SOC Reports: Why Does Your Business Need Them?
Pritesh Vora
Feb 27, 2024

SaaS adoption has increased across the board, especially in large enterprises. Accelerated digital adoption is a result of the COVID-19 pandemic. It has added to the growing cybersecurity risks of today’s cloud-based environments.
Cloud services provide large enterprises the opportunity to save costs and increase efficiencies. But, it requires them to share sensitive data with service providers.
SOC reports assure customers that their data can be safely handled by SaaS vendors. So, it drives greater transparency and builds trust. It also gives vendors a competitive edge. This article will explain what is a SOC report, the SOC report meaning, and the different SOC report types.
Key Points

- SOC reports are a compliance standard for service providers who handle sensitive customer data. E.g. healthcare, banking, SaaS companies.
- There are three types of SOC reports: SOC 1 for financial reporting, SOC 2 for design and operational effectiveness of internal controls, SOC 3 for presenting SOC 2 report information to the general public.
What is a SOC Report?
A SOC report serves as a verification tool to ensure your organization adheres to specific best practices for safeguarding client data. This report is shared with customers and auditors, offering transparency into your control environment
It is produced after an audit by an independent third-party AICPA-certified public accountant (CPA).
SOC audits cover one or all the trust service criteria or the trust services principles:

Thus, SOC reports detail the vendor lifecycle and offer actionable feedback on vulnerabilities. This helps the organization remove inconsistencies if any.
Having a SOC report sends a strong signal to customers that your organization upholds its policies and procedures. Independent third-party auditors create and confirm these SOC reports. The American Institute of CPAs oversees these auditors, specifically SSAE 18 standard compliance.
SOC examinations are not formally required. But they’re often requested by large enterprises for assurance that vendors are operating in a compliant and ethical manner. You can help prospects make easy hiring decisions by presenting your platform as completely risk-free.
Also check out: SOC 2 Compliance Guide
Why do you need a SOC Report?
SOC reports apply to organizations that provide services or software. E.g., financial services, payroll, healthcare, and data centers. It also applies to third-party service providers like web hosting, cloud storage, and software-as-a-service (SaaS) companies.
Such organizations store, process, or impact the financial or sensitive data of their user entities or clients.
SOC reports help customers to understand a vendor’s security and legitimacy of data and systems. It also enables vendors to fix flaws and identify vulnerabilities before customers do.
Most large enterprises need a SOC 2 report before they onboard a service provider. It can be difficult to determine which type of SOC report fits your specific business needs. Hence, let’s understand what each type of report entails.
Recently, Dassana decided to choose Sprinto based on its user-friendliness, automated workflows, design, and affordability. Owing to this, they got SOC 2 audited in 2 weeks within 3 sessions.

If you want to know more about, read the case study in detail.
Get a wingman for your SOC 2 audit
Different Types of SOC Reports
There are different SOC reports: SOC 1, SOC 2, SOC 3, and SOC for cybersecurity reports.

Let’s look at each different types of SOC reports in detail:
What is a SOC 1 Report?
SOC 1 reports focus on financial reporting and it is based on the SSAE 16 (Standards for Attestation Engagements) reporting standard. It checks controls that directly affect or have the potential to affect the financial statements of customers.
SOC 1 compliance proves you can ensure that the design and operation of your service are effective and predictable.
Your clients will need a SOC 1 report if you provide a service that may impact your client’s internal controls over financial reporting (ICFR). A SOC 1 attestation demonstrates that you have:
- General IT controls
- Business process-related controls e.g. transaction authorizations, reconciliations
These controls help achieve the objective statements determined by your industry and level of risk.
There are two types of SOC 1 reports – Type I and Type II:
SOC 1 Type I
It focuses on the description of a service provider’s controls and the suitability of their design to achieve control objectives on a specified date. Also, it covers controls relevant to an audit of a user entity’s (customer’s) financial statements.
It does not check for the operational effectiveness of the control set.
SOC 1 Type 2
It contains the same opinions as a SOC 1 Type I report but adds an opinion on operating effectiveness.
Designed to reduce the risk of financial inaccuracy, it checks the operational effectiveness of controls over a period of time.
SOC 1 audit reports are restricted to the management of the service provider, its customer, and the customer’s auditors. These reports help customers who need to comply with the Sarbanes-Oxley Act (SOX) of 2002. Other benefits to customers are:
- Combats corporate and accounting fraud
- Improves adherence to corporate responsibilities
- Ensures compliance with financial rules and regulations.
Learn the difference between SOC 1 and SOC 2 here:
What is a SOC 2 Report?
SOC 2 reports outline five trust services criteria (TSC). They are security, availability, processing integrity, confidentiality, and privacy. These criteria address internal controls unrelated to ICFR.
The TSC is closely aligned with frameworks like the PCI-DSS and the HIPAA security standards. But, unlike PCI-DSS which has explicit requirements, SOC 2 requirements allow more flexibility to decide how to meet the TSC.
Security controls testing is also called common criteria and is mandatory for SOC audits. Whereas the others are optional. You can choose one or more of the criteria that apply to your business practices. Thus, SOC 2 reports are unique to each service provider.
SOC 2 reports are issued under the Attestation Standards 101. They are general provisions that provide a broad-based framework for auditing organizations.
A SOC 2 report includes the following:
- An opinion letter
- Management assertion
- Detailed description of the system or service
- Details of the chosen trust services categories
- Testing of controls and its results
- Additional information (optional)
The use of SOC 2 reports is restricted to existing and prospective clients.
The reputation and experience of the auditor are important to SOC 2 reporting. The SOC 2 audit is simply the auditor’s opinion of whether the service provider’s controls meet the TSC.
There are two types of SOC 2 reports – Type I and Type II.
SOC 2 Type I reports
It checks the organization’s systems at a specific date or point in time. It does not test operational effectiveness. Organizations usually run a Type I report first to quickly check the level of compliance.
SOC 2 Type II reports
It tests how an organization’s systems have complied over time. The operational effectiveness of the systems is checked with a sampling methodology.
It could take between 3-12 months, but six months is the most common. It is easier to run a SOC 2 Type 2 report if you’ve run a Type I report before.
Get SOC 2 ready faster with automation
What is a SOC 3 Report?
A SOC 3 report contains the same information as the SOC 2 report, but since it’s presented to a general audience, it is shorter and less detailed.
A SOC 2 report contains sensitive information about specific systems and network controls, which should be protected from malicious entities. A SOC 3 report is public-facing, excludes all sensitive information, and does not compromise or disclose internal control details.
It provides a high-level summary without disclosing details of internal controls so it can be freely distributed. Typically, it contains a short auditor’s opinion, management assertion, and system description.
SOC 3 reports are used as front-facing reports such as marketing materials. Often, service providers make SOC 3 available on their websites while customers have to request a copy of the SOC 2 report.
Take a look at Oracle’s SOC 3 report.
SOC for cybersecurity report
Similar to other attestations within SOC, the American Institute of CPAs (AICPA) oversees SOC for Cybersecurity, which was introduced in 2017 to address growing concerns about cyberattacks in the marketplace.
Who Needs a SOC for Cybersecurity Report?
A SOC for Cybersecurity examination suits any organization, regardless of size or industry. It’s ideal for businesses, non-profits, and virtually any organization aiming for a proactive approach to risk management.
This includes business investors, lenders, insurance providers, analysts, and regulators. If you seek to reduce your company’s risk, the SOC for Cybersecurity may be the right choice.
What If I Already Have a SOC 2 Report?
There are key differences between SOC 2 and SOC for Cybersecurity reports in terms of scope, purpose, use, and controls. While SOC 2 examines the AICPA’s Trust Services Criteria for a broad range of users, SOC for Cybersecurity provides specific assurance that the necessary systems, processes, and controls exist to manage a cyberattack.
Does it seem too much for you?
What if you could meet all the cybersecurity requirements for SOC without hassle? Well, with the Sprinto solution, you can do just that! It provides an easy way to achieve quick compliance by integrating people, processes, documentation, incident management, and more for 24/7 security.
Thanks to its fully automated checks, you can maintain continuous compliance and address malicious behavior while gaining visibility into all your risks based on their threat level.
Types of SOC for Cybersecurity Reports:
| Type 1 Report | Type 2 Report |
| The SOC for Cybersecurity Type 1 Report, describes a service organization’s system as it operates on an, at times, point-in-time basis. It verifies whether the organization’s internal controls, as described by them are adequately designed to achieve particular control objectives. This report illustrates your organization’s controls available at a certain date, typically used by first-time issuers as an initial step prior to the Type 2 report. | The SOC for Cybersecurity Type 2 Report, similar to the Type 1 report, is a specific point-in-time report that shares the same information. However, it goes further by adding a management assertion and your auditor’s opinion on how effectively your controls operate. This report provides insights into your organization’s controls over a specific review period, offering a view of their effectiveness. |
SOC Examination
At a high level, a SOC examination is an assessment of the internal controls within a business. Often referred to as a SOC audit, this examination results in the creation of a SOC report.
Businesses rely on these reports, typically generated by independent CPAs, to reassure their clients and partners that they adhere to approved internal controls.
Get compliant faster with automation
Typical timelines for SOC examinations in weeks
If you’re considering a comprehensive process covering readiness assessment, Type 1, and Type 2 examinations, it typically spans from 12 to 15 months on the calendar. This is often the path taken by organizations newly embarking on compliance or introducing a new service or system yet to be evaluated.
However, if you’re repeating a similar effort from a previous SOC audit, your next Type 1 SOC audit should only require about two total calendar months, and your Type 2 would take approximately six total calendar months.
Also, several types of SOC examinations exist, with SOC 1 and SOC 2 examinations being the most common. In the future, it’s anticipated that additional examinations, such as SOC for Cybersecurity and SOC for Supply Chain, will become more prevalent.
Benefits of SOC report
The main benefit of the SOC attestation or report is to assure your clients that you are handling customers and operational data. But that’s not all; you will get to enjoy many more benefits as well, which we have listed below:
- Create trust and transparency with internal and external stakeholders
- Improve efficiencies by reducing compliance costs and time spent on audits and vendor questionnaires
- Address contractual obligations and market concerns through flexible, customized reporting
- Proactively tackle operational risks across the organization
- A “clean” SOC report can set your company apart from competitors in terms of credibility
- A SOC audit can pinpoint areas of weakness in the control environment, enabling improvements to manage risks better
Challenges you may face getting a SOC report
As you can see, although the benefits of getting a SOC report far outweigh, there are still some challenges you may face. Here are some of the challenges you need to pursue:
1. You need to adhere to policy and process consistently
Your adherence to policies and processes will face rigorous testing by the audit team. Failures may result from poor communication, overly simple or complicated policies, or insufficient time to address issues.
This is where you need Sprinto’s help!
Sprinto’s Policy module provides easily deployable policies at your fingertips. You can assemble different policy versions in one central location and automate policy acknowledgment. This saves your infosec team from policy management’s manual strain and stress, reducing the likelihood of gaps and errors.
2. The time it takes for the report to get ready
SOC compliance requires thorough planning, preparation, documentation, testing, and auditing. So, dedicate significant time and resources to align policies, procedures, and controls with SOC criteria.
If you want to reduce your time to get SOC ready, choose Sprinto!
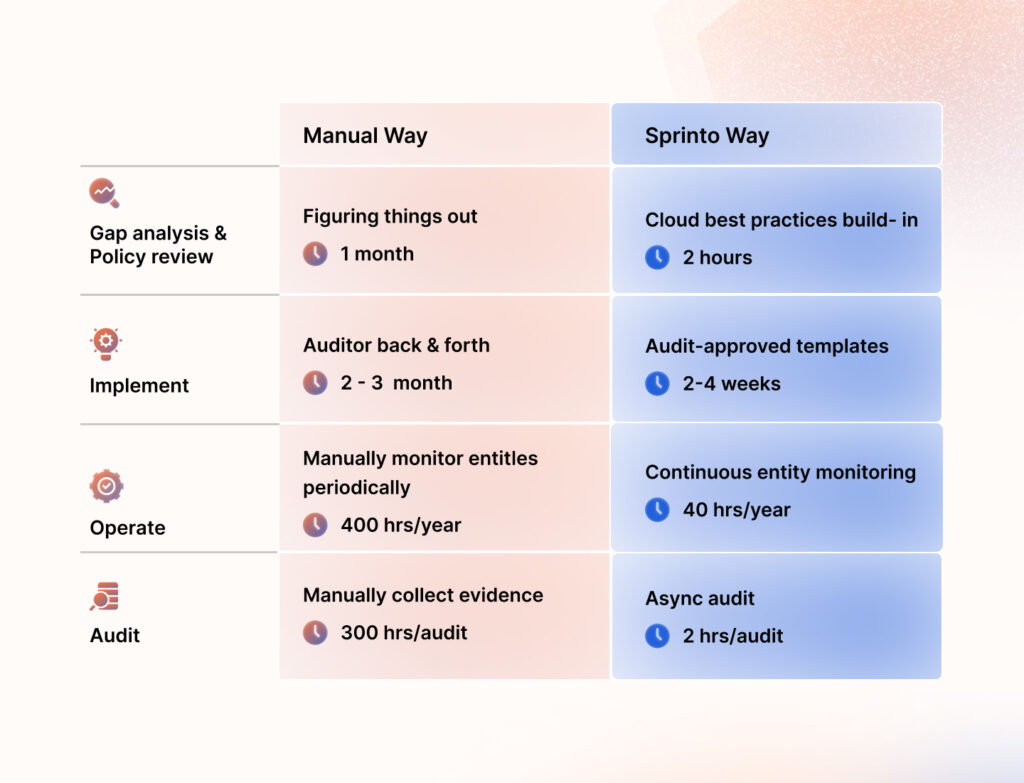
Manual compliance processes require months for monitoring, remediation, and reporting, consuming valuable bandwidth from your team. Sprinto streamlines and accelerates these tasks, allowing you to get a more efficient SOC readiness assessment and process.
3. You don’t have a proper understanding of scope
At its core, a SOC 2 examination aims to ensure that your organization fulfills its commitments to customers, emphasizing the importance of keeping promises.
This extends beyond system boundaries and software, focusing on your organizational commitments and forming the critical basis for scoping your audit.
In determining the proper scope, it’s vital to consider what your organization promises in its services. This aspect becomes the focal point of the SOC audit, influencing your auditor’s opinion not just on security or operations but on the fulfillment of promises.
4. Budgeting for SOC
Getting SOC 2 compliant comes with a price, and grasping the investment in time and money can be intricate. To achieve and sustain compliance, you’ll have to make several investments in tools, technologies, and services.
For example, you might need to invest in purchasing or upgrading your security software, hiring external consultants or auditors, acquiring compliance automation software, and securing penetration testing services.
5. Maintaining a balance between process and technical aspects
Preparation for a SOC 2 audit requires a dual focus on having effective policies and processes to fulfil control and customer requirements and the necessary technical solutions to support these procedures.
It’s common for technical teams to prioritize deploying technology without considering the corresponding processes.
This can lead to a situation where the process aligns more with the needs of the technology than the team’s overall needs. Striking a balance between process and technology is crucial for a successful SOC audit preparation and getting a SOC report.
Conclusion
Enterprises form alliances with service providers to put in place and manage areas such as IT and accounting. But, they need assurance that their chosen partner is trustworthy, secure, and operating according to industry standards.
A SOC report is the “seal of trust” between enterprises and service providers. But it isn’t that easy, especially if you have never got a SOC audit done. It requires advanced planning, teamwork, and coordination.
Use Sprinto to get your SOC 2 certificate with a hassle-free process. Book Personalized Demo with Sprinto
Reprioritize growth. Leave the stress to us.
FAQs
1. When are SOC reports required?
SOC reports establishing trust and confidence in the design and operational efficiency of a service provider’s internal controls.
2. What are SOC reports?
A SOC report is a common compliance standard. It aims to create more transparency, value, and awareness within service organization reporting. There are three types of SOC reports – SOC 1 , 2, and 3.
3. How often are SOC 2 reports required?
Annually SOC 2 audits are required for service providers.
4. Who Manages SOC 2 Reports?
SOC 2 audits are overseen by the American Institute of Certified Public Accountants (AICPA) and require the involvement of an external auditor affiliated with a licensed CPA firm. A company can obtain an official SOC 2 report through collaboration with such auditors, be it a Type 1 or Type 2 report.
5. What is the difference between SOC for cybersecurity and SOC 2?
When comparing SOC for Cybersecurity and SOC 2, it’s essential to note key similarities and differences. SOC for Cybersecurity reports typically encompass the entire entity but may spotlight specific organizational aspects. In contrast, SOC 2 reports specifically concentrate on the sections of a service organization that handle, process, or engage with user data.
Pritesh Vora
Pritesh is a founding team member and VP Growth & Marketing at Sprinto. He comes with over a decade of experience and is a data-driven dynamo in growth strategy, sales, and marketing! His strategies have crafted the success of not one, but two early-stage SaaS startups to 7-digit revenues within a year – he’s your go to guy for all things growth.
Grow fearless, evolve into a top 1% CISO
Strategy, tools, and tactics to help you become a better security leader
Found this interesting?
Share it with your friends
Get a wingman for
your next audit.
Schedule a personalized demo and scale business

Sprinto: Your growth superpower
Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.


