ISO 27001 is the centerpiece of the ISO 27000 series of international standards. In brief, the framework, formally known as ISO/IEC 27001:2022, establishes guidelines for developing, implementing, and maintaining an Information Security Management System (ISMS). Doing so not only helps the organization demonstrate compliance with international data security standards but improves its security posture.
Aligning your organizational controls and policies with the requirements of the ISO 27001 certification comes with a host of benefits—from securing assets and the business environment to enabling business and lending competitive advantage. In this blog, we explore the complete list of ISO 27001 policies and the steps to implement them.
What are ISO 27001 policies?
ISO 27001 policies are foundational documents defininig the organization’s protocol and information management practices that your ISMS is built on. And so, every policy undergoes meticulous definition, rigorous management reviews, approvals, and revisions to keep the ISMS updated. An organization’s policies are largely driven by business requirements, legal and legislative mandates, and regulatory requirements.
ISO 27001 mandates that organizations maintain transparency and communicate with stakeholders, customers, and senior management about their policies. Organizations are often requested to have their policies furbished as a part of their contract requirements.
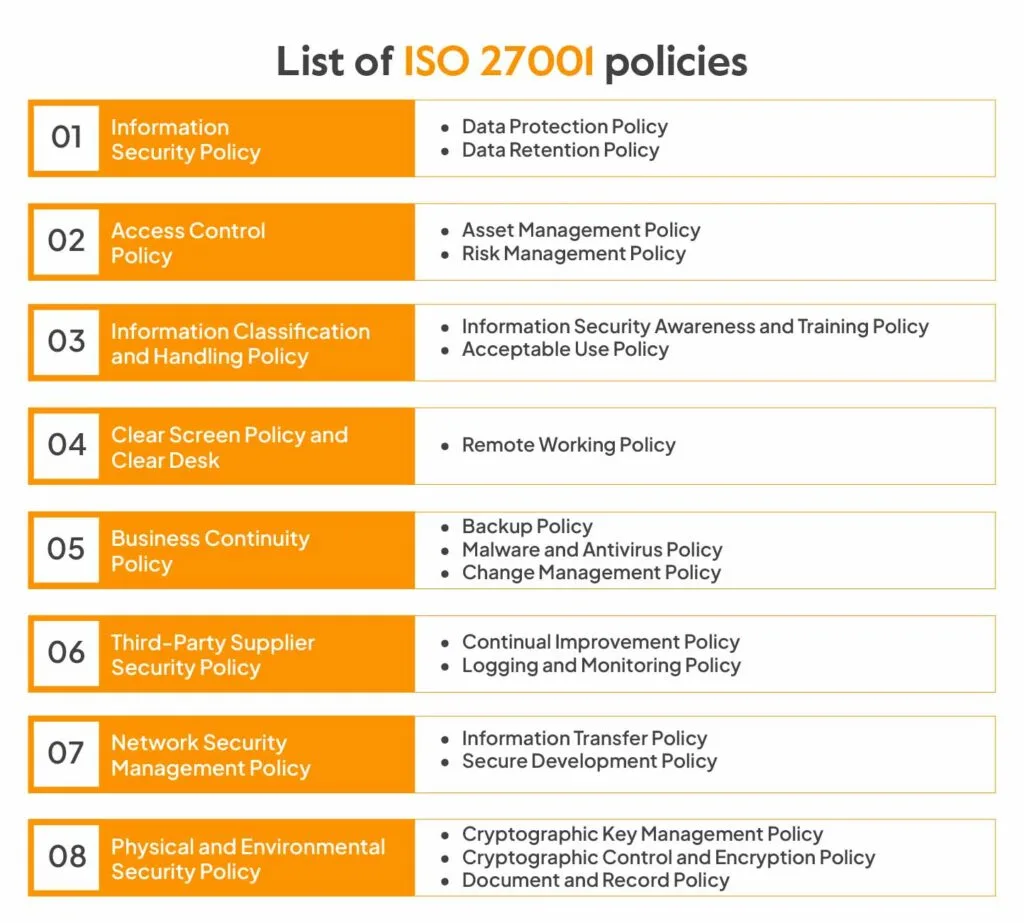
List of ISO 27001 policies
The ISO 27001 certification audit process is a tedious one, a large chunk of which goes into policy creation and implementation. In this section, we discuss key ISO 27001 policies and give you an overview of what each one covers.
Need ISO 27001 fast? We can help
Information Security Policy
In its essence, the information security policy lays down the foundational groundwork and stance for how the company manages information security. It covers basic principles, legalities, management commitment, security objectives, roles, and responsibilities with respect to information security.
Data Protection Policy
The data protection policy primarily ensures that organizational data has sufficient safeguards in place through the implementation of security controls that are in line with compliance and legal standards.
Data Retention Policy
The data retention policy defines the limitations regarding the storage, retention, and deletion of sensitive data collected by the organization within legal and operational requirements.
Access Control Policy
The primary aim of the access control policy is to ensure that access to organizational data and resources is granted only to personnel with authorized permissions and privileges. The policy covers key aspects such as user registration, authentication requirements, review of access and privileges, reporting, and external access control.
Automate ISO 27001 compliance with the help of Sprinto
Asset Management Policy
The asset management policy aims to enable the identification, protection, and management of key organizational assets. It covers key aspects throughout the asset lifecycle, namely, classification, allocation, inventory, ownership, and return.
Risk Management Policy
The aim of the risk management policy is to help an organization identify risks, assess and review impact, risk register, implement risk treatment plans, and report on security risks to key assets while understanding it’s risk appetite.
Information Classification and Handling Policy
The information classification and handling policy is a key policy that defines how the organization classifies, stores, processes, backs up, transmits, and purges information. It also covers roles and responsibilities that employees need to be aware of to protect sensitive information.
Information Security Awareness and Training Policy
The information security awareness and training policy ensure that employees receive appropriate security and awareness training, are kept abreast with the risk, and know to respond to them as they arise. This policy additionally covers creating training plans and assessment modules for internal employees as well as external third parties.
Acceptable Use Policy
The acceptable use policy helps organizations to ensure internal employees and external stakeholders are aware of individual responsibility, the appropriate use of organizational assets related to information processing, intellectual property, reporting, and monitoring.
Clear Screen and Clear Desk Policies
The purpose of the clear desk and clear screen policies are to prevent unauthorized access to internal systems, resources, and assets as well as the resulting loss or damage during and over standard working hours at the workplace.
Remote Working Policy
The remote working policy helps organizations identify and mitigate security risks of remote work that are introduced through the usage of personal devices as well as set protocol on how information is collected, processed, and stored off-premise. The remote working policy covers aspects of device registration, firewalls, network security, remote access, owner responsibilities, and data backups.
Business Continuity Policy
The business continuity policy focuses primarily on restoring and maintaining business continuity in the face of disruptions or security incidents of any nature. The policy outlines elements of impact analysis, continuity testing, business continuity plans, recovery and restoration, incident management, disaster recovery plans, and escalation.
Here is a sample incident management policy you can download:
Download Your Incident Management Policy Template
Backup Policy
An organization’s backup policy outlines the protocol that employees should follow in order to prevent any loss of data. It entails procedures that come into effect when disruptions occur and highlights tactics that help with conduct, test, and deploy backup instances to restore business continuity.
Malware and Antivirus Policy
The malware and antivirus policy helps organizations educate employees about viruses and malware as well as how to mitigate damage as a result of such threats. In essence, the malware and antivirus policy covers details such as acceptable software usage, system configuration management, antivirus software specifications, security awareness, integrity, network intrusion, etc.
Change Management Policy
The aim of the change management policy is to facilitate smooth operational transitions and mitigate the impact of risks posed by carrying out changes in the company. The change management policy details everything from change requests, classification, approvals, prioritization, security risk assessment, impact assessment, version control, testing, rollbacks as well as aspects of emergency change management and reporting.
Third-Party Supplier Security Policy
A company’s third-party security policy specifically focuses on ensuring third-party vendors and registered, onboarded, and implement sufficient safeguards in place throughout their lifecycle. It also ensures that third-parties collect, process, transmit, and store data in a secure manner and in accordance with compliance requirements.
Continual Improvement Policy
One of the crucial elements of ISO 27001 standard is its focus on continuous improvement. The continual improvement policy lays emphasis on suitability which is facilitated by periodically reviewing the effectiveness and adequacy of the information security and the implemented ISMS.
Logging and Monitoring Policy
The logging and monitoring policy enables the identification and management of risk systems through thorough audit logging and monitoring procedures. The policy covers all aspects of event and activity data, its collection, logging, processing, analysis, and storage as well as maintenance of access control and protection of such data.
Network Security Management Policy
The network security management policy is a security policy document specifically designed to safeguard network infrastructure as well as the data nested in them. It also provides guidelines on network controls, segregation, access, physical devices, locations, and secure processing of data.
Information Transfer Policy
The aim of the information transfer policy is to ensure an organization follows the right protocol when data is in transit, ie, when information is being transferred internally or externally. The policy covers data transfer methods, encryption methods, and loss of information.
Secure Development Policy
The secure development policy is a vital policy that ensures information security best practices are ingrained throughout the development lifecycle. Broadly, the policy covers topics related to segregation of environments, coding guidelines, development code repository, approvals, code reviews, testing, test data management, and moving code to production.
Physical and Environmental Security Policy
The physical and environmental security policy primarily lays emphasis on the prevention of unauthorized physical access to the organization’s data as well as its data processing facilities. It covers key topics such as physical security, employee access, network access control, visitor access, etc.
Cryptographic Key Management Policy
The cryptographic key management policy aims to ensure that encryption keys are safeguarded throughout their lifecycles—from generation, distribution, storage, escrow and backup while also ensuring accountability and regular audit management. It also lays down the protocol for when keys are compromised and how to recover them.
Cryptographic Control and Encryption Policy
The cryptographic control and encryption policy outlines the processes involved in the effective implementation of encryption while safeguarding the integrity and confidentiality of sensitive information. It includes guidelines on encryption algorithms, web and cloud encryption, wireless encryption, email encryption, cardholder data, data in motion, database encryption, mobile and laptop encryption, etc.
Document and Record Policy
The aim of a document and record policy is to help organizations keep track of documents and records within the Information Security Management System. It lays down foundational guidelines for creating and managing documents while ensuring the availability, security, confidentiality, and integrity of documentation. It also defines how an organization needs to conduct key tasks such as version control, approval, and classification of key documents.
Understanding policy requirements of ISO 27001 clause 5.2
As per Clause 5.2 of the ISO/IEC 27001:2022, top management is responsible for establishing an information security policy that:
- Is suitable to the purpose of the organization (ISO 27001 Clause 5.2a)
- Provides the framework for setting information security control objectives or includes information security objectives (ISO 27001 Clause 5.2b)
- Includes a commitment to fulfill applicable requirements related to information security (ISO 27001 Clause 5.2c)
- Includes a commitment towards the continual improvement of the ISMS (ISO 27001 Clause 5.2d)
- Is accessible as documented information (ISO 27001 Clause 5.2e)
- Is shared within the organization (ISO 27001 Clause 5.2f)
- Is made accessible to interested parties as appropriate (ISO 27001 Clause 5.2g)
A nine-step guide to implementing ISO 27001 policies
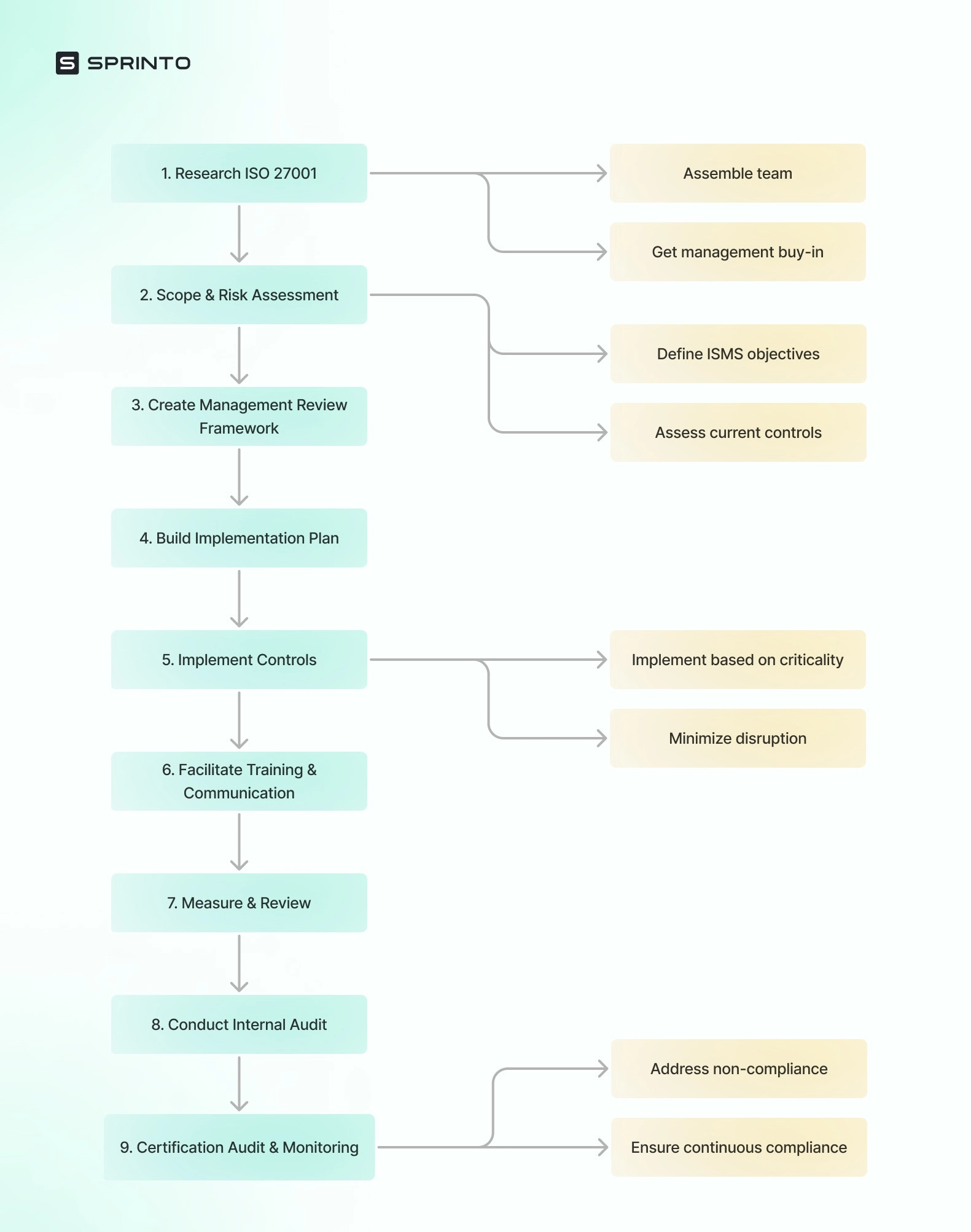
Implementing ISO 27001 policies requires a lot of groundwork. We’ve broken this down into a simple nine step process.
Research the ISO 27001 standard
Spend some time to research the ISO 27001 standard. Gaining a deeper understanding of the standard helps break down requirements and interpret them within the context of the organization. Make sure to assemble an implementation team that is trained on their roles and responsibilities, as well as know how to execute policy making. Management buy-in is also a crucial step to initiating implementation.
Scope and risk assessment
The next step in establishing strong ISO 27001 policies is understanding the scope of objectives of the ISMS policies. Conduct a thorough risk assessment to understand the current status of security controls against the requirements of ISO 27001. The organization will also need to take crucial decisions on tolerating, treating, terminating, and transferring risk based on these findings.
Create a management review framework
Upper management has a crucial role in policy creation and implementation. They often create foundational policies that form the bedrock of other policies and functions within the ISMS. They also play a crucial role in reviewing policies periodically, handling emergency changes, and rolling out updates as and when required.
Build an implementation plan
Charting an implementation roadmap is a vital step in creating an effective list of policies. The plan needs to specify owners for each process, enlist timelines and checkpoints, and help employees understand the need for change and the risks associated with not pivoting effectively.
Implement controls
Once all the groundwork and research has been completed, it’s time to flesh out controls and implement policies across the organization. This step essentially entails facilitating large-scale change. Changes that are likely to impact operations at a granular level. And so, it’s important to carry out these changes based on criticality while also ensuring disruptions are kept to a minimum.
Facilitate training and communication
Training and facilitation is an integral aspect of the ISO 27001 standard. Staff and process owners will have to undergo mandatory security training to ensure they are aware of their roles and responsibilities within the security framework of the organization. A clear path of communication will also have to be established in order to help employees gain access to training material and resolve any queries they may have.
If you’re looking for a tool that speeds up the ISO 27001 certification process, Sprinto has you covered. As an intuitive compliance automation platform, it provides you with out-of-box policy templates that you can customize based on your organization’s needs. It also helps you schedule employee training and rollout policies to ensure effective implementation. It also automates key tasks such as evidence collection, significantly reducing the time you need to get audit-ready.
Take a step in the right direction. See Sprinto in action.
Measure and review
Reviews, updates, and improvements are a regular part of the ISO 27001 standard. This means organizations will need to constantly monitor their ISMS for effectiveness and adherence to compliance requirements. This not only helps identify misses or lapses in security but also highlights improvement to existing policies and controls.
Conduct an internal audit
An internal audit is a great way to gain an independent assessment of the effectiveness of the ISMS. The exercise will need to be planned, executed, and meticulously documented to ensure potential gaps and risks are identified, addressed, and resolved as soon as possible before an external certification audit.
Organize a certification audit and monitor controls
The external audit is the first segment of the final step. The certification audit is conducted by an external auditor and assesses an organization’s evidence of compliance against the requirements of ISO 27001. The documentation highlights areas of major non-compliance, minor deficiencies, and areas of improvement. These policy or controls changes need to be made and re-evaluated before the certification is published. The organization will also have to monitor policies and controls regularly after the external audit to ensure continuous compliance.
Accelerate audit readiness with Sprinto
With a total of 28 base policies and considering policy writing takes about 7 hours per policy, the estimated time to fulfill these is about 200 hours. This is no simple task and organizations often spend a lot of time on gaining certifications instead of mission-critical tasks. And that’s just half the problem. These endeavors can be incredibly costly if not managed correctly.
Sprinto’s powerful automation capabilities help you implement security controls and policies with ease. The platform seamlessly integrates with any setup and tech stack, allowing you to monitor entity-level risk from within a single dashboard. It also notifies security teams when controls are about to fail so they can initiate remediation action without delays. In essence, we help you cut short the certification process from months to weeks.
Don’t believe us? Click here to find out how Sprinto helped OfficeBeacon achieve ISO 27001 audit-readiness in 2 weeks.
Ready to get started? See Sprinto in action.
Frequently Asked Questions
What are the different ISO 27001 audit categories?
There are four main audit categories for ISO 27001—certification audit, surveillance audit, internal audit, and recertification audit. Each of these audits are unique and important in their own ways and need to be performed correctly for the business to achieve and maintain certification.
What are the three pillars of ISO 27001?
The three pillars of the ISO 27001 standard are referred to as the CIA triad. CIA refers to an information security model composed of three main elements—confidentiality, integrity, and availability.
What are the six main security areas covered by ISO 27001?
The six primary security areas covered by the ISO 27001 standard are company security policy, asset management, physical and environmental security, access control, incident management, and regulatory compliance.
Vishal V
Vishal, Sprinto’s Content Lead, masterfully weaves nuanced narratives and simplifies convoluted compliance topics with seasoned expertise. His perennial curiosity fuels his pursuit of fresh angles in every piece. Off-work, he’s an avid photographer, birder and a music buff, he blends expertise and exploration seamlessly in work and life.
Explore more ISO 27001 articles
ISO 27001 Overview & Requirements
ISO 27001 vs Other Frameworks
ISO 27001 Audit & Certification Process
ISO 27001 Management & Assessment
ISO 27001 Implementation & Automation
ISO 27001 Industry-Specific Applications
research & insights curated to help you earn a seat at the table.











