Risk assessment and management is a critical step in your ISO 27001 certification journey. An organization-wide risk assessment, in fact, is the central focus of ISO 27001. The information security standard helps to protect an organization’s information assets by identifying the risks and protecting them by deploying relevant security controls and measures.
In this article, we highlight the main steps to an effective ISO 27001 risk assessment and discuss the best practices involved in going about this critical step. And don’t miss our ‘quick and dirty’ cheat sheet on risk assessment at the end of the article.
TL;DR
| The ISO 27001 risk assessment process helps organizations identify various types and levels of risks relevant to a business and score them based on severity and likelihood of occurrence. |
| Under ISO 27001, risk management guidelines entail implementing preventive controls, establishing an incident response plan, enabling response reporting, and continuously monitoring control effectiveness. |
| The risk treatment plan under ISO 27001 guidelines necessitates a detailed action plan to mitigate the impact of control failures or breached safeguards. |
Overview of ISO 27001 risk assessment
ISO 27001 risk assessment is a systematic process by which an organization identifies information security risks, their likelihood of occurance, and impact, in order to implement the right measures to mitigate them. It follows the setting up of a robust and cost-effective Information Security Management System (ISMS).
ISO 27001 demands a structured approach to risk management – from risk identification to risk assessment, and eventually executing a risk treatment plan to mitigate the risks.
Risk assessments aren’t just for audits—they’re an ongoing process. ISO 27001 requirements (6.1, 6.2, 7.5) emphasize clear documentation, with assessments conducted regularly and after any significant changes.
Why do organizations need to perform ISO 27001 risk assessment?
Organizations perform ISO 27001 risk assessments to proactively identify and evaluate information security risks that could impact the confidentiality, integrity, and availability of their data. The assessment helps organizations prioritize security controls and build a more risk-informed ISMS.
ISO 27001 advocates for robust information security policies and procedures, and risk assessment is a crucial part of this process. The purpose of ISO 27001 risk assessment is to help organizations identify the threats and vulnerabilities along with their severity and likelihood of occurrence so adequate measures can be taken against each of those threats.
As we jump into the article, here’s an interesting take on risk management by the industry veteran and Co-Founder of Sprinto, Girish Redekar:
“Risk is something which is common sense and we do it every day. It is also core to frameworks like ISO. If you find a good system that helps you translate that risk into the way your business runs, then you can do well as a risk function.”
Girish Redekar, Co-Founder at Sprinto
Great advice adds up. Get more from the brightest minds in GRC — Subscribe to our newsletter
5 ISO 27001 security areas
Knowing the key security areas is a game changer when managing risks under ISO 27001. Our in-house experts, who live and breathe ISO 27001 compliance, say that understanding these areas can simplify your approach to building an effective ISMS. So, let’s dive into the five crucial ISO 27001 security areas you need to know to keep your risks in check and your organization secure.
1) Company security policy
A company security policy is typically a document outlining an organization’s procedures and approach to identifying, treating, and managing risks. Functioning as a foundation, it helps scope out key objectives, roles and responsibilities, and timelines of the activities.
2) Asset management
You can’t protect what you can’t see or don’t know about. Asset management involves identifying all assets that need protection, maintaining an updated inventory, and establishing safeguards to protect them against known threats.
3) Physical and environmental security
Even though the number of digital threats greatly outpaces physical and environmental threats, physical security breaches can cause serious repercussions for any organization, necessitating certain mechanisms of resilience against such instances.
This section of ISO 27001 risk management covers the necessary controls to mitigate such risks, for example, authenticated entry, physical barriers, and backup power generators to protect your valuable resources and ensure operational resilience in the face of potential threats.
4) Access control
Access controls define the levels of information access within an organization, ensuring that people can access what they are authorized to. These controls typically use authentication workflows to verify users’ identities and grant access according to their authorization level.
For example, biometric authentication along with role-based access controls offer baseline resilience against phishing attacks and internal vulnerabilities within an organization.
5) Incident management
To put it simply, Incident management is your response plan for handling security incidents effectively. It includes immediate actions to contain failures, assigns responsibility for managing risks, outlines procedures and timelines for reporting incidents, and assembles a response team. Each action is classified by priority and severity to ensure appropriate and timely responses.
How often should you perform ISO 27001 Risk Assessments?
ISO 27001 doesn’t mandate a fixed frequency for risk assessments, but performing one once a year is a best practice. It is also vital to conduct a risk assessment whenever significant changes occur, such as new systems, processes, regulations, or security incidents.
Regular assessments help ensure your risk profile stays up to date and your controls remain effective against evolving threats. Most organizations align their risk assessment cycle with internal audits or ISMS reviews.
How to perform ISO 27001 risk assessment
ISO 27001 risk assessment involves identifying infosec risks, assessing their likelihood and impact, and determining appropriate actions to mitigate them. The risk assessment must align with your operational context and ISO 27001 requirements to ensure effective risk management and compliance.
Here is the five-step procedure to perform ISO 27001 risk assessment for your organization:
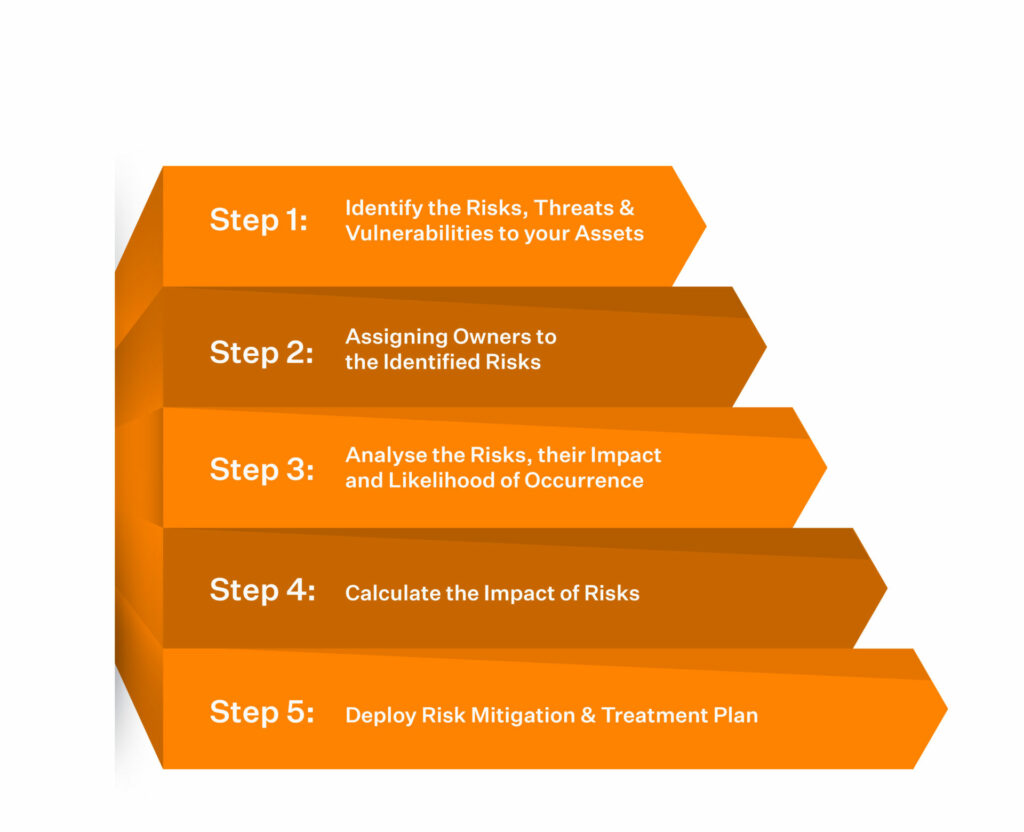
1. Identify the risks, threats, and vulnerabilities
Identification of assets: Make a list of the information assets across your organization. These would include your software, hardware, databases, and intellectual property, to name a few.
Assessing the risks attached: Once you have a comprehensive asset list, identify the risks attached to each asset – risks that could impact the confidentiality, integrity, and availability of each listed information asset. Your threats and vulnerabilities could range from unauthorized access to your database to embezzlement and espionage to inadequate data backup, and password management, to name a few.
How can Sprinto help?
Integrate Sprinto with your cloud stack, select your framework, and start scoping out risks with Sprinto’s comprehensive risk library. Score risks for their likelihood of occurrence and impact using trusted industry benchmark that come right out of the box with Sprinto.
Save time by automating the ISO risk assessment process
Sprinto lets you assign risk owners and sends automatic alerts for remediation actions to the right individuals.
2. Assigning owners to the identified risks
Often overlooked, this is an essential step in determining the success of your organization’s risk assessment exercise. For every risk, assign risk owners who would be in charge of monitoring the risk, and eventually implementing the risk treatment plans.
3. Analyze the risks, their severity, and the likelihood of occurrence
ISO 27001 doesn’t prescribe a specific method for risk analysis, so it’s important to define a consistent, organization-wide approach. This ensures consistency in your risk treatment process.
Once you’ve identified your risks, analyze the severity of risks by assigning a likelihood of occurrence and rating its potential impact, either on a scale (e.g. 1–10) or as Low, Medium, or High. The scale will help you prioritize risk remediation based on criticality.
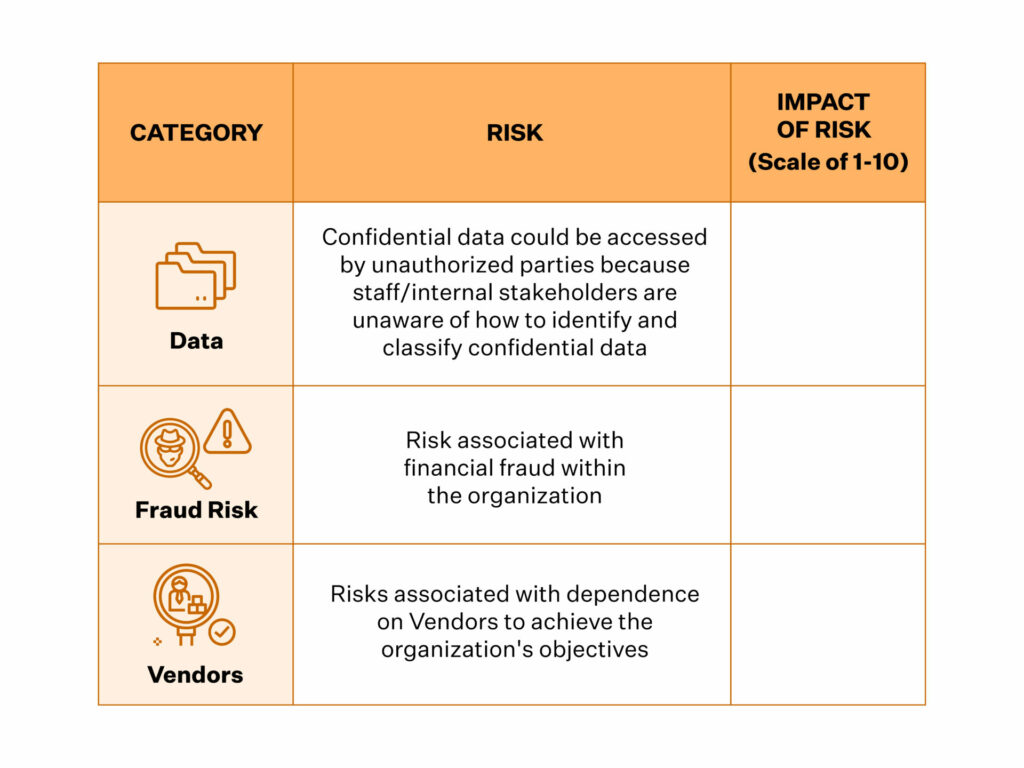
4. Calculate the impact of risks
To calculate the impact of the risks, it is a good step to categorize them first. Depending on the nature of your business, your risk categories could be financial, legal, regulatory, and your reputation, to name a few. While rating the impact, you must also consider factors such as how fast the impact will be felt and the likelihood of its occurrence.
The scores you assign (from 1-10 or low-medium-high) will help you design and prioritize your risk treatment process.
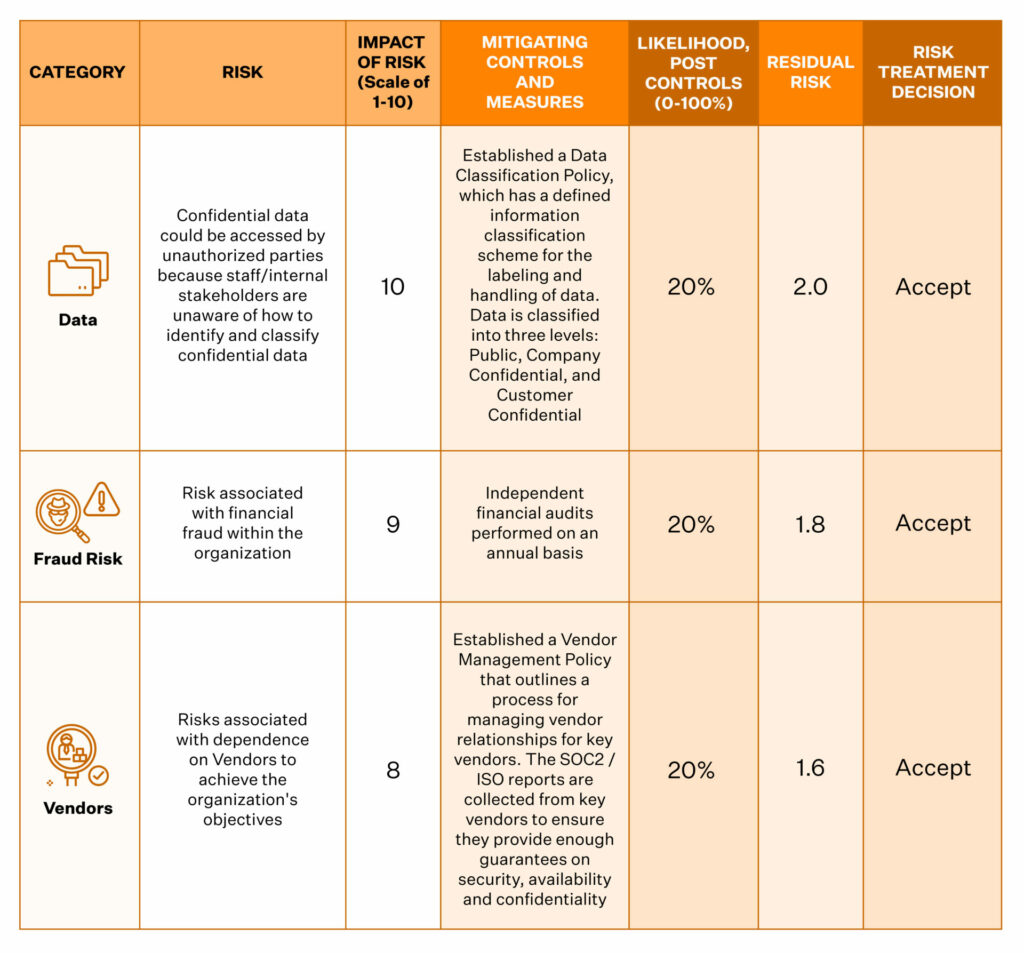
Sprinto’s integrated heat map helps you visualize the impact and likelihood of risks
5. Deploy risk mitigation and treatment plan
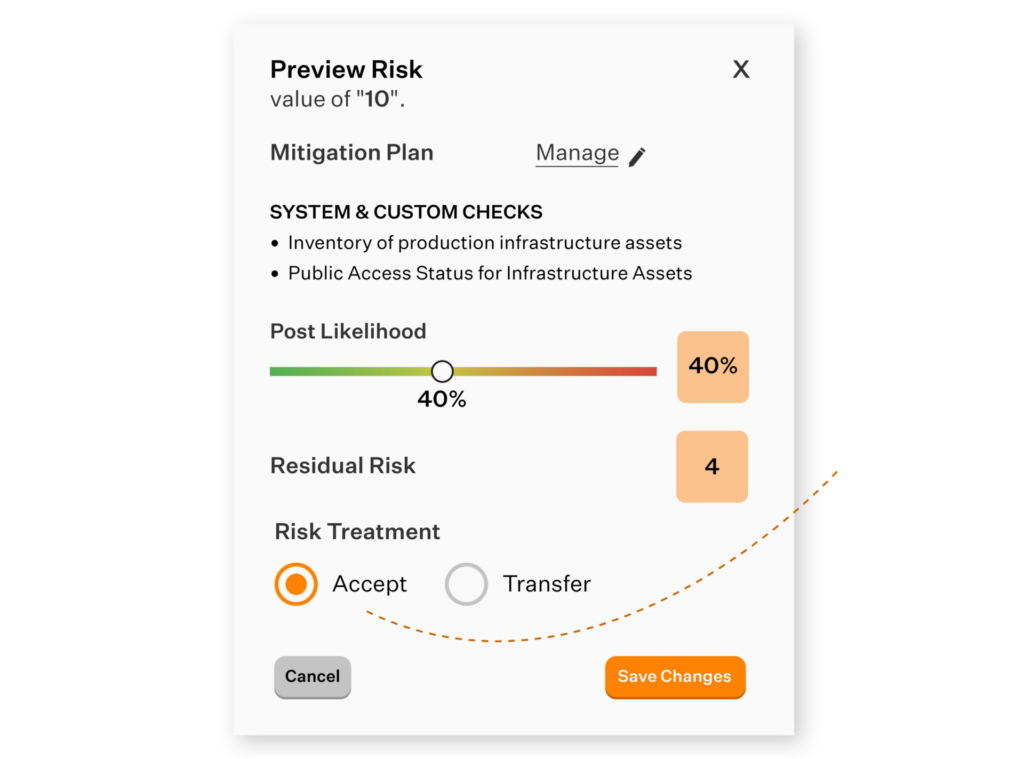
Risk mitigation and treatment involve prioritizing risks based on their potential impact and selecting from three response strategies: accepting the risk, rejecting the risk, or implementing controls to reduce risk likelihood or impact for residual risks.
In short, risk treatment plans document your responses to the threats, vulnerabilities, and risks you have identified in your risk assessment exercise. Know that this piece of document is critical to your ISO 27001 certification. Your external auditor will go over it in detail during your ISO 27001 certification audit and the subsequent periodical audits.
Here are four ways to mitigate the risk:
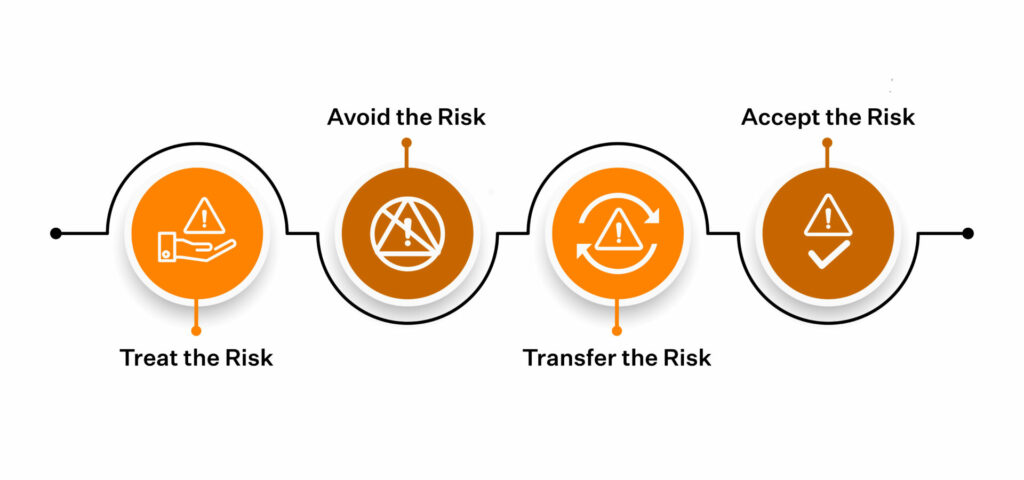
(I) Treat the risk
If the risk score is above what’s acceptable, you can reduce its impact or likelihood by deploying the security controls as outlined in the ISO 27001 controls in Annex A. Security awareness training, access control, penetration testing, and vendor risk analysis are some of the ways you can treat risks.
(II) Avoid the risk
Another response to the identified risk is to look for ways for avoiding the risk altogether. If the risk-return matrix is lopsided, you can choose to avoid the risk in totality. For instance, if you are a remote-only organization, you can avoid the risk of maintaining the physical security of your production infrastructure or data centers.
(III) Transfer the risk
Where feasible, you could modify the risk by transferring it to a third party. You could do this by contracting vendors, outsourcing a particular job function, or buying insurance, for instance.
(IV) Accept the risk
The objective of your risk treatment plan is to bring the risk levels of your information assets, wherever possible, to an acceptable level. Remember, you can’t eliminate all your risks. You can devise a detailed plan on what should be done in the event of a ‘risky eventuality’. These include data breaches, cybersecurity attacks and other such incidents that risk the security of your data. Your risk treatment plan should include well-thought incident response and incident management.
Sprinto suggests you the right risk response strategy and you can accept, transfer or reject risk as per preferences.
(V) Risk treatment plan and Statement of Applicability
Your Risk Treatment Plan and Statement of Applicability are two crucial documents in your ISO 27001 assessment journey.
Clause 6.1.3 of the ISO 27001 Standard states that an SOA must contain the following:
- List of controls identified as a response to the identified risks
- An explanation for the choice of controls, how they have been implemented, and reasons for the omission of controls, where applicable)
A Statement of Applicability outlines whether each of the controls defined within Annex A of the ISO 27001 standard will be applied or not based on your Risk Treatment Plan. For each risk, you must evaluate the options for treatment.
For instance, applying controls, accepting, avoiding or transferring risks. The SOA must comprise the actions performed based on the selected option. Again, management approval with documentation is needed for each situation where risks are accepted.
If you are finding it difficult to implement ISO risk assessment then talk to experts about how you can simplify this process.
How can we help?

If you are finding it difficult to implement ISO risk assessment, consider talking to our experts about simplifying the process. (Click here to schedule the meeting)
How to pick the right ISO 27001 risk assessment methodology?
A risk assessment is not where ISO 27001 starts. The starting line is the risk assessment methodology which is a structured and repeatable approach to identify and manage risks.
Clause 6.1.2 of ISO 27001:2022 mandates that you define five things in your risk assessment methodology:
- How you identify risks to ensure the confidentiality, integrity, and availability (CIA) of information
- How you assign risk ownership
- How you evaluate risk ie. the criteria for impact and likelihood
- How you calculate risk levels
- How you determine risk acceptance thresholds
Here’s how you can use these requirements to write a risk assessment methodology:
- For risk identification ISO 27001 gives you the freedom to choose
- Asset-threat-vulnerability mapping (the classic model)
- Business process-based identification
- Department-driven or scenario-based methods
Sprinto recommends sticking with asset-threat-vulnerability if you’re starting out. It’s comprehensive, auditor-friendly, and easily mapped in compliance platforms.
- To define risk ownership, assign each risk to someone with both the authority and accountability to mitigate it. This is not always the asset owner but the function or business owner who can act on the risk.
- For risk assessment criteria, define how you’ll measure likelihood and impact, and also define the scale of measurement.
- The risk calculation method is always likelihood x impact. Sprinto’s methodology defaults to a similar model, automating this calculation across all mapped risks and controls so there’s no room for guesswork.
- To finalize the risk assessment criteria, decide what risk levels you’re comfortable accepting and which ones must be mitigated, and document them explicitly.
ISO 27001 Risk Assessment Examples
The risks vary depending on the industry and other factors. However, here is what a risk assessment table looks like in general. Let us see some examples of ISO 27001 risk assessment.
| S. No. | Threat | Vulnerability | Risk Impact (Out of 10) | Mitigation |
| 1 | Malware, ransomware, and viruses | Lack of antivirus program and weak firewall defense | 7-8 | Install and regularly update the antivirus program. Have a secure firewall in place. |
| 2 | Unauthorized access to sensitive data | Weak and common system/server passwords and unorganized access controls | 8-10 | Have strong password policies in place with two-factor authentication and implement access controls |
| 3 | Social Engineering (Phishing Attacks) | Lack of security awareness training among the company’s staff | 8-10 | Conduct security awareness training sessions with employees to identify and prevent social engineering attacks |
| 4 | Physical theft or unauthorized access to server rooms | Lack of physical security measures | 5-7 | Install surveillance cameras, access control systems, and alarm systems to improve your physical security |
Check out our customer’s case study on ISO 27001 audit
ISO 27001 risk assessment template
The overall objective of the risk assessment exercise is to implement a risk treatment plan using ISO 27001 controls list such that your organization’s residual risk is acceptable. The primary objective is business continuity.
You will do well to keep this in mind while selecting a risk assessment and treatment template. While there are many free ISO 27001 risk assessment tools and templates, choose one that fits your organization’s risk universe. A simple spreadsheet with a logical approach to asset-based risk management can also help here.
Download Your ISO 27001 Risk Assessment Template
ISO 27001 risk assessment report
The ISO 27001 risk assessment report will provide an overview of what you find. It would be reviewed meticulously during your ISO 27001 internal audits as well as certification audits. It should include the following:
- List of information assets and asset owners, risk assessment framework (includes the criteria for accepting risk), and management approval for acceptance of residual risks, to name a few.
- The risk treatment applied and the impact of the risk affecting the availability, integrity and confidentiality of each your assets after and before treatment.
- Order of priority for treating the risks, the controls applied, and target timeline for applying the treatment.
- A comprehensive risk management framework that describes all steps and relevant methods required to be carried out in terms of the risk assessment process. These include asset identification, threat & vulnerability identification, control analysis, business impact analysis, risk determination, control recommendations as well as results documentation.
These apart, your documentation should also include the evaluation periodicity of the controls. An internal audit of your controls will help find glaring gaps, if any, in the process. A gap analysis will help you ensure you are on the right track.
How Sprinto helps simplify ISO 27001 risk assessment?
Sprinto’s newly-introduced Integrated Risk Assessment feature has been designed to ensure your approach to risk assessment is as holistic as it is sure-footed. From identifying risks to assessing their impacts to mitigating them, the entire risk management process has now been broken down into easy-to-understand, scalable and framework-agnostic steps in the app.
What’s more, you needn’t worry about having missed any pertinent risk(s), thanks to Sprinto’s expertly-organized risk library.
Here’s a look at why Sprinto’s Integrated Risk-Assessment feature can help you:
Curated risk profile
With Sprinto’s curated risk register, your risk assessment will be more exhaustive but without the exhaustion of it! With a comprehensive risk library, Sprinto will now give you a 360-degree view of org-wide, entity-down risks. As a result, you will only work with the risks relevant to your business instead of wasting time chasing tangential ones.
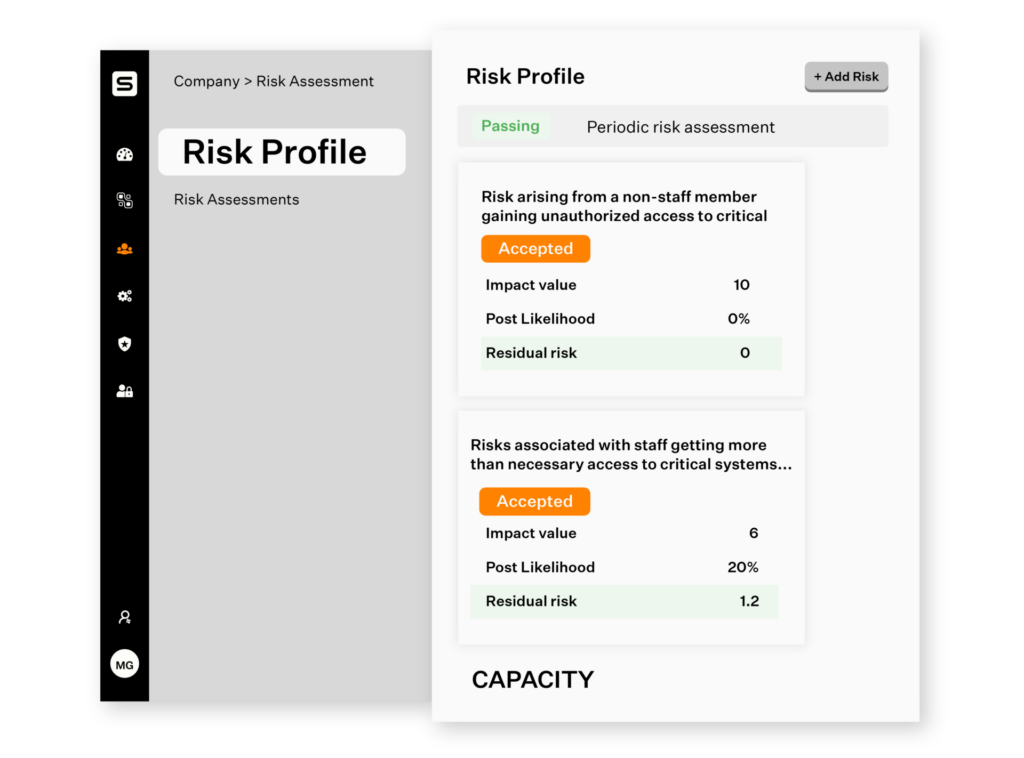
Continuously monitor risks
Sprinto automatically maps risks to controls and relevant compliance criteria. Compliance checks are run throughout the day and you can check the live status on the health dashboard. In case of any deviation automated alerts are sent to the risk owners to initiate proactive response.
Rate your impact with insight
Rating the impact of the identified risks needn’t be just a game of intuition. You can use Sprinto’s baked-in industry benchmarks as a sounding board to ensure you are on the right track. You can then dig into Sprinto’s pre-mapped controls list to decide your risk treatment and mitigation plan. You can assign risk owners and the remediation workflows to the right individuals.
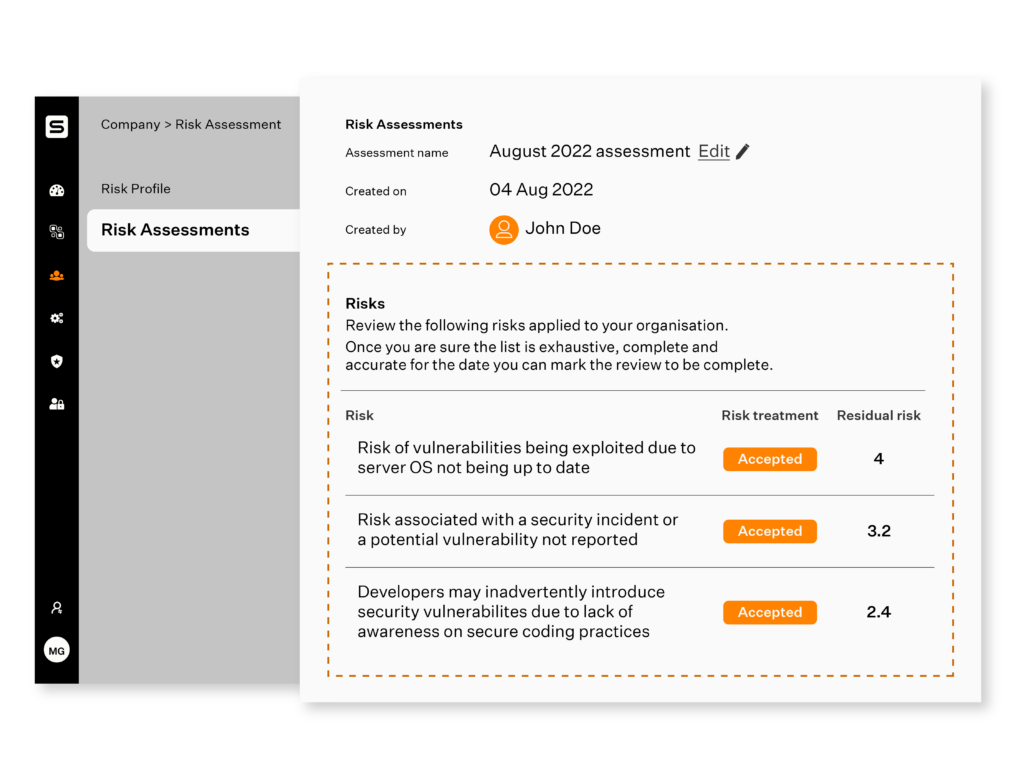
Single-screen management
You needn’t meticulously maintain versioning of spreadsheets and to and fro mailers to get management approval anymore. You can now assess, review, edit, and ready your organization’s risk profile from a centralized screen.
You can also get your management to review the risk register simply by adding them to the platform. And once you have the management buy-in, your onboarded auditors can review and audit your risk profile on their dashboard. It is that simple.
Also read how Giift completed ISO 27001 implementation in 8 weeks
Wrapping Up
So, that’s all about ISO 27001 risk assessment. The importance of risk assessment is quite evident, and you should be following the risk assessment practices not just from a compliance point of view but from an overall security aspect as well.
However, you can skip the lengthy spreadsheets and can automate most of the risk assessment processes to generate compliance-ready reports and more. Sprinto is a great risk assessment and compliance automation solution and can be a good fit for your organization. You can request a demo to see for yourself. Make risk assessment a strength. Talk to us today!
FAQs
What is ISO 27001 risk assessment?
An ISO 27001 risk assessment identifies and evaluates security risks to protect an organization’s data. To get ISO 27001 certified, you need to:
- Identify Risks: Spot potential security threats to your systems.
- Evaluate Impact: Assess the likelihood and impact of these risks.
- Document Actions: Record everything to show compliance.
- Treat Risks: Take actions to reduce or eliminate them.
- Review Regularly: Update assessments as needed or when changes occur.
How to calculate risk score?
Risk score is calculated by multiplying the likelihood of risk by its impact. This is a numerical value, usually on a scale of 1-10, 10 being a high-risk score and 1 being the lowest.
What is iso 27001 risk management framework?
ISO 27001 risk management framework is a structured approach to identifying and mitigating information security risks. It includes components such as risk assessment, analysis, risk treatment and continuous risk monitoring.
What documentation is required for ISO 27001 risk assessment?
ISO 27001 requires mandatory documentation on risk assessment and risk treatment processes. The organization must attach proofs for risk identification, analysis and initiation of risk response actions.
What is the difference between asset owner and risk owner in ISO 27001?
An asset owner is responsible for overall management and protection of information assets. A risk owner is only accountable for specific risks related to assets. Both the roles are crucial for maintaining an effective ISMS.
What is the ISO 27001 risk treatment plan?
The ISO 27001 risk treatment plan is a tactical guide to address the identified risks during risk assessment. It outlines the details of the assessed risks along with the corrective actions to be taken, the responsible stakeholders, budget and resources required and the timeline for remediation.
Is ISO 27001 risk assessment mandatory?
Yes, risk assessment is a requirement for the ISO 27001 standard. To get certified, you need to identify the risks associated with confidentiality, integrity, and availability of the assets defined in the ISMS.
Why is risk assessment important in ISO 27001?
The ISO 27001 risk assessment is important because it helps organizations identify the potential risks and vulnerabilities in the current IT security setup. By doing so, organizations can work on risk mitigation approaches to eliminate potential security threats.
Srividhya Karthik
Srividhya Karthik, is a Content Lead at Sprinto, she artfully transforms the complex world of compliance into accessible and intriguing reads. Srividhya has half a decade of experience under her belt in the compliance world across frameworks such as SOC 2, ISO 27001, GDPR and more. She is a formidable authority in the domain and guides readers with expertise and clarity.
Explore more ISO 27001 articles
ISO 27001 Overview & Requirements
ISO 27001 vs Other Frameworks
ISO 27001 Audit & Certification Process
ISO 27001 Management & Assessment
ISO 27001 Implementation & Automation
ISO 27001 Industry-Specific Applications
research & insights curated to help you earn a seat at the table.









