosted, tools used and access control here. For instance, if your business is hosted in AWS, you will need to give details about the AWS environment here. It will contain a detailed description of your infrastructure, software, people, procedures and data.
Control activities: A detailed description of the various control activities of the organization can be found here. From how the organization onboards new employees to how it keeps data secure through database protection, encryption and access, this is your go-to section for how the organization has designed its controls.
Not applicable trust services criteria specifics: If any specific criteria didn’t apply to the organization, they would be described here.
This section is critical for your customer to decide whether they trust you enough to conduct business with you. Invest time to read this section in your vendors’ SOC 2 report.
Complementary User Entity Controls (CUECs) and Complementary Subservice Organizations Controls (CSOCs) are also included here. Any significant changes to the system during the period (Type 2 reports only) are also described here. For instance, a new acquisition, or a change in cloud service provider, to name a few. This section will also contain system incidents if the organization failed to meet its commitments.
Find out how to automate SOC 2 reporting
Section 4: Applicable Trust Services Criteria and Related Controls, Tests of Controls, and Results of Tests
This section details all the tests (and their results) performed during the audit and therefore is a critical section in the report. It gives the insights that explain the auditor’s opinion detailed in section 2.
This section includes (in a tabulated format) the following:
- Control Criteria
- Control Number
- Control Description from the Organization
- Test Description from the Auditor
- Test Results
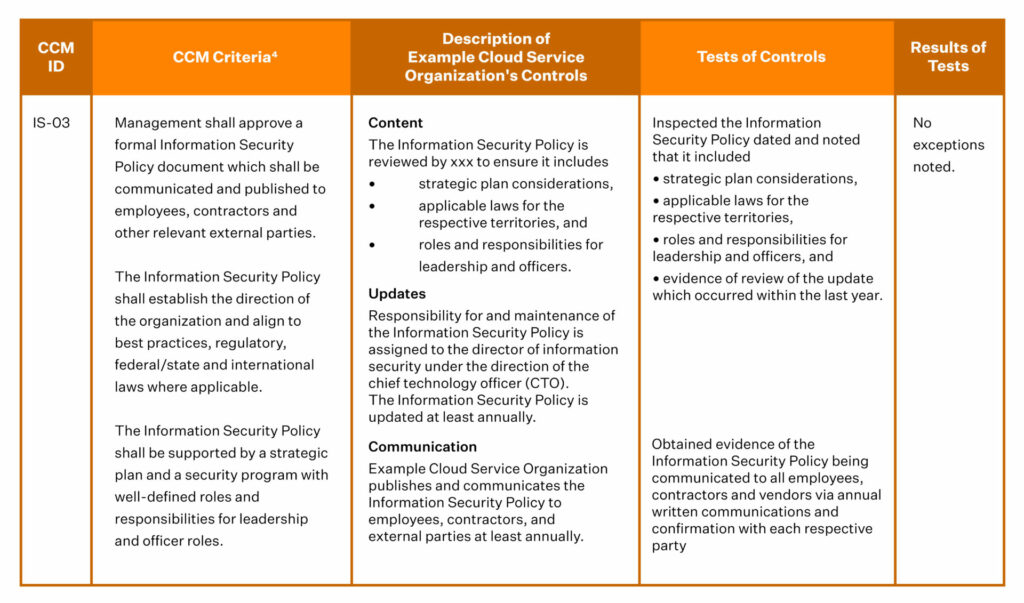
Source: AICPA’s Illustrative Type 2 SOC 2 Report with the Criteria in the Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM)
Download the complete list of SOC 2 controls
Difference between SOC 2 Type 1 and SOC 2 Type 2 Report
While the first three sections of the report will be the same for both SOC 2 Type 1 and SOC 2 Type 2 reports, this section would be significantly different.
In a Type 1 report, this section will feature the list of all the controls tested during the audit. It won’t feature the auditor tests or the results of tests. This is because Type 1 assesses the design of the controls at a point in time.
In a Type 2 report, you will find the controls list, auditor’s tests and the test results for each listed control. This section (for a Type 2 report) will also showcase exceptions or deviations noted by the auditor.
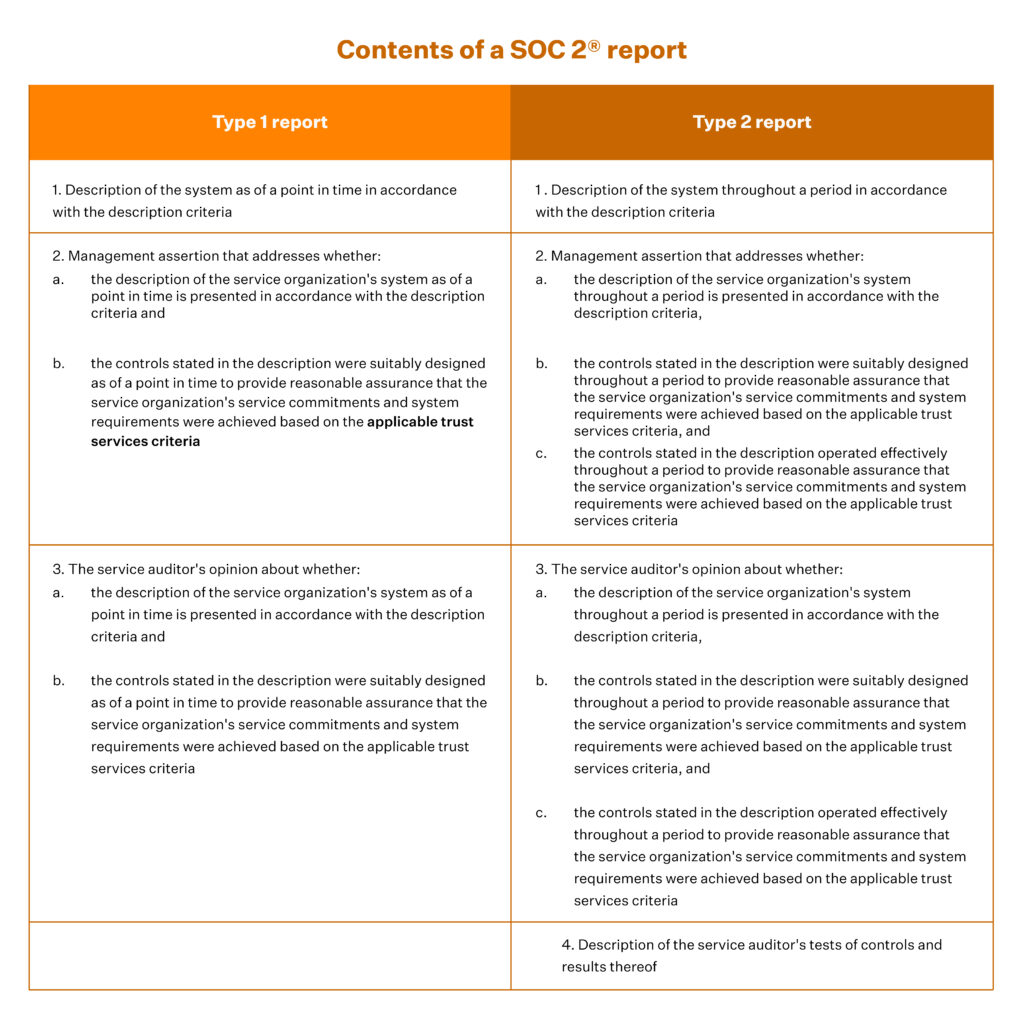
Source: AICPA’s Information for Service Organization Management report
Section 5: Other information provided by the Management
This section is optional and details management’s response to any deviations or exceptions highlighted by the auditor in Section 4 by giving more context and information about the exceptions. For instance, if one of the exceptions noted by the auditor was that some of the new hires didn’t undergo background verification, the management can acknowledge the same here and cite reasons why and propose ways to ensure such misses don’t repeat.
This section also contains information on the organization’s future plans that can have a bearing on its control environment and system(s).
Automation: Smarter audits and effortless SOC 2 reports
Sprinto helps SOC 2 compliance by transforming it into a streamlined, efficient process. Our automation-led approach fast-tracks compliance, making it ten times faster than manual methods while ensuring continuous monitoring through automated checks and proactive alerting.
With Sprinto, you benefit from integrated risk assessment, effortless mapping of risks to SOC 2 controls, and efficient audit preparation that leads to 100% audit success. Our simple three-step process – implementation, risk assessment and control, and automated monitoring – guides you smoothly through the compliance journey.
FAQs
What is the SOC 2 report?
The SOC 2 report is a comprehensive document that details how a service organization manages and protects customer data. It focuses on five trust service criteria: security, availability, processing integrity, confidentiality, and privacy.
SOC 2 reports are particularly relevant for technology and cloud computing companies that store customer data.
What are SOC 1 and SOC 2 reports?
SOC 1 and SOC 2 are two different types of Service Organization Control reports:
SOC 1 reports focus on a service organization’s internal controls that are relevant to their clients’ financial reporting. These are typically used by companies that provide financial services or handle financial data.
SOC 2 reports focus on controls related to the five trust service criteria. They are more relevant for companies that handle sensitive customer data but don’t directly impact financial reporting.
Who prepares the SOC 2 report?
SOC 2 reports are prepared by independent third-party auditors, typically Certified Public Accountants (CPAs) who specialize in information security audits. These auditors must be licensed by the American Institute of Certified Public Accountants (AICPA) to perform SOC audits
Srividhya Karthik
Srividhya Karthik, is a Content Lead at Sprinto, she artfully transforms the complex world of compliance into accessible and intriguing reads. Srividhya has half a decade of experience under her belt in the compliance world across frameworks such as SOC 2, ISO 27001, GDPR and more. She is a formidable authority in the domain and guides readers with expertise and clarity.
Explore more SOC 2 articles
SOC 2 Compliance Overview
SOC 2 Preparation and Documentation
SOC 2 Audit and
Reporting
SOC 2 Differences and Similarities
SOC 2 Updates & Management
SOC 2 Industry-Specific Applications
research & insights curated to help you earn a seat at the table.







