SOC 1, SOC 2, and SOC 3 are independent attestation reports that help organizations prove they have reliable security, privacy, and internal controls in place. Although they originate from the same AICPA framework, each report serves a distinct purpose: SOC 1 focuses on financial reporting controls, SOC 2 evaluates security and trust principles, and SOC 3 is a public-facing summary of controls.
Each report covers different types of controls, and is intended for different audiences. Because of this, companies often struggle to understand which report they need, when they need it, and how each one supports customer and compliance requirements.
This guide breaks down what each SOC report covers and when organizations typically need them.
Quick Summary: SOC 1 vs SOC 2 vs SOC 3
| SOC 1 | SOC 2 | SOC 3 | |
| What it covers | Financial controls | 5 Trust Services Criteria | Public security summary |
| Who’s it for | Finance auditors | Customers & prospects | General audience |
| Report detail | Detailed | Detailed | Minimal |
| Use Case | Financial impact services | Security assurance | Marketing proof |
Types of SOC reports
SOC is a verifiable auditing report performed by a Certified Public Accountant (CPA) designed by the American Institute of Certified Public Accountants (AICPA) concerning the systematic controls in place at a service provider, including:
- Data privacy
- Cybersecurity
- Confidentiality
- Processing integrity
- Controls related to financial reporting
SOC reports help establish more credibility for you — a competitive advantage worth both monetary and time investments. There are three types of SOC reports — SOC 1, SOC 2, SOC 3 — wherein SOC 1 and SOC 2 are the most used.
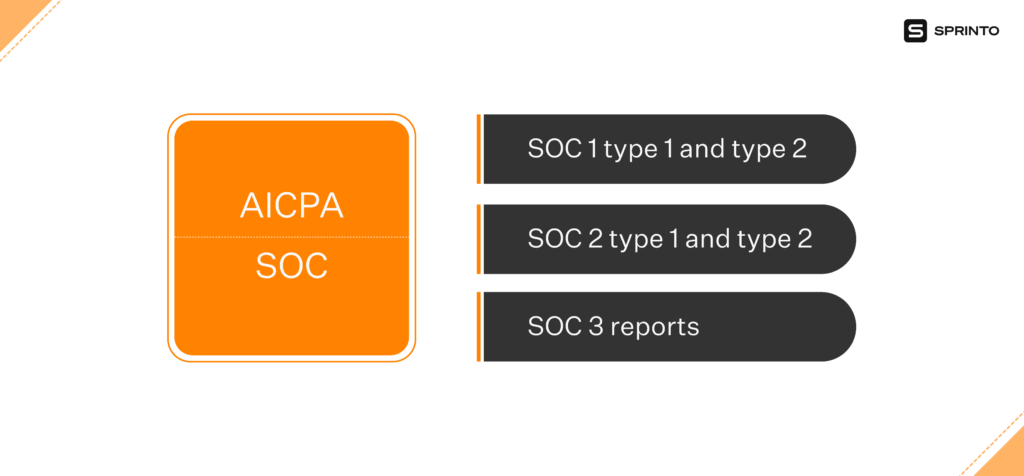
The main difference between SOC 1 and SOC 2 is that the former focuses on financial reporting and the latter on operations and compliance. Whereas SOC 3 is less common and is a variation of SOC 2, designed for the company’s clientele.
Save 80% of man hours spent on SOC 2
Difference between SOC 1 vs SOC 2 vs SOC 3
Each SOC report—SOC 1, SOC 2, SOC 3—fulfills distinct roles within compliance assessments. SOC 1 primarily focuses on an organization’s internal financial controls, while SOC 2 and SOC 3 assess controls related to the Trust Services Criteria. Also, SOC 3 serves as a public-facing demonstration of an entity’s control effectiveness, in contrast to SOC 2’s more confidential nature among SOC report types.
Here is a quick difference between SOC 1 vs SOC 2 vs SOC 3:

So, now that you know the overview of SOC 1 vs SOC 2 vs SOC 3, let’s dive further into each report.
Everything you need to know about SOC 1
Developed mainly for third-party service providers by the AICPA, a SOC 1 report gives your company’s clients assurance that their financial information is being handled safely and securely.
What is SOC 1?
SOC 1 is an attestation report issued under SSAE 18 that evaluates how well a service organization’s controls support accurate and reliable financial reporting for its customers. In simple terms, it examines whether your systems and processes handle financial-related data correctly and consistently. SOC 1 is focused entirely on controls that could influence a customer’s financial statements.
What SOC 1 Covers
SOC 1 reviews internal controls that relate directly to financial reporting. This includes operational, IT, and security controls that can affect how financial data is processed, stored, transmitted, or reported. Key areas include:
- Transaction processing controls (accuracy, completeness, timeliness)
- Billing, invoicing, payment, and settlement workflows
- Input, processing, and output accuracy for financial data
- Logical access controls impacting financial systems
- Change management affecting financial applications
- Data integrity safeguards for financial reporting
- Reconciliation, exception handling, and error correction processes
SOC 1 Type I vs SOC 1 Type II
There are two types of SOC 1 reports: Type I and Type II. Both assess the same financial reporting controls, but they differ in what they validate. A SOC 1 Type I report reviews whether your controls are designed effectively at a specific point in time, making it a good starting point for organizations undergoing their first audit or establishing baseline assurance.
A SOC 1 Type II report evaluates whether those controls operate effectively over a period of 3–12 months. This provides stronger evidence of consistency and reliability, which is why customers—especially enterprise teams—commonly request Type II. Many companies begin with Type I and move to Type II as their processes mature and customer expectations increase.
Who Needs SOC 1?
SOC 1 is necessary for service providers whose systems or processes can impact their customers’ financial reporting. It is commonly required in industries where financial accuracy is critical.
Organizations that typically need SOC 1 include:
- Payroll processors
- Payment processors and payment gateways
- Billing, invoicing, and subscription management platforms
- Fintech and financial operations tools
- Claims processors and insurance administrators
- Loan servicing and mortgage management platforms
- Revenue cycle management systems
- Any service that feeds data into customer financial statements
Please Note

SOC 1 audit reviews internal controls over financial reporting rather than a review of your financial statements.
Benefits of SOC 1 compliance
SOC reports help your clients acquire an objective evaluation of the effectiveness of controls that address the operations, compliance, and financial reporting processes of your organization. It:
- Assures your clients that their sensitive data is protected
- Evaluates policies and procedures that are key to your company’s operability
- Verifies that you have proper internal controls and processes in place to deliver high-quality services to your clients
When to get SOC 1 compliance?
If you are a new business, SOC 1 is not likely to be on your radar. However, the timing of your compliance is essential, as you do not want to be scrambling to get certified when a deal is in jeopardy. Here are three SOC 1 report examples:
- Your client asks for a “right to audit”
- Your company is going to be publicly traded
- You need to apply with another regulation (e.g., SOX)
See exactly which SOC audit your business needs
👉 Talk to experts →
Everything You Must Know About SOC 2
While SOC 1 focuses on financial reporting controls, the SOC 2 framework shifts the focus to how well an organization protects customer data and system security.
What is SOC 2?
SOC 2 is an attestation report that evaluates how well an organization protects customer data using the AICPA’s Trust Services Criteria (TSC). Unlike SOC 1, which focuses on financial reporting, SOC 2 is centered on security, privacy, and operational controls.
It is the most widely requested security assurance report for SaaS companies, cloud services, and any business that stores or processes customer data. SOC 2 helps customers understand whether your systems are secure, reliable, and designed to safeguard information.
What SOC 2 covers
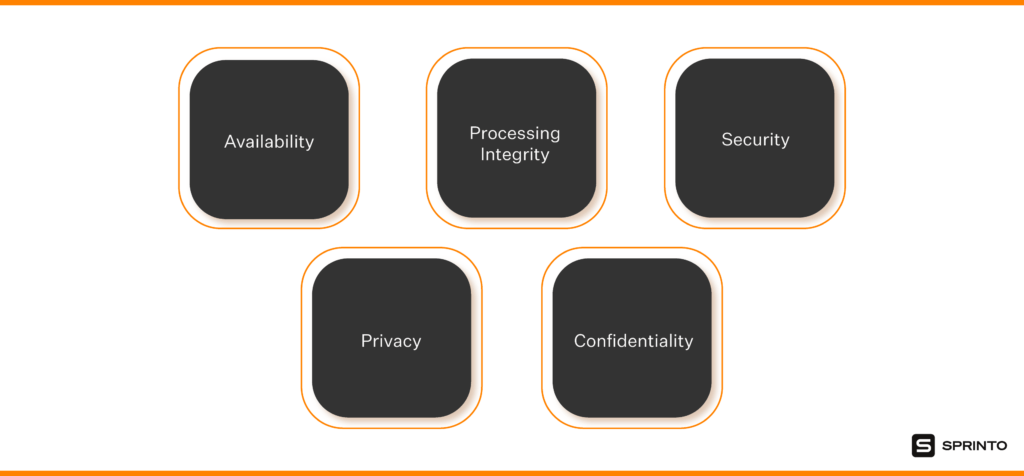
SOC 2 evaluates an organization’s controls using the AICPA’s Trust Services Criteria (TSC). These criteria define how securely and reliably a system should operate. Every SOC 2 report must cover Security, while the remaining principles are included based on the nature of your services.
SOC 2 covers the following areas:
- Security (mandatory): Preventing unauthorized access through controls like authentication, monitoring, access reviews, network protections, and secure configurations.
- Availability: Ensuring systems stay operational through incident response, uptime monitoring, redundancy, and continuity planning.
- Processing Integrity: Ensuring systems process data accurately, completely, and on time.
- Confidentiality: Protecting sensitive information using encryption, restricted access, and secure data handling.
- Privacy: Governing how personal data is collected, used, stored, and disposed of according to privacy commitments.
Together, these principles give customers a complete view of your security posture and how you safeguard the data they entrust to you.
Types of reports under SOC 2
Similar to SOC 1, SOC 2 also has Type I and Type II reports. SOC 2 Type I compliance audit covers design controls’ suitability and effectiveness and provides a point-in-time snapshot of the organization’s controls.
On the other hand, SOC 2 Type II compliance audit looks at the effectiveness of the same controls over a period, say, six months or a year, and takes longer for service providers to prepare for it.
Benefits of SOC 2 compliance
A SOC 2 audit plays a crucial role in regulatory oversight, corporate governance, and internal risk management processes. Any client that needs detailed information and assurance about the controls deployed at the service organization may request a SOC 2 audit.
SOC 2 compliance ensures:
- Your company’s information security measures align with the evolving requirements of data protection in the cloud.
- You have the infrastructure, tools, and processes to protect your clients’ sensitive information from unauthorized access.
- Your system maintains high availability, and their processing occurs as intended on time.
Talk to our experts if you are looking to get SOC 2 compliant
When to get SOC 2 compliance
The marketplace will influence how much you need to be compliant for SOC 2. The bigger the client you pursue, the more likely you will need it. If you process or host non-financial data, you should pursue SOC 2 at some point.
Please note that SOC 2 is not required by big-time compliance frameworks like PCI DSS or HIPAA. However, with the number of data breaches, enterprises especially will want to see SOC 2 compliance before finalizing a deal.
Who cares about SOC 2 compliance
Unlike SOC 1, where the report is prepared for the clients’ auditors and controller’s office, SOC reports are shared by the service providers, under an NDA agreement, with the clients, managers, and regulators.
Who should go for SOC 2 auditing
Companies that should go for SOC 2 audit include services such as data hosting and processing, cloud storage, colocation, and SaaS.
If you are a service provider storing, processing, or transmitting any information, you may need to get compliant to gain a competitive edge in the market, much like the decision to have an ISO 27001 certification.
SOC 2 audits may also be performed as part of your regular security program or if you suspect a data security issue.
Moreover, if you do not materially impact your clients’ Internal Control over Financial Reporting (ICFR) but do provide critical services to them, you will need to be SOC 2 compliant.
You must opt for a SOC 2 audit, post preparing for all the SOC 2 requirements. Here’s some help:
Prepare for audits faster, download the SOC 2 Checklist
To know more about Sprinto’s work – Check out our case studies
How Sprinto enables SOC 2 Compliance
Acquiring SOC 2 Type 2 certification requires at least six months of meticulous planning and implementation if done independently. However, Sprinto’s compliance automation significantly reduces this timeframe. Here’s how we expedite your journey towards certification:
- Automating 90% of compliance tasks, Sprinto allows focus on core business goals while ensuring efficient compliance.
- Supporting 100+ integrations, Sprinto facilitates seamless setup of controls for all cloud applications.
- The intuitive dashboard offers real-time insights into control statuses and security adherence.
- Prompt notifications for irregularities ensure swift action on security gaps or missed training.
- Continuous 24/7 monitoring conducts over a million monthly checks, ensuring ongoing control assessment for cloud services.
Over the next two weeks, StepSecurity completed its audit in 4 weeks and received SOC 2 Type 1 audit report. “Thanks to Sprinto, we pulled it off with such finesse!” adds Ashish, Founder of StepSecurity.
Everything You Must Know About SOC 3
While SOC 2 reviews data security and system-level controls, SOC 3 serves as a publicly shareable summary of the same criteria and parameters without divulging audit findings or sensitive information.
What is SOC 3?
SOC 3 is a high-level, publicly shareable version of a SOC 2 report. It is based on the same Trust Services Criteria as SOC 2 but excludes sensitive details such as control descriptions, testing procedures, and audit results.
Because of its simplified, non-technical format, SOC 3 is designed for broad distribution and is commonly used as a trust-building asset on websites, sales pages, and marketing materials.
In comparison to SOC 2, According to the AICPA, a SOC 3 report is prepared to meet the requirements of those who want assurance about the controls — related to security, processing integrity, availability, confidentiality, or privacy — of a service provider but do not need the knowledge to use a SOC compliance report effectively.
In simple words, SOC 3 comprises the same information found in SOC 2, but it is drafted to be presented to a general audience.
Businesses often use SOC 3 reports to post on their website, along with a stamp or seal that indicates compliance. A SOC 3 report is always a Type II, and the auditor testing of controls is not described in the report.
What SOC 3 covers
SOC 3 covers the same five Trust Services Criteria used in SOC 2—Security, Availability, Processing Integrity, Confidentiality, and Privacy—but at a summary level. Instead of reviewing each control or test result, SOC 3 simply provides the auditor’s conclusion that the organization met the SOC 2 requirements.
In practical terms, SOC 3 tells readers:
- The organization was assessed against the Trust Services Criteria
- The auditor found the controls to be suitably designed and effective
- The organization maintains strong security practices
But it omits details such as exceptions, evidence, system configurations, or audit scope specifics.
This makes SOC 3 safe for public sharing and useful for non-technical audiences who want validation without extensive detail.
Types of SOC 3 reports
Just like SOC 2, SOC 3 is available in both Type I and Type II formats. A SOC 3 Type I report provides assurance that the organization’s controls are designed effectively at a specific point in time, while a SOC 3 Type II report demonstrates that those controls operated effectively over a defined period, usually 3 to 12 months.
Even though both follow the same underlying audit rigor as SOC 2, the difference between Type I and Type II is less apparent to readers because SOC 3 presents only a high-level summary rather than detailed test results or control descriptions.
When to get SOC 3 compliance
Any time you want to add another layer to your company’s marketing, you can do a SOC 3 audit to showcase your commitment to excellent service. Look at SOC 3 auditing as a way to reinforce your SOC compliance report’s results.
It is considered a brilliant marketing tool to attract new customers who instantly recognize the stamp of approval from a credible third-party auditor.
Who cares about SOC 3 compliance
This report is designed for those who want assurance on your company’s controls but do not have the expertise or knowledge to understand the detailed and comprehensive SOC report. A SOC 3 report is easy to understand by the general public.
Who should go for SOC 3 auditing
If you are a cloud service provider (SaaS, PaaS, IaaS) housing third-party data, a data center colocation facility, or an IT systems management and you want to communicate your controls effectively minus the complexity of a report, in that case, SOC 3 auditing is for you.
How to choose the right SOC audit for your business?
Choosing the right SOC report depends on what your service does and the kind of assurance your customers expect.
- Choose SOC 1 if your service impacts customers’ financial reporting, such as payroll processing, billing, payments, or any system tied to financial statements.
- Choose SOC 2 if you handle or store customer data and need to demonstrate strong security, availability, confidentiality, processing integrity, or privacy controls. This is the standard for SaaS and cloud companies.
- Choose SOC 3 if you want a publicly shareable, high-level summary of your security posture without revealing sensitive audit details. Ideal for marketing and trust pages.
Most companies start with SOC 2 for customer assurance, add SOC 3 for public visibility, and use SOC 1 only when financial processes are involved.
Get SOC 2 certified with Sprinto in 4 simple steps
Sprinto is an AI-native GRC platform that helps businesses manage compliance, risk, audits, and vendor oversight all in one connected system. It integrates across your tech stack and automates key workflows to keep you continuously compliant, audit-ready, and in control.
Sprinto’s AI automates setup, monitors risks, flags issues, and assists with audits — reducing manual effort and enabling faster, more reliable compliance.
Here’s how Sprinto helps you get SOC 2 certified:
1. Integrate your tech stack
Sprinto integrates with your cloud, identity, code, and device systems in minutes no manual work or third-party tools needed. 300+ native integrations ensure full visibility from day one.
2. Set up your SOC 2 program with AI
Sprinto automatically maps SOC 2 criteria to your environment. Controls, policies, and checks are pre-mapped using AI, and continuously monitored reducing setup time from weeks to hours.
3. Monitor compliance and fix gaps early
Sprinto’s AI monitors your systems in real time, flags failed checks, identifies missing or outdated evidence, and helps you resolve issues proactively not at audit time.
4. Complete your audit with confidence
Sprinto prepares your audit environment with clean, validated evidence. It supports your chosen auditor, reduces back-and-forth, and provides audit-ready summaries and dashboards to speed up the review.
Why companies choose Sprinto
- AI-native compliance: Automate 90% of compliance work, from setup to audit
- Single platform: Manage SOC 2, ISO 27001, GDPR, HIPAA, PCI-DSS, and 200+ frameworks
- No consultants needed: Out-of-the-box policies, controls, and auditor-grade workflows
- Scales with you: From first audit to multi-framework GRC programs
- Proven at scale: Trusted by 3,000+ companies across 75 countries
As you know, when we started our first company and had to get a SOC 2 attestation while running the business, we spent months and tens of thousands of dollars in the process.
We soon realized that there were many companies facing the same issue and so Sprinto came into existence with a mission to help companies get their SOC 2 compliance certificates with little hassle.
SOC 2 auditing is complicated as it requires you to implement numerous security policies. Piecing together policies and procedures from the internet with dense language can be quite a hassle. Unlike generic compliance platforms, Sprinto is designed specifically for cloud-based companies.
Here is how you can get your SOC 2 certification in just four steps:
1. Connect your systems
Sprinto integrates with a wide range of systems, which takes just minutes to get all set up.
2. Bespoke to your needs
Sprinto is designed to meet your company’s specific needs. Once integrated, the tool continuously monitors your systems and gathers evidence, further cataloging the evidence as per SOC 2 criteria via standard read-only API access. Thanks to managed implementation by Sprinto’s compliance experts, this step is a breeze.
3. Tend to alerts
Once the platform is up and running, Sprinto detects new gaps and sends trigger alerts for you to fix them.
4. Pick an audit partner
Sprinto does the heavy-lifting for you and partners with accredited (AICPA/ISO) third-party audit firms to conduct your audits. It also trains auditors on the platform, so you get a hassle-free experience.
FAQs
SOC 3 is a curtailed, publicly sharable version of the SOC 2 Type 2 report. SOC 3 is meant for a general audience and is hosted by organizations on their websites, whereas SOC 2 report is confidential and circulated on a need-to-know basis to stakeholders.
SOC 2 Type 2 report is the basis for the SOC 3 report. While SOC 2 is detailed, private and meant for a knowledgeable audience, SOC 3 is the public version of SOC 2. It is meant for a general use purpose audience.
SOC 3 reports are meant for general audiences who need assurance regarding the security, availability, confidentiality, processing integrity or privacy of an organization.
SOC reports can be categorized into two main types: SOC 1 and SOC 2. SOC 1 primarily concerns controls that affect financial reporting, especially important for service organizations impacting clients’ financial statements.
On the other hand, SOC 2 assesses controls related to security, availability, processing integrity, confidentiality, and privacy, showing how well controls operate in systems beyond financial reporting areas.
The key difference between SOC 2 and SOC 3 reports is their confidentiality and detail level. SOC 2 reports provide in-depth, confidential information about a company’s systems and audits, shared only with specific parties upon signing non-disclosure agreements. In contrast, SOC 3 reports offer less detail and are non-confidential, designed for public distribution, and often used as marketing materials.
Pritesh Vora
Pritesh is a founding team member and VP Growth & Marketing at Sprinto. He comes with over a decade of experience and is a data-driven dynamo in growth strategy, sales, and marketing! His strategies have crafted the success of not one, but two early-stage SaaS startups to 7-digit revenues within a year – he’s your go to guy for all things growth.
Explore more SOC 2 articles
SOC 2 Compliance Overview
SOC 2 Preparation and Documentation
SOC 2 Audit and
Reporting
SOC 2 Differences and Similarities
SOC 2 Updates & Management
SOC 2 Industry-Specific Applications
research & insights curated to help you earn a seat at the table.