Why Should Companies Invest in Growing Their Cybersecurity Posture?
Meeba Gracy
Feb 02, 2024

Cybercrime is predicted to cost the world a whopping $10.5 trillion annually by 2025, warns Forbes in their latest article.
With diverse and increasingly terrifying cybersecurity challenges in the offing, organizations must invest in protecting their businesses from falling prey to the evolving tactics used by fraudsters.
If you are still undecided or don’t think data breaches and hacks can happen to you, we will tell you why you cannot be more wrong in this article. Read on to know why you should invest in growing your cybersecurity posture.
Why should you invest in growing your cybersecurity posture?
Cyber attacks are on the rise, but the good news is that investing in cybersecurity can safeguard your cloud data and ensure customers that their information is safe.
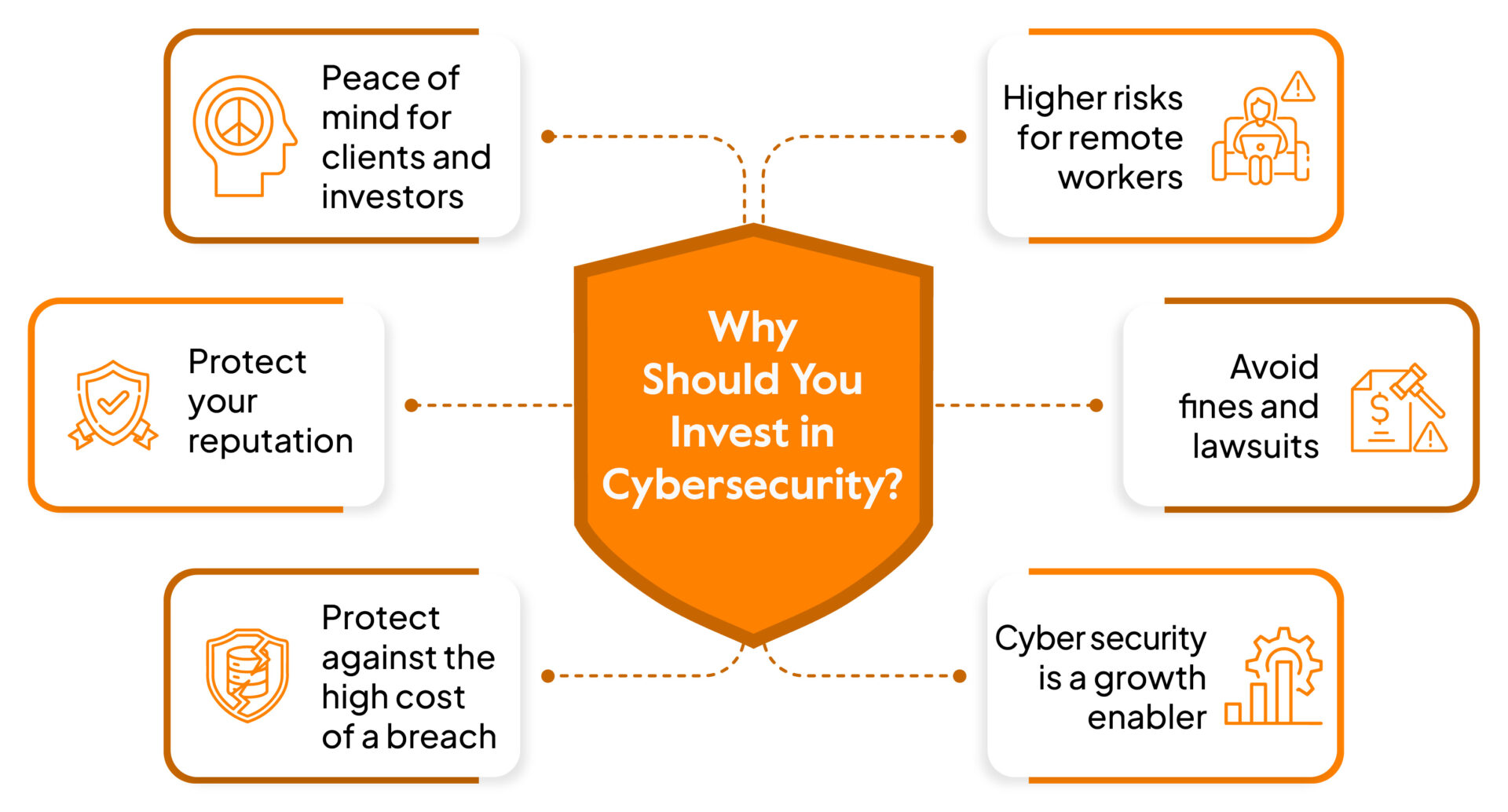
Here are the 7 reasons why you should invest in a cybersecurity posture:
Increasing reliance on cloud infrastructure
At the time, the cloud was considered just a small part of IT infrastructure and referred to some tasks. But the current reality is different, and companies are overly dependent on cloud technologies.
This is especially true with the pandemic and quarantine, which forced a significant shift towards remote working. This made the companies migrate to cloud infrastructure rather quickly to store data over the past year.
According to Fernando Montenegro, an experienced senior principal analyst of Cybersecurity Infrastructure Security Intelligence Service with analyst firm Omdia – one in every four organizations has already managed to shift most workloads to the cloud. Moreover, 44% of workloads are currently running in the public cloud.
But wait, there’s more; many companies rely solely on AWS (Amazon Web Service). Imagine a significant power outage in the cloud computing service; now, this could not only cripple Amazon’s business but also cripple the businesses that solely rely on AWS for all their operations.
This scenario happened on December 7, 2021, when AWS was fully down for the day.
Hence, Increasing reliance on cloud providers such as AWS has meant that organizations can focus on their core competencies while retaining agility. It is, however, important to remember that cloud security is not the same as cybersecurity within an organization.
While CSPs may offer infrastructure and information systems security measures, you have to deploy additional investments into cybersecurity-related solutions if you wish to protect yourselves from external threats.
These investments must go beyond the basic protection offered by CSPs and be tailored to the specific needs of each organization depending on its industry, risk profile and other factors.
Therefore, relying solely on a CSP for security isn’t enough for organizations looking for stronger security coverage; further investments must go into implementing tailored cybersecurity solutions.
Protection from data hacks and breaches
The cost of data breaches can no longer be underestimated. The Ponemon Institute’s (US-based cybersecurity think tank) study painted a grim picture for organizations hit by a data breach–their share prices plummeted as customers churned away in droves, and the organization’s reputation suffered tremendous damage.
These consequences alarm enterprises, making it imperative to take data protection seriously. It is no longer just an IT issue but a problem that requires unified action from everyone- from the boardroom to the shop floor.
The WannaCry ransomware worm demonstrated the damaging potential of unpatched vulnerabilities. Despite Windows releasing a patch to fix this specific zero-day vulnerability, many vulnerable machines could not update quickly enough for the attack to be halted.
Once unleashed, it spread through networks like wildfire and wreaked havoc on hundreds of thousands of organizations worldwide. What made this attack even more chilling was that it could’ve been prevented had machines been patched on schedule and a better incident response plan been adopted.
Although the standard practice of conducting a one-time cybersecurity risk assessment helps pinpoint security risks, it’s essential to have continuous monitoring in place to avoid any gaps in your security program.
The ideal option is to have a Cybersecurity risk assessment which allows security professionals to understand what assets you are trying to protect, the value of data, and infrastructure. Common questions asked during security assessments include:
- What data do you collect?
- How and where are you storing this data?
- How do you protect and document the data?
- How long do you keep data?
- Who has access internally and externally to the data?
- Is the place you are storing the data properly secured?
Hence the best way to avoid this is by doing the following:
Conduct Regular audits
You can validate your security posture by conducting regular audits to identify new gaps in compliance or governance. A security audit is more thorough than a vulnerability assessment or penetration test.
Asset Inventory
Taking stock of your technologies can be the first step to greater security. Knowing what hardware and software you have in place gives valuable insight into potential vulnerabilities that need attention.
An asset inventory is a great way to group assets according to risk factors so that nothing gets overlooked, allowing organizations to prioritize their response plans for maximum effectiveness.
Vulnerability and Compliance Management
Utilizing a Vulnerability and Cyber Compliance Management tool or process can be a great way for organizations to ensure that their systems are configured securely and that all vulnerabilities are identified, prioritized and mitigated.
Without proper vulnerability identification and management, organizations will remain exposed to risk, making VCM integral for securing today’s IT environments.
Train & educate your staff
After outfitting your employees with the knowledge of data privacy and security, you develop a formal security policy for your employees. The document of best practices will ensure that all employees in the organization are on the same page regarding protecting their data from malicious actors.
But knowledge alone is not enough – people need to be informed and educated about these policies before they can truly comply.
That’s why it’s so important to hold regular security training sessions so that everyone is continually updated and aware of what they need to do to keep virtual and physical systems secure.
When establishing your security policy for employees, you might consider training on the following:
- Controlling end-user access to data and applications is essential to cybersecurity. The principle of least privilege (POLP) makes sure that users have only the minimum level of access required to perform their job functions.
- Using different, original passwords for devices used for work.
- A documented system for employees, vendors, and contractors who are leaving the company helps ensure a smooth transition. This system should include how to turn in keys, laptops, access cards, and passwords.
Comply with legal requirements
A compliance framework is essential in any security program, emphasizing this bedrock principle: We Trust but Verify. This viewpoint implies that we must take extra steps to ensure that stated policies, standards, laws, and regulations are followed to issue pertinent attestations and verification.
Such intense effort toward confirming adherence to rules and regulations is significant. Whether on an individual or organizational level, proper compliance catalyzes trustworthiness and authenticity – there is no substitute for diligently obtaining evidence of compliance with the expected standards.
Keeping electronic Protected Health Information (ePHI) secure is an ongoing industry challenge. According to HIPAA and the HITECH act, organizations in the health sector must employ strong access control measures when handling ePHI.
That means monitoring and managing who has access to data while at rest, in use, or in transit – a daunting task even for well-staffed organizations.
These laws are actively audited throughout health organizations to protect patient privacy and personal information to ensure compliance with their requirements.
Payment Card Industry Data Security Standards is created to bring a sense of security and trust to the card industry. They are an important safeguard, providing guidelines and recommendations for organizations that store, process, and transmit cardholder data.
The twelve domains of PCI DSS address how to properly protect cardholder data – from its initial creation until its disposal or demolition.
Many circumstances require specific attention, such as access control, encryption, and network security measures – all of which can be found in the PCI DSS. Collectively, this help verifies that systems are secure and safe from threats or malicious activity.
Growth Enabler
Whether you operate in the financial, pharmaceutical, recruitment, or retail see ctor, it’s becoming clear that a trust-worthy, secure cyber posture is essential for many customers to do business with you.
It’s true – last year, Vodafone conducted a survey where 90% of companies said strong cyber security would help build a positive reputation in the market and draw in more customers while also helping keep them loyal.
In essence, a robust cyber security infrastructure can transform from potential overhead costs into enablers of your business growth. Investments here could pay significant dividends further down the line and be the cornerstone for success.
Firms need to innovate and take risks to stay ahead of the competition. When a company is looking to reap the rewards of being a first-mover in its industry, launch a new product, or expand into uncharted territory, decisive decisions from senior leadership are key.
Without a robust security posture that can keep up with these changes—and any subsequent threats that may result from them—the board’s SWOT analysis will remain incomplete.
Having a secure platform not only gives the company some protection against hacker activity but also provides an extra boost of confidence for their most significant decisions. With such substantial investment in reinforcement, firms can push beyond their limits and reach their fullest potential.
Builds your brand’s trustworthiness
Customer satisfaction is a priority for every company. With modern technology, customers are more aware of their rights and the importance of data privacy.
As they conduct their transactions online, they expect to be protected from cybercriminal activities like phishing scams, identity theft, and other threats to their safety and privacy – making it almost impossible for businesses to thrive without the trust of their customers.

Implementing a reliable cybersecurity system is essential to ensuring customer confidence and trust in your brand; research shows that as much as 40% of shoppers in online stores will discontinue a transaction if they suspect your website’s security is questionable.
After all, this could mean the difference between successful endeavors and incredible losses! Read the case study of how Sprinto helped Data Plant (an Analytics Platform) achieve SOC 2 attestation when the question about data security started arising from the clients.
For instance, a hacker known as ‘UberLeak’ started posting confidential information they had stolen from Uber and Uber Eats on an online hacking forum.
The breached data allegedly includes employee email addresses, corporate reports and even IT asset information from third-party vendors utilized by the company.
On top of that, the hacker also released archived source codes for various mobile device management platforms which both companies used to manage their operations.
It looks like this massive data breach may be another example of Uber’s leadership failing to ensure optimal cybersecurity measures for their employees, customers and service providers.
Avoid fines and lawsuits
No one likes to receive a fine or be the target of a lawsuit, and data breaches are both potential causes for concern. Business owners can take steps to protect themselves in case their company’s private information is ever breached.
For example, according to the data from IBM – the average cost of a data breach in the US has increased from $3.5 million in 2006 to $9.4 million in 2022. This is a nearly 170% increase in 16 years.
Government agencies can impose hefty fines on organizations whose data aren’t properly protected. And even if your organization doesn’t face these fines, you could be sued by affected individuals or other groups who felt their sensitive information was exposed.
Inform yourselves about relevant laws, regulations, and best practices related to data security. For example, ensuring all employees understand privacy policies and the need to keep personal customer device information secure – so your organization is prepared in case of a breach.
Taking extra steps like these can help avoid future fines or lawsuits resulting from compromised data.
Also read: Cyber security best practices
Investing in cybersecurity really isn’t an option anymore. It’s a necessity!
Despite the challenges of scaling a cybersecurity program, the payoffs are well worth it for companies that invest. Growing your company’s cybersecurity posture will help you build trust with customers, prospects, and partners and foster a security culture throughout your organization.
And when done right, an effective cybersecurity program can be a competitive differentiator for your business. If you’re ready to take your company’s cybersecurity posture to the next level, we can help.
Our team of experts can partner with you to assess your current state, identify gaps and develop a road map for improvement with the right security frameworks. Contact us today to get started.
Meeba Gracy
Meeba, an ISC2-certified cybersecurity specialist, passionately decodes and delivers impactful content on compliance and complex digital security matters. Adept at transforming intricate concepts into accessible insights, she’s committed to enlightening readers. Off the clock, she can be found with her nose in the latest thriller novel or exploring new haunts in the city.
Grow fearless, evolve into a top 1% CISO
Strategy, tools, and tactics to help you become a better security leader
Found this interesting?
Share it with your friends
Get a wingman for
your next audit.
Schedule a personalized demo and scale business

Sprinto: Your growth superpower
Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.


