SOC 2 Compliant Data Centers – Quick Guide
Meeba Gracy
Mar 04, 2024
Data is at the heart of every modern business—not only does it dictate their every move, but it also forms the basis of their evolution. As the business scales, the volume of data it handles grows. And so, it becomes vital that companies safeguard and manage this precious resource to maximize profitability. One solution that modern businesses have found and largely adapted to is data centers.
Although data centers are fortresses, they still require constant protection from cybersecurity threats. One of the ways data centers can provide their customer with better protection is by getting certified with frameworks like SOC 2.
Becoming SOC 2 data centers (certified) allows you to keep abreast of the evolving threat landscape, protect yourself against malicious activities, and ensure high security and availability of your data and applications.
This article explores what SOC 2 data centers are and the benefits of being SOC 2 compliant.
What are SOC 2 data centers?
SOC 2 data centers are facilities that adhere to the standards set forth by the Service Organization Control (SOC) 2 framework. It demonstrates that a data center has established and maintained effective controls related to security, availability, processing integrity, confidentiality, and customer data privacy.
Why is it crucial for data centers to be compliant?
Data centers must be compliant because it helps safeguard the data against potential data breaches. Enhancing the security posture by being compliant with regulatory frameworks fortifies them against the sea of cyber threats waiting to exploit weaknesses in the system.
Here are some consequences you can expect if your data center is not compliant with a framework like SOC 2:
1. Legal consequences
Failure to comply with key regulations can lead to significant fines and legal ramifications. Penalties can vary based on the seriousness of the violation and the industry, sometimes exceeding $1 million or more.
Note: On average, the fines imposed reached a staggering $145.33 million.
Regulatory authorities are vigilant about enforcing security standards, and data centers that fall short may incur severe penalties.
2. Reputational damage
Warren Buffett says, “It takes 20 years to build a reputation and five minutes to ruin it.”
The impact of a cybersecurity breach and the penalties faced by noncompliant data centers are tangible. However, the less quantifiable aspect is the harm to reputation caused by non-compliance lawsuits.
In this age, news of legal violations spreads rapidly through digital media channels.
So, reputational harm is a significant negative performance area that the centers will have to deal with due to non-compliance. Data breaches and incidents when meeting compliance standards are the factors that quickly mint customer distrust and shatter the data center’s reputation.
3. Operational disruptions
Data centers are power intensive—they require a consistent and dependable power supply. Any power outages or fluctuations can cause operational disruptions, availability issues, and performance challenges, potentially leading to data loss.
Managing these issues requires careful operational planning, backup management, and frequent maintenance activities.
4. Loss of sensitive data
Data exposure occurs when sensitive information is inadvertently leaked. Data exposure is distinct from a data breach, where unauthorized individuals or groups intentionally obtain private data during an attack. Exposure typically results from a company’s actions or negligence.
The loss of sensitive data due to non-compliance can have serious repercussions for individuals and businesses alike. It can result in identity theft, financial fraud, and various other issues for those impacted.
Get SOC 2 compliant on a budget. Speak to our experts
Requirements of SOC 2 for data centers
Becoming a compliant SOC 2 data center is an achievable goal, but first, you need to meet the rigid requirements of SOC 2. However, your compliance with this framework will depend on how thoroughly you adhere to the Trust Services Criteria. To get more details on which applies to you, here are the 5 TSCs you need to follow:
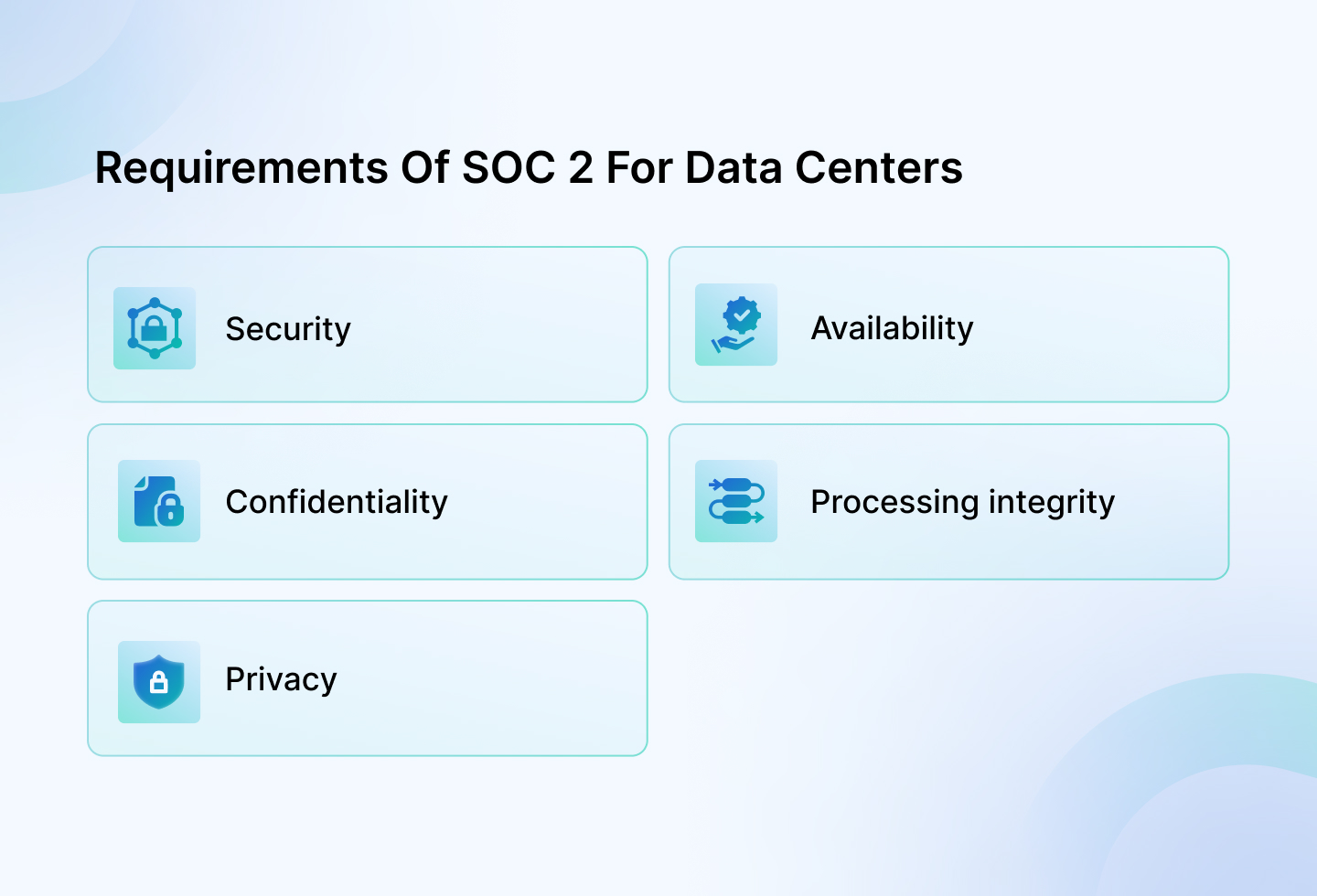
1. Security
The security principle evaluates the data center, your systems, and information fare against unauthorized access. This principle upholds the importance of protecting data and systems against unauthorized entry.
To that end, it requires implementing physical and logical access control measures and identity management systems so that only the right people can access data.
Also, enhance firewall security for stricter inbound and outbound rules. You can deploy intrusion detection and recovery systems as well.
2. Availability
In the data center industry, service incidents like outages happen occasionally. It’s just a part of the deal—you can’t promise 100% system uptime.
To address this, you need controls like network performance monitoring and disaster recovery procedures. This helps ensure your systems can bounce back quickly from any hiccups.
These criteria also look at how your business handles security incidents. Having policies in place for backup, data recovery, and business continuity is essential to meet the SOC 2 trust service criteria for availability.
3. Confidentiality
As a data center company, handling user data is natural, but it’s crucial to handle it carefully.
Privacy is one area where confidentiality comes in handy; it is specifically used to veil your vital details from all observers. To keep confidentiality among the highest, only a few employees and limited users should have access, the data should be kept in private servers, and its use should be monitored.
There are two specific criteria for confidentiality:
- C1.1: Put protocols in place to safeguard the confidentiality of information if it is destroyed
- C1.2: Create policies that will allow you to get rid of such personal information safely and legally when it is no longer needed
Also read: SOC 2 Compliance Requirements
4. Processing integrity
Processing integrity helps in making sure your data processing is accurate and complete.
This principle checks if your cloud data is handled accurately, reliably, and on time. It also examines whether your systems are doing what they’re supposed to do.
You can use quality assurance procedures to monitor how your data is processed to keep things in check.
5. Privacy
Here’s an interesting fact: for every dollar you invest in data privacy, your organization gains $2.70 worth of improvements in data loss prevention, agility, risk mitigation, and customer loyalty.
This trust service criteria (TSC) focuses on protecting Personally Identifiable Information (PII) from breaches and unauthorized access. It does this by setting up strict access controls, using two-factor authentication, and encrypting sensitive data.
Automate SOC 2 compliance effortlessly
How can data centers be SOC 2 compliant?
As a data center, if you are thinking of attaining SOC 2 certification on any of the trust service criteria, you must implement some steps before that.
Here are some helpful steps that will get you there:

1. Preparation and scoping
Preparation involves tasks like creating policies, documenting procedures, and establishing new processes. Having some experience with similar security frameworks can make it easier to implement SOC 2.
SOC 2 scope is about defining the parameters for evaluating the effectiveness of controls during the audit. It clarifies which controls and systems of the service provider will be assessed to ensure the protection of customer data.
We’ll talk about which SOC 2 controls apply to you in the next step.
2. Choose which TSCs apply to you
As a data center, only two sets of SOC 2 security controls have implications for containers and the cloud. The first set deals with logical and physical access control, while the second focuses on system operations.
Logical and Physical Access Control Family:
Access control comes in two types: physical and logical. Physical access control restricts entry to places like campuses, buildings, rooms, and physical IT equipment.
On the other hand, logical access control regulates connections to computer networks, system files, and data.
This family includes six controls relevant to container and cloud environments:
| CC6.1 | Ensure tools are in place to protect against security events |
| CC6.2 | Detect and block unauthorized access attempts |
| CC6.3 | Prevent attempts to bypass access control mechanisms |
| CC6.6 | Detect unauthorized network connections using networking monitoring tools |
| CC6.7 | Securely manage secret data (e.g., passwords) |
| CC6.8 | Detect and prevent deployment of malicious software |
System Operations Control Family:
SOC 2 refers to a set of criteria or controls related to the operation and management of a service organization’s systems. These controls focus on ensuring that the systems are effectively monitored, maintained, and controlled to meet the organization’s objectives and commitments to clients.
Under this family, there are two controls to follow:
| CC7.2 | Detect anomalies indicating security events by collecting and analyzing data logs |
| CC7.3 | Evaluate security events to understand their impact by correlating various data sources |
The Sprinto advantage
Instead of spending time and effort deploying and monitoring controls manually, it’s much smarter to invest in a compliance automation platform like Sprinto.
With Sprinto, controls from TSCs are automated, saving you from tedious work. You can easily label your data assets and set security criteria for each.
For example, you can exclude certain data assets from the audit process, making compliance management a breeze.
Here’s an example of a client who chose Sprinto:
3. Conduct a SOC 2 readiness assessment
You’re almost ready to go, we assure you. A readiness assessment conducted by an independent auditor determines how prepared your data center company is for a successful SOC 2 audit. It helps you understand if your current controls are sufficient for compliance and identifies any gaps that need fixing before the audit.
Here’s what a readiness assessment helps you with:
- Assessing your company’s readiness for a SOC 2 examination
- Evaluating if your existing controls demonstrate compliance
- Identifying and addressing any gaps in your controls
- Creating a plan to fix those gaps and ensure they’re resolved
- Reviewing if your audit scope aligns with the controls
- Examining your documents and evidence
- Getting insights into your overall security posture
- Communicating observations and suggestions to your organization’s leadership
The Sprinto advantage
With Sprinto, you can access a dashboard that shows your SOC 2 audit readiness percentage, along with a breakdown of passing or failing controls, critical scanning results, and pending test activities. It also provides an overview of responsibilities at the entity level.
Entering your SOC 2 compliance with Sprinto means being fully prepared. Its user-friendly interface makes evidence collection, control mapping, and documentation easy and accessible with just a click.
4. Remediate the gaps identified
After identifying the gaps from the readiness assessment, your next step should be to design a plan to fill these gaps. This will help mitigate the situation and strengthen your defenses, especially in places that are at risk of malicious attacks or any other security issues.
Creating a rock-solid remediation plan allows you to address any gaps and ensure the security and integrity of your operations.
Get SOC 2 compliant with ease
5. Conduct an internal audit
After establishing a SOC 2-compliant system and remediating the gaps, you need to conduct an internal audit. This internal audit ensures that your access and compliance controls are in place, prevent unauthorized access, and stay in place for the long run.
The Sprinto advantage
Sprinto offers a continuous internal audit of your SOC 2 controls and provides real-time updates on the status of checks to your key stakeholders. This means you only need to spend a few hours each week to keep your organization audit-ready.
If you encounter any challenges, Sprinto’s in-house compliance experts are just a call away to assist you.
6. Get ready for external audit and get certified
In order to prepare for the external audit and to obtain the certification, you should first look for a respectable auditing company with the experience of working with organizations like yours. Check reviews on different sources and inquire about procedures and their methods.
- Schedule a date to conduct the test
- Request a list of evidence for your controls
- Test the processes, document them, and address any issues that arise
- Create and deliver the final report
The Sprinto advantage
With Sprinto, you can access a network of experienced auditors tailored to your specific needs. Once the SOC 2 Type 1 audit is complete, you can publicly showcase the results using Sprinto’s Trust Center feature.
The Sprinto Trust Center provides a personalized and customizable portal where you can easily display governance policies, documents, reports, and certifications for customers to view.
How long does it take to become compliant?
The time it takes to become compliant varies a lot. The whole process might take a few months to a year, from planning your report to going through a SOC 2 audit.
However, it also depends on how ready and cooperative your data center provider is in providing the required information.
Usually, the actual audit meetings can wrap up within a week, covering all the necessary areas. But again, the overall timeline can change based on how big the audit is and if your team can meet with the auditors during that same week.
Bonus: Here’s a SOC 2 Compliance Checklist for you.
Download Your SOC 2 Compliance Checklist
How much does it cost to become SOC 2 compliant?
The cost of becoming a SOC 2 compliant data center depends on a lot of factors. However, the cost averages between $7500 and $50000. Here are some factors that affect the cost of SOC 2 certification.
- Size of your organization
- The complexity of your operations
- Maturity of your security controls
- Number of in-scope Trust Service Criteria
- Whether you choose a Type1 or Type 2 report
- Cost of your chosen auditor
Other costs of SOC 2 certification
| Staff Training | $25 per user |
| Security Tools | $6000 to $25000 |
| Readiness Assessment | $10000 |
Your SOC 2 Compliance Cost, Revealed in Minutes. Calculate Now
Benefits of being SOC 2 compliant data center
The benefits of being SOC 2 data center far outweigh the initial investment you have to make. When you undergo the audit and get certified, you’ll be able to demonstrate that you provide a fully secure service and the highest degree of security.
- As a data center company, having a SOC 2 certification shows that you have a strong evidence base and have taken all the necessary measures to prevent a data breach.
- With so much at stake, a SOC 2 attestation will definitely give your data center a competitive edge and increase prospect appeal.
- Usually, SOC 2’s requirements and controls dovetail with frameworks like ISO 27001 and HIPAA. So, being SOC 2 compliant means it can speed up your overall compliance efforts.
- A SOC 2 report will provide you with crucial security insights. Moreover, you will have greater visibility into your system’s internal controls, vendor management, etc.
- A SOC 2 certification will help you reduce costs and avoid expensive security breaches. This is because a single data breach can put you back many years.
How Sprinto can support SOC 2 compliance for your data center?
Becoming a SOC 2 data center manually can be a real struggle—it can eat up time that you could be spending on growing your business.
What if there was an effortless solution to handle all those tedious tasks? Well, there is.
With Sprinto, you no longer have to worry about tedious compliance work. Our continuous monitoring feature ensures your compliance stays ahead at every turn. Do away with long policy acknowledgments or manually check whether controls pass or fail tests.
Sprinto centralizes everything within a single dashboard, making it centralized in action tracking, process management, and issue resolution. Your security teams are alerted when controls are about to fail, allowing you to take action before the problem arises.
Ready to take your first step? Speak to our experts today.
FAQs
1. How long is a SOC 2 type 2 report valid?
A SOC 2 type 2 report is valid for 12 months from the date of issue. This means that you need to have an evaluation every year.
2. What is a SOC 2-certified data center?
A SOC 2-certified data center is a company that underwent SOC 2 auditing procedures and can demonstrate that they securely manage your data and the privacy of clients.
3. Who needs SOC 2 certification?
SOC 2 certification is beneficial for those service organizations that store, transmit, or process any kind of client data.
4. Who can perform a SOC audit?
SOC 2 audits are performed by independent CPAs (Certified Public Accountants). This is according to the standards set by AICPA.


Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.


























