SOC 2 Auditors and Service Providers
Vimal Mohan
Mar 19, 2024

Every business aiming to become SOC 2 (Service Organization Control) compliant must eventually engage with SOC 2 Auditors at the end of their SOC 2 audit readiness journey.
Having a credible Auditor review your compliance posture and align their attestation standards with the best practices you have in place is just as important as the audit readiness process itself.
Your efforts in selecting a SOC 2 Auditor should not end after considering reviews from a few business aggregator websites’ scores. You can use those reviews to filter out the good ones from the lot.
While genuine testimonials from users are not wrong, it is imperative to spend time understanding the Auditor and the organization types they typically work with.
Talk to the best SOC 2 Auditors you have on the list and get a hang of how they conduct their audits. Enquire if they have audited any other businesses similar to yours. What has their experience or examination been in auditing organizations with remote workforce?
Align these learnings with your organization/company to extrapolate a projection on your SOC 2 audit experience with them.
When and how to use SOC 2 auditors?
An Auditor is brought in the final stage of the compliance process. Before an Auditor gets involved in your SOC 2 journey, clearly define the audit scoping and understand and implement controls that are relevant.
For example, choose which of the five trust service categories apply to your organization and apply the controls required for the chosen ones.
Document all the policies, controls, and measures deployed within your organization. This enables you to seamlessly demonstrate to your Auditor how the deployed controls and measures meet the requirements for the chosen trust service criteria of SOC 2.
Before an Auditor begins the audit, perform a readiness assessment exercise. It gives you insights into any gaps in the system and organizational controls. Solving these gaps helps you go through the audit process with minimal non-conformities.
How do you select a SOC 2 auditor in 2023?
Choosing a SOC 2 Auditor can be a rather daunting task, especially when you’ve never done it before and are unsure what you want.
Here are a few things you should keep in mind when choosing an auditor for your SOC 2 audit:
AICPA Certified
The AICPA (American Institute of Certified Public Accountants) regulates the SOC audit process. When any organization undergoes an audit, they are audited by AICPA-approved
SOC 2 Auditors from licensed CPA firms or independent auditors.
Tip:
The Auditor should be AICPA certified.
The SOC 2 service Auditor should also have a specialization in information security. They usually have this, but it doesn’t hurt to check 🙂
Budget and Brand
CPAs who work independently charge less than ones from a CPA firm. It is a common misconception that since independent CPAs charge less, their work might not be on par with CPAs firms. Unfortunately, that’s not the case.
Unless you are an organization with enterprise-grade clients, you wouldn’t necessarily need an Auditor from the large CPAs (Deloitte, KPMG, EY) to stamp your audit report.
Tip:
Unless your customers specifically request an audit report from a CPA firm, or you notice a pattern in your line of work where a SOC 2 audit report from an independent Auditor is not considered, the idea of working with an independent Auditor is not worth dismissing.
Independent Auditors work faster, give their undivided attention (since they usually take on one client at a time), and are significantly cost-effective.
Experience
Working with a SOC 2 Auditors who have audited organizations similar to yours is always a huge plus. In the SOC 2 audit process, the Auditor often comes back asking for evidence for things like specific controls or asks you to show training acknowledgments.
This to-and-fro could become more complicated if the Auditor has never previously worked with organizations similar to yours. For instance, the complication could be profound if you are a fully remote organization.
So, conversing about their experiences and introducing them to your organization prevents a terrible audit experience.
Find out, what is SOC 2 bridge letter and its importance
Working with SOC 2 service providers
SOC 2 audit readiness platforms (also known as compliance automation platforms) and other software designed to help organizations become SOC 2 compliant can only go as far as assisting them to become audit ready.
There are a few exceptions where the audit readiness service providers are also AICPA certified. Hence, they conduct the audit too.
Working with compliance automation solutions is optional but going through the audit and working with the Auditor is mandatory to become SOC 2 certified.
Compliance automation platforms aim to smoothen your audit readiness journey. A few of them act as your liaison and communicate on your behalf with the SOC 2 Auditors to provide additional evidence for controls, policies, and measures if the need arises.
With compliance automation, businesses are now freed from the laborious and time-intensive activity of setting up appropriate controls, measuring the effectiveness of deployed controls, conducting gap analysis, conducting an audit readiness assessment, and providing additional evidence to the Auditor.
Compliance automation services automate repeatable technology-based requirements in SOC 2 compliance framework.
They enable businesses to channel their focus back to core business activities that contribute to revenue generation and business expansion instead of spending hundreds of hours on becoming SOC 2 compliant.
What is the process for going through a SOC 2 audit?
Every organization going through a SOC 2 audit will need to demonstrate their compliance with the requirements of the SOC 2 framework depending on the trust principles they’ve chosen for their business.
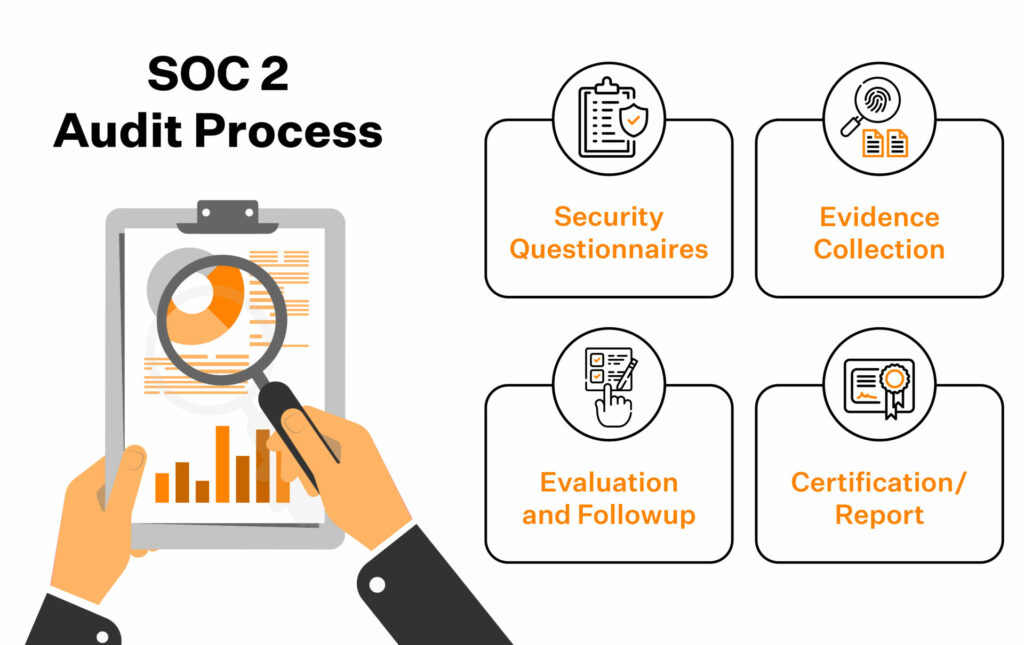
In SOC 2 audits, businesses are generally advised to expect these four things in their audit journey:
Security questionnaires
In the early stages of an audit, the Auditor sends a lengthy and exhaustive questionnaire asking for security controls to the organization.
They are asked to provide details on the trust principles applicable, a list of controls they’ve used, infrastructure in place, cloud security policies, people policies, security programs, and more.
Evidence collection
The organization is asked to provide evidence for all the controls they’ve deployed and evidence of optimum efficiency results of deployed controls. The Auditor then reviews this proof to make their assessment of how compliant the organization is.
Evaluation and followup
Suppose the Auditor feels that additional evidence is required to demonstrate compliance for any control(s). In that case, they ask the organization to provide more evidence.
When gaps in information security management are spotted, the audit process is paused until the organization remediates those gaps.
Certification/Report
For SOC 2 Type 1/Type 2, once the Auditor has completed the audit process, based on their assessment of your organization’s controls and policies, they write the report.
Recommended: How to get SOC 2 Type 2 certified
How do I prepare for a SOC 2 audit?
Based on the SOC 2 certification Type, the audit readiness journey varies. For example, for SOC 2 Type 2, the audit preparedness time generally ranges from six days to a few months depending on the organization’s size and business model.
Before starting the SOC 2 audit, it is a good practice to ensure that your organization has implemented all the controls and policies required by SOC 2 for the chosen trust principles.
Conducting an audit readiness assessment allows you to analyze the current security compliance posture and identify gaps that require remediation.
It is also a good practice to map control and their respective evidence to ensure that the Auditor is presented with data that is easy to consume.
Classifying your audit readiness implementations into two categories for easy identification and classification is advisable:
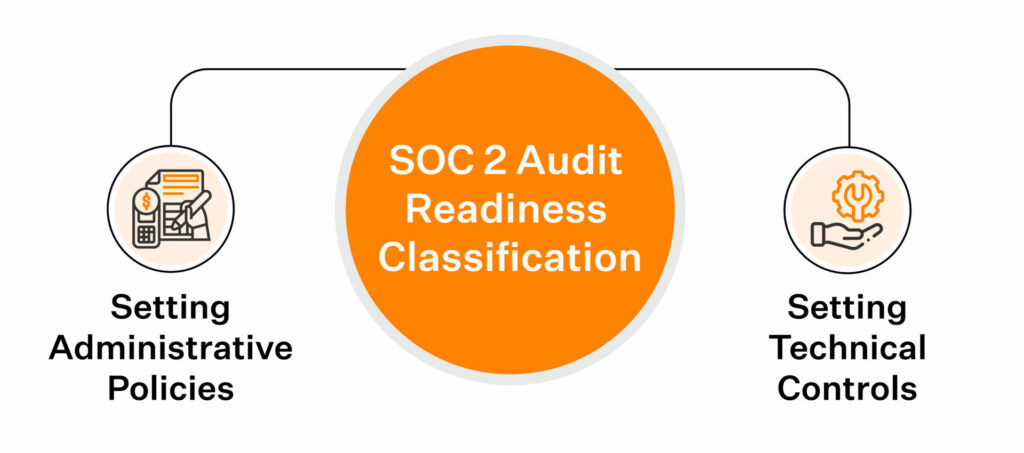
Setting administrative policies
Your organization’s policies should be centred around SOC 2’s key security principles and internal controls for disaster recovery, audit logging, employee training, onboarding and offboarding, and system access activities
Setting technical controls
Deploy controls around your organization’s cyber security information, encryption, access control, vulnerability scanning, threat detection, intrusion detection, penetration testing, firewalls, and network rules, among others.
Classifying the controls and policies helps systemically check if a strong compliance posture is successfully demonstrated. This then helps you identify the active requirements and controls that are actively contributing to the posture and list the dormant ones and fix those gaps.
Also read: Benefits of ISMS Implementation
Audit Experience with Sprinto
Let’s hear it from our clients!
How did we achieve this?

Sprinto is purpose-built to focus on two key objectives. The first objective focuses on automation to implement controls and policies to reduce the time taken to become audit ready from months to weeks.
The second focus is on automating the evidence-collection process to align with the practices and methods of SOC 2 service Auditors.
This allowed us to present evidence in a way that is easy to consume for the Auditor, thus eliminating the to-and-fro between Auditors and organizations.
This helped us reduce the average time Auditors took to complete the audit from months to days.
Speak to an expert from Sprinto to see how we can make your SOC 2 journey a breeze.
Vimal Mohan
Vimal is a Content Lead at Sprinto who masterfully simplifies the world of compliance for every day folks. When not decoding complex framework requirements and compliance speak, you can find him at the local MMA dojo, exploring trails on his cycle, or hiking. He blends regulatory wisdom with an adventurous spirit, navigating both worlds with effortless expertise
Grow fearless, evolve into a top 1% CISO
Strategy, tools, and tactics to help you become a better security leader
Found this interesting?
Share it with your friends
Get a wingman for
your next audit.
Schedule a personalized demo and scale business

Sprinto: Your growth superpower
Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.



