List of Evidence Collection for Compliance
Payal Wadhwa
Oct 15, 2024
You know it’s audit season when there’s an influx of requests for evidence. Feelings of apprehension are in the air. Having all your evidence organized and readily available is the only thing separating you from a stress-free audit.
Given that data is scattered across multiple systems and sources, it becomes imperative to have a well-structured process around evidence collection. This ensures a high level of preparedness.
Transcend evidence collection barriers with our curated list of necessary documents and discover ways of evidence collection.
What is meant by evidence collection under compliance?
Evidence collection is the process of gathering and documenting data, records and other compliance process proofs to demonstrate adherence to rules, regulations and standards.
List of evidence of compliance
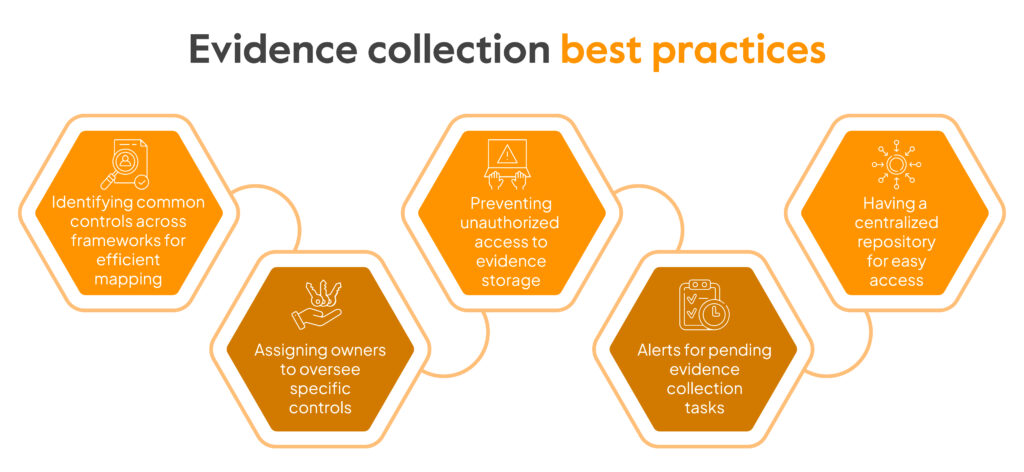
It is vital to include evidence collection within the process of compliance prep. Not only does it lay the foundation for a robust compliance program but when done right, it can save stakeholders a lot of time and effort.
Listed below are the main evidence documents that’ll help you get started. The requirements may however not just be limited to this list.
Here is the list of 8 evidence of compliance:
1. Policies and standard operating procedures
Policies and procedures are non-negotiable aspects of evidence. The accuracy of infosec policies is evaluated based on their alignment to the assessment requirements.
It is also necessary to submit proof of policy acknowledgments by all employees to ensure their awareness. If there are any policy or procedural updates, these must be documented to clearly bring out the changes from previous versions.
2. Audit trails and logs
Audit trails and logs are records of detailed actions initiated by users or systems with timestamp accuracy. If there have been any previous audits, the audit findings including major areas of non-compliance, minor non-conformities and improvements must be documented.
Records of corrective action initiated after the audit findings must also be maintained. Additionally, policies regarding retention of these logs as per regulatory requirements must be in place.
For example, in the case of HIPAA, the log retention requirement is 6 years.
3. Training records
In order to build a compliant organization, it is necessary to have a well-informed workforce. Publishing awareness training for all employees and logs of training completion serve as documented proof. It helps validate employee competency and their understanding of the regulations.
Automate compliance evidence collection process with the help of Sprinto
4. Testing and validation reports
In order to assess the quality of current practices, controls, and processes, a series of testing and validation rounds is conducted.
Reliable and transparent knowledge transfer is facilitated by detailed documentation of the test plan, test data, code or instructions used for execution and the key results. The validation summary ensures conformity with standards or regulatory requirements and streamlines the audit process.
5. Incident response plans
An organization must produce evidence of the incident response plan. This should include documentation on the incident response team with clearly defined roles and responsibilities.
Additionally, it must have details on incident identification process, escalation, and mitigation procedures as well as post-incident reporting. To help understand an organization’s preparedness for security event handling, key learnings and improvement areas must be highlighted
6. Change management policies
Change management policies are required when making strategic imperative changes to systems, processes etc. These changes can include system or technology upgrades, organizational restructuring, infrastructure additions or other changes that may impact compliance efforts.
Necessary evidence includes documenting the overall strategy, impact assessment, management review, process and post-implementation review.
7. Risk assessments
For risks, assessing precedes addressing. At the onset of your compliance efforts, it is crucial to understand the compliance risk universe in order to address regulatory shortcomings.
The risk assessment procedure, gap analysis report, tactical plan for mitigation and the evidence of corrective action must be produced to support compliance audits. The auditor can track progress and connect the dots with respect to various decisions and actions initiated by the organization.
8. Third-party agreements
Third-party agreements help in understanding vendor due-diligence and risk mitigation associated with their services. These agreements make it easier to comprehend business relationships, reinforcing that the organization has initiated necessary steps for vendor risk management.
Also, check out how to conduct an internal audit
What are the ways to collect evidence to prove compliance?
Compliance necessitates the establishment of a solid evidence base. Organizations can choose to go manual and collect documents, conduct interviews, and opt for other traditional methods or can leverage technology for automated evidence collection.
Here are the 8 ways to collect evidence of compliance:

Manual methods
Documentation review
All the relevant compliance documents are referred and cross-referred to validate accurate representation. Organizations also assess completeness of documents and adequacy as per compliance requirements. The findings are recorded and a final summary documenting any areas of concern is drafted.
Observation and Inspection
Observation involves actively looking around and noting things in real-time. The observer witnesses’ procedures, behaviours, tests of controls and adherence to practices firsthand and verifies compliance.
Inspection on the other hand primarily involves the examination of records, documents, and test results. It does not require a physical presence at the time of control testing but acts as a confirmation that the procedure was performed and recorded accurately.
Interviews and surveys
Interviews involve direct conversations with employees and relevant stakeholders to gather information regarding processes, responsibilities etc. and other compliance functions. The discussions are then validated against the documented policies and procedures.
Surveys involve circulating questionnaires to employees, vendors or any other important stakeholders related to compliance activities. These are particularly used for large-scale companies for collecting and analyzing data.
Using tools
According to a report by Telos, IT professionals receive about 17 evidence requests every quarter and it takes them 3 working days to respond to one single request!
Since compliance isn’t a one-and-done task, manual methods of evidence collection can prove cumbersome. Here are some examples of tools that can help with gathering evidence:
Risk management tools
Risk management tools serve as a valuable resource in documenting risk assessment procedures, capturing mitigation activities and providing evidence of corrective action. By acting as a centralized repository of risks involved, these tools provide a comprehensive view of the security stance.
Vulnerability management tools
Vulnerability management tools scan vulnerabilities across systems, networks and applications serving as a single source of truth for identified weaknesses. These tools offer the functionality to track remediation progress as evidence and support compliance reporting processes.
Data collection and analytics tools
Data collection and analytics tools gather data from multiple sources and employ various techniques for analyzing and correlating information. These tools facilitate identification of patterns and anomalies as well as generating compliance-specific reports.
Compliance automation tools
Compliance automation tools streamline compliance-related activities including evidence collection. These tools fortify security defenses through continuous monitoring, proactive alerting about issues and capturing evidence of corrective action taken.
Sprinto is the #1 rated compliance automation tool facilitating cybersecurity monitoring and automated evidence collection.
How does evidence collection help prepare for compliance audits?
Different sets of regulations and standards require organizations to conduct numerous checks and demonstrate posture appropriateness. By continuously collecting evidence, organizations can validate their progress and effectively prepare for the desired outcome-passing the audit.
Here’s a lowdown on how evidence collection helps prepare for a compliance audit:
Supports assertions
Scheduling the final compliance audit indicates that the organization is ready to make confident compliance assertions and claims. The collected evidence serves as a credible source of truth to validate these assertions.
Gives insights about remaining weaknesses
Evidence is collected after corrective actions have been initiated but there can still be persistent issues. That is why the cycle of improvement is always ongoing. The evidence gives a quick snapshot of any remaining gaps in the compliance efforts.
Expedites the audit process
Well-structured and comprehensive evidence collection minimizes the effort and delays involved in going back and forth with follow-up requests. The auditor doesn’t have to perform detailed tests in all departments and can focus on assessing controls in key areas.
Also read: Guide to continuous compliance
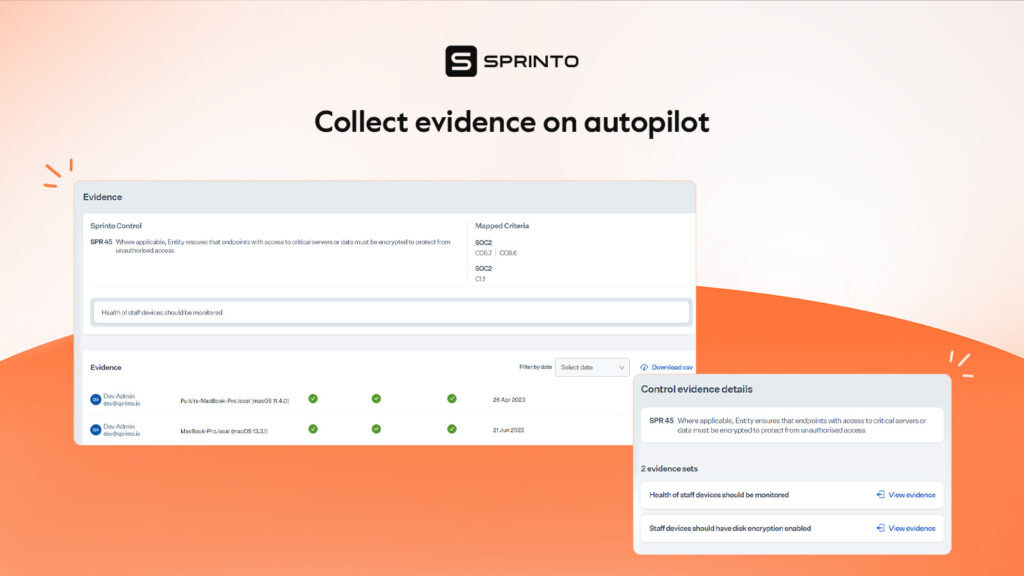
Automate evidence collection with Sprinto
Manual evidence collection involves repetitive entries into excel spreadsheets, capturing screenshots, managing befuddlement related to standardization and version controls and dealing with human errors. Sprinto takes the hassle out of evidence collection by automating the entire process. This saves the bandwidth of engineering staff for mission-critical work.
Here’s what automated evidence collection looks like with Sprinto:
- Real-time and audit-friendly evidence collection is ensured against every corrective action.
- There’s mapping of evidence against each control/requirement.
- The dashboard facilitates time travel for each evidence.
- Each evidence is available in a verifiable format and can be downloaded effortlessly.
- The audit dashboard facilitates one-touch auditor collaboration allowing for easy access evidence. Additionally, it offers a shareable link to communicate the current status of compliance with key stakeholders.
Stay always watchful with continuous compliance monitoring by Sprinto and simplify evidence collection for 100% audit success. Talk to our compliance experts and start your journey today.
FAQs
What are the techniques for gathering compliance evidence?
Techniques for gathering compliance evidence include inspection, observation, employee interviews, examination of records and using tools for automated evidence collection.
What are the 3 main sources of compliance evidence?
The three main sources of compliance evidence are documents and records, risk assessments and testing and validation results.
Are there any specific guidelines or standards for compliance evidence collection?
Yes, there may be different evidence collection requirements as per various standards or regulatory laws. For example, SOC 2 requires historical evidence for demonstrating consistency over a defined period and ISO 27001 requires evidence related to information security management systems (ISMS).


Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.





















