7 Benefits of ISMS Implementation
Meeba Gracy
Mar 25, 2024

Is securing your business’s data and information security in today’s ever-evolving digital threat landscape keeping you up at night?
An effective way to get started is by implementing an Information Security Management System (ISMS). ISMS are global standards for handling security for data collected, presenting a structured approach for managing activities related to the organization’s security assurance.
Here we’ll review all that goes into a successful ISMS implementation, from protecting customer data with strong cybersecurity measures to ensuring smooth workflows.
Why do companies need ISMS?
A good ISMS is vital for organizations today. It can provide a much-needed overview of where things stand regarding information security and the tools to make sure it remains strong. Picture an organization’s data as a castle, encompassed by thick walls that protect its valuable content from unwanted intrusions.
With an ISMS, these walls are made stronger. An ISMS helps implement periodic checks to ensure everything is secure and up-to-date with your security measures.
The gates allow only those who are cleared by the stringent criteria to pass through while alerting you simultaneously if there’s suspicious activity in your perimeter. That way, information inside the castle stays safe at all times. This is why the importance of ISMS should not be taken lightly.
Elevate your ISMS with Sprinto’s continuous compliance
Now, let’s dive into the benefits of this exciting framework below.
7 Important Benefits of ISMS (Information security management system)
The benefit of an ISMS is that it is designed to fortify your business against cyber threats by establishing controls that minimize the risk of an attack. You also need to have a plan ready in case one should arise.
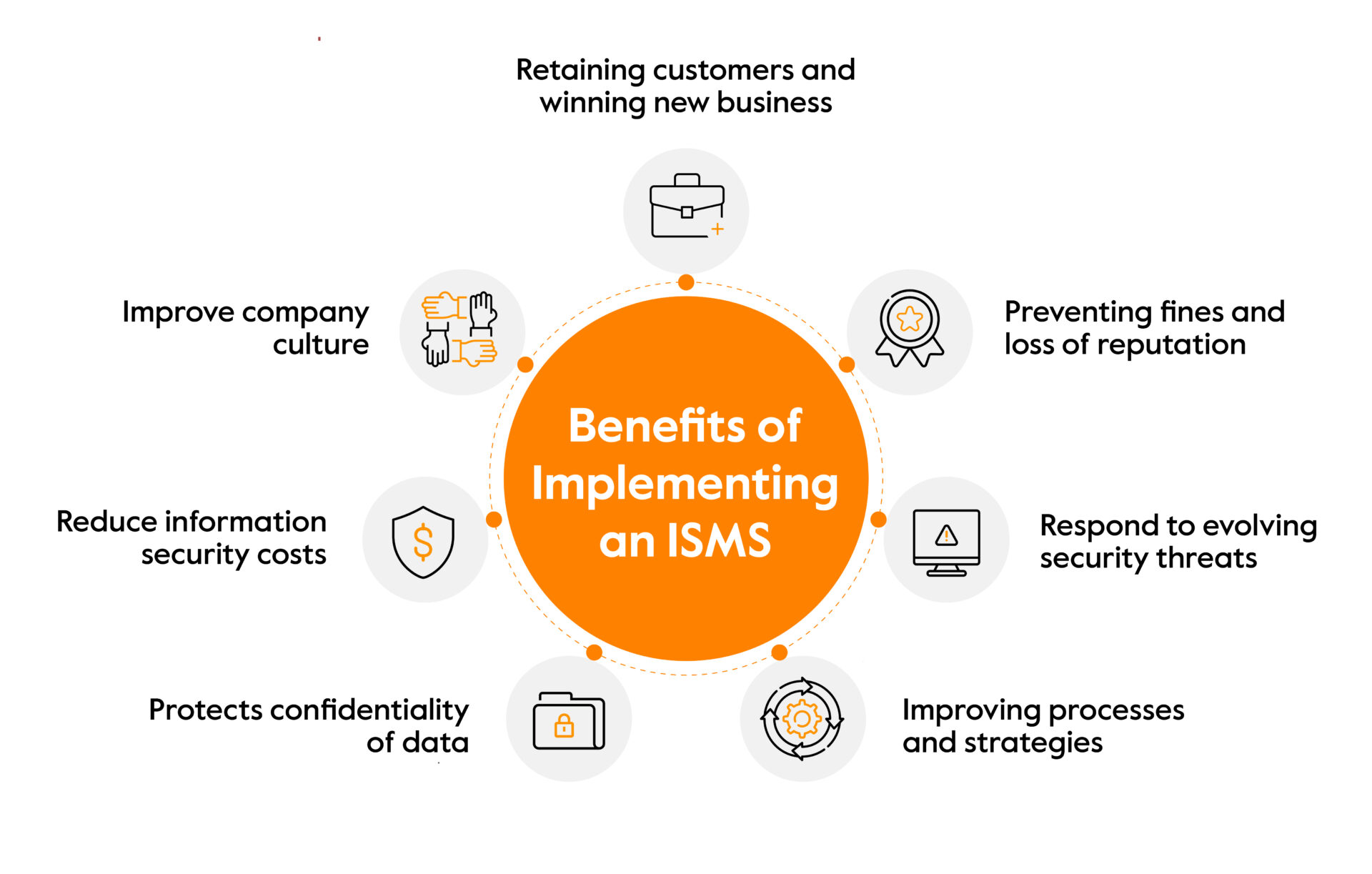
Here are some of the important ISMS benefits you need to know:
Retaining customers and winning new business
Implementing an ISMS can be a wise investment with new customers since providing proof of a high standard of data privacy and secure handling techniques can be the decisive factor in winning over powerful stakeholders.
Until the recent past, it for granted that organizations would innocuously manage their data with the highest levels of privacy and security, but now everyone has their doubts.
For example, customers today seek organizations that prioritize their needs and demonstrate ISO compliance.
Gaining an ISO 27001 certification adds value to your organization. It signals your commitment to robust security practices, thus boosting customer relationships and empowering you within the competitive market.
For most of our customers in Sprinto, attaining ISO 27001 certification is necessary to meet their client needs and acquire new clients.
Preventing fines and loss of reputation
As budgets tighten and data breaches and cybercrime continue to increase, business owners across the globe need a way to protect themselves from data loss and avoid huge fines associated with non-compliance (HIPAA and GDPR).
ISMS establishes protocols that allow businesses to develop their internal security – reduce intrusions, increase security measures as required, and minimize the potential effects of any future breach.
For example, the EU’s General Data Protection Regulation (GDPR) has enabled the Information Commissioner’s Office (ICO) in the UK to take severe action against data protection violations by imposing penalties of up to €20 million or 4% of a company’s annual turnover, whichever is greater.
Implementing an ISMS is one important tool for protecting sensitive customer information while simultaneously avoiding those potentially catastrophic fines.
It’s estimated that since GDPR came into play in the EU, over 60 million euros have been fined in data breach-related cases. While larger companies are certainly not immune – take British Airways and Marriott, for example – even smaller businesses can expect sizable fines when falling foul of the ICOs regulations.
No matter the size of the fine inflicted on an organization; it can still cause long-term damage to its credibility and reputation in the market. This is not just limited to the short-term financial losses incurred either; such blemishes on an organization’s record may well reduce customer trust, even if they were unaware of the issues that put them under investigation in the first place.
Focusing on information security solutions is important regardless of the size of your business. This is because even minor infringements could later have disastrous consequences for their operations. Mistakes like these are often broadcasted across the news and online forums, so you must do whatever it takes to stay safe from hefty fines and reputational harm.
Enhance security by automating Threat Detection & Remediation
Respond to evolving security threats
The dangers posed to organizations are ever-evolving and highly sophisticated. It can seem overwhelming for businesses to respond to these threats in a way that remains effective over time.
That’s why having an ISMS is so essential. It helps your business anticipate future needs, create strategies that address external and internal security threats, and evolve with the changing environment.
With its proactive approach, an ISMS proactively mitigates the risk of an incident while protecting precious data and systems. Businesses need to be constantly secure and compliant to defend themselves against today’s sophisticated attack vectors and adapt their strategies for tomorrow’s risks.
An effective ISMS can face off against any new security threats and threats from inside so that organizations are always one step ahead and never caught off guard.
Achieve Always-on compliance with Sprinto and minimize incidents
Improving processes and strategies
With ISMS, everyday processes, internal systems, and structures become much smoother and more secure. By implementing a strong ISMS structure following the Annex A.12 framework, procedures such as change management, capacity management, development and testing, and more are standardized, which helps to build trust within an organization and with partners.
And, of course, these changes also provide your organization with a healthy layer of DRM (Digital Rights Management) that helps keep your data safe in-house.
By improving processes and strategies, your company has the opportunity to become better secure and protect itself from potential attacks. ISO 27001 standardization provides organizations with a landscape that outlines clear policies that all staff members should adopt.
These policies encompass everything from using external drives safely and safely browsing to requiring solid passwords for accounts and systems. With processes in place, the effectiveness of safety protocols increases, thus helping build a more reliable security system.
Protects confidentiality of data

Securing confidential data is a huge responsibility. That’s why ISMS exists – to provide a complete framework for protecting data and ensuring its privacy. Activities like encryption, access management, visibility and control of sensitive information, and even policies regarding paper documents and other physical media are handled by the ISMS.
This helps ensure all relevant personnel has the necessary permissions to fulfill their duties without exposing sensitive material to those who don’t have access. Furthermore, over time various policies, procedures, and technical/physical controls get adjusted and improved to protect confidential data from any threats.
This way, an ISMS provides a comprehensive solution to protect your data with every possible assurance that privacy will be maintained throughout its duration!
Reduce information security costs
A wise man once said that the best way to spend money is to invest it into something more effective than originally planned. This mantra can be applied to information security costs too.
By implementing ISMS, you can approach spending on security measures with logic and reason. Rather than trying to protect every unknown by investing in costly technologies, an ISMS allows for risk assessment and analysis so that only necessary security measures are used.
This ensures that costs don’t stack up – both financially and resource-wise – while securing from potential breaches.
Improve company culture
Creating and maintaining a healthy company culture is essential for long-term success. It can seem like a heavy burden, but taking steps to improve the environment of your workplace can make all the difference.
The Standard’s approach helps ensure everyone in the organization remains aware of potential risks while also understanding why security controls are necessary, making it easier for employees to implement them as part of their ongoing responsibilities.
There’s no one-size-fits-all solution, but by taking an integrated approach covering all aspects of the business, everyone can be empowered to do their job more effectively while contributing to a secure work environment.
Get Started With Your ISMS With Sprinto
Understanding the risks and threats posed upon your information systems is essential to take measurable and effective action. However, as all businesses know, this process can take an immense amount of time since it is traditionally done manually – pouring over documents and going through data.
That’s why, today, automated solutions like Sprinto are invaluable. Sprinto provides a comprehensive answer to your organization’s compliance requirements by streamlining the entire process – from policy creation to mapping security controls and analyzing potential security gaps.
Join Sprinto’s 450+ satisfied compliance conquerors
Moreover, Sprinto ensures everyone within the company stays safe with its in-built staff security training and tracking feature that educates people on the latest best practices in terms of cybersecurity.
Trying things out for yourself? Book a demo with Sprinto today – the first step towards smarter compliance!
FAQs
What is ISMS and its importance?
ISMS stands for Information Security Management System. It’s a framework for identifying, assessing, and managing information security risks. It provides a structure for implementing and managing security controls to protect your organization’s information.
What are ISMS principles?
Organizations must craft and maintain a cohesive set of policies, processes, and systems to deftly manage potential risks to ensure the utmost security of information assets. This approach will guarantee an acceptable level of protection for their treasured asset – data.
Who is responsible for ISMS?
Stakeholders, managers and IT personnel form an ISMS team. Tasked with transforming their organization into a paragon of data security excellence, the team designs processes in line with ISO 27001 international standards. This drive for knowledge protection allows every network member to rest easy, knowing that information safeguarding is at its peak performance.
Meeba Gracy
Meeba, an ISC2-certified cybersecurity specialist, passionately decodes and delivers impactful content on compliance and complex digital security matters. Adept at transforming intricate concepts into accessible insights, she’s committed to enlightening readers. Off the clock, she can be found with her nose in the latest thriller novel or exploring new haunts in the city.
Grow fearless, evolve into a top 1% CISO
Strategy, tools, and tactics to help you become a better security leader
Found this interesting?
Share it with your friends
Get a wingman for
your next audit.
Schedule a personalized demo and scale business

Sprinto: Your growth superpower
Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.


