How To Prepare For SOC 2 Audit
Meeba Gracy
Feb 03, 2024

We’ve all been there: You hear from a business partner or customer that you need to pass a SOC 2 audit, and your mind races. How do you create an environment where the auditors feel confident in your security protocols?
So, how to prepare for SOC 2 audit? What steps can you take to ensure success later on during the audit?
In this blog post, we provide insights and tips on how to get ready for SOC 2 audit with minimal stress.
Let’s dive in…
Why do you need to prepare for a SOC 2 audit?
You need to prepare for the SOC 2 audit because it provides the proof that your clients and potential customers may need to verify your company’s security compliance.
Here are some reasons why you need to prepare for the SOC 2 audit:

It helps demonstrate compliance with industry regulations and standards
SOC 2 audits verify that your organization follows best practices for data security, privacy, availability, and processing integrity. This helps customers feel confident that their data is secure and protected from unauthorized access.
It builds trust and credibility with customers
Having a successful SOC 2 audit under your belt can show potential customers that you take data security seriously and have taken the necessary steps to protect their data.
Get rid of the manual SOC 2 audit process with the help of Sprinto
It provides an independent review of your processes
During a SOC 2 audit, an auditor will review all aspects of how your organization handles sensitive information, such as customer data or financial records. This will provide an independent review of your processes and help identify potential risks.
It gives you a competitive edge
SOC 2 audits are becoming increasingly common in the marketplace, and having one can give you a competitive edge over organizations that don’t. This could be especially helpful if your organization works with large enterprises or government entities requiring vendor selection audits.
It provides an opportunity to make improvements
A SOC 2 audit is also an opportunity to improve existing processes or implement the best data security and privacy practices. The auditor will provide recommendations on strengthening your security posture, which can help protect customer data even more effectively.
How to prepare for SOC 2 audit (step by step)
Here are the 7 steps to prepare for SOC 2 audit:
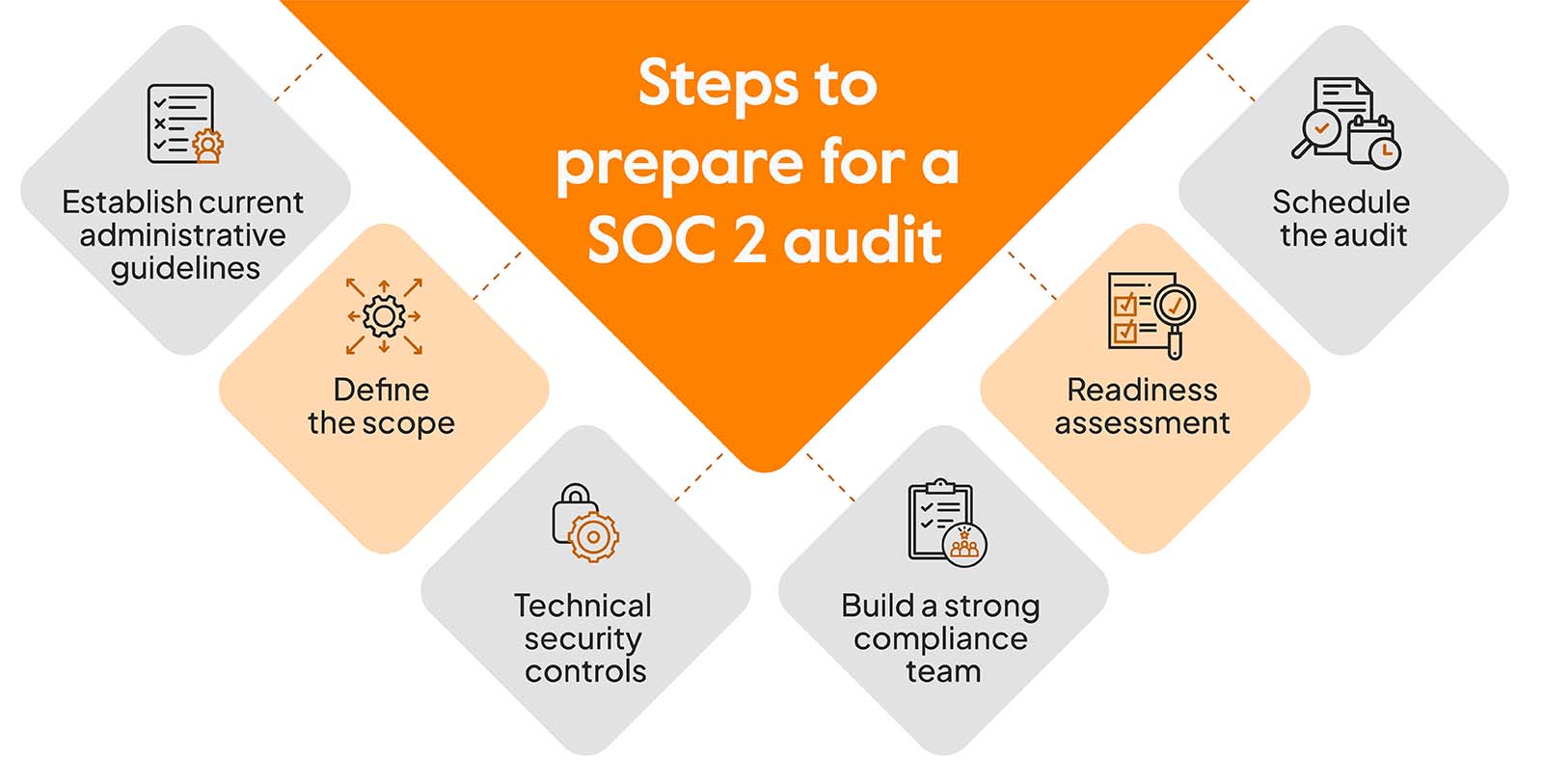
Establish current administrative guidelines
Administrative policies and standard operating procedures (SOPs) are essential to any security program. These policies must be tailored to the team’s structure, technologies, and workflow to keep security risks at a minimum.
These guidelines need to be in plain english instead of complex legal speak, so that everyone understands these regulations. An effective policy should include regular staff training sessions, so that everyone in the org knows their roles and responsibilities.
Your policies should outline standard security processes which cover a range of topics such as System Access, Disaster Recovery (DR), Incident Response, Risk Assessment and Analysis, Security Roles, and Security Training.
Doing this regularly safeguards your business from malicious threats and secures a good reputation within the industry.
Define the Scope
The next step is defining the scope of your audit. There is a wide range of areas to consider depending on the function, such as security, availability, processing integrity, and confidentiality or privacy.
Now, choosing which categories to include requires extra consideration. Focusing on specific policies driven by contractual obligations can also benefit organizations within a heavily regulated industry.
For instance, healthcare organizations—whose data needs to remain secure from malicious attacks- want to ensure privacy in their audits.
This is why defining a comprehensive scope for the SOC 2 audit process is key to getting attested.
Technical security controls
When it comes to keeping your applications and infrastructure secure, implementing technical security controls are a must. While administrative security policies are essential for providing guidance and regulating behavior, technical security controls put the necessary measures in place to protect systems.
Hence, numerous technical security control solutions are available to help teams do this. With the right tools and best practices, you can create efficient access control solutions for your cloud operations, firewall, and network protections with encryption enabled.
From technologies that detect malicious intrusions to vulnerability scanning software with robust audit logging features – there is much you can do to give your operations the advantage of keeping data safe from cyber-attacks.
Implement custom controls based on your requirements
Build a strong compliance team
Achieving SOC 2 certification is a long-term endeavor, but you can make the process smoother and more efficient by selecting individuals to fill essential roles. Good candidates are people who know risk management, internal control design & execution – so be bold about tapping into their expertise! With dedicated personnel leading the way, navigating this lengthy marathon will seem manageable.
- Executive Sponsor: The executive sponsor is typically a senior leader, such as the CEO or COO. They will be the one who signs off on the project and its viability. They will be able to understand more about how current security issues, revenue potentials in the future, and risk management strategies impact business.
- People ops: People operations have become increasingly important in SOC 2 compliance as they are in charge of safe onboarding, background verification, and maintaining an up-to-date legal framework.
- Project Manager: The project manager is the ringleader, helping bring SOC 2 to fruition through coordination and organization. They’ll be gathering essential resources for success, setting hard deadlines, so progress continues steadily; and making sure everyone has what they need to reach greatness together! Note that they don’t need to have experience in compliance.
- Primary Author: To excel in this primary author role, the ideal candidate must bring technical writing savvy and excellent communication skills to the table – not just that, but also an intimate understanding of operations and business. This will help them capture first-hand knowledge from other teams so that the reports are comprehensive and accurate.
- IT and Security team: The IT and Security teams are the guardians of your organization’s data – charged with creating, proving, and demonstrating a practical approach to detecting potential security issues. To ensure success during audit processes, this team must have personnel knowledgeable in the area and financial resources to purchase additional cyber defense tools if necessary. Not only that – they may also be responsible for updating physical access control measures. It’s your responsibility to ensure these warriors have everything they need to prepare for the SOC 2 audit.
- Legal Personnel: Give your legal personnel the reins, and they’ll steer you in the right direction regarding SOC 2 compliance! Get them involved early – their expertise keeps vendor contracts up-to-date and helps ensure that all your documentation remains fresh.
- External Consultants: From startups to established enterprises, Sprinto can help your organization fast-track its way toward SOC 2 certification. We know a thing or two about what it takes for successful compliance and will guide you through the process with our automated software. Let us use decades of expertise in helping companies, big and small, ensure you remain secure!
Readiness Assessment
Readiness Assessments are critical when auditing any organization. They double up as a systems check for IT teams to understand which elements need work. Without the diligence of this process, you may not discover profound issues until the official audit – where it may be too late to fix them.
It happens more often than you think when preparing for a SOC 2 assessment; issues can surface. This can range from minor inconsistencies and sloppiness to significant deficits that cause delays or worse problems. Readiness Assessments are an essential step in completing a successful SOC 2 audit. They can make all the difference.
Review and write security procedures
In preparation for a SOC 2 audit, it is vital to ensure all security procedures are comprehensively reviewed and detailed on paper. Without written policies to serve as a reference for your auditor, the audit process may be cumbersome and result in delays.
Furthermore, without these documents, your employees would not have structured information outlining what actions are permissible on the audited systems, leaving your organization open to potential risks associated with improper protocol.
Updating outdated security procedures and taking the time to create new ones now will simplify the process. This will give your auditor an added sense of assurance in successfully completing the audit.
Schedule the Audit
After assessing where your company stands and what you need, finding a reputable auditing partner accredited with AICPA (American Institute of Certified Public Accountants) is crucial. Finding a partner that has worked with similarly sized companies and is knowledgeable in SOC 2 audits- these will provide you with invaluable insight and ensure an efficient process.
What are the benefits of being SOC 2 audit-ready?
The benefit of being SOC 2 audit ready is that it gives your business the security protocols and resources needed to establish trust with customers and cultivate strong relationships.
Being SOC 2 audit ready can be one of the smartest things you do for your organization. Knowing that your team and processes are in line with the SOC 2 trust principles ensures that you can have peace of mind and rest easy knowing that your data, systems, reports, and security will be up to the highest standard when the audit comes around.
Not only that, but businesses that are already SOC 2 ready show their customers they understand the importance of security and assurance – it’s a sign of excellence.
Being audit-ready provides a result-oriented approach to achieving compliance as it reduces both cost and time spent on preparation. You’ll appreciate how this efficient process lets you get back to focusing on running a successful business without interruption or delay before the official audit.
Are you ready for your SOC 2 Audit?
Every business regulation entails a certain level of difficulty and certification processes. This is even more difficult when you are nearing your official audit.
This is why it’s essential to be equipped with the right assistance throughout this journey to ensure all requirements have been met. After all, it’s no small feat – the process can be time-intensive, leaving your security compliance program all over the place.
Also check out: A quick guide to SOC 2 readiness assessment.
How can Sprinto help?
Sprinto can be such a resourceful ally in helping map out a plan from start to finish.
Ensuring internal control system requirements are met is of utmost importance. Sprinto makes that job easier with its streamlined SOC 2 process and readily-available dashboard.
The scoring system on the dashboard allows you to have a visible account of your organization’s compliance status that can be monitored in real-time, enabling you to stay on top of your SOC 2 preparedness for an audit more effectively.
It’s reassuring to know that this innovative technology can provide peace of mind when dealing with audits.
We track every step efficiently so that you don’t miss a beat. And with its wide range of entity-level security controls, Sprinto aims to ensure no element is left unaccounted for during the audit procedure.
So what are you waiting for?
Let’s get you started with a demo call!
FAQs
Can any CPA perform a SOC 2 audit?
No, a SOC 2 audit must only be conducted by an auditor from a certified CPA firm with expertise in information security. SOC 2 audits are regulated strictly by the AICPA.
What is SOC 2 readiness?
A SOC 2 Readiness Assessment is an audit process that deeply delves into how your organization manages its information assets. It evaluates the effectiveness of physical facilities, data processing systems, and communications processes to ensure they are secure and compliant with industry standards.
Do startups need SOC 2?
The simple answer is yes. Startups should take SOC 2 into consideration when building their operational structure and security protocols.
Meeba Gracy
Meeba, an ISC2-certified cybersecurity specialist, passionately decodes and delivers impactful content on compliance and complex digital security matters. Adept at transforming intricate concepts into accessible insights, she’s committed to enlightening readers. Off the clock, she can be found with her nose in the latest thriller novel or exploring new haunts in the city.
Grow fearless, evolve into a top 1% CISO
Strategy, tools, and tactics to help you become a better security leader
Found this interesting?
Share it with your friends
Get a wingman for
your next audit.
Schedule a personalized demo and scale business

Sprinto: Your growth superpower
Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.


