SOC 2 Type 1 Vs Type 2 (A Detailed Comparison)
Meeba Gracy
Mar 16, 2024

Confused about which SOC 2 report type is right for your business: SOC 2 Type 1 vs Type 2? You’ve come to the right place.
This blog post will provide a comprehensive overview of the difference between SOC 2 type 2 and type 1, plus tips on choosing one that best fits your organization.
We’ll explore what each report means, how they measure up against each other in terms of security protocols, and more. Get ready to learn everything there’s to know about SOC 2 Type 1 vs Type 2 reports – let’s get started!
What is the difference between SOC 2 Type 1 vs Type 2
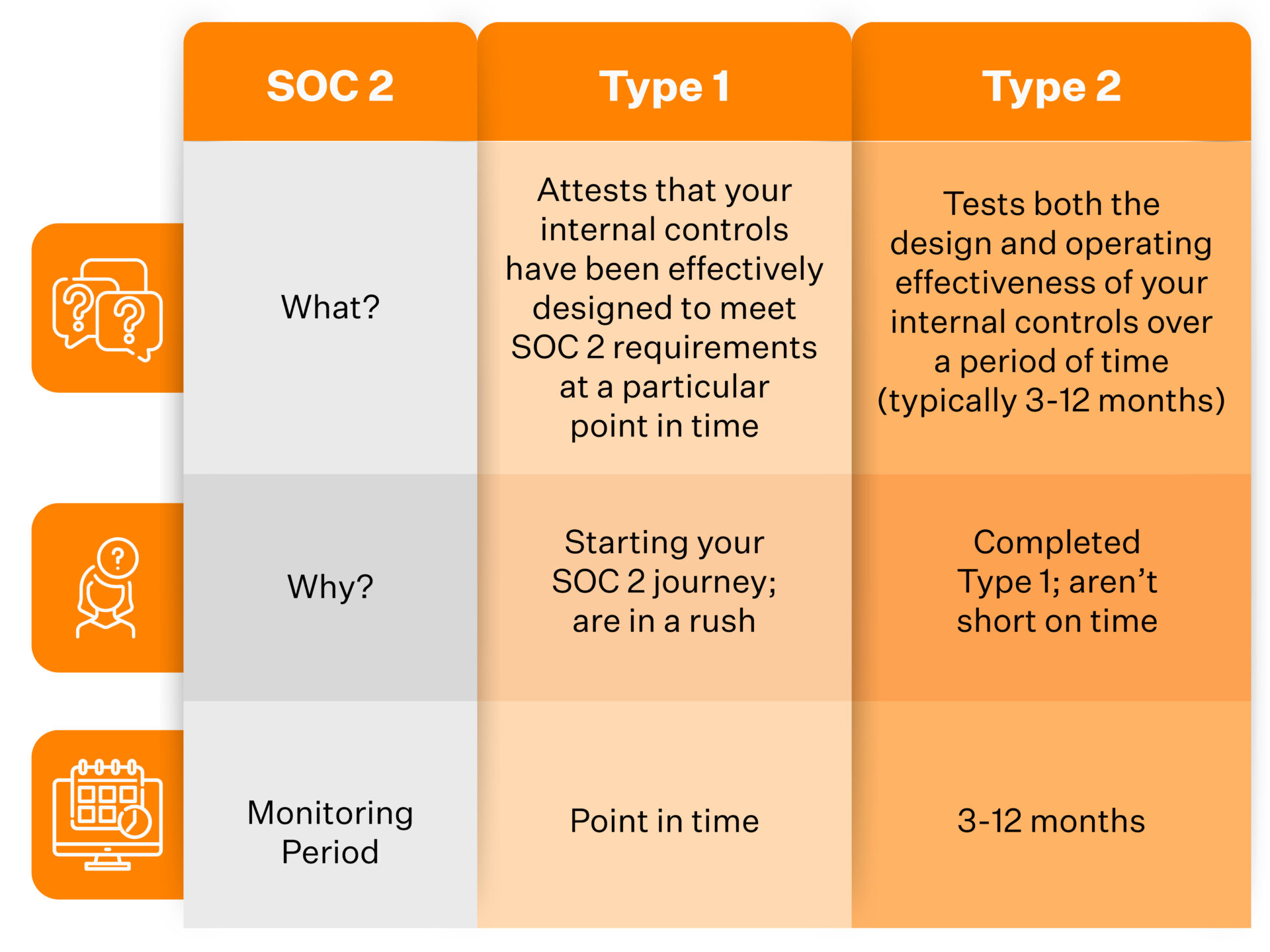
SOC 2 Type 1 evaluates the design of safety measures at a predetermined moment, while SOC 2 Type 2 assesses how effective these controls are over time by observing daily operations for three-six months.
The SOC 2 report outlines any service organization’s controls through the Trust Services Criteria (TSC). This includes five criteria: security, availability, processing integrity, confidentiality, and privacy.
All five criteria are not mandatory, only the security TSC is required. The other four criteria can be optional depending on an organization’s services, operations, and compliance requirements.
Now, let’s deep dive into what SOC Type 1 vs Type 2 are:
SOC 2 Type 1
SOC 2 Type 1 compliance is a rigorous cybersecurity framework designed to protect customer data and transaction information.
Organizations wishing to establish this type of security must submit themselves for an evaluation at a single point in time, which is intended to evaluate the design of the internal controls they have put in place.
SOC 2 Type 1 compliance provides an independent assessment by a CPA to verify these controls are sufficient and designed correctly, so customers can know that their data is being handled appropriately by the organization.
It is important to note that the Type 1 audit can be completed in weeks.
SOC 2 Type 2
With a SOC 2 Type 2 report, you can determine precisely the performance of operating effectiveness of your internal controls and other security measures over a period ranging from 3 to 12 months.
You’ll be able to identify whether or not they are working as intended – giving you peace of mind and confidence in your services!
However, Type 2 audits can be lengthy, often taking 3-12 months of preparation and costing more than Type 1 audits.
As you can see, the major difference between SOC 2 Type 1 and Type 2 compliance is the time period of monitoring during the audit. SOC 2 Type 2 is conducted over a considerably longer duration.
This means that while the shorter Type 1 can only attest to whether the design is suitable, the more extensive Type 2 report has the additional capability of verifying controls’ effectiveness.
Should you choose SOC 2 Type 1 or Type 2 based on your organization?
Whether you need a Type 1 or Type 2 report, both require an audit by a competent service auditor or a CPA firm accredited by AICPA. Therefore, the key question is: What type of SOC 2 report fits best for your service organization? Almost always, it all comes down to timing.
You need to consider the type of data you store, how often it must be accessed, and the overall security environment of your system when selecting the right type of SOC 2 certification.
For example, if you want to make a big sale, but your company is too young or recently made data security changes, don’t worry! You can still prove compliance ASAP with a Type 1 report. This evaluates your current information security controls and provides the perfect short-term solution for closing that major enterprise deal.
For instance, if you collect personal information and need it regularly, a Type 2 audit may make more sense than a Type 1. On the other hand, if you have high security and access controls in place but only sometimes require access to sensitive information, then a Type 1 audit might work better for you.
Whatever direction you go, do your due diligence to get the best possible certification for your organization’s needs.
Also read: SOC 2 Compliance checklist
How SOC 2 type 1 or type 2 will benefit you?
Here is how a SOC 2 Type 1 or Type 2 will benefit your company:
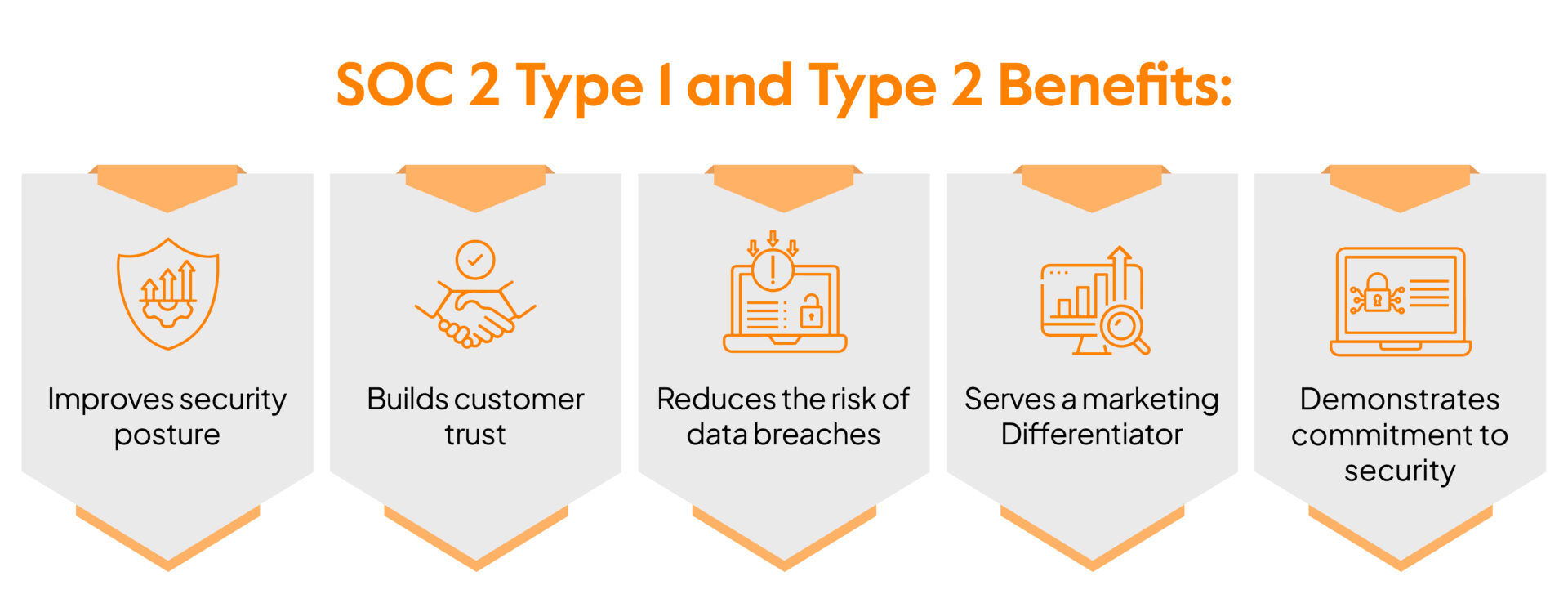
Improve security posture
Ensuring the security of mission-critical data and systems is a basic requirement for any organization. Therefore, conducting a regular review of your security posture is essential.
SOC 2 Type 1 & 2 attestations can help with this by providing a detailed look at your company’s controls over information systems and the services they provide.
Not only do these attestations allow you to benchmark your current performance, but they also serve as an important certification that potential clients may require.
With SOC 2 attestations, you can have confidence in the future and trust in knowing your security posture is strengthened and up-to-date.
Build customer trust
For any organization, trust is paramount. If your company suffers a data breach, your clients may go elsewhere, resulting in total business loss.
Our uncertainty about the present and future makes it increasingly necessary to take proactive steps to secure our systems. That’s where SOC 2 Type 2 auditing comes in. SOC 2 Type 2 attestation provides invaluable reputational recoup for companies that have already suffered an attack, rebuilding the trust of your consumers and saving brands.
Even for companies not yet affected by an attack, this certification can bring a competitive edge that puts them ahead of their uncertified peers.
Customers will be reassured knowing that an independent third party has assessed your security controls and found them adequate. This can help you to win new business and retain existing customers.
Reduce the risk of data breaches
Having SOC 2 Type 1 or Type 2 in place will reduce the risk of data breaches. This is because the assessment will identify any weaknesses in your security controls that attackers could exploit.
The cost of a data breach is far greater than that of a SOC 2 Type 1 or Type 2 audit. In fact, according to IBM, the average cost of a data breach in 2022 was $4.35 million – an increase of almost 10 percent from the year before.
One of the highest financial losses comes from reputation damage, accounting for roughly 38 percent of the total costs associated with the breach. Safeguarding against such violations is paramount and worth any investment necessary.
Remedying these weaknesses will make it much harder for attackers to breach your systems successfully.
Marketing Differentiator
Companies need a SOC 2 report to demonstrate their adherence to rigorous industry standards, which can be an essential selling point in a competitive market. (here are some SOC 2 report examples)
Obtaining a SOC 2 attestation sets you apart from your competition. It shows customers that you have gone the extra mile by investing time and capital to ensure compliance with these requirements.
With a SOC2 Type 1 or, better yet, a Type 2 report, you can proudly showcase your dedication to providing secure services and trustworthiness.
Demonstrate commitment to security
Having SOC 2 type 1 or 2 attestation is such a great tool for demonstrating to shareholders, customers, partners, and other stakeholders that your company is making the best effort to bring its security measures up to the highest standard.
Not only will this improve brand perception, but it can also inspire greater confidence in your ability to protect sensitive data, which is priceless.
What’s Next?
Your next SOC 2 audit doesn’t have to be a grueling experience. With Sprinto, you can rest assured that your journey will be well-planned and precise. Our platform provides accurate controls and checks to move forward with your audit without any issues.
Plus, part of our service includes automation – we’ll take care of the manual, time-consuming tasks for you so that you can focus on higher-value activities. Ready to get started? Book your free demo today and discover how Sprinto can help you easily conquer the SOC 2 world.
FAQs
1. What does a SOC 1 Type 2 report cover?
A SOC 1 Type 2 report covers the controls at a service organization that are relevant to user entities’ internal control over financial reporting. It includes an examination of the service organization’s controls over a specific period of time, typically six months, and the report provides an opinion on the fairness of the presentation of the service organization’s description of its system and the suitability of the design and operating effectiveness of the controls. The report is intended for use by user entities and their auditors.
2. Do I need a SOC 1 or SOC 2?
SOC 1 or SOC 2 is not mandatory, but they can be helpful if you’re working with sensitive data. A SOC 1 report covers the design of your system and the controls you have in place to protect your data. A SOC 2 report dives deeper into your system’s operations and how effectively your controls are being implemented. So, a SOC 2 report is your best bet if you’re handling sensitive customer data.
3. Who needs a SOC 2 Type 2 report?
SOC 2 Type 2 report is needed by organizations that store and manage customer data on the cloud, such as SaaS providers or cloud service providers. They should obtain a SOC 2 report to demonstrate their responsibility in safeguarding personal information from intruders. A valid report proves trustworthiness and confirms that their precious data is safe with you.
Meeba Gracy
Meeba, an ISC2-certified cybersecurity specialist, passionately decodes and delivers impactful content on compliance and complex digital security matters. Adept at transforming intricate concepts into accessible insights, she’s committed to enlightening readers. Off the clock, she can be found with her nose in the latest thriller novel or exploring new haunts in the city.
Grow fearless, evolve into a top 1% CISO
Strategy, tools, and tactics to help you become a better security leader
Found this interesting?
Share it with your friends
Get a wingman for
your next audit.
Schedule a personalized demo and scale business

Sprinto: Your growth superpower
Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.


