How To Get SOC 2 Audit For Small Businesses
Payal Wadhwa
Feb 24, 2024
As a forward-looking small business aiming to attract large and enterprise clients, Know that questions about the security makeup and overarching security practices come up in most sales conversations. A SOC 2 audit then becomes a single source of truth for validating the effectiveness of security infrastructure, controls, and personnel.
Integrating SOC 2 audits in your cybersecurity arsenal is crucial for maintaining a strong defense against threats and moving stronger on the growth trajectory.
This blog goes all in on SOC 2 audits for small businesses: importance, process, timeline, and costs.
SOC 2 audit for small business: An overview
A SOC 2 audit is an independent evaluation of an organization’s internal controls to ensure the protection of customer data or any sensitive information. The AICPA’s five trust service categories (security, availability, confidentiality, processing integrity and privacy) serve as the foundation for conducting SOC 2 audits.
Any medium or enterprise client entrusting its data with a small business would still want a validation of a robust cybersecurity system in place. Therefore, SOC 2, while typically associated with larger organizations, is highly recommended even for small businesses.
The SOC 2 audit for small business is mostly like that of larger organizations. However the differences are in scope, resources, security maturity and third-party relationships that must be considered.
The audit process for small businesses includes in-depth planning, meticulous implementation, formal audit and reporting. The business can seek SOC 2 Type 1 or Type 2 reports depending upon the requirements and duration.
Get Our Practical SOC 2 Guide;
Yours at No Cost

Importance of SOC 2 audit for small business
A SOC 2 report provides an audited assurance of a formal information security policy and tight security controls implemented by businesses to protect customer data from distortion or unauthorized access.
SOC 2 audit is essential for small businesses that handle sensitive data and need to meet regulatory requirements. These can include cloud service providers, SaaS providers, payment processors, electronic health record providers etc. Additionally, it helps build market credibility and tighten internal security controls.
Here’s why a small business must undergo a SOC 2 audit:
Elevates customer & partner satisfaction
To ensure repeat business, higher sales, reduced costs and build brand reputation, it’s crucial to maintain the trust of existing clients and partners. Getting a SOC 2 audit demonstrates the effectiveness of controls implemented by an organization and helps retain already established customers for long-term success.
Unlocks enterprise acquisition opportunities
Pitching to an enterprise client means getting showered by questions like: “How do you ensure data security?” “Are you SOC 2 compliant?”. Nevertheless, these questions are justified because every business wants its sensitive information to be protected.
Getting a SOC audit helps gear up for enterprise readiness and unlocks new opportunities.
Helps address internal control weaknesses
A SOC 2 audit process is comprehensive and requires rigorous identification and addressing of gaps in internal controls. This helps in tightening the security stance of the organization and reduce risk of cyber incidents and data breaches.
Reduces vendor questionnaire burden
A number of small businesses have to undergo a time-consuming and resource-intensive exercise of filling lengthy security questionnaires from vendors. Getting a SOC 2 audit replaces this with a standardized document about security controls as the single source of truth and expedites vendor onboarding process.
Also check out this video on SOC 2 2023 update:
Steps to prepare for SOC 2 audit for small business
An audited assurance for a rock-solid compliance posture is not an easy feat. It’s an arduous process that requires sifting through numerous documents, some painstaking implementation, and an ever-vigilant eye for ensuring things are moving right.
Here are the detailed steps for preparing for a SOC 2 audit for small business:
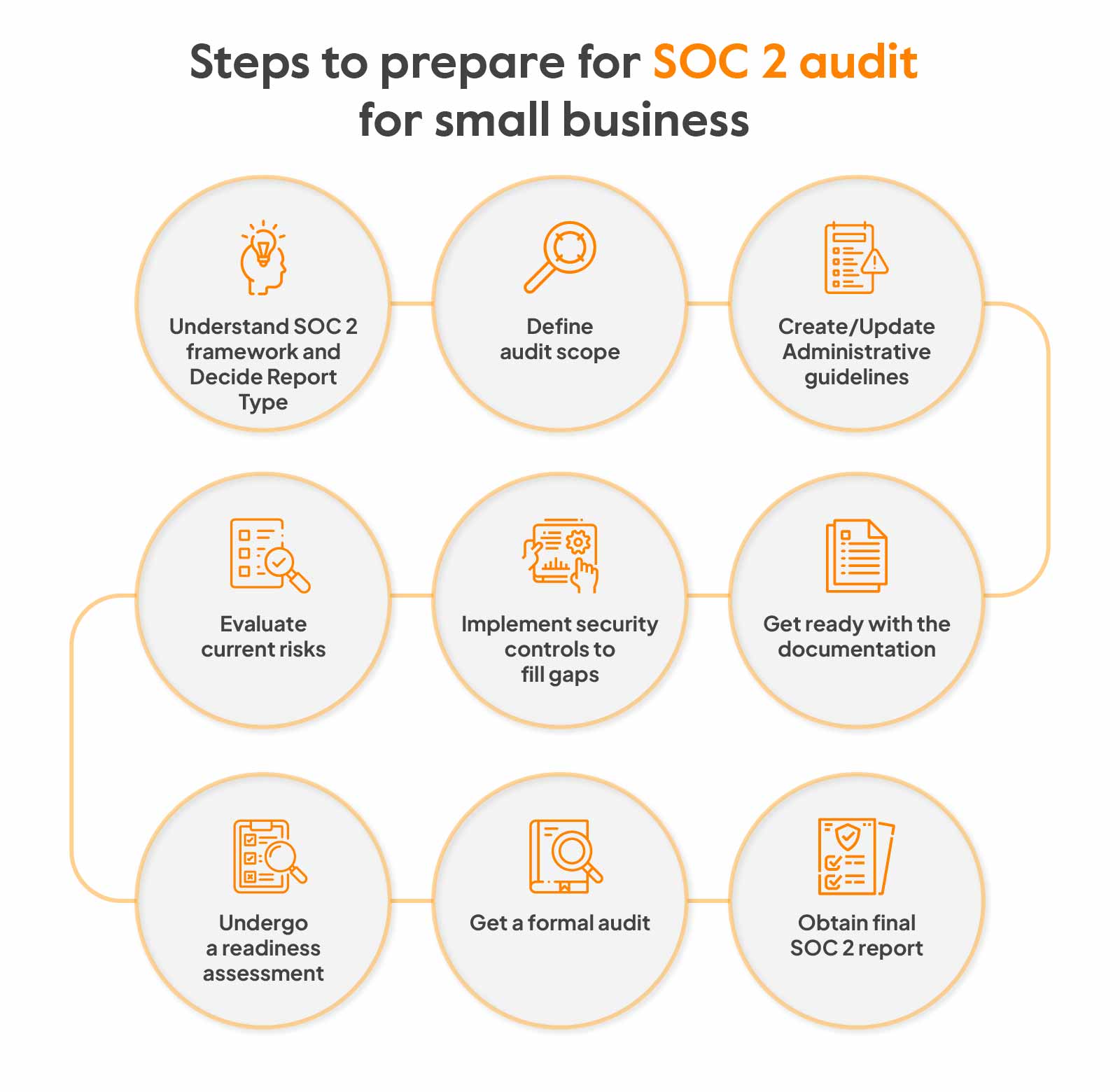
Understand SOC 2 framework and Decide Report Type
Getting familiar with the SOC 2 framework and 5 trust categories (security, availability, processing integrity, confidentiality and privacy) will help you pick the criteria that are applicable to the business. Thereafter, detailed requirements of the criteria must be studied to have a roadmap of what needs to be accomplished.
Also, decide on the report type. If there’s urgency, SOC 2 Type 1 report can be obtained. It takes less time and can help give a helicopter view of how good your systems have been designed. Type 2 gives actual assurance about security controls with details.
Define audit scope
The audit scope sets the audit limits. It establishes clarity on the systems, processes and controls that need to be audited. This decision can be based on a number of factors like overall business objectives, regulations that apply, processes, reliance on third-party vendors, information assets etc.
Create/Update Administrative guidelines
Administrative policies and standard operating procedures (SOPs) as per business size, structure, workflows and operations must be created or updated. These policies must establish clear guidelines on people, processes and technology within the scope of audit. This can include policies related to user access, risk assessments, security roles and responsibilities, training timelines, etc.
Evaluate current risks
It is pretty normal for small businesses to not have a dedicated security staff and people with other primary job functions carrying out such tasks. So there are edge cases & risks to handle and implementation gaps to fill. Running a risk assessment to evaluate current risks and compliance level helps understand the risk profile and prioritize them accordingly under the remediation plan.
How to run a risk assessment?
- Identify the critical components: Data, IT infrastructure, people, procedures
- Include risk factors that exist: For example, data retention and disposal processes, third-party risks, network and system vulnerabilities etc.
- Bifurcate them into internal and external threats and score them based on criticality, say 10 being the most critical
- Note down the current processes in place for mitigating the identified risks
Additional tips:
- Also perform fraud risk assessment as it is often considered as part of evaluation during the audit. This includes financial fraud, misconduct by employees, bribery acts etc.
- Include vendor risks as part of assessments and request their SOC 1 and SOC 2 certifications
Implement security controls to fill gaps
The next step is to implement administrative, technical and physical security controls on the basis of identified risks and gaps. These can include:
- Access controls
- Network security controls
- Encryption
- Incident response
- Surveillance systems
- Application security controls etc
There can also be system reconfigurations in accordance with industry best practices. For example, reconfiguring firewalls or backup systems.
Get ready with the documentation
Documentation is the tangible evidence for the implemented controls and forms an important part of the SOC 2 audit. Let an experienced member from the engineering team coordinate and follow-up for the documents related to security.
Here’s the list of documentation that will be required:
- Management assertion: This compromises of operational objectives, internal control processes, system requirements and physical security arrangements
- Technical security documents: Log management policy, password requirement policy, data retention and destruction policy, backup logs etc.
- Operational documents: Physical office diagram, risk management plan, vendor agreements etc.
- Human resource documents: Organizational chart, security awareness training logs, onboarding policies, evaluation of employees etc.
- Privacy and compliance documents: Notice of Privacy practices, confidentiality policy etc.
- Third party and vendor contracts and other complementary user entity controls (SOC 2 controls performed by your service provider)
Note: You will also require administrative policies and cloud infrastructure certifications as part of evidence production along with these documents.
Undergo a readiness assessment
A readiness assessment helps understand the organization’s preparedness for an actual audit through a preliminary view. More often than not, small businesses do not have an internal audit team so this is performed by a service auditor. The existing controls are mapped to the Trust Service Criteria to spot any misfires and corrective actions are recommended so that final audit takes lesser time, energy and resources.
Get a formal audit
Next step is to find an auditor (tips on that in the later section) and get a walkthrough of the process.
The audit process can require you to start with a security questionnaire followed by gathering evidence and documentation of controls. The auditor then understands the security practices and business processes through observation, inspection and consulting responsible employees for each process.
There can be a lot of moving back and forth for evidence collection and corrective actions (not with Sprinto though) and it can be a rigorous exercise.
Sprinto has automated evidence collection and auditors are added to the dashboard to see a single-shot view of compliance evidence.
Obtain final SOC 2 report
The final SOC 2 report has a summary of audit findings. However, you never fail a SOC 2 audit but you receive an opinion on the effectiveness of controls.
- An unqualified opinion suggests the organization cleared the audit with flying colors
- A qualified opinion means there’s an area of concern but not a critical deficiency so it can be accepted by customers mostly.
- An adverse opinion signifies concerning material misstatements with impact.
- A disclaimer of opinion is issued when the auditor doesn’t find sufficient evidence for issuing an opinion.
In case you do not receive an unqualified opinion, rework on the controls and retry.
Also check out: A Guide to SOC 2 for startups
How long does it take to complete the audit process?
The time taken to complete the audit process will depend on the type of audit chosen.
SOC 2 Type 1 audit only reviews the design of controls at a point in time and takes 5 weeks to 3 months. SOC 2 Type 2 audit assesses the effectiveness of internal controls over a period of time and can take 3-6 months or more.
Note: This time period is only for the final audit process and does not include the time taken for pre-audit preparations and review period.
How to select the right auditor as a small business?
Higher costs, compromised engineering bandwidth and disrupted operations are the biggest nightmares of a small business. That is why it is so crucial for them to find the right auditor and navigate through the compliance process with ease.
Here’s how you can go about selecting the right auditor as a small business:
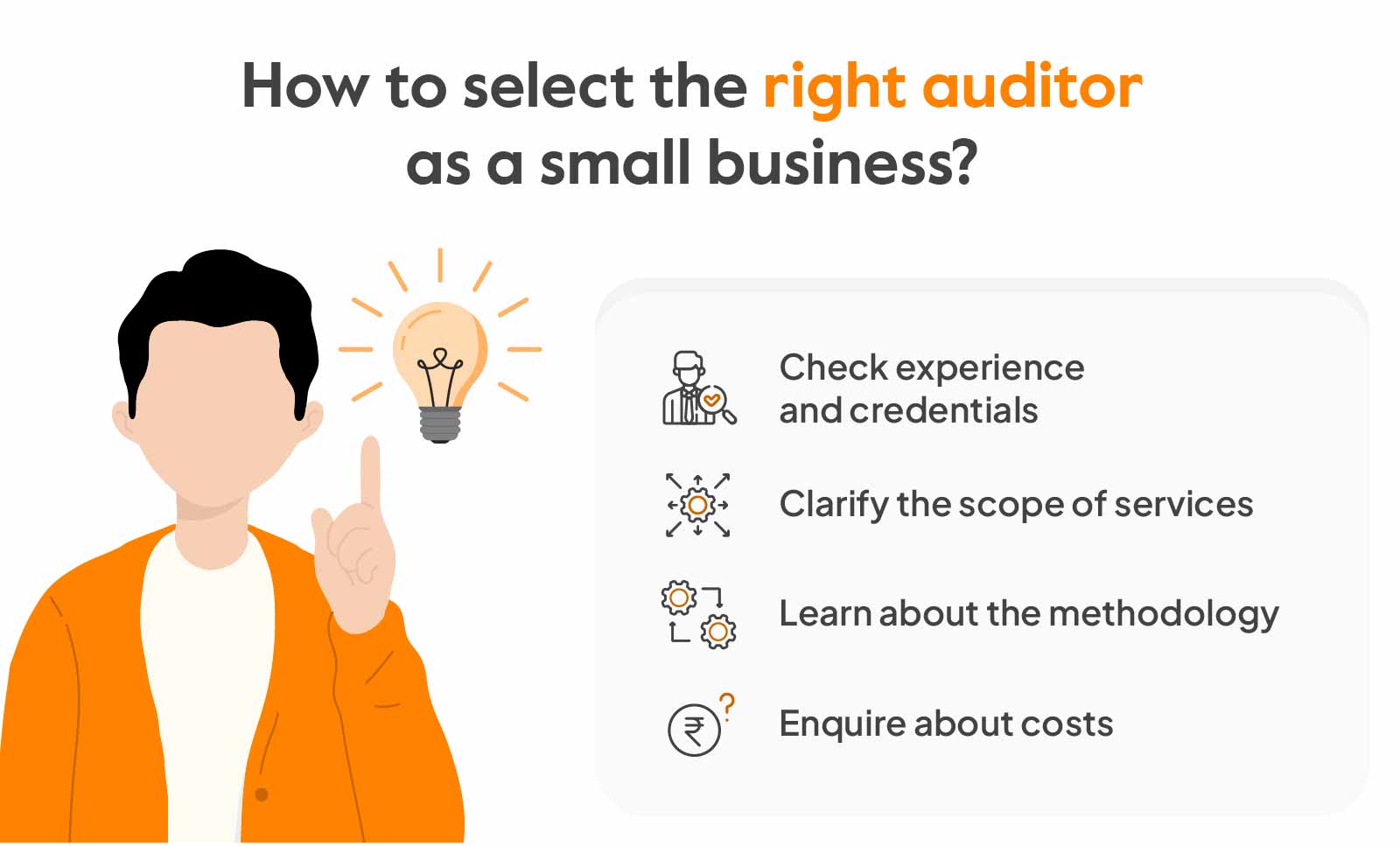
Check experience and credentials
The auditor must be a Certified Public Accountant firm and should have experience in SOC 2 audit for small business. To find a good personal fit, also enquire about experience in SOC 2 audit for a firm with a similar security maturity level and look for reviews.
Clarify the scope of services
It is always advisable to get clarity on the scope of services that will be included in the SLA (service level agreement) before selection. Questions like what types of controls will be evaluated, will there be recommendations for improvements etc. must be addressed. As a small business these little things matter for strengthening internal controls.
Learn about the methodology
Make sure to enquire about the approach used by the auditor for conducting the SOC 2 audit. This includes methods used for risk assessments, evaluating controls, reporting and ensuring the quality of audit. Additionally, ask if the auditor uses automation tools for performing the audit.
Enquire about costs
Get accurate cost estimates before final selection because there’s less financial flexibility and tighter budgets for small businesses. Seek details about total costs, breakdown of cost components and any hidden/additional costs to strike the right balance between value and costs.
Additional questions that must be asked:
- What all will not be included in the SLA and how much will it cost additionally to get that service?
- How are contingencies or unexpected events handled during the audit?
- What will be the timeframe for the audit?
- Will there be any ongoing support services or annual follow ups?
- How many people will be needed from the organization for helping with the audit process?
How much does it cost to get SOC 2 audit for a small business?
SOC 2 audit for small business can feel like paying through the nose but recovering from data breaches and reputational damages is thrice as expensive. So, consider the long-term win.
A SOC 2 Type 1 audit can cost a small business anywhere between $8000 to $30000 and a SOC 2 Type 2 audit cost can range from $20000 to $50000.
Tips:
- Choose boutique or mid-tier audit firms instead of highly priced Big4 audit firms to stay within the budget.
- Some auditors charge on the basis of the TSC chosen. A Type 1or Type 2 audit upto 3 TSCs can be done in about $25000.
Become SOC 2 compliant with Sprinto
SOC 2 audit process is heavy on documentation, evidence gathering, testing and implementing controls. Manually it can take hundreds of hours and still be an error-prone process. Enter Sprinto.
With Sprinto, SOC 2 audits are as easy as launching integrated risk assessments, activating automated checks, capturing continuous evidence and launching an async audit from Sprinto’s network. This process is 10x faster than manual spreadsheets and has given businesses 100% audit success so far.
Ditch the compliance pain with Sprinto’s adaptive automation. Talk to our experts to understand why Sprinto makes the perfect SOC 2 partner.
FAQs
Is it worth getting SOC 2 for small business?
Yes, any small business that aims at unlocking big opportunities and win enterprise clients needs SOC 2 because it will be questioned about security at every step. Moreover, it gives compliance confidence and makes business scalability easy and secure.
Which type of SOC 2 is suitable for small business?
Although it depends on the needs of the business, SOC 2 Type 1 is a good starting point for a small business new to the audit process. It can help identify areas of concern that can be addressed to prepare for SOC 2 Type 2. It is however worth noting that for greater assurance to customers and stakeholders, the business will ultimately require a Type 2 report.
Which staff members will be needed to support a SOC 2 audit?
In case of small business, a member from senior management or the owner can be the execute sponsor. Then an HR, an experienced engineering team member or somebody from IT staff and a legal team member will be required to support the audit.


Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.


























