
Do you know that 29% of organizations have lost at least one new business deal simply because they lacked the required compliance certification? This should alert you if you’re selling software or services in today’s environment. B2B buyers have become more selective; they expect clear, verifiable proof that their data is safe with you.
A SOC 2 Type II report does precisely that, and it’s quickly becoming a minimum standard requirement rather than a competitive bonus.
Here’s everything you need to know about SOC 2 Type II.
| TL;DR SOC 2 Type II proves your security controls verifiably work over time, not just that they exist. The audit covers a 3 to 12 month period, costs typically $20K to $60K, and needs serious preparation, especially for growing tech teams. Buyers expect a fresh report every year, and not having one slows, even kills, opportunities with enterprise or security-conscious clients. |
What’s a SOC 2 Type II report?
A SOC 2 Type 2 report is an independent, third-party attestation that measures the design and effectiveness of your company’s security controls over an observation period, typically spanning between 3 and 12 months.
A SOC 2 attestation is issued by a licensed CPA firm based on criteria set by the American Institute of Certified Public Accountants (AICPA). It’s a rigorous test of how your systems, policies, and processes perform in practice.
Every SOC 2 report is based on five Trust Services Criteria (TSC) developed by the AICPA. These are:
- Security: Mandatory. Covers protection against unauthorized access.
- Availability: Uptime, disaster recovery, and incident response.
- Processing integrity: Accuracy and reliability of your system’s operations.
- Confidentiality: Handling of sensitive information like IP, contracts, or business data.
- Privacy: Focused on personal information and how it’s collected, used, and retained.

Most companies start with Security and optionally include one or more of the others, depending on their industry or client needs.
Expect the SOC 2 Type 2 report to be anywhere from 50 to even 100+ pages.
The two types of SOC 2 reports
Before we step into what a type 2 report encompasses, it’s important to understand the types of SOC 2 reports and their purposes.
- SOC 2 Type I: A SOC 2 Type 1 report is a snapshot of an organization’s operational controls at a given point in time. It’s useful if you’re new to compliance. It’s also faster to complete, but carries less weight with the security-conscious buyer.
- SOC 2 Type II: A SOC 2 type 2 report observes an organization’s operational controls over a defined period, known as the observation period, and assesses both the design and effectiveness of controls. Procurement and security teams consider it more credible and thorough.
Here’s are the key difference between SOC 2 Type I vs Type 2
| Feature | SOC 2 Type I | SOC 2 Type II |
| Scope | Point-in-time assessment | Ongoing assessment over a period |
| Focus | Control design | Control design and operating effectiveness |
| Audit timeline | Shorter (a few weeks) | Longer (3+ months) |
| Report frequency | Typically once, or prior to Type II | Renewed annually (or biannually) |
Why is having a SOC 2 Type 2 report important?
A SOC 2 Type II report gives you a credible, independent signal that your company takes security seriously, not just in theory, but in practice. It shows that your controls have been tested, verified, and proven.
According to Gartner, 78% of buyers now ask for SOC 2 compliance before signing a contract. For companies in SaaS, healthtech, and fintech, not having a SOC 2 Type II report means you’re out of the running before the first call.
There’s also the cost of not having it. Companies now spend up to 25% of their annual revenue on compliance activities. Without a framework like SOC 2, those efforts become duplicated, manual, and reactive.
A proper SOC 2 Type II process brings structure and repeatability to risk management. Over time, this reduces audit fatigue and compliance overhead.
Benefits of having a SOC 2 Type II report
A SOC 2-compliant organization indicates that the organization has the infrastructure, tools, and processes to safeguard its data from threats from the firm and externally. Here are some benefits of getting a SOC 2 Type II report:
1. Increases trust
Arguably, the biggest benefit of achieving SOC 2 Type II compliance is trust. When you’re selling to larger organizations or handling sensitive customer data, buyers want assurance that you’re not approaching it without a proper strategy and processes. A clean SOC 2 Type II report reduces uncertainty and builds confidence with stakeholders at every level.
2. Accelerates operations
SOC 2 compliance helps you move faster. If you’ve ever filled a 200-question security questionnaire, you already know how tedious and time-consuming that process can be. But when you have a SOC 2 Type II report, you can bypass much of that red tape.
Many procurement teams will skip large portions of due diligence if you’ve already passed a third-party audit. That can shave weeks, sometimes months, off the sales cycle.
3. Operationalizes your security posture
With SOC 2, you have systems in place to monitor access controls, encryption, change management, incident response, and evidence that they’re working. This pushes maturity across your organization. You’ll be better prepared for security incidents and more capable of handling risk.
4. Makes you stand out
While many peers are still scrambling to meet basic security requirements, showing up with a recent SOC 2 Type II report instantly sets your organization apart. It proves your systems, processes, and controls have been independently verified over time.
In fact, 29% of organizations have lost potential new business due to the absence of a required compliance certification, like SOC 2 Type II.
Who needs a SOC 2 Type II report?
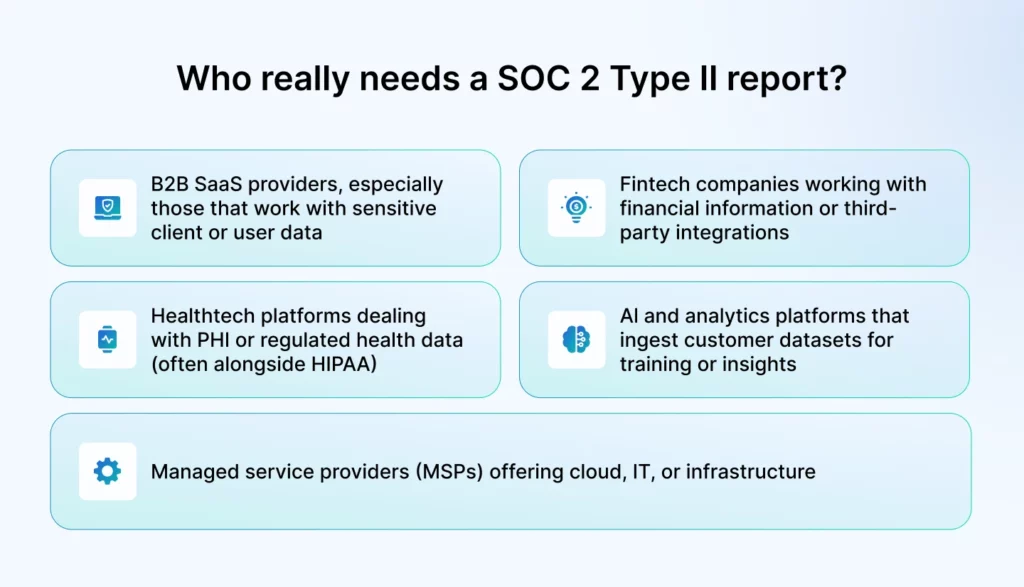
If your business stores, processes, or transmits customer data, in the cloud or otherwise, you need a SOC 2 Type II report. No, it’s not only for publicly traded companies or enterprise vendors. It’s becoming the baseline for trust across data-driven service providers.
A simple way to think about it: If your customers are asking about data security during onboarding or procurement, a SOC 2 Type II report answers that question in a way they’ll recognize and respect.
Typical companies that benefit from SOC 2 Type II:
- B2B SaaS providers, especially those that work with sensitive client or user data
- Fintech companies working with financial information or third-party integrations
- Healthtech platforms dealing with PHI or regulated health data (often alongside HIPAA)
- AI and analytics platforms that ingest customer datasets for training or insights
- Managed service providers (MSPs) offering cloud, IT, or infrastructure services
As SMBs move upstream or enter more regulated markets, SOC 2 Type II becomes less optional and more expected.
What must your SOC 2 Type II report contain?
The SOC 2 report itself usually has many components, including:
1. Management assertion
This is your official statement signed by leadership, asserting that the controls you’ve implemented to meet the relevant Trust Services Criteria (TSC) are designed and operating effectively. It shows that your organization takes ownership and responsibility before the auditor weighs in.
2. Independent auditor’s opinion
The independent auditor’s opinion section contains the final verdict from the CPA firm. Based on their testing, they’ll state whether your controls met the required criteria over the audit period. A clean, or “unqualified,” opinion means the auditor found no significant issues.
3. System description
The system description contains a detailed overview of the systems, services, and boundaries covered by the audit. This includes everything from infrastructure and software to people and processes, giving context for how your environment supports security, availability, processing integrity, confidentiality, and privacy.
4. Control activities
The control activities section includes a full list of your implemented controls for each applicable TSC. It outlines what each control is intended to do (e.g., restrict access, monitor activity, respond to incidents) and how it relates to the TSC. This section often maps each control directly to specific risks and requirements.
5. Testing results
Finally, the testing results is where the auditor shares what they did to evaluate each control—what evidence they reviewed, what tests they ran, and whether each control passed or failed. This section gives readers a transparent view into the rigor of the audit and how your organization performed under scrutiny
How much does a SOC 2 Type II audit cost?
SOC 2 audits don’t come cheap, but the investment is lower than the cost of not being compliant. Although not written in stone, here’s what you need to expect:
- Audit firm fees range from $7,000 to $50,000, depending on the complexity of your systems, the number of controls, and whether you’ll be including criteria beyond Security.
- Preparation and tooling: Compliance automation tools help automate evidence collection and manage controls. These alone cost $5,000 to $20,000 a year.
- Internal resource time: Expect anywhere between 100 to 300 hours from your team over the course of preparation and audit, if you’re starting from zero.
- Remediation work: If your environment isn’t ready, you will need to invest in infrastructure upgrades, documentation, access control policies, or incident response plans.
The total cost can easily exceed $75K for a mid-size team. Many startups and smaller companies can do it for far less by narrowing the scope and using automation to lighten the load.
However, the time and cost of SOC 2 prep can quickly add up for growing teams. Consider compliance automation tools like Sprinto that allow you to pay for what you use.
Sprinto offers you a personalized dashboard with specific features and workflows to minimize manual effort and maximize efficiency, reducing the time and cost to achieve the SOC 2 Type 2 report marginally.
Sprinto helped Ripl achieve SOC 2 readiness in just 25 days and complete their Type 2 audit in 14 days after surveillance. With Sprinto’s automation in place, Ripl now manages ongoing compliance with just 10 minutes of oversight per week.
When should you conduct a SOC 2 Type II audit?
You should conduct a SOC 2 Type II audit once your security controls are fully implemented and once you have reasonable confidence and evidence that they have functioned consistently (through monitoring) over a period of the observation period.
This audit is especially important when customers or partners require proof of sustained compliance and operational reliability.
A common path is to begin with a SOC 2 Type I to validate your control design, then transition to a Type II once your systems have stabilized, as this Redditor exemplifies.
Via Reddit
For many high-growth SaaS companies, on the other hand, the right time to kick off a Type II audit is just after raising a seed or Series A round, when you’re scaling, building trust with enterprise prospects, and trying to close larger deals.
With all that said, let’s see how you have to prepare for a SOC Type II audit.
How to prepare for a SOC 2 Type II audit?
Follow these proven preparation steps, which have been used by companies with successful audits, to complete the audit without disrupting your team’s workflow.
Step 1: Define your scope early on
SOC 2 scope defines the boundaries for assessing internal controls during a SOC 2 audit. It clarifies which service providers control and which systems must be evaluated to ensure the protection of customer data.
To define your SOC 2 Type 2 scope, typically involves the following steps:
- Identify key services: Focus on the services that handle sensitive customer data.
- Map supporting systems: List the apps, infrastructure, and workflows behind those services.
- Document policies: Include the security and availability policies that guide your operations.
- List involved personnel: Call out the teams and roles directly managing in-scope services.
- Align with trust criteria: Ensure your scope matches relevant Trust Services Criteria like security or availability.
Step 2: Document your policies and procedures
Auditors want to see written, approved, and distributed policies. That means access control policies, vendor risk management, change management, incident response, encryption standards, and more. It doesn’t count if it’s not documented,
Don’t just download templates and call it done. Review and adapt them to reflect how your team works. Auditors are quick to catch on when policy and reality don’t match.
Step 3: Implement the technical controls
Technical controls depend on your SOC 2 scope and the Trust Services Criteria (TSC) selected by your organization. These controls must be precisely mapped to the specific SOC 2 requirements, as SOC 2 does not mandate any particular controls by default.
At a minimum, make sure you have:
- SSO and MFA are enabled for all critical systems
- Role-based access control with provisioning and deprovisioning processes
- Logging and monitoring on production systems
- Secure development and deployment practices like code reviews, CI/CD controls
- Regular backups and disaster recovery testing
The tools we mentioned earlier can automate much of this, but they don’t replace the need for operational discipline.
Getting ready for a SOC 2 Type II audit can feel overwhelming, especially when you’re juggling documentation, tooling, and team coordination. This is where a platform like Sprinto can make a big difference.
It maps controls to the SOC 2 framework out of the box, automates evidence collection, and guides you through what needs to happen next.
Instead of duct-taping your way through spreadsheets and screenshots, Sprinto plugs into your existing systems and helps you stay audit-ready without the heavy lift.
Step 4: Carry out a readiness assessment
A SOC 2 readiness assessment is a pre-audit evaluation that helps your organization determine how prepared it is to undergo a formal SOC 2 audit.
Either self-led or conducted with a consultant, before you invite an auditor, it helps point out gaps and broken processes before they become official audit findings.
After the assessment, your next steps are to review the findings, fix any gaps, update your policies, and make sure your security practices are clearly documented.
Once everything’s in place, you’re ready to bring in a certified auditor to start the official SOC 2 process.
Step 5: Choose an audit partner
You’ll work with this firm for at least a few months, possibly years. Choose a CPA firm with evidential SOC 2 experience; ideally, one that’s worked with companies your size and in your industry.
Here are some more things to keep in mind:
- Must be a licensed CPA firm: If they’re not licensed, the SOC 2 report won’t be valid.
- Relevant industry experience: Choose an auditor who understands your specific industry (e.g., SaaS vs. healthcare).
- Pre-audit support: Some firms offer readiness assessments to help you prepare before the formal audit.
- Clear pricing and timelines: Make sure you know what you’re paying for and how long the process will take.
- Strong security knowledge: Auditors should be familiar with modern DevOps, cloud environments, and compliance tools.
Also, consider whether they work well with your tech stack. Misalignment here creates unnecessary friction.
Step 6: Train your team
Everyone should understand their role in compliance, from engineers and IT to HR and support. Even a 10-minute security awareness session does a lot.
SOC 2 Type 2 auditors often speak with team members during virtual or onsite walkthroughs to see if policies are being followed in practice. These are usually casual interviews or quick chats with people across IT, HR, support, or engineering.
The goal isn’t to quiz anyone deeply, but to confirm that basic processes like access control or incident response are understood and followed. It can raise red flags if someone seems unaware of key security steps relevant to their role.
So while not everyone will be interviewed, it’s best to prepare your team as if they might be.
The fastest & most cost-efficient way of getting a SOC 2 Type 2 report
Getting SOC 2 Type II compliant is a big step, but it doesn’t have to drain your time or budget. Sprinto makes it easier.
Sprinto handles up to 90% of the heavy lifting while getting you a SOC 2 Type 2 report. From pre-mapped SOC 2 controls and real-time evidence collection to built-in security training and expert guidance, it helps you get audit-ready without burning out your team.
Because compliance isn’t a one-time event, Sprinto keeps you on track year-round with smart alerts, continuous monitoring, and support for other frameworks like ISO 27001 and GDPR.

Automate and Fastrack with Sprinto.
FAQs
1. How long is a SOC 2 Type II report valid?
SOC 2 Type II reports are generally valid for 12 months from the end of the audit period. After that, customers may start asking for an updated report to confirm that your controls are still working.
2. What’s the difference between ISO 27001 and SOC 2 Type II?
SOC 2 Type II is a U.S.-based framework focused on how your controls perform over time, especially around the five Trust Services Criteria.
ISO 27001 is an international standard that certifies that your information security management system (ISMS) is designed and maintained properly. U.S. clients mostly prefer SOC 2; ISO 27001 is more global.
3. How often are SOC 2 reports required?
Most companies update their SOC 2 Type II report annually. The newest version must not be more than a year old if you’re working with regulated or enterprise clients.
Pansy
Pansy is an ISC2 Certified in Cybersecurity content marketer with a background in Computer Science engineering. Lately, she has been exploring the world of marketing through the lens of GRC (Governance, risk & compliance) with Sprinto. When she’s not working, she’s either deeply engrossed in political fiction or honing her culinary skills. You may also find her sunbathing on a beach or hiking through a dense forest.
Explore more SOC 2 articles
SOC 2 Compliance Overview
SOC 2 Preparation and Documentation
SOC 2 Audit and
Reporting
SOC 2 Differences and Similarities
SOC 2 Updates & Management
SOC 2 Industry-Specific Applications
research & insights curated to help you earn a seat at the table.






