
In today’s day and age, data security is a pivotal selling point. Customers and prospects want to know that their data is secure and that the companies they sign on with have sufficient measures to ensure it stays that way. And so, companies are often tasked with proving the effectiveness of their security controls.
A SOC 2 report isn’t just a goldmine of information on how a company secures its sensitive data and information. It can also help prospects and customers understand the robustness of its security measures and posture.
Here’s a quick lowdown on who needs a SOC 2 report, what your customers will look for in it, and why you need it.
| TL; DR |
| SOC 2 report: The SOC 2 report exhaustively describes your audit and testifies to the strength of your infosec practices. |
| SOC 2 report contents: Management Assertion, Independent Service Auditor’s Report, System Description, Applicable Trust Services Criteria, Related Controls, Tests of Controls, Results of Tests, and Other information provided by the Management. |
| SOC 2 report preparation cost: The costs to prepare for the report depend on your organization’s size, the complexity of operations, and the type of auditor chosen. |
What is a SOC 2 report?
A SOC 2 report is an AICPA-accredited auditor’s analysis of a service organization’s internal operational controls and their effectiveness per SOC 2 requirements against security, availability, processing integrity, confidentiality, and privacy. It helps build trust for customers and business partners for handling sensitive data in compliance with the SOC 2 standard.
Why do companies need a SOC 2 report?
SOC 2 reports help by building your customers’ trust, strengthening your security posture, adopting security best practices, and enabling organizational growth. It acts as a testament of trust for your vendors and boosts stakeholder confidence.
Here are the 9 reasons for organizations to have SOC 2 report:
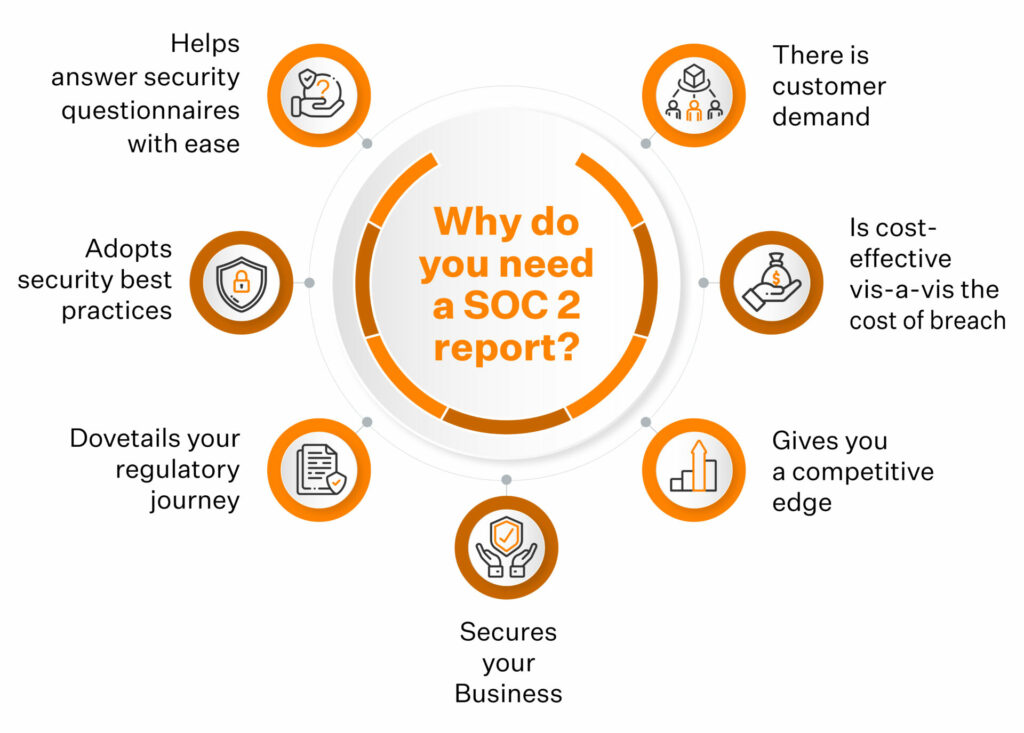
Who needs a SOC 2 report?
A SOC 2 report is needed by service organizations that store, process or transmit sensitive customer data or handle critical functions for clients. A SOC 2 compliance report is crucial to foster client trust and ensure integrity of services.
For example, the following service organizations must obtain a SOC 2 report:
1. Cloud service providers
Cloud service providers are third-party organizations providing infrastructure (IaaS), platform (PaaS) or software as a service (SaaS) to businesses. CSPs provide access to computing resources to manage data, security needs, analytics etc. As such, they are required to assure the customer about the safety of data stored and that is where a SOC 2 report precisely plays its part.
2. Healthcare service providers
Healthcare service providers such as medical billing companies that handle sensitive PHI are required to submit a SOC 2 report to hospitals, insurance companies etc. The SOC 2 report serves as an assurance of implementation of safeguards to protect privacy and confidentiality of patient data.
3. Payment processors
Payment processors that handle sensitive cardholder data for various payment related services need to obtain a SOC 2 compliance report. The report certifies that necessary tools and practices have been deployed to secure bank account details, credit card numbers and other such critical and vulnerable information.
4. Managed service providers
Managed service providers provide remote solutions for managing customer’s IT needs such as network management, data backups, infrastructure and security among others. A significant amount of client’s sensitive data is exposed to the MSP and a SOC 2 report is essential to confirm the effectiveness of controls in place for safeguarding information.
5. Other organizations handling sensitive data
Other organizations such as data centers, government contractors, financial institutions etc. handling critical data must obtain SOC 2 to demonstrate that they prioritize data security and compliance. Such service providers also have a competitive edge in differentiating them from peers.
Sprinto automates SOC 2 compliance for all such organizations and enables them to breeze through SOC 2 audit. The platform helps you build a tightly integrated pipeline of controls and run automated checks to ensure continuous compliance. Read how Phyllo cut through compliance complexity with Sprinto.
Get Our Practical SOC 2 Guide;
Yours at No Cost

Types of SOC 2 reports
There are two types of SOC 2 reports based on the depth of evaluation and the monitoring period—Type 1 and Type 2. A Type 1 report evaluates the effectiveness of controls and compliance with SOC 2 at a point in time. A Type 2, on the other hand, is an evaluation of compliance and controls over an evaluation period.
SOC 2 Type 1 report reviews the design of an organization’s internal controls as per SOC 2 requirements at a point in time. It’s like a snapshot of the design of internal controls. So, to that extent, it is not very comprehensive and takes lesser time to obtain (relative to SOC 2 Type 2).
SOC 2 Type 2 report is detailed and comprehensive. It has an in-depth description of the design and operating effectiveness of the organization’s internal controls vis-a-vis framework requirements over a 3-12 months period.

Also find out the difference between SOC 2 vs ISO 27001 compliance, if you are planning to get ISO certified as well.
How does SOC 2 compliance ensure data security?
SOC 2 compliance is essentially a seal of approval for how well a company safeguards your data. This assurance comes after thorough audits scrutinizing every aspect of data handling to ensure it’s done responsibly.
SOC 2 requires the establishment of comprehensive security policies and procedures. These policies define how data should be handled, accessed, and protected throughout its lifecycle.
Moreover, SOC 2 requires continuous monitoring of systems and networks to detect potential security incidents or anomalies promptly. Logging and audit trails are maintained to track access to sensitive data and to facilitate forensic investigations if security breaches occur.
For more information, we have a SOC 2 self assessment checklist for you:
Download Your SOC 2 Self Assessment Checklist
What does a SOC 2 report include?
Apart from general information on the audited organizations, SOC 2 reports are sought after for the auditor’s opinion on their independent assessment of the organization’s controls. It also comprises a description of the tests involved and recommendations to improve data security protocols where needed. You must select an AICPA-accredited CPA (firm or individual) to conduct your audit.
SOC 2 reports can run into many pages and include the following sections:

Section 1: Management Assertion
The section captures a summary of the organization’s services, products, applications, structures, systems and security controls and gets written by the audited organization. The management acknowledges that the information provided is accurate and relevant.
Section 2: Independent Service Auditor’s Report
This section comprises the much sought-after auditor’s opinion on the organization’s cyber security posture; it, however, doesn’t give details beyond that.
An auditor’s opinion is divided into four types:
Unqualified – You pass with flying colors!
The auditor’s unqualified opinion indicates that the auditor found no issues during the audit. All the controls tested were designed appropriately (Soc 2 Type 1 report) and operated effectively (Type 2 report).
Qualified – Close, but not quite
This means that some areas need attention. What is the worst thing about a qualified report? It depends on the failed controls and how they affect the report’s users.
Adverse – You failed
An adverse opinion means the organization materially failed one or more standards, and its controls and system aren’t reliable.
Disclaimer of Opinion – No comments!
This isn’t really an opinion. Essentially, the independent auditor could not form an opinion based on the information provided. It occurs when auditors do not have access to the required information or cannot complete it neutrally.
Section 3: System Description
This section of the audit report is a must-read and describes the system(s), scope & requirements, components, controls, and other systems information. Control activities (policies and procedures) get detailed in this section alongside information and communication systems, monitoring and risk assessments.
Section 4: Applicable Trust Services Criteria and Related Controls, Tests of Controls, and Results of Tests
This section summarizes all the tests and its results performed during the audit, which makes it a critical part of the report. The section provides insights into the auditor’s opinion described in section 2.
SOC 2 Trust Service Criteria, formerly known as Trust Service Principle, comprise security, availability, confidentiality, privacy, and processing integrity. The first three sections in both SOC 2 Type 1 and SOC 2 Type 2 reports are similar, but this section differs significantly.
Type 1 report features a list of all the controls in the evaluation period. Type 2 report will also present the auditor’s tests and the test results for each listed control. For a Type 2 report, this section will also highlight exceptions or deviations noted by the external auditor.
Aside from the Trust Service Principles, the organization’s infrastructure, software, people, data and procedures also get audited.

Section 5: Other information provided by the Management
This section is optional. It comprises management’s response to the variations highlighted by the auditor in the earlier section. The management gives more context and information around the exceptions, citing reasons for the deviations and proposing ways to ensure it doesn’t repeat.
How long does it take to prepare a SOC 2 report?
The time to obtain your SOC 2 report depends on several factors – the type of SOC 2 report, the route to SOC 2, and the complexity of your business processes. If you use a DIY approach or rope in an external consultant to get your report, you must set aside 3-6 months for audit preparation alone.
Add to that the audit monitoring period of 3-12 months for SOC 2 Type 2, and the minimum time to procure a SOC 2 report is roughly six months! And that’s an optimistic bet. Type 1 takes lesser time in comparison.
Also read: Guide to SOC 2 Type 2 certification
When you work with compliance automation platforms like Sprinto, you can drastically cut down the audit period and time to get a report. Our clients get audit ready in weeks and are able to fast-track the certification process because of streamlined workflows. Read how Ripl achieved audit readiness in 25 days and completed the audit in 14 days after moving to SOC 2.
Here’s what Dassana has to say about getting SOC 2 Type 2 with Sprinto:
How much does SOC 2 report preparation cost?
The costs to prepare for the report depend on your organization’s size, the complexity of operations, and the type of auditor chosen. In addition to readiness assessments (optional) and other overheads, a SOC 2 report can set you back by about $20000-$50000. Again, these are just ballpark estimates.
Automating your compliance with Sprinto can bring down your costs considerably. The platform helps you address multiple aspects such as out-of-box policy templates, security awareness training enablement, and automated compliance tasks such as evidence collection and control checks without any additional costs. Want to learn more? Speak to our experts.
Benefits of obtaining a SOC 2 report
A SOC 2 report helps manage risks better, strengthen brand image, build a security conscious culture and prepare for other frameworks quickly. Every organization reaps long-term benefits of a SOC 2 report.
Let’s have a look at some of these benefits:
Risk management
A SOC 2 audit requires a rigorous risk assessment of the control environment with an evaluation of severity, impact and likelihood of each risk to information assets. This is done for gap analysis and creating a tactical mitigation plan. The process helps instill effective risk management practices and integrate them into organizational culture.
Credibility and competitive advantage
Displaying a SOC 2 report on your company website can demonstrate your commitment to data security and enhance public perception. It can shorten the sales cycle as the report serves as tangible evidence of a secure environment and builds quick credibility giving you an edge over competitors.
Want to share your SOC 2 report with clients? You can create a public or private profile with Sprinto’s trust center to communicate your live compliance status and security posture.
Enhanced security posture
The systematic enforcement of controls such as data encryption, access management policies, third-party risk management among others an ongoing improvement process. Moreover, continuous monitoring of compliance drifts ensures that the organization adheres to regulatory requirements. These airtight security practices gradually translate into a strong security posture for the organization.
Cost savings
A SOC 2 report saves long-term costs of the organization on multiple fronts. It minimizes the costs of data breaches and penalties with lesser instances of non-compliance. The streamlined security processes bring benefits of efficiency and reduced downtime. These benefits outweigh the costs of getting SOC 2 compliant over a course of time.
Compliance with other regulations
Preparing to get a SOC 2 report can help you fast-track compliance processes for other regulations. For example, ISO 27001 has a significant overlap with SOC 2 controls. Preparing for SOC 2 can help you automatically prepare for ISO 27001 and minimize duplication of efforts.
Want to understand the overlap between frameworks? Sprinto can help. The platform automatically maps common controls for making the process easier.
Read how DNIF simultaneously achieved SOC 2 and ISO 27001 readiness in 14 days.
Reduced effort for security questionnaires
While you can’t eliminate the time you spend answering the security questionnaire, having a SOC 2 report makes the process easier, seamless and faster. Find the best SOC 2 Report examples here.
Find out how Sprinto can help you get your SOC 2 report
SOC 2 audit framework can be exhaustive and come with multiple back-and-forths between the auditor and you. Sprinto’s compliance automation platform removes inefficiencies and automates repeatable tasks. As a result, you spend less time toggling between windows and more time on business-critical tasks.
Gain a bird’s eye view of all your controls on Sprinto’s dashboard. You can track the effectiveness of controls, live compliance, and security health status, as well as identify gaps in controls. The platform also alerts your security teams when your controls are about to fail.
This way, they can proactively take action to ensure continuous compliance. Sprinto makes audits easy as well. Your auditor gets a custom dashboard that compiles all of your evidence and documentation in an easy-to-read format.
Even with the type of SOC 2 report, Sprinto saves you 100+ hours of audit prep time and helps you invest your time where it matters most.
Ready to see Sprinto in action? Talk to our SOC 2 experts today.
FAQs
Can a SOC 2 report be shared with anyone?
A SOC 2 report is not for public display. They have sensitive information about your security processes and controls. However you can share parts of the report privately and sign NDAs for safety concerns.
Which principle must always be included in the SOC 2 report?
The security principle is a mandatory criteria that must be included in the SOC 2 report. This principle contains common criteria for other principles and ensures data protection.
How long is the SOC 2 report valid for?
A SOC 2 report is valid for a year from the date of issue of report. Organizations are therefore required to get the controls evaluated regularly and schedule an audit every 12 months.
Who audits the SOC 2 report?
Your SOC 2 auditor is the one who prepares your report. The report is a detailed evaluation of your internal controls, tests, and results and comprises management assertion, and system description, among other things.
Srividhya Karthik
Srividhya Karthik, is a Content Lead at Sprinto, she artfully transforms the complex world of compliance into accessible and intriguing reads. Srividhya has half a decade of experience under her belt in the compliance world across frameworks such as SOC 2, ISO 27001, GDPR and more. She is a formidable authority in the domain and guides readers with expertise and clarity.
Explore more SOC 2 articles
SOC 2 Compliance Overview
SOC 2 Preparation and Documentation
SOC 2 Audit and
Reporting
SOC 2 Differences and Similarities
SOC 2 Updates & Management
SOC 2 Industry-Specific Applications
research & insights curated to help you earn a seat at the table.






