
Say your SOC 2 report expired yesterday but the customer’s financial reporting period extends beyond the validity. Does it imply a weak security posture in the gap period or lost compliance status? Definitely not. But your clients will need some kind of solid document in the absence of an audited assurance. Enter SOC 2 Bridge letter.
A SOC 2 Bridge letter acts as an interim assurance when there’s a need to bridge the gap between your SOC report and the customer’s year end. Read on to find answers to the most common questions about bridge letters and more.
What is a SOC 2 bridge letter?
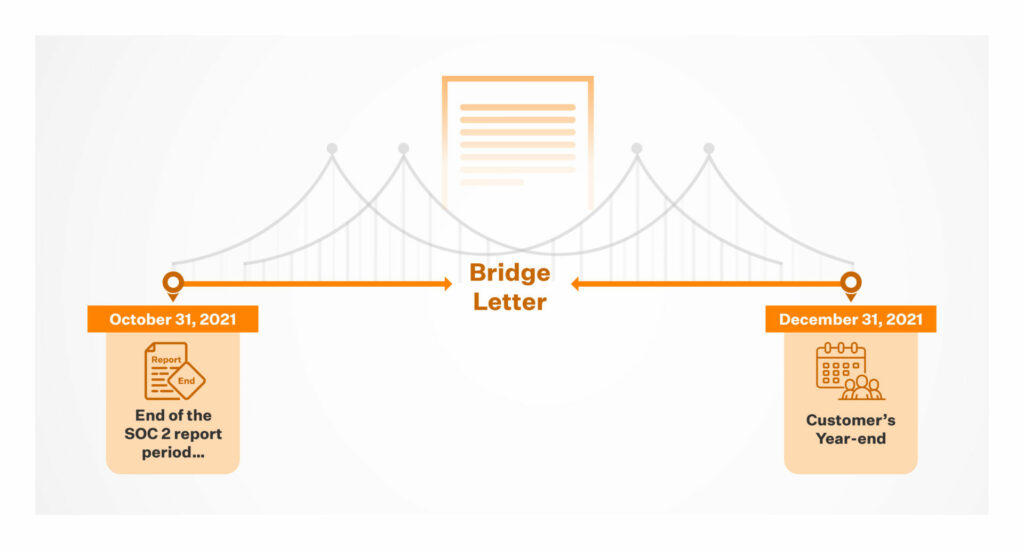
A SOC 2 bridge letter, also known as a gap letter, is a document provided by a service organization to assure customers of continued compliance with SOC 2 controls. It’s valid between the end date of the last SOC 2 audit report and the start of the next audit or the end of the customer’s fiscal year. It serves as a temporary attestation that the organization’s controls remain effective, addressing short gaps (typically 1 to 3 months) when a new SOC 2 report is not yet available.
It assures your customers of your organization’s continued security posture, and that there have been no material changes in your internal controls that could adversely affect the conclusions arrived at in the earlier SOC 2 report.
Automate SOC 2 compliance with the help of Sprinto. Talk to our experts now
What’s included in a SOC 2 Bridge Letter?
Although the AICPA’s SOC 2 compliance guidance doesn’t specifically talk about bridge letters, it’s a good practice to include the following components in the bridge letter SOC report:
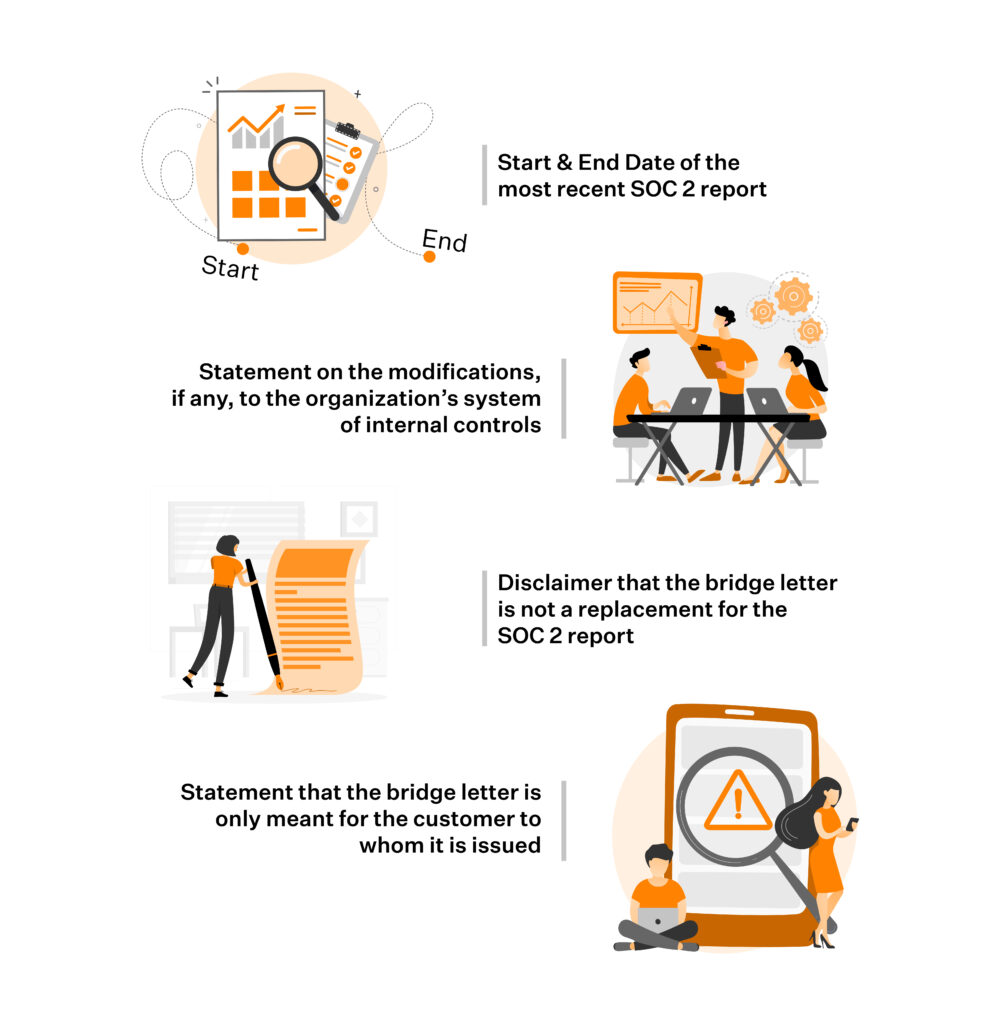
- Start and End Date of your most recent SOC 2 attestation.
- A statement on the modifications or changes made, if any, to your organization’s system of internal controls since the end date of your most recent SOC report; an explanation of the changes made since the audit.
- In case of no changes, include a statement that the organization is unaware of any material changes that might affect the auditor’s opinion.
- Disclaimer that the bridge letter is not a replacement for the SOC 2 report.
- A statement that the bridge letter is only meant for the customer to whom it is issued and no other entity.
- The final paragraph of a gap letter should reiterate your organization’s commitment to constantly evaluating and upgrading physical and cloud-based technology and information security controls and procedures.
SOC 2 Bridge Letter Sample: Download Template
Here’s a SOC 2 Bridge Letter example for your reference.
Download Your SOC 2 Bridge Letter Sample
You could also share an accompanying copy of your last SOC 2 report with your customer, so they can refer to it. However, note that you cannot use a gap letter to replace your SOC 2 audit report.
Get SOC 2 ready in no time with the help of Sprinto. Let’s talk!
Who issues a SOC 2 Bridge Letter?
Upon request, the management of the service organizations can issue bridge letters to their customers. The auditor (or CPA firm) that conducted your SOC 2 audit doesn’t publish these letters.
For one, they aren’t in a position to hold any opinion on your internal controls’ design and operating effectiveness outside the SOC 2 report period. Two, they aren’t aware of any material changes the service organization may have made to their system of internal controls.
For instance, if a service organization adds a new SaaS application or changes its DevOps software package outside its audit window, the auditor cannot attest to its continued compliance.
Therefore, only the management of the service organization that knows material changes (if any) can issue these bridge letters.
Duration of a SOC Report Bridge Letter
For how long is a bridge letter valid? SOC bridge letters cover short durations to bridge the gaps between SOC 2 reports or between the end date of a SOC 2 report period and the date on which a customer requests the bridge letter. Thus, a bridge letter typically covers no more than three months.
In cases where a bridge letter is needed for more than three months, you might want to perform another SOC 2 audit or revisit the examination period with the service auditor.
It is, therefore, advisable to complete the annual SOC audits on time to establish continued trust in the strength of your internal controls.
What is the importance of the SOC 2 bridge letter?
The importance of a SOC 2 bridge letter includes:
- Ensures continuity of trust by confirming ongoing SOC 2 compliance during gaps between audit reports.
- Addresses client and regulatory needs for up-to-date assurance on control effectiveness.
- Maintains business relationships by providing interim evidence of security and compliance.
- Reduces compliance risks for clients relying on SOC 2 reports for due diligence.
- Supports transparency by disclosing any significant control changes since the last audit.
- Facilitates vendor management by bridging short-term gaps (1–3 months) until the next SOC 2 report.
Importance of SOC 2 Bridge Letter for Vendor Relationship
Even though SOC bridge letters aren’t a replacement for SOC 2 audit reports, they make for a nifty stop-gap measure in the interim. The importance of bridge letters for vendor relationships cannot be overemphasized.
For one, they reassure your customers and prospects about your information security posture in the interim period. Two, it saves time and cost, and helps you remain a trusted vendor in your customer’s ecosystem.
Overall, bridge letters make for a smart way to maintain customer confidence and trust, and, consequently, future sales.
What’s Next?
As we can see, a SOC 2 bridge letter is an essential document and contains the necessary proof to demonstrate full compliance with the standard. Compliance does not have to be complicated or time-consuming, especially with a comprehensive platform like Sprinto, which helps organizations manage the process from end-to-end.
Our automated solution is built to make managing evidence easier than ever and our intelligent continuous monitoring feature will help ensure that you stay up-to-date on your controls and any new standards. If you have been facing difficulty in keeping up with these requirements, then why not try something new and book a demo with us?
See for yourself how Sprinto’s solution can help you keep your policies compliant in a simpler, faster way than ever before!
FAQs
What is the SOC report bridge letter?
A SOC report bridge letter is an assurance document for stakeholders that covers the interim period between the organization’s last SOC 2 audit report and the next report. It is intended to satisfy the customers about the effectiveness of organization’s internal controls between the gap period.
Do you need a bridge letter?
A bridge letter is not frequently needed but is a good document to have in case the clients require an interim assurance of SOC 2 control integrity and the organization is waiting for the report.
What is a SOC 2 engagement letter?
A SOC 2 engagement letter is a contractual agreement between the service organization and the auditing firm outlining the terms and conditions of the SOC 2 examination such as scope of services and applicable Trust Services Criteria.
What is the maximum period of a bridge letter?
While there is no minimum or maximum period defined for a bridge letter, it mostly covers for a SOC 2 report for no more than 3 months.
Is a SOC 1 bridge letter the same as a SOC 2 gap letter?
A SOC 1 bridge letter and a SOC 2 gap letter serve similar purposes but are not the same. Both are interim documents issued by a service organization to assure clients of continued compliance during the period between audit reports.
Meeba Gracy
Meeba, an ISC2-certified cybersecurity specialist, passionately decodes and delivers impactful content on compliance and complex digital security matters. Adept at transforming intricate concepts into accessible insights, she’s committed to enlightening readers. Off the clock, she can be found with her nose in the latest thriller novel or exploring new haunts in the city.
Explore more SOC 2 articles
SOC 2 Compliance Overview
SOC 2 Preparation and Documentation
SOC 2 Audit and
Reporting
SOC 2 Differences and Similarities
SOC 2 Updates & Management
SOC 2 Industry-Specific Applications
research & insights curated to help you earn a seat at the table.








