How to Get ISO 27001 For Startups (Free Guide)
Anwita
Jan 29, 2024

ISO 27001 is not an easy framework to understand, especially for startups new to compliance. It is not quite straightforward and does not provide checklists and examples to make your job easy. But without ISO 27001, startups lose out on a ton of growth opportunities.
To address this, we’ve drafted this article to bridge the gap and offer directional guidance on the next steps. In this article, you will learn about the steps involved in becoming ISO 27001 compliant as a startup and its associated costs.
What type of startup needs to be ISO 27001 certified?
First things first, ISO is not compulsory. The compliance policy (if there was one) won’t come knocking on your doors if you don’t have one. However, it is becoming increasingly common for businesses to prioritize security as one of the criteria to partner with other service organizations.
Having said that, you should consider ISO 27001 if:
- Your business collects, stores, processes, transmits, or has access to sensitive customer data.
- You conduct business mainly outside the North American region.
- Your business’s global presence would benefit from an internationally recognized certification.
No matter what the type of industry and service you offer, you can be ISO certified. The chart below shows the number of ISO certifications in 2021 by industry.
How to get ISO 27001 certified as a startup?
Depending upon the industry you cater to, each startup has its unique compliance needs. The process of acquiring certification is multifaceted and depends on the measures that you have already implemented to adhere to ISO 27001 and the work still required to be done. Once the ISMS is ready you can proceed with an informal assessment followed by a 2-phased audit process.
Here is the list of nine steps to get ISO 27001 certified as a startup :
Build your team
Before starting an extensive project, figuring out who takes care of what is crucial. ISO 27001 comprises a lengthy list of granular requirements, so assigning accountability for each task is a good practice. Ideally, these roles would include:
Upper management – Usually includes CEO, COO, CISO, or other roles who would be actively participating in this process (This usually depends on the organization). They are responsible to align information security with the company goals, manage resource allocation, and overseeing delivery.
Information security steering committee – Security decisions can be quite challenging for organizations with no existing structure for infosec management. Nevertheless, it is important to chalk out strategies with stakeholders and top decision makers from each department.
Information security steering committee deals with a plethora of issues: process approval, risks analysis, audit results, security strategy monitoring, security goals, performance indicators, disaster recovery plan, and more.
Chief information security officer – CISOs help to reduce interdepartmental chaos and improve coordination. You don’t necessarily need to hire someone for this role – anyone with a thorough knowledge of information flow should suffice.
CISOs engage with departmental heads to finalize security strategies, align business goals with security objectives, decide budget, set policies and processes, identify best options to mitigate risks, and monitor security activities. Additionally, they may conduct training and security awareness programs.
Some organizations assign the role of a system administrator to process data, make workflow changes, and be in charge of security controls.
Understand data protection requirements
Now that you have the roles sorted, it’s time to figure out which data and assets need securing. One way to figure this out is by using the top-down approach. You can use this data flow chart for reference.
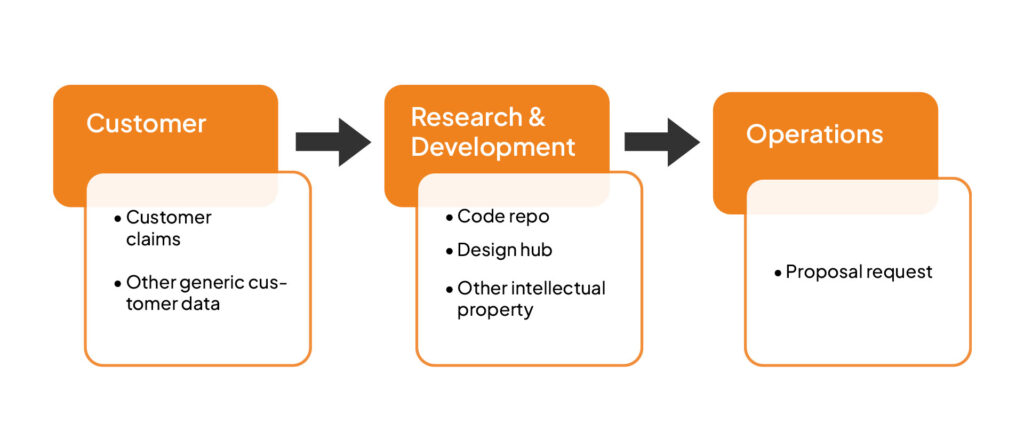
In order to execute this process seamlessly, you should have clarity on each process and its type, who is responsible for what, and operational workflows. This helps to gain insight into the link between assets and activities.
System administrators have a comprehensive understanding of this and can help others too.
Another way to approach this is by the bottom-up method. This is an ideal choice if you don’t sufficiently understand the processes. The bottom-up approach relies on your ability to understand the type of information your organization handles throughout its end to end process.
For example, you may consider sensitive and non-sensitive personal data, enterprise data, design data, and more. Once you have the asset map ready, use it to know your data on a conceptual level.
Apart from electronic data, physical data storage facilities should be identified to secure them. You can use the bottom-up technique to identify physical assets like paper documents, endpoint devices, hard drives, physical offices, and even employees. After identifying these assets, list them in categories. For example, CRM solutions and other tools can fall under software. Servers, laptops, and smartphones can go under hardware. Third-party providers like cloud hosting solutions or TLC providers.
Once you are done cataloging, use an excel sheet to track how information is connected to assets. Use the sheet below for convenience and keep it updated.
Download your Information Value Tracking Sheet
Evaluate risks
The saying “know your enemies to defeat them” holds true for ISO – know your threats to mitigate them. A comprehensive insight into the existing and potential risks throughout your infrastructure is a crucial step towards ISO 27001 for startups. Knowing risks helps to prioritize them, implement appropriate controls, investigate breaches effectively and contain them.
The first step to your risk assessment is to know the level of risk. Use the asset flow map above to assign a value to each. A simple way to execute this is by assigning security based values like availability, integrity, and confidentiality. Use the table below to figure out where each stands.
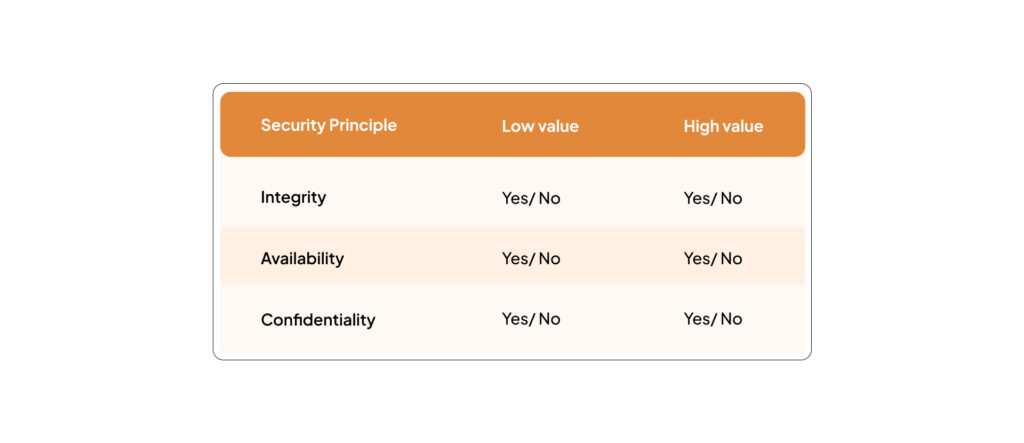
Using the table above can result in the example shown below
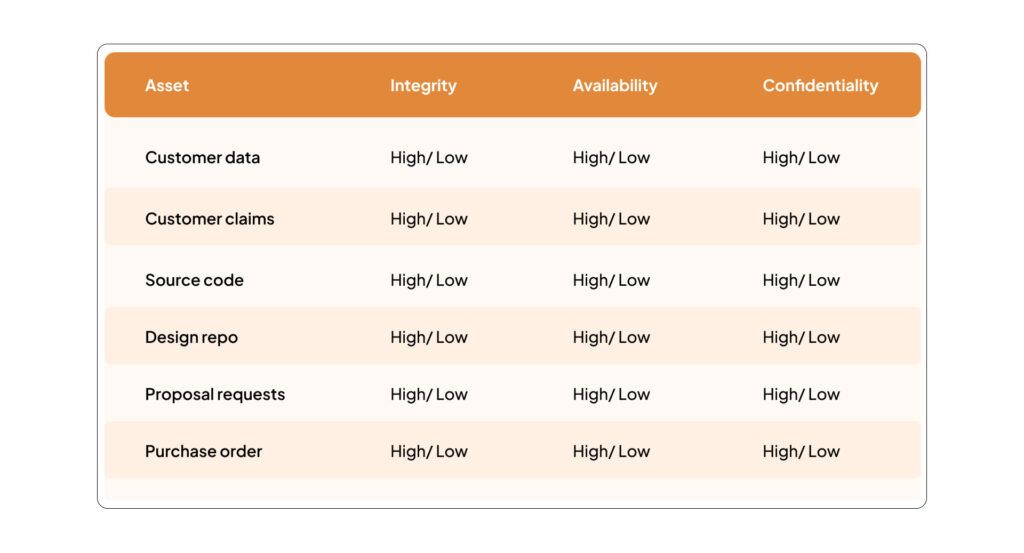
Since all other assets have their main values related to the information they store, process or transmit, this first evaluation can be inherited by all assets connected with the evaluated information in the asset map. This assumes that their relationship with the highest evaluated information gives them their true value for the organization, as shown below.
The relationship with the highest evaluated information shows the actual value, as you can see in the downloadable sheet below.
Download your Information Asset and Tracking Sheet
Evaluate context to prioritize risks
Here, you need to understand your organization’s environment better. It will be required to define your information security requirements. To simplify this step, you could align your model with the EU Agency for Network and Information Security (ENISA) threat model.
| Threat category | Examples |
| Disaster | Earthquake, fire, flood, |
| Outage | Power shortage, service unavailability |
| Physical threats | Theft or sabotage |
| Legal | Violation of regulation or inability to follow law |
| Unintended damage | Device loss, unintentional disclosure of information |
| Malfunctioning | Hardware failure, technical glitches, device malfunctions |
| External data threat | Ransomware, trojans, zero day attack, social engineering |
| Internal data threat | Eavesdropping, espionage, man in the middle |
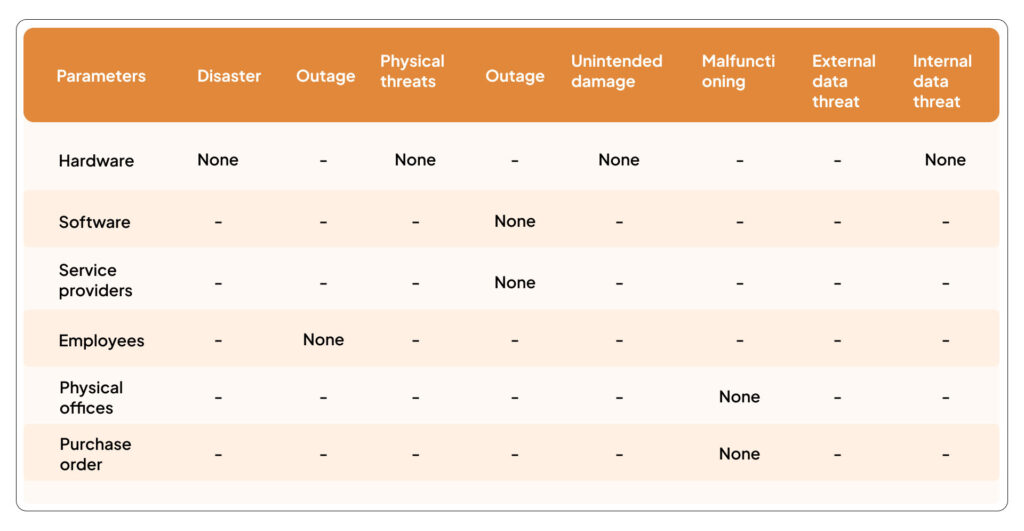
Use historical data and employee expertise to evaluate the level of threat for each of the threats in the table above. Now try to evaluate how prone your assets are to these threats using a questionnaire. For example, How prone is your office location to floods? How trustworthy are your employees? Or, Are there any gaps to compliance within the business?
You can use a rating system to answer these questions – like High, Medium, Low, and None.
Use the table below to quantify the level of risk. Assets that are not marked as “none” should be considered a potential risk.
Identify controls for ISMS
Annex A of ISO 27001 document is about security controls. These are simply measures and processes you implement to protect data from threats. It has a list of 114 controls, but not all are compulsory. You can choose the ones partially or fully applicable to you.
Once you have an idea of risks and assets, you can proceed to the next step – plan how to address the risks, a budget, and timeline. System administrators, steering committee, and system processing officers are ideally involved for this task.
The decision making process for which control to implement in a given environment is easier said than done. For many organizations, this turns out to be a tedious process that is a combination of trial and error as well as permutation combination. The outcomes are almost always difficult to project and end up stretching the budget. Depending on the type of data, your team can make a call on which controls are required and which can be passed for the time being.
Check out: List of ISO 27001 controls and clauses
Conduct frequent internal audits
Periodic assessments are crucial to measure your progress as per the plan. Security administrators monitor this regularly; monthly or quarterly. This involves all the concerned members of the team – their input regarding updates, new requirements, changes, roadblocks, and more is to be reported. Even for minor changes, keep the top management in the loop.
A good practice that helps to stick to the plan is through audits. Auditors are independent bodies who check your described controls against what is implemented and create a report based on their observations. Audits can be conducted by internal staff but should not be biased.
The report must list the areas of non-compliance and improvement. You should adequately address any gaps in compliance with corrective action to avoid issues in the future. Wherever you make changes, document it in your plan.
Monitor to ensure ISMS effectiveness
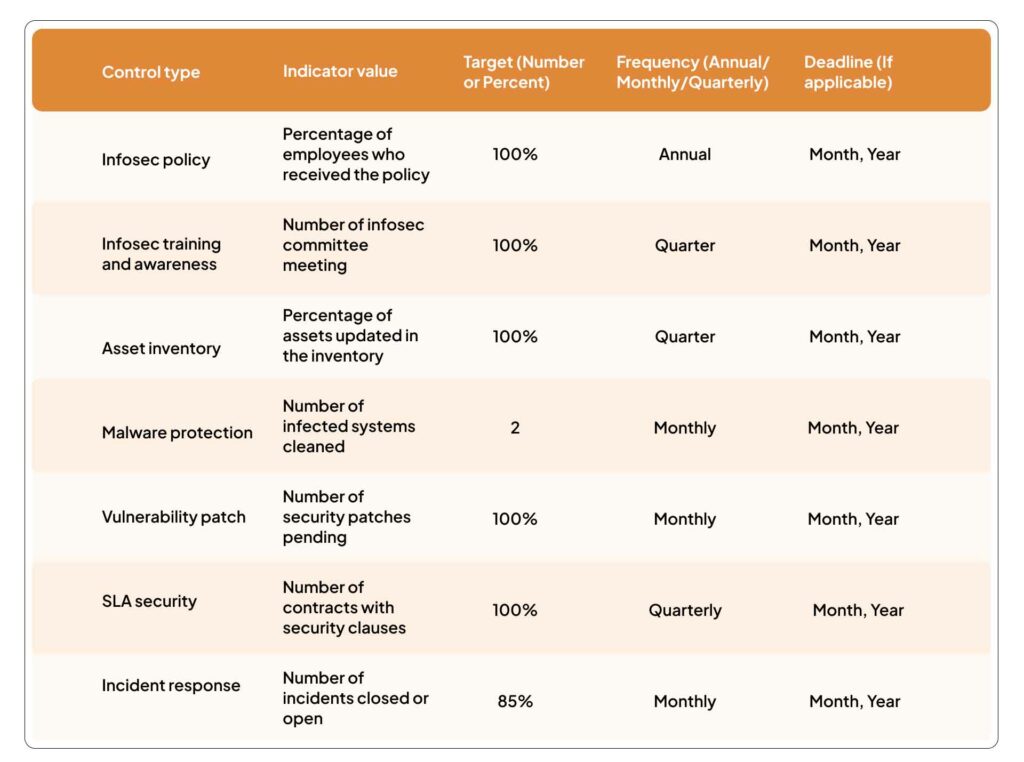
Continuously monitor activities to ensure that your ISMS is working as planned. Address and document gaps as and when required. A good practice to efficiently monitor is by using performance indicators – codes set up to trigger a notification when a breach or unauthorized action is detected. Additionally, you can use goal indicators to measure your business objectives.
Use the suggested table below to measure performance in percentile values. Indicators vary from one organization to another.
External audits
Once you are done with internal processes, it’s time for an external audit (Stage 1). An ISO 27001 accredited auditor reviews your documents against the standards requirements. After reviewing and assessing your organization’s ISMS, they will provide an audit report which contains your certification.
After the stage 1 audit, you should go through the main or stage 2 audit. In this round, you basically demonstrate that your controls are functioning as per ISO requirements. The auditor reviews if you have implemented the corrective actions or improvements suggested in the first round.
Stage 2 audit also ends with a report detailing minor non conformities, and suggests areas for improvement. In case of major issues, you need to take corrective actions and share the evidence of the same with your auditor.
Here is a quick guide to ISO 27001 audit checklist
Continuous improvement
ISO 27001 compliance for startups is not a one time activity. Your job does not end with certification. As threats continue to evolve and malicious actors gain access to better technology, keeping your system a step ahead of vulnerabilities is crucial.
For example, when you partner with new vendors, integrate new tools, employ more people, or make changes in your process, it changes the nature of risks. This means security issues will keep piling up – unless you perform risk assessments and continuously deploy measures to address them.
Note:
ISO 27001 has not officially released a unique compliance subset for startups. However, using the above-mentioned best practices and structured approach, you can easily kickstart your journey.
Sprinto can help you fast-track the ISO 27001 certification process with it’s adaptive automation capabilities. It has in-built policy templates, training modules, automated evidence collection and much more to streamline the compliance journey. Read how Sprinto enabled Capptions to achieve ISO 27001 3X faster than an ISO consultant.
Also find out: How ISO 27001 can be automated
What does ISO 27001 certification cost to startups?
ISO 27001 certification can cost you anywhere from $10000-$50000 depending on a number of factors. These can include the scope of certification, the current security maturity of the organization, the level of support required and more. Furthermore, there are multiple ways to become ISO compliant. These include using an internal team, via an external consultant, using a Governance, Risk Management, and Compliance (GRC) tool, or compliance automation tool.
- Internal Team: Will cost you time and productivity. It can take up to at least five months.
- External consultant: Cost estimates up to $10,000+. Can take a minimum of five months.
- GRC: Costs an average of $7,500.
- Compliance automation: Costs about $8,000. Takes around two weeks.
There are additional preparation costs to be considered as given in the table below.
| Requirement | Cost estimation |
| Official standard document cost | $350 |
| Gap analysis | $7500 |
| Penetration tests | $5000 and $20000 |
| Vulnerability assessment | $2000 and $2500. |
| Employee training | $25 per user |
| Anti-malware tools | $50 annually |
Also check out: ISO 27001 requirements checklist
How does ISO 27001 benefit startups?
Startups and small businesses often look at ISO 27001 certification as a regulatory requirement to fulfil or because their customers ask for it. But the certification has several benefits to offer and improves the overall security posture of startups.
Check out these benefits of ISO 27001 for startups:
Consistent approach to information security
ISO 27001 is a control-heavy standard. Most organizations rely on security controls to protect their data but fail to implement them efficiently—poor coordination among controls implemented as independent solutions. ISMS offers a systematic solution that answers this problem and provides a consistent approach to managing information security.
Asset protection
Security controls often fail to secure non-IT assets that contain data such as paper documents, physical office locations, hard drives, and more. ISO 27001 guides organizations to secure every type of asset from data theft or damage.
Minimization of data breaches
As a small business, you are more likely to face a breach when compared to medium to large organizations. This is because large companies have the budget to spend on security while the smaller ones don’t—a fact that malicious actors know and exploit to their advantage. Not to mention that data breaches are costly. A study by Ponemon Institute shows that more than 83% of organizations faced more than one breach. It is therefore important for startups to build resilience.
Cost savings
As a startup, you cannot afford to shell out on corrective measures. It is cheaper to implement security compliance like ISO than to spend on corrective actions, at least in the long run. Not to mention that you would want your employees to focus on their tasks and growth opportunities rather than waste productive hours on damage control.
Competitive advantage
With startups mushrooming everywhere, investors are no longer cutting checks to clean up after messy situations which could have been avoided in the first place. ISO 27001 is an easy way to gain trust and demonstrate the efficiency of information security practices. Startups with ISO 27001 certification certainly have more chances of unlocking an enterprise deal.
The easy path to ISO 27001 compliance
Challenges of ISO 27001 faced by startups
Early-stage startups need to do a lot of preliminary work for ISO 27001 implementation. Leadership teams play a crucial role in fostering a culture of collaboration and ensuring alignment with security objectives to overcome the complexities.
Here are the top challenges faced by startups when implementing ISO 27001:
Understanding framework guidelines
ISO 27001 is a complex and detailed standard that does not directly specify which organization should implement what controls. Every organization must select and implement the relevant controls based on its risk profile and information security requirements. Startups lack awareness on many of these aspects and find it difficult to interpret the application of standard.
Resource constraints
Startups face a number of challenges from a human resources, budget, and time angle. More often than not, one person handles multiple roles in the organization and there is limited bandwidth and expertise to dedicate efforts towards ISMS implementation.
Stakeholder resistance
ISO 27001 implementation for startups requires a cultural change. Several new policies are created and the old ones are updated or scrapped. The procedural changes often find resistance from stakeholders and without complete buy-in, the execution becomes difficult.
Documentation challenges
ISO 27001 has extensive documentation requirements. Several mandatory documents and records need to be maintained to demonstrate strong practices towards the protection of information security. As startups have limited experience with documentation processes, they often find it overwhelming.
Process gaps for ongoing monitoring
The framework thrives on the creation and maintenance of a robust ISMS which requires a continuous monitoring mechanism. Startups usually do not have well-established processes for 24/7 monitoring because of cost and time considerations. Because of this, there can be visibility issues and gaps in implementation.
Expedite ISO 27001 certification with Sprinto
ISO 27001 does not lay down specific controls to implement and is rather a framework that must be interpreted as per business requirements. As a startup with limited resources and expertise, it can be challenging to dedicate a team for ISO 27001 interpretation and implementation. That is where compliance automation tools like Sprinto play their part.
Sprinto makes it easy to get ISO 27001 certification for startups by identifying compliance gaps and establishing ISMS scope. It enables you to build a tightly integrated pipeline of controls and run automated checks to initiate corrective actions on time. The entire implementation is managed through a centralized dashboard and you can engage with an accredited Sprinto auditor to expedite the certification process.Have more questions about ISO 27001 for startups? Talk to a compliance expert today.
FAQs
Should I get ISO 27001 or SOC 2?
ISO 27001 is a globally accepted standard and a more comprehensive framework for information security. SOC 2 is industry-specific and is more relevant for technological businesses or cloud companies that need to secure customer data. You must understand business and customer requirements before making this decision. Several businesses opt for both certifications.
What documentation is required for ISO 27001 for startups?
ISO 27001 mandates documents such as risk assessments, statements of applicability, inventory of assets, acceptable use of assets etc. You also need records for training, results of management review, internal audits and more. You can check the complete list here.
How long is ISO 27001 valid for startups?
ISO 27001 certification is valid for 3 years. However, there are surveillance audits during this period to ensure ongoing compliance.
Is ISO 27001 certification for startups worth it?
The short answer is yes. No organization, especially small to medium-sized ones is safe from breaches. ISO certification is your ticket to gain customer trust and ensure continued business growth.
Is ISO 27001 better than cyber essentials?
ISO 27001 is an internationally recognized standard for information security. It is much more comprehensive, intensive, and risk-focused.
Anwita
Anwita is a cybersecurity enthusiast and veteran blogger all rolled into one. Her love for everything cybersecurity started her journey into the world compliance. With multiple certifications on cybersecurity under her belt, she aims to simplify complex security related topics for all audiences. She loves to read nonfiction, listen to progressive rock, and watches sitcoms on the weekends.
Grow fearless, evolve into a top 1% CISO
Strategy, tools, and tactics to help you become a better security leader
Found this interesting?
Share it with your friends
Get a wingman for
your next audit.
Schedule a personalized demo and scale business

Sprinto: Your growth superpower
Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.



