Rated #1 Access Management Software
Access that’s easy to track, for any tech stack
Simplify and automate critical systems access reviews at scale. Sprinto helps you implement zero-trust security that is compliant with your preferred security frameworks. Ensure robust safeguards through adaptive access policies, flexible review mechanisms, and real-time access visibility—all in one interface!
Automate critical system access
Continuously track controls

Manage access lifecycle
Critical systems supported
and more…
NIST CSF
NIST SP 800-53
CMMC
CCPA
PIPEDA
ISO 27017
ISO 27701
FedRamp
CSA Star
CIS
FCRA
OFDSS
Compliance should not cost convenience
Manual access management methods are time-consuming, costly, and prone to human oversight. To ensure business-as-usual and enable productivity, it is tempting to prioritize convenience over compliance. However, this compromise opens the door to heightened risks, major security vulnerabilities, and potential audit failure.
Sprinto: Where smooth operations and complete compliance intersect
Sprinto helps you achieve a fine balance between safeguarding critical systems, enabling frictionless access, and maintaining compliance. It automatically maps users to critical systems and supports adaptive access policies based on dynamic factors like roles. It tracks changes to roles and notifies you of any anomalies. By ensuring visibility into users accessing critical systems and their impact on compliance, Sprinto provides a light yet responsive mechanism for critical system security and compliance.
Your needs and challenges

You want to protect critical infrastructure, without hindering access and business progress. You also need system safeguards to help you check various compliance criteria.

You want to eliminate the time cost, chaos, and errors that manual access reviews come with.

You want to build a robust, zero-trust practice around access. Without bogging down the team.
Our solution

Sprinto helps you set adaptive access policies based on dynamic, contextual factors like role, level of risk, and more. It automatically authenticates access as per set policies and the principle of least privilege, ensuring timely action.

Sprinto is an integrated system that seamlessly connects people, critical systems, and compliance. With responsive integrations, it efficiently handles access throughout an employee’s lifecycle—onboarding, transitions, and offboarding. Receive instant notifications of role changes for streamlined control and oversight.

Sprinto maintains an up to date inventory of user accounts and access level, and spots patterns of poor configuration automatically. It prompts remediation and helps you proactively check rules for valid access across critical systems. With Sprinto, you can see behavior anomalies related to access from a mile away.
Your needs and challenges
Our solution

You want to protect critical infrastructure, without hindering access and business progress. You also need system safeguards to help you check various compliance criteria.

Sprinto helps you set adaptive access policies based on dynamic, contextual factors like role, level of risk, and more. It automatically authenticates access as per set policies and the principle of least privilege, ensuring timely action.

You want to eliminate the time cost, chaos, and errors that manual access reviews come with.

Sprinto is an integrated system that seamlessly connects people, critical systems, and compliance. With responsive integrations, it efficiently handles access throughout an employee’s lifecycle—onboarding, transitions, and offboarding. Receive instant notifications of role changes for streamlined control and oversight.

You want to build a robust, zero-trust practice around access. Without bogging down the team.

Sprinto maintains an up to date inventory of user accounts and access level, and spots patterns of poor configuration automatically. It prompts remediation and helps you proactively check rules for valid access across critical systems. With Sprinto, you can see behavior anomalies related to access from a mile away.
How Sprinto’s Access Review
module works
Sprinto helps you put access management into autopilot and gives you real-time access discovery and analytics. Build and manage the right access guardrails for your security and compliance goals.
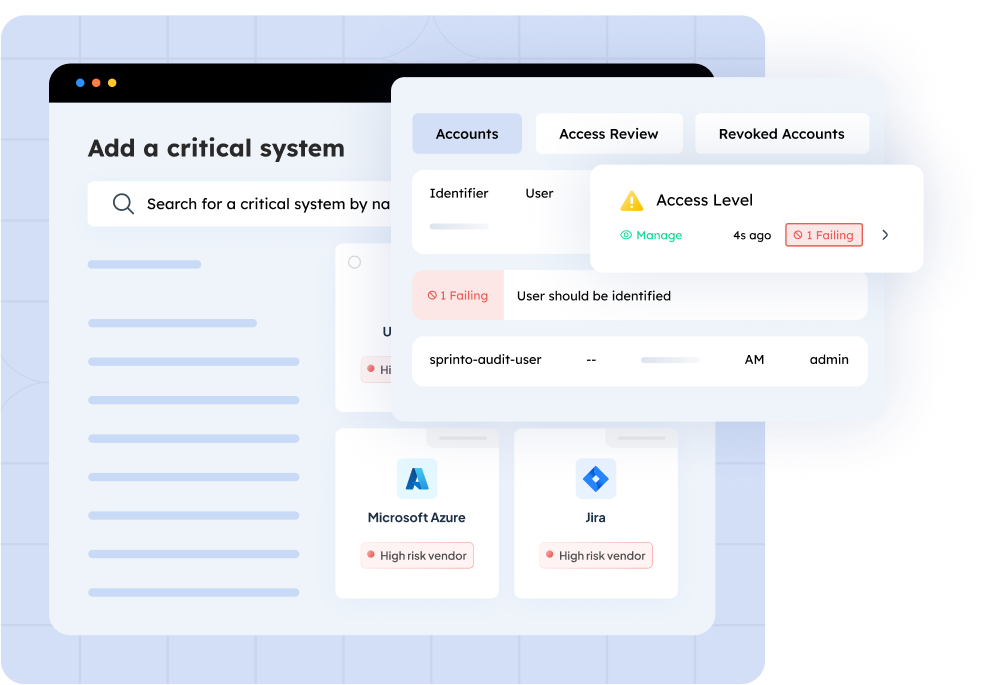
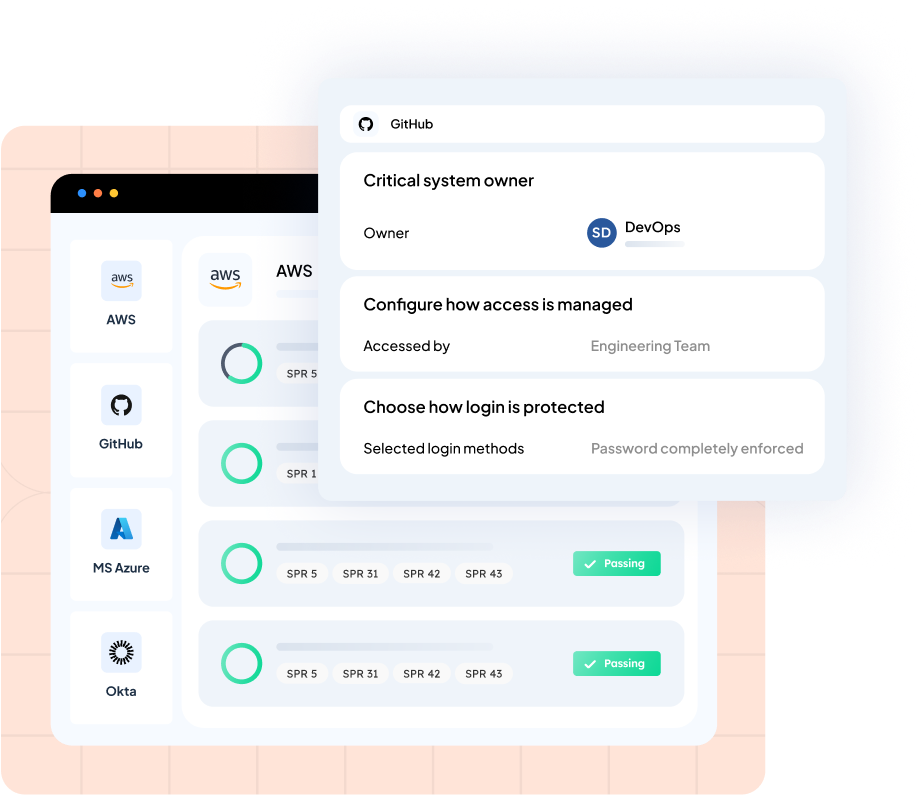
Configure
Choose critical systems from the Sprinto directory or add your own. Define access criteria and suitable login workflows as per your policies. Sprinto automatically maps critical infrastructure controls, policies, and various compliance criteria to underscores configuration gaps, making zero-trust security, access management, and compliance alignment easier.
Control
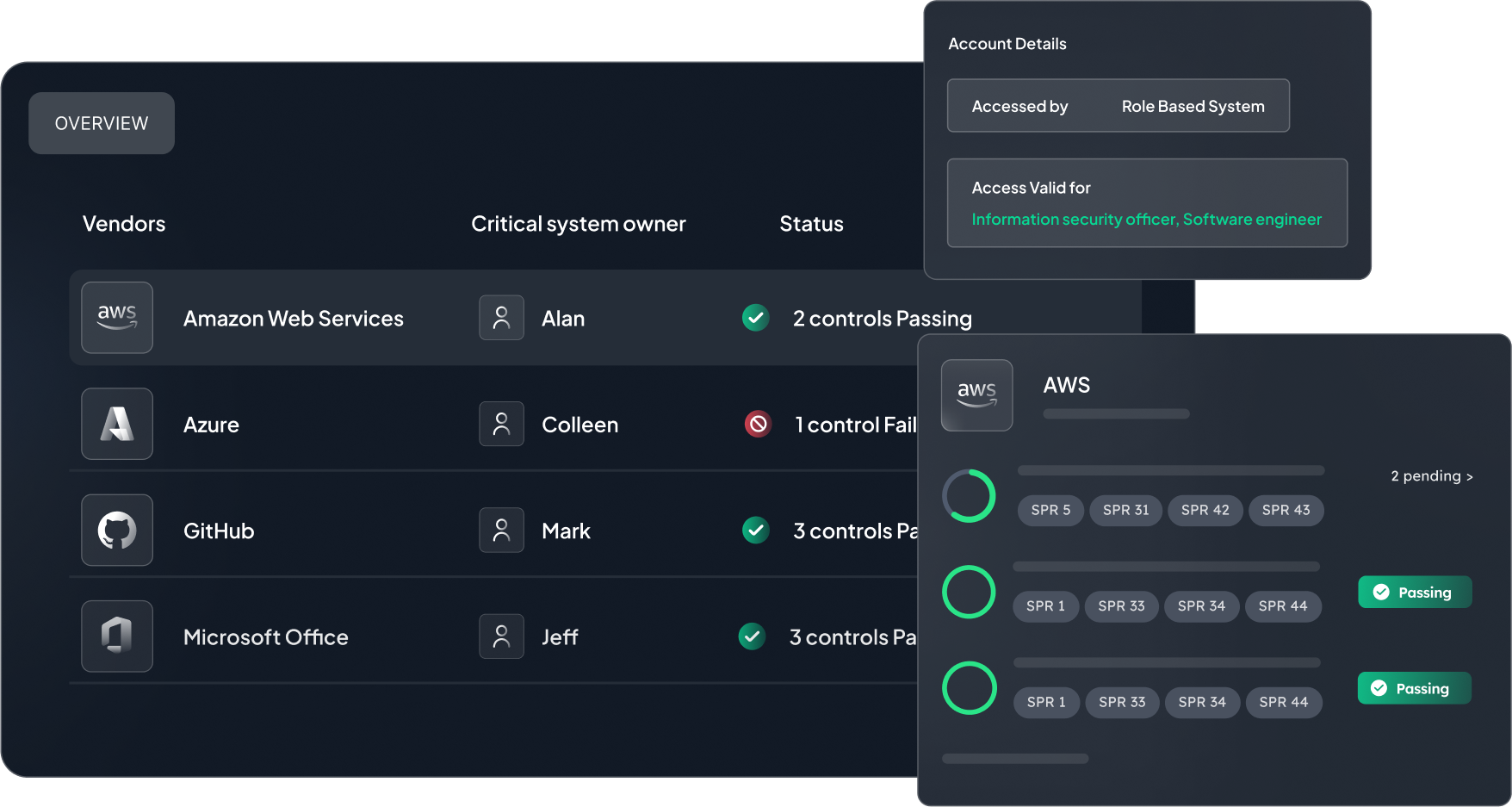
Manage and review access requests as you best see fit – Sprinto puts role-based and ticket-based access control at your fingertips. Delegate access management ownership of critical infrastructure to trusted members of your team. Track access-related controls to assess compliance in real-time. Tick all your access management checkboxes, from one place.
Check
Use Sprinto to monitor access control with automated and non-automated workflow checks. With continuous monitoring, you always have visibility into accounts, access status, ongoing checks, and upcoming actions, ensuring you never miss a cue to upload evidence or review an access query. Sprinto also logs evidence of your access control practices, making audits a breeze.

Sprinto: Your access control hub
use Sprinto to roll out powerful, compliant governance for your business, without unnecessary obstructions to daily workflows and accessibility.
Maximize infrastructure and minimize risk.




