If your business touches even a byte of data from someone in the EU, congratulations, you’re now playing in the big leagues of privacy. The GDPR doesn’t care whether you’re a global enterprise or a two-person startup. The moment EU data enters your world, the rulebooks open; and it’s a long one.
But beneath the legal jargon lies a clear blueprint for building trust. In this blog, we break down GDPR plainly, who it applies to, what it demands, and how companies can stay compliant without losing their minds (or their money to hefty fines).
Treat this as your roadmap to getting GDPR right, whether you’re shipping products, running a SaaS app, tracking analytics, or simply storing customer emails.
- GDPR requires organizations to document what personal data they collect, why they collect it, where it flows, who accesses it, and how long they retain it (via a ROPA).
- Every processing activity must be tied to a valid legal ground such as explicit and purpose-specific consent, contractual or legal obligations, or legitimate interest.
- A clear, accessible privacy notice that accurately reflects your current data practices is mandatory under GDPR.
What is GDPR, and who needs to comply?
GDPR, or the General Data Protection Regulation, is the European Union’s core privacy law that governs how organizations collect, store, process, and protect the personal data of individuals located in the EU.
It applies regardless of where a business is physically based; any company that handles EU personal data must comply with its rules. GDPR ensures transparency, consent-based data use, strong security measures, and strict accountability for data handling.
GDPR applies to:
1. Businesses targeting or serving EU residents
This includes any international organization that offers products or services to people in the EU. SaaS companies catering to EU customers, e-commerce platforms that ship to EU countries, and mobile applications used or downloaded by EU residents all fall under this category. Even if a company provides goods or services for free, the act of targeting EU individuals makes GDPR compliance mandatory.
2. Companies collecting or processing EU personal data
Any organization that collects, stores, or processes the personal information of EU individuals must comply. This also covers businesses that monitor the behaviour of EU users through analytics, tracking, or profiling activities. Marketing and ad-tech companies that track EU visitors, whether through cookies, online campaigns, or behavioural data, are directly subject to GDPR requirements.
3. Data processors handling EU data on behalf of others
Companies acting as data processors must comply even if they do not directly interact with EU users. This includes B2B service providers processing data for clients with EU users, outsourcing firms, cloud service providers, and other third-party vendors. If a business processes EU personal data under the instruction of a data controller, the GDPR also applies to them.
4. Platforms operating in data-sensitive sectors
Industries handling sensitive or high-volume data also fall within the scope of the GDPR. Healthcare and wellness applications that collect health information, as well as marketplaces, fintech platforms, and edtech apps managing various forms of user data, are required to meet GDPR standards due to the nature and sensitivity of the data they handle.
5. organizations of any size
GDPR does not discriminate based on team size or revenue. Even small startups with one or two members must comply if they collect, process, or store personal data of EU residents. The presence of EU data, regardless of scale, is the only factor that determines compliance obligations.
Why is GDPR given so much importance?
GDPR shifts control back to individuals, ensuring that their information isn’t collected, used, or shared without transparency and consent. At its core, GDPR protects a person’s right to know what data is being gathered about them, why it’s being processed, and how securely it’s being handled.
For businesses, GDPR sets a high but necessary benchmark for accountability. It requires organizations to maintain strong security practices, document their data flows, and remain prepared for incidents through clear breach response protocols.
The financial penalties or fines for non-compliance are deliberately steep:
- Level-one fines (Article 83(4)) — up to €10 million or 2% of global annual revenue (whichever is higher): Applied for less severe violations such as failing to maintain an inventory of processing activities, not appointing a Data Protection Officer when required, not cooperating with supervisory authorities, lacking proper data records, or failing to communicate personal data breaches appropriately.
- Level-two fines (Article 83(5)) — up to €20 million or 4% of global annual revenue (whichever is higher): Applied for more serious violations such as ignoring core data processing principles, not obtaining valid customer consent, failing to honour data subject rights, transferring personal data without adequate safeguards, or not responding properly to data breaches.
Even if a business isn’t naturally inclined to take EU privacy seriously, the hefty fines associated with GDPR violations are more than enough to ensure they pay attention.
The 13-step GDPR checklist
GDPR can seem intimidating at first glance, but when broken down into manageable parts, it becomes much easier to navigate. This checklist distills everything your organization needs to put in place, across scope, data practices, legal foundations, security, vendors, and more.
1. Focus on data inventory and documentation
A strong privacy program starts with knowing exactly what you collect, why you collect it, and where it goes. Creating a ROPA (Record of Processing Activities) helps build that clarity.
Every organization should:
- Document each type of data you collect and the purpose behind it.
- Map how data travels across your systems and who can access it.
- Maintain a list of storage locations—databases, SaaS tools, third-party services.
- Define how long each category of data is kept.
- Capture the legal basis for each processing activity.
Review the above documentation regularly and update it as your systems, tools, and processes evolve.
2. Choose the right legal basis and take consent
GDPR expects organizations to process data only when they have a lawful reason. Sometimes, that reason is contract fulfillment; other times, it’s a legal requirement or a legitimate interest. But in many cases, especially marketing, consent is everything. Here’s a table with the six lawful bases:
| Lawful basis | What it means | When it typically applies |
| Consent | The individual has given clear permission for their data to be processed for a specific purpose. | Marketing communications, optional features, or any non-essential processing. |
| Contract | Processing is necessary to enter into or perform a contract with the individual. | Providing a service the user signed up for, fulfilling orders, and managing subscriptions. |
| Legal obligation | Processing is required to meet a legal requirement. | Tax reporting, employment laws, and regulatory compliance duties. |
| Vital interests | Processing is necessary to protect someone’s life or prevent serious harm. | Medical emergencies or urgent situations where consent cannot be obtained. |
| Public task | Processing is necessary to perform a task carried out in the public interest or under official authority. | Government activities, public authorities, tasks mandated by law. |
| Legitimate interests | Processing is necessary for the organization’s legitimate interests, provided they don’t override individuals’ rights and freedoms. | Fraud prevention, internal analytics, and improving services, when interests are balanced and documented. |
When processing personal data, make sure every activity is tied to a valid lawful basis and collect purpose-specific consent whenever it’s required. People should actively choose to opt in, rather than assuming consent or using pre-checked boxes.
Keep the process fair and flexible by making it easy for individuals to withdraw consent at any time. Maintain thorough records of all consent interactions to demonstrate compliance whenever needed.
3. Make your privacy notice visible
A privacy notice is your public-facing explanation of how you treat user data, so it must be honest and easy to understand. This is not the place for vague or overly legalistic language. Instead, outline what data you collect, why you collect it, how long you keep it, and the rights users have over their information.
Make it accessible, whether in your website footer, onboarding flow, or anywhere users first interact with you. As your business evolves, it becomes increasingly vital to revisit this notice. It should reflect your actual data practices, not an outdated version of them.
4. Support all data subject rights
GDPR grants individuals a powerful set of rights, and organizations need to be prepared to honour them. You need to allow users to:
- Request access to their data
- Request corrections or updates to their data
- Request deletion when applicable
- Restrict certain types of processing
- Receive their data in a portable format
- Object to certain processing activities
- Avoid automated decision-making without consent
Establish clear internal procedures, understand where data is stored, and maintain the ability to respond within the expected timeframe (typically 30 days). Treat each request as a structured workflow rather than an ad-hoc exercise.
5. Strengthen access control and security measures
Security is a core expectation under GDPR, requiring organizations to take proportionate, risk-based steps to protect personal data from unauthorised access, loss, or breaches. This means designing controls that match the sensitivity of the data and the threats your environment faces.
Focus on:
- Implementing role-based access control (RBAC): Define roles clearly and grant permissions based on job responsibilities, ensuring that employees only see the data necessary for their specific function.
- Applying the principle of least privilege: Continuously ensure users, systems, and applications hold the minimum access rights needed and nothing more to reduce the attack surface.
- Encrypting data at rest and in transit (TLS/SSL 1.2+): Protect stored data using strong encryption and secure all data transfers to prevent interception or tampering.
- Enabling multi-factor authentication (MFA): Add a second layer of verification for critical accounts to significantly reduce the risk of compromised credentials.
- Maintaining audit logs and continuous monitoring: Track access, changes, and unusual activity, enabling early detection of security incidents and supporting forensic analysis.
- Running vulnerability scans and penetration tests: Regularly assess systems for weaknesses and simulate real-world attacks to validate that security controls work as intended.
6. Conduct DPIAs for high-risk processing
Whenever you engage in activities that could materially impact user privacy, such as handling sensitive data or conducting large-scale monitoring, a DPIA (Data Protection Impact Assessment) helps evaluate the associated risks.
Rather than treating this as a box-ticking exercise, use it as a decision-making tool. Assess what could go wrong, whether users could be harmed, and what safeguards you can implement to reduce that risk. DPIAs should be carried out before high-risk processing begins and revisited when practices change.
7. Manage vendors and third-party processors
Any vendor handling EU personal data on your behalf becomes part of your risk landscape. Start by signing Data Processing Agreements (DPAs) that outline responsibilities and data protection expectations.
Download Data Processing Agreement
Evaluate the vendor’s security posture, understand where the data will be stored, and ensure appropriate safeguards exist for cross-border transfers. Maintain a list of all processors you rely on and review them periodically. Keep in mind that vendor oversight is not a one-time activity, it’s ongoing governance.
8. Define your data retention and deletion practices
Holding on to data “just in case” contradicts GDPR’s principles. Instead, define clear retention periods for each type of data you collect and ensure the timeframe is justifiable. Deletion and archival workflows need to be part of your processes to ensure outdated data doesn’t linger in your systems.
Proper data minimisation reduces both privacy risk and storage cost.
9. Prepare a 72-hour breach response plan
GDPR’s 72-hour reporting rule leaves no room for improvisation. If the event of a breach, you need to know exactly who to inform, what information to provide, and how to communicate the impact.
A good breach response plan outlines how incidents are detected, who is responsible for escalation, what documentation must be kept, and when individuals must be notified. Regular drills help teams practice these workflows before a real incident hits.
10. Train employees on privacy and security
People are often the first and last line of defence in data protection. Training shouldn’t be a one-time lecture. It should be part of your culture. Teach employees how to recognise phishing attempts, handle personal data safely, and understand the basics of GDPR.
Tailor training for roles that handle sensitive or high-risk information. Maintain attendance records and refresh training annually. When employees understand why privacy matters, they’re far more likely to protect it.
11. Appoint a Data Protection Officer (DPO) when required
Not every organization needs a DPO, but if you process sensitive data at scale, monitor users systematically, or operate as a public authority, GDPR requires you to appoint one.
| When a DPO in mandatory: 1. The organization is a public authority or body 2. The organization’s core activities require large-scale, regular, and systematic monitoring of individuals 3. The organization’s core activities involve large-scale processing of special category data or criminal offence data When a DPO is not mandatory, but recommended: 1. The organization handles high-risk data regularly 2. There is complex data sharing or international transfers 3. The business wants demonstrable accountability and oversight |
A DPO should possess the expertise to oversee data protection strategies and have sufficient independence to challenge internal decisions when necessary. They require direct access to leadership and the necessary resources to perform their job effectively. Here are the main responsibilities of a DPO:
- Monitor GDPR compliance across the organization
- Advice on lawful bases, consent, DPIAs, and high-risk processing
- Act as the contact point for supervisory authorities
- Oversee data protection policies, training, and awareness programmes
- Conduct or review privacy impact assessments
- Advice on technical and organizational measures for data protection
- Support incident response and breach notification processes
- Maintain records of processing and ensure ongoing oversight
12. Know what counts as personal data under GDPR
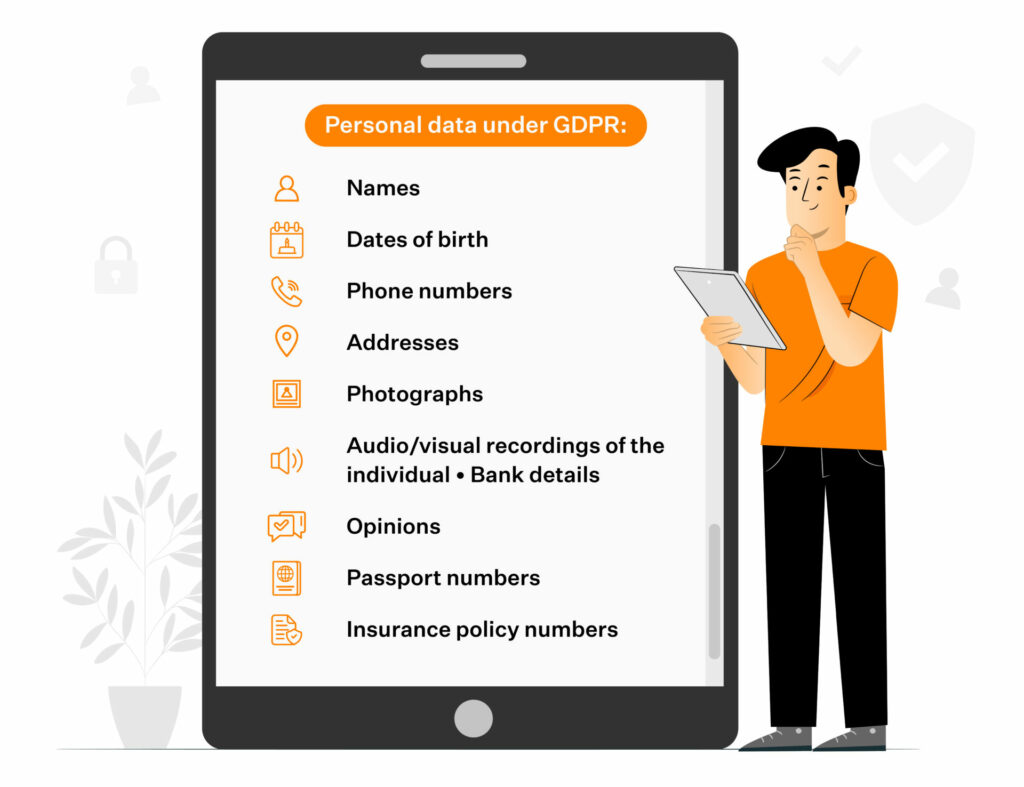
GDPR has a broad definition of personal data, extending far beyond names and email addresses. Device identifiers, location data, behavioural analytics, IP addresses, and even certain types of metadata can all qualify.
If a piece of information can link back to a specific individual, directly or indirectly, it must be treated as personal data. Understanding this is crucial because it determines which safeguards and obligations apply.
13. Maintain GDPR compliance continuously
Treat the GDPR as a living framework rather than a project with a fixed end date. organizations evolve as new tools get added, new data is collected, and new risks emerge.
Regular audits help ensure that documentation remains up to date, privacy notices remain accurate, and controls are aligned with current practices. Keep a record of all compliance activities to demonstrate accountability if regulators request it.
Maintain continuous GDPR compliance with Sprinto
GDPR involves a lot of repetitive work, which is often evidence-heavy, and easy to mess up if handled manually with spreadsheets, emails, and scattered documentation. Leveraging a AI-first compliance automation tool like Sprinto is the easiest way to streamline GDPR and embed true security and privacy within your existing infrastructure.
In practical terms, that means you can:
- Turn this checklist into live workflows: Sprinto AI maps GDPR requirements to controls, owners, and recurring tasks so nothing slips through the cracks.
- Automate evidence collection: Connect Sprinto to systems like AWS, GCP, Azure, GitHub, Okta, Google Workspace, etc., so it automatically pulls logs, configs, and status checks you’d otherwise hunt down manually before every audit.
- Monitor real-time control health: Instead of treating GDPR as an annual project, Sprinto AI continuously tests controls, flags drifts (like a missing MFA, an open port, or a misconfigured policy), and helps you fix them before they become findings—or worse, incidents
- Centralise risk, vendors, and policies: Manage your risk register, vendor due diligence, data processing agreements, and policy acknowledgements from a single platform. Sprinto’s personalized AI bot helps you track updates, surface gaps, and keep everything regulator-ready.
- Stay audit-ready all year: With automated continuous monitoring, status dashboards, and audit-ready reports, you’re not scrambling before reviews. You already have timestamped evidence, mapped controls, and a clear story of how you meet GDPR requirements.
Frequently asked questions
Personal data is any information that can identify an individual, directly or indirectly. This includes names, emails, phone numbers, IP addresses, device IDs, location data, behavioural data, and even certain metadata. If it can be traced back to a person, GDPR treats it as personal data.
GDPR doesn’t mandate a formal third-party audit, but businesses must be able to demonstrate compliance at any time. Many organizations voluntarily undergo audits—internal or external—to validate their controls, especially when working with enterprise customers.
A DPIA is required only when the processing is high-risk, such as large-scale monitoring, handling sensitive data, or using new technologies that affect people’s rights or freedoms. If the risk is significant, a DPIA becomes mandatory.
While GDPR doesn’t specify a fixed document list, core documents commonly required include:
– ROPA (Record of Processing Activities)
– Privacy notice/policy
– Data retention policy
– Data protection impact assessments (when applicable)
– Data processing agreements (DPAs) with all processors
– Incident response and breach notification procedures
– Security controls documentation
Yes, GDPR applies globally. Any US business that offers goods/services to EU residents, collects their data, or monitors their behaviour must comply, even if it has no physical presence in the EU.
Pansy
Pansy is an ISC2 Certified in Cybersecurity content marketer with a background in Computer Science engineering. Lately, she has been exploring the world of marketing through the lens of GRC (Governance, risk & compliance) with Sprinto. When she’s not working, she’s either deeply engrossed in political fiction or honing her culinary skills. You may also find her sunbathing on a beach or hiking through a dense forest.
Explore more
research & insights curated to help you earn a seat at the table.




























