How to Pass a SOC 2 Audit: Essential Steps and Tips
Meeba Gracy
Apr 25, 2024
The rise of cloud technology has revolutionized business operations, enabling remote work but also increasing cyber vulnerabilities. Ransomware and phishing attacks have become more prevalent, making security measures in B2B commerce increasingly complex. In response, the AICPA has developed comprehensive compliance guidelines, including the globally recognized SOC 2 audit certification. SOC 2 audits, conducted by accredited CPAs, involve a thorough examination of an organization’s control systems. This rigorous process evaluates both the design and operational effectiveness of security measures. SOC 2 certification ensures that service providers securely manage data, protecting the interests and privacy of their client organizations.
What is SOC 2 audit?
A SOC 2 audit is the final stage in the SOC 2 attestation process that evaluates controls against the five Trust Services Criteria (TSCs) — security, availability, processing integrity, confidentiality, and privacy, as stated by the AICPA.
Please take note: SOC 2 audit process largely revolves around the Trust Services Criteria. Nevertheless, it is important to acknowledge that not all five principles universally apply to every organization.
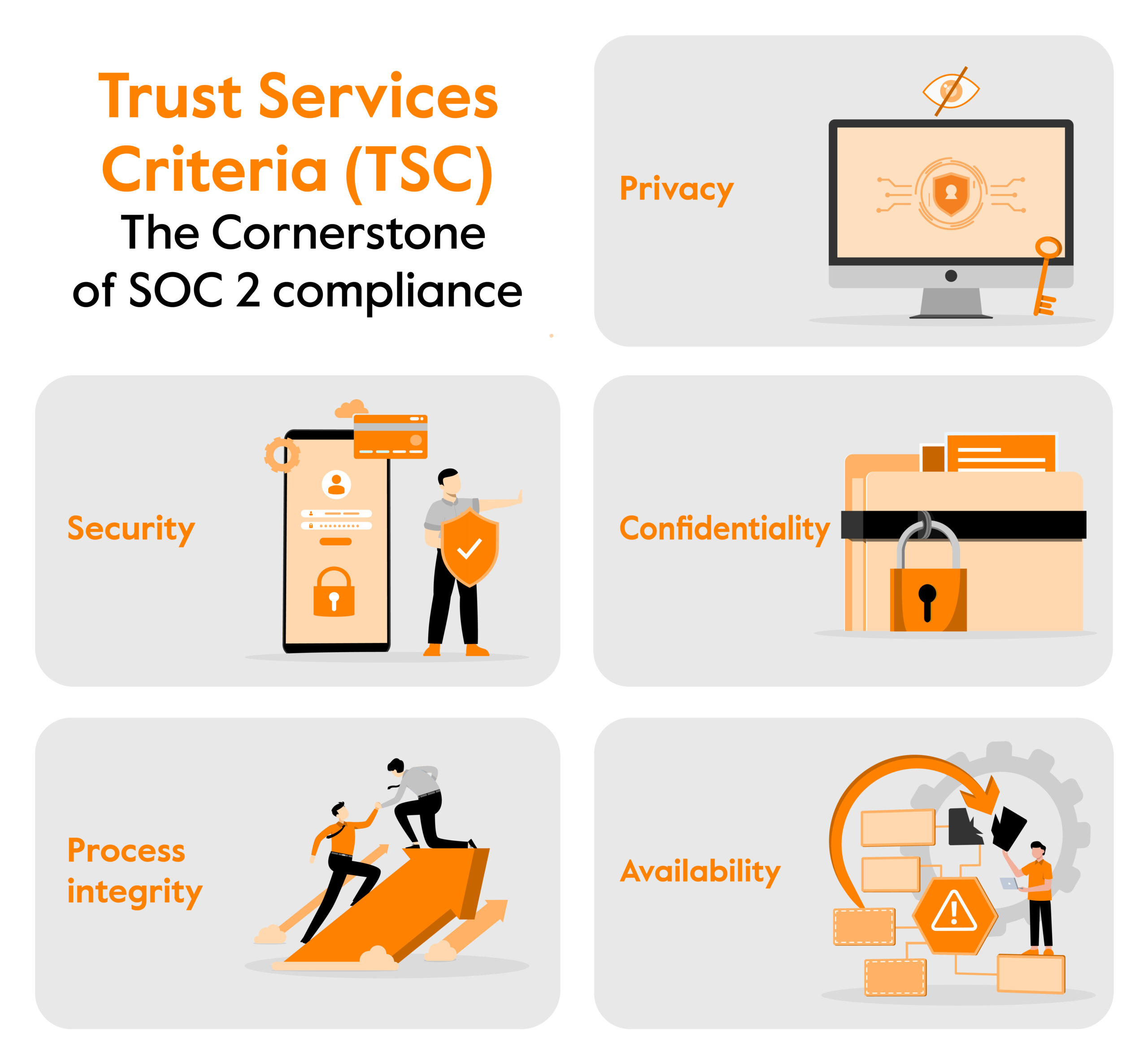
For example, in cases where data storage involves personal information, the privacy principle becomes relevant. Similarly, the security and availability principle assumes significance for organizations that operate data centers and provide storage services to customers.
Companies generally adopt SOC 2 audits to show their clients and partners that they comply with all rules and regulations.
What is the purpose of SOC 2 auditing?
SOC 2 auditing evaluates an organization’s controls according to trust services criteria, aiming to pinpoint security and compliance weaknesses. The process involves implementing security measures, safeguards, and risk assessments. The SOC 2 audit encourages organizations to address vulnerabilities, protect data, showcase compliance commitment, meet security objectives, and continuously enhance internal controls. Ultimately, SOC 2 audits instill confidence in customers, business partners, and stakeholders regarding the service organization’s ability to manage and protect data securely.
Who needs to go through the SOC 2 audit process?
It is a norm for all technology-based service organizations that store client information in the cloud to go through the SOC2 audit process. In simple terms, this requirement will apply to all businesses that offer SaaS and other cloud services, wherein the cloud is the main source for storing client data.
Get Our Practical SOC 2 Guide;
Yours at No Cost

What are the types of SOC 2 audit?
There are 2 types of SOC 2 compliance: Type 1 and Type 2 audits. Type 1 and Type 2 audits have distinct uses based on the business requirement and the scope of SOC 2.
A Type 1 SOC 2 audit process attests to your company’s use of compliant systems and processes at a specific time. It evaluates the design and how you implement certain relevant controls to TSCs.
Overall, it provides a snapshot of your company’s compliance status and whether it offers assurance that the proper systems and processes meet the standard during the audit.
In contrast, a Type 2 SOC 2 audit attests to compliance over a designated period, typically 12 months. This type of audit evaluates the design and implementation of controls like Type 1 and assesses their effectiveness and operational integrity over the duration.
Overall, it provides a complete analysis of how well your system’s controls have been operating and whether they have consistently met the TSC throughout the assessment period.
Soc 2 audit readiness assessment
A SOC 2 audit readiness assessment is part of the audit evaluation that examines whether an organization securely maintains its data processing systems. The assessment captures the lapses or misses in your organization’s processes, policies, and gaps before the final audit. Typically, your SOC 2 readiness assessment will involve 2 the following steps:
Audit scope
The first step is assessing your audit scope and examining how well your internal controls align with the Trust Service Criteria (TSC) chosen. This involves thoroughly examining your controls, documentation (such as management assertion letter, system description, and policies), and understanding what systems need to be included in scope. The readiness assessment identifies missing controls or processes, allowing you to address gaps before the SOC 2 compliance audit. It’s essential to have sufficient time for remediation.
Short on time? Experience the Sprinto Advantage: Streamline your SOC Readiness Assessment with Sprinto, a smart compliance automation solution. Sprinto’s security program evaluates your control environment, automates security controls, conducts gap analysis, performs risk management, manages audit documentation, and enables you to adhere to the SOC compliance framework—all within a user-friendly dashboard.
Breeze through your SOC 2 audit
Develop a comprehensive remediation plan
Following the SOC 2 readiness assessment, a detailed remediation plan is crafted to address identified deficiencies in controls, design, and operational oversight about SOC 2 compliance requirements. This includes conducting vulnerability scanning, risk assessments, and penetration tests to pinpoint areas of improvement.
External consultants provide recommendations and remediation plans, suggesting enhancements such as process redesign, implementation of security awareness training programs, and improvements in evidence collection. A management letter outlines observations, recommendations, and opinions on your SOC 2 readiness.
What are the steps involved in SOC 2 audit?

The SOC 2 audit involves several steps to assess the controls established by. Here are the six steps for SOC 2 audit:
1. Identify Your Scope
First, take into account the TSCs defined by the AICPA. These criteria serve as the foundation for evaluating the systems and processes within your firm. However, not all SOC 2 auditing necessarily have to have all 5 criteria categories.
Hence, it is important to determine which specific systems, policies, and procedures are relevant to supporting the applicable principles.
For example, if your company’s services revolve around data security and availability, the scoping process involves identifying the systems, policies, and procedures related to that aspect. Hence, this scoping exercise ensures that the audit focuses on the relevant areas and provides a clear framework for assessment.
Throughout the audit process, the auditor will carefully examine both your documentation and your systems to gauge how effectively they operate. The documentation you might be required to provide covers various aspects, such as:
- Lists of your assets
- Details about changes you’ve made and how you manage them
- Records of equipment maintenance
- Logs for system backups
- Your code of conduct and ethical policies
- Plans for business continuity and responding to incidents
2. Choose your report type
The initial step in the process is to determine the suitable SOC 2 attestation report for your service organization before inviting an auditor over.
SOC 2 Type I: This audit assesses if your systems are designed in alignment with the TSCs.
Type I audits are quick and cost-effective (often within a month), but they offer less comprehensive insights.
SOC 2 Type II: A type 2 audit evaluates your systems’ design and their operational effectiveness.
Type II SOC reports require more time (possibly up to a year) as auditors conduct tests on your information systems. Yet, once you pass, your compliance and security standards are unquestionable.
Your choice of audit type should consider your budget and the urgency of your situation.
Find out: How to get SOC 2 Type 2 certification
3. Conduct a risk assessment
SOC 2 compliance journey, the risk assessment is a vital step to safeguard your information assets. It’s like a safety check to identify potential dangers and protect your valuable data.
The risk assessment helps you figure out what risks your information assets might face.
For example, you might discover that there’s a chance of unauthorized access to your customer database, putting their sensitive information at risk.
Next, you assess how severe the impact of each risk would be if it were to happen. Then, you determine the likelihood of each risk occurring.
4. Control mapping and gap analysis
The second step in the audit involves conducting a thorough Gap Analysis & Control Mapping exercise. The readiness assessment or gap analysis is done to understand the alignment between the internal control environment and the TSC.
This assessment helps identify gaps or deficiencies in compliance, enabling proactive measures to address them before the audit.
For instance, if the criteria highlight the need for regular monitoring and logging of system activities, the gap analysis would help assess whether the existing controls fulfill these requirements.
5. Conduct internal audit
Internal audit step in SOC 2 as a way to ensure the safety and protection of your business assets. The goal is to make sure that everything is secure and that your business is following its own rules.
For example, let’s say your company stores sensitive customer data. With an internal audit, you can regularly check if this data is properly protected from potential threats like hackers or unauthorized access.
This way, you can be confident that your customers’ information is safe.
Moreover, the internal audit program helps your management team and stakeholders by identifying any risks that might be lurking around before the main SOC 2 audit.
6. Choose external reporting
Now is the time to select a partner to conduct your SOC 2 audit process. You can either get in touch with a Certified Public Accountant or select a suitable third-party compliance app “Sprinto.”
Once you are audit ready, the auditors will conduct their independent testing and assessments, providing an unbiased opinion on your company’s controls with TSC.
Get SOC 2 the easy way with Sprinto. Our automated platform replaces manual work with smart workflows to collect evidence, document controls, identify compliance gaps, and enable you to adhere to the relevant SOC 2 requirements. Ready to see how it’s done? Speak to our experts today.
Case Study:
“Our audit was a cakewalk. There was no instance of non-compliance across Type 1 and Type 2 reviews!” says Bhargava, MNN, Engineering Lead at Zipy.
Check out: How Zipy used Sprinto to get compliant and ace SOC2 Type 1 and Type 2 audits.
What are the types of SOC 2 Audit?
There are 2 types of SOC 2 compliance: Type 1 and Type 2 audits. Type 1 and Type 2 audits have distinct uses based on the business requirement and the scope of SOC 2.
A Type 1 SOC 2 audit process attests to your company’s use of compliant systems and processes at a specific time. It evaluates the design and how you implement certain relevant controls to TSCs.
Overall, it provides a snapshot of your company’s compliance status and whether it offers assurance that the proper systems and processes meet the standard during the audit.
In contrast, a Type 2 SOC 2 audit attests to compliance over a designated period, typically 12 months. This type of audit evaluates the design and implementation of controls like Type 1 and assesses their effectiveness and operational integrity over the duration.
Overall, it provides a complete analysis of how well your system’s controls have been operating and whether they have consistently met the TSC throughout the assessment period.
Tips for a Successful SOC 2 Audit
Here are some tips to successfully complete a SOC 2 audit. However, please note that preparing for a SOC 2 audit is not a one-time event but an ongoing process. You need to continuously monitor, assess, and improve your security controls; this is where Sprinto comes in. More on that below!
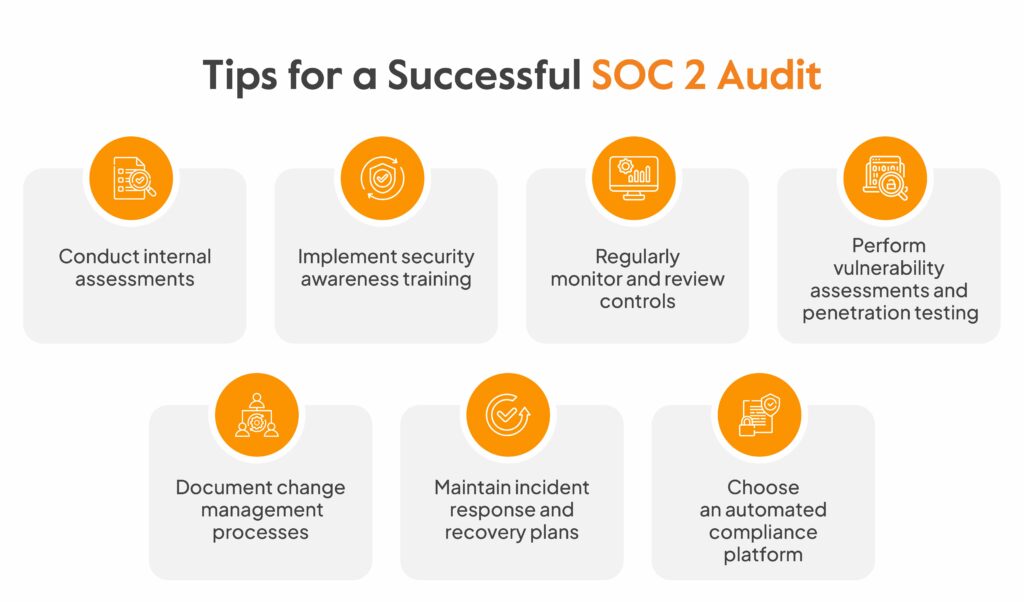
Conduct internal assessments
Before your SOC 2 audit, performing internal assessments can help identify any gaps or weaknesses in your security controls. With this step, you can address any issues and ensure you are prepared for the audit.
Implement security awareness training
Educating your employees about security best practices and responsibilities is crucial for a successful SOC 2 audit. Conduct regular security awareness training sessions to ensure everyone understands their role in maintaining a secure environment and complying with the necessary controls.
Regularly monitor and review controls
Continuous monitoring and review of your security controls are essential to maintain compliance. Implement mechanisms to monitor your systems and promptly address deviations or security incidents. This shows your commitment to creating a secure environment that complies with SOC 2 requirements.
Perform vulnerability assessments and penetration testing
Regularly conduct vulnerability assessments and penetration testing to identify and remediate any security vulnerabilities. This helps ensure your systems are adequately protected against potential threats and align with industry best practices.
Document change management processes
Maintain thorough documentation of your change management processes to demonstrate that system changes are properly planned, tested, and approved. This includes documenting change requests, approvals, implementation details, and post-change reviews.
Maintain incident response and recovery plans
Have well-defined incident response and recovery plans to address security incidents promptly and effectively. These plans should outline the steps during a security breach, including containment, investigation, remediation, and communication procedures.
Choose an automated compliance platform
Selecting the right automation platform is crucial for a successful SOC 2 audit. SOC 2 requirements may seem manageable, but gathering auditable evidence? That’s a whole new ballgame.
That’s where Sprinto steps in, tirelessly monitoring your systems and collecting the evidence you need. And here’s the best part: it categorizes the evidence according to SOC 2 criteria. Now you can say goodbye to countless hours of mind-numbing busy work. With Sprinto, you and your team can reclaim that valuable time.
What is included in SOC audits for service organizations?
SOC2 audits for service organizations are structured in three levels, each serving distinct purposes as listed below:
- SOC 1 Audits: Focus on internal financial reporting (ICFR) control and adhere to ISAE 3402 or SSAE 18 standards.
- SOC 2 Audits: Evaluate security, availability, processing integrity, confidentiality, and privacy controls against the AICPA’s Trust Services Criteria (TSC) following SSAE 18 or ISAE 3000 in the UK. SOC 2 reports are typically used for clients.
- SOC 3 Audits: Similar to SOC 2 but with more concise reports tailored for a broader audience and public consumption.
SOC 1 and SOC 2 audits are categorized into Type 1 (on a specified date) and Type 2 (over a period of time, usually six months minimum). SOC 3 audits are always Type 2. Additionally, the AICPA has introduced SOC for cybersecurity and SOC for Supply Chain.
Who Performs a SOC 2 Audit?
SOC 2 audits are typically performed by certified public accounting (CPA) firms. These firms specialize in conducting audits and have professionals trained to audit an organization’s controls and compliance with SOC 2 requirements.
When selecting a CPA firm for your SOC 2 audit, choosing one with experience and expertise in performing SOC 2 audits is important. Look for a firm with a strong understanding of your company’s specific industry or sector, as this can contribute to a more effective and efficient audit process.
How Much Does SOC 2 Audit Cost?
The cost of a SOC 2 Type 2 report can vary, typically within the range of $7,000 to $50,000. However, the cost is influenced by several factors that are specific to your organization.
First off, size matters. The larger your company, the more complex your systems and controls will likely be. This will again impact the overall cost. Also, your level of audit readiness plays a role.
The more prepared you are with well-documented processes and evidence, the smoother and more cost-effective the audit can be.
The specific TSCs you choose to include in your audit also affect the cost. Depending on your industry or customer requirements, you may select different TSCs, and each one adds a layer of complexity and evaluation to the process.
How Frequently Does the SOC 2 Audit Take Place?
SOC 2 audits are conducted annually. Completing a SOC 2 audit annually offers immense benefits to your organization. It is also common for organizations to perform a SOC 2 Type 2 audit shortly after completing a SOC 2 Type 1 audit.
Sprint through security audits without breaking your stride with Sprinto
Several companies now consider SOC 2 audits to be essential since it enables them a way to prove that their data is being managed and maintained in a secure manner.
Sprinto maps risks to SOC 2 controls and allows you to run automated checks to ensure continuous compliance for your SOC 2 audits.
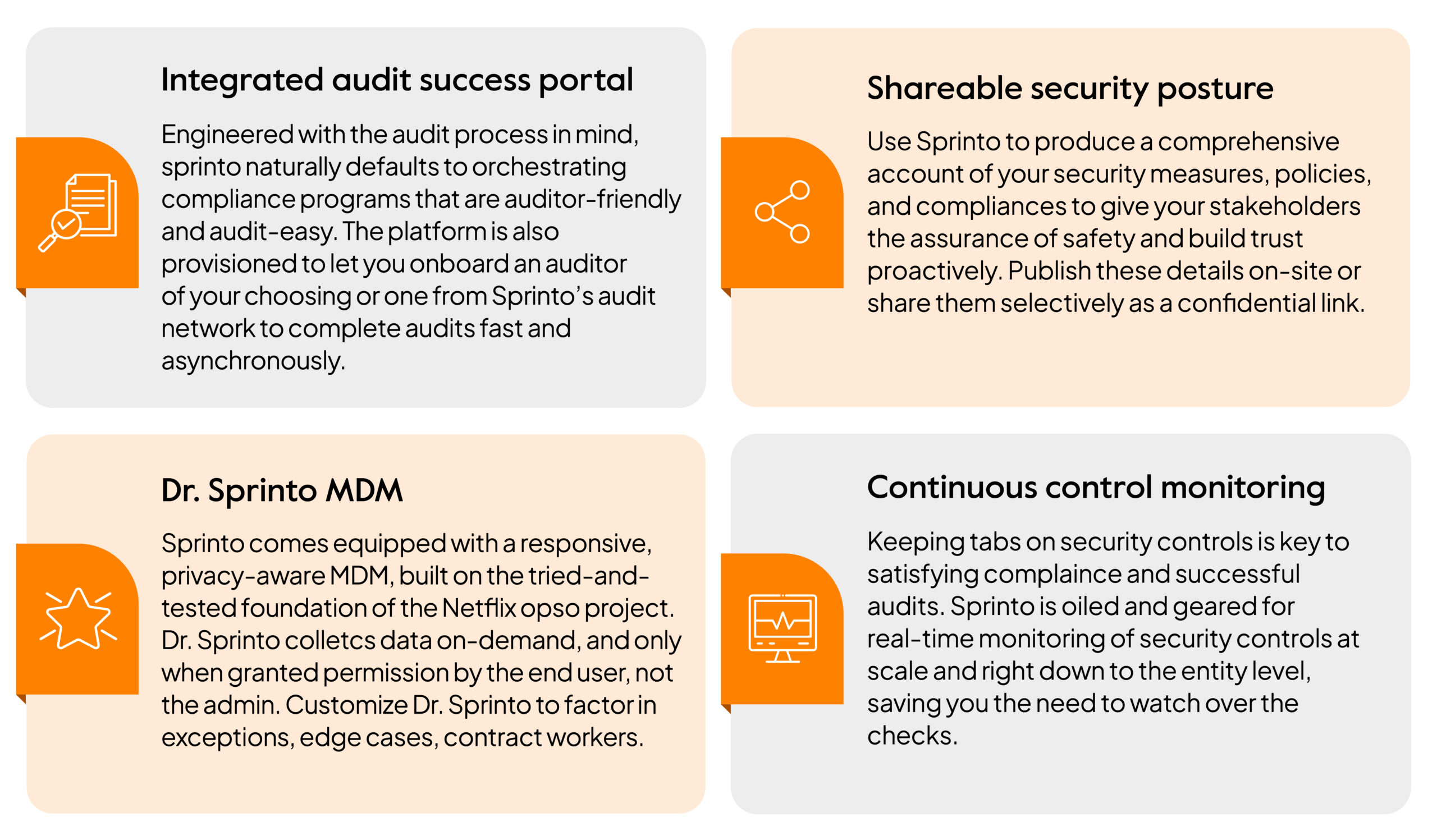
Sprinto has a plethora of features and tools to help organizations maintain regulatory compliance and prepare for SOC 2 audit processes. They include:
- Provides prebuilt, security training modules for SOC 2 audits.
- Sprinto’s risk library aids in locating and putting into place relevant controls to meet SOC2 criteria.
- Sprinto’s centralized compliance plus dashboard aids in gathering compliance evidence in a way that is auditor-friendly.
- Availability of pre-made templates for system descriptions and policies.
- Mobile device management (MDM) built-in for entity health inspections.
Schedule a call with us to know more!
FAQs
What is the difference between SOC 1 and SOC 2 audits?
The difference between SOC 1 and SOC 2 audit is that: Type 1 assesses the design of controls at a specific point in time, and Type 2, evaluates the operational effectiveness of controls over a specified period, usually 6 to 12 months.
Is SOC 2 audit mandatory?
SOC 2 audits are not mandatory in a legal sense, and there is no legal requirement for companies to obtain SOC 2 attestation. However, many businesses, particularly those in the B2B and SaaS industries, often find SOC 2 compliance and certification beneficial.
Who can perform a SOC 2 Audit?
SOC 2 auditing is usually performed by certified public accounting (CPA) firms. These firms specialize in conducting audits and have professionals trained to audit an organization’s controls and compliance with SOC 2 requirements.
How often are SOC 2 audits done?
SOC 2 audit reports are valid for 12 months from the issuance date. It is recommended that organizations conduct a SOC 2 audit on an annual basis to ensure the sustained compliance and robust security of their systems and processes. Regular audits are a proactive measure to uphold a consistent commitment to security standards and demonstrate ongoing adherence to SOC 2 requirements.
What happens if you fail a SOC 2 audit?
In a SOC 2 audit, you do not technically “fail” or “pass” the audit. The purpose of a SOC 2 audit is to evaluate the design and effectiveness of your controls and provide an opinion on your system’s adherence to the TSCs.


Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.




























