FedRAMP Compliance Of AWS EC2 Instances: Should You Worry?
Pansy
Jan 24, 2025
If you’re using AWS EC2 (Elastic Compute Cloud) for your infrastructure, you might be wondering if you need to do anything to meet the security standards for handling government data. The good news is that your cloud service provider has already taken care of that with FedRAMP (Federal Risk and Authorization Management Program).
FedRAMP sets the bar for cloud security in federal agencies. But how does all this apply to your AWS EC2 instances? Let’s dig in.
| TL;DR AWS EC2 instances are authorized for FedRAMP-Moderate and FedRAMP-High, enabling you to handle federal data securely. While AWS ensures infrastructure-level compliance, you must manage access controls, data encryption, and security configurations for your EC2 instances. Adopt measures like monitoring network traffic, updating guest OS, managing credentials, and encrypting sensitive data to maintain security in your cloud environment. |
What is FedRAMP compliance?
FedRAMP compliance involves adhering to CSPs’ security standards for managing and protecting federal data, including controls for data security, encryption, access management, and continuous monitoring.
FedRAMP compliance is necessary for cloud services to be authorized for use by U.S. government agencies. It ensures that a consistent level of security is maintained across all federal cloud systems.
FedRAMP glossary:
| ATO – Authority to Operate | An official authorization is granted to a cloud service provider, allowing them to operate within federal systems. |
| 3PAO – Third-Party Assessment Organization | An independent organization accredited by FedRAMP to perform security assessments of cloud service providers to ensure compliance with FedRAMP requirements. |
| CSP – Cloud Service Provider | A company that offers cloud-based services such as IaaS, PaaS, or SaaS to customers, including government agencies. |
| JAB – Joint Authorization Board | The primary governance and decision-making body for FedRAMP consists of representatives from major federal agencies. |
| SAR – Security Assessment Report | A document detailing the security posture of a cloud service provider, including findings from security assessments. |
| SSP – System Security Plan | A comprehensive document outlining the security controls for a cloud service as part of the FedRAMP authorization process. |
| FIPS – Federal Information Processing Standards | U.S. government standards for information processing, particularly data encryption and security protocols. |
| P-ATO – Provisional Authority to Operate | A temporary authorization granted by the JAB for a cloud service provider to operate while completing full FedRAMP authorization. |
| CSO – Cloud Service Offering | A CSP provides a specific cloud service and can undergo the FedRAMP authorization process to serve federal agencies. |
Why is FedRAMP critical for AWS EC2 servers?
Regardless of your cloud computing platform, FedRAMP is necessary if you want to work with federal agencies and handle government data.
If you’re using AWS EC2 servers, complying with FedRAMP enables your infrastructure to meet rigorous security and risk management standards. Without FedRAMP, you would not be authorized to host or process sensitive government information.
For AWS and its customers, having FedRAMP-authorized EC2 instances opens up opportunities to serve a broader range of federal clients.
Which FedRAMP security level is supported by AWS EC2?
As per AWS, EC2 instances are supported under two FedRAMP security levels: Moderate or High.
- Moderate: This is the most common level for federal systems, including AWS EC2, covering sensitive but unclassified information where the impact of a breach would be more significant.
- High: Intended for systems with information that, if compromised, could cause severe or catastrophic effects.
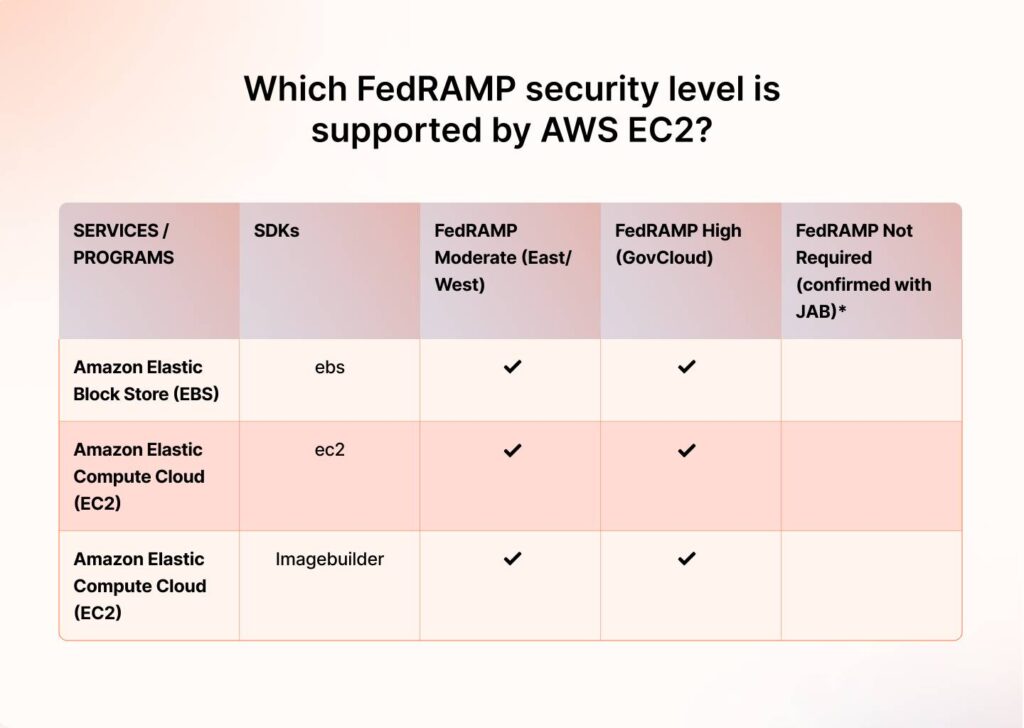
“AWS has AWS GovCloud (US) regions, and GovCloud supports FedRAMP-High compliance, whereas AWS US East-West (Northern Virginia, Ohio, Oregon, Northern California) supports FedRAMP-Moderate.” – Orhun Dalabasmaz, AWS Solutions Architect, Atlassian.
How does FedRAMP compliance with AWS EC2 instances work?
Once you’re in the AWS EC2 architecture, you hardly need to worry about complying with FedRAMP, but since you’re curious about how it works, here’s an overview of the process:
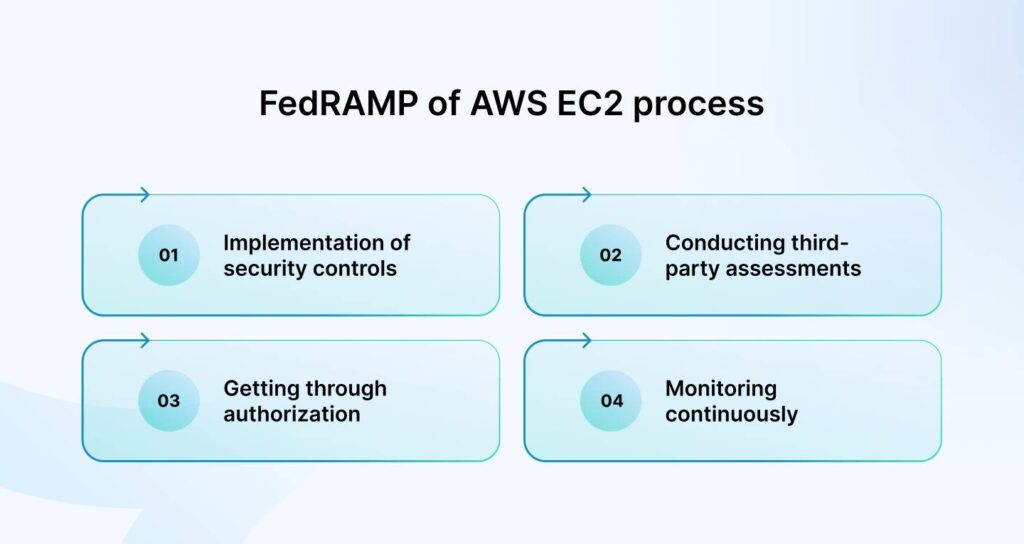
1. Implementation of security controls
AWS implements the security controls FedRAMP requires for different models with respective security levels. These controls cover data encryption, identity and access management (IAM), continuous monitoring, and incident response.
Naturally, AWS EC2 instances, as part of the AWS cloud services, adhere to these controls to ensure they meet federal security requirements.
2. Conducting third-party assessments
Once all controls are in place, AWS engages the 3PAO (Third-Party Assessment Organization). They conduct a detailed assessment of all the controls implemented by AWS. This assessment ensures that the instances are configured and managed following FedRAMP standards.
3. Getting through authorization
The findings from the assessment provided by the 3PAO are reviewed by the JAB (Joint Authorization Board) or an individual federal agency. If the EC2 server meets the necessary security criteria, they are granted either a Provisional Authority to Operate (P-ATO) by the JAB or an Agency Authority to Operate (ATO) by a specific federal agency.
4. Monitoring continuously
All CSPs under FedRAMP undergo continuous monitoring, which includes regular security scans, logging, and periodic reviews to ensure ongoing adherence to FedRAMP standards. Similarly AWS ensures that all their cloud products are monitored as federal requirements require.
If you’re using AWS EC2 for your business, do you need to get FedRAMP authorization separately?
Here’s the good news: You do not need to get FedRAMP authorization separately if you are using AWS EC2 for your business. Since AWS is your cloud service provider, they’re responsible for obtaining FedRAMP authorization for its services, including EC2 instances.
However, your organization is still responsible for implementing and maintaining specific security controls within your environment, such as configuring security settings, access controls, and continuous monitoring.
The continuous monitoring of controls is necessary to comply with FedRAMP requirements. This shared responsibility model means AWS handles the security of your cloud infrastructure while you are responsible for security in the cloud.
What can you do to maintain security in your EC2 cloud?
You have specific responsibilities for maintaining security in your AWS EC2 cloud environment. You cannot entirely rely on AWS to ensure compliance with FedRAMP. Here are some suggestions:
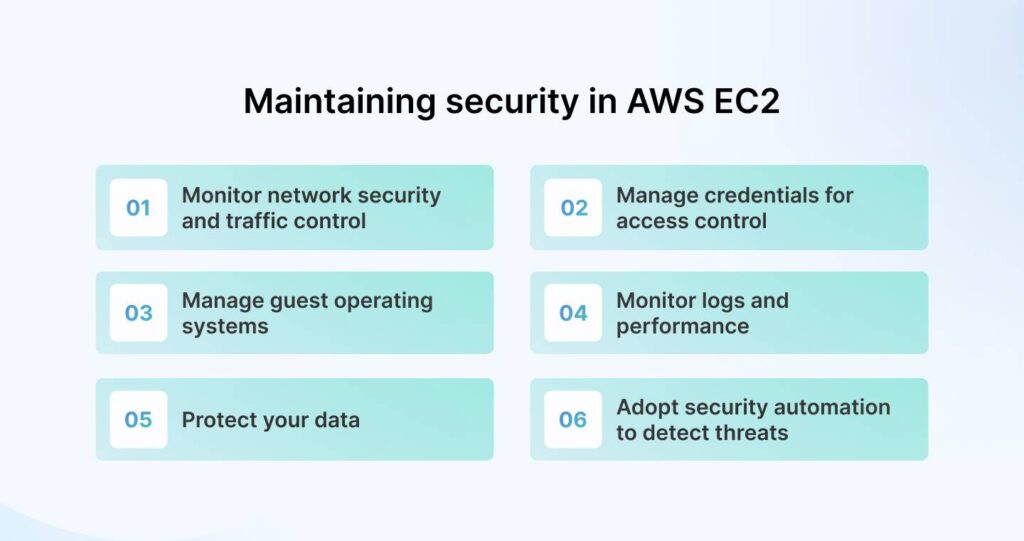
1. Monitor network security and traffic control
Your responsibility includes controlling network access to your EC2 instances by configuring your Virtual Private Cloud (VPC) and Security Groups. Use security groups to control inbound and outbound traffic to and from your EC2 instances. Only allow trusted IP ranges or specific ports required for your application.
Here are ways how you could monitor network exposure:
- VPC subnets: Consider placing sensitive EC2 instances in private subnets to minimize exposure to the public internet.
- Network ACLs: In addition to security groups, configure Network ACLs to control traffic flow at the subnet level further.
- VPC flow logs: Enable VPC Flow Logs to monitor network traffic patterns and identify suspicious activity or misconfigurations.
2. Manage credentials for access control
Use IAM (Identity and Access Management) roles attached to your EC2 instances and make sure they have the least privileges necessary for their operation. Manage and rotate SSH keys for secure access to EC2 instances. Avoid hardcoding or sharing keys in insecure locations.
Enable multi-factor authentication in all your AWS accounts for administrative access, strong protection, and privileged access.
3. Manage guest operating systems
Here are a few ways to manage guest operating systems of your EC2 instances:
- The guest OS should regularly update with the latest security patches to minimize vulnerabilities.
- Configuring and managing security software within the guest OS, like firewalls or intrusion detection systems.
- Use AWS Systems Manager to automate patch management
- Regularly perform vulnerability scans and use AWS Inspector to assess potential weaknesses in your EC2 instance OS.
4. Monitor logs and performance
Enable AWS CloudTrail to log all API activity related to your EC2 instances. Monitor their health and set alarms for any suspicious behavior. You also need to ensure that your instances remain secure. You can do this by using AWS Config to track changes.
5. Protect your data
All sensitive data processed or stored by your EC2 instances must be encrypted. This includes:
- Encrypting data at rest using Amazon EBS encryption for block storage
- Encrypting data in transit with SSL/TLS for protection of communications between instances and other services or users
- Using AWS Key Management Service (KMS) to effectively manage and protect encryption keys securely
6. Adopt security automation to detect threats
You must continuously monitor your EC2 instances for suspicious activity, such as unusual network traffic or unauthorized access attempts. You can use WS Macie to automatically classify and protect sensitive data, such as PII (Personally Identifiable Information), stored or processed by your EC2 instances.
Tip:
Products like AWS Security Hub and Sprinto can aggregate findings from any AWS security service. They can give you a comprehensive view of your security posture and help you manage incidents.
Security automation also includes scanning for security vulnerabilities and misconfigurations. This includes checking for outdated packages or missing security patches and conducting regular penetration testing and security audits.
So, should EC2 worry about FedRAMP?
The straight answer is: Not really. You don’t need to lose sleep over FedRAMP, but staying proactive about your security is always a good move.
Furthermore, FedRAMP compliance for AWS EC2 isn’t just a regulatory hurdle; it’s a strategic advantage. AWS, as your cloud service provider, takes care of the intricate, high-level compliance work, letting you focus on what actually matters: innovating and scaling your business.
You’re not only securing your operations but also positioning your business as a reliable partner in the federal space. Data is power, and FedRAMP compliance ensures you’re wielding it responsibly and effectively.
Frequently asked questions
1. How does Amazon CloudWatch support FedRAMP compliance?
Amazon CloudWatch enhances security monitoring by logging audits and tracking malicious activity in your AWS environment. These logs are vital for meeting FedRAMP requirements, emphasizing continuous monitoring of services like Amazon EC2, Amazon RDS, and Amazon Virtual Private Cloud (VPC).
2. How does AWS Identity and Access Management (IAM) help achieve FedRAMP standards?
AWS IAM is critical for managing access to resources in compliance with FedRAMP. It enforces the principle of least privilege by controlling root access, defining granular permissions, and utilizing Access Analyzer to identify unintended access or unauthorized users.
3. What steps ensure FedRAMP-compliant storage with Amazon S3?
To meet FedRAMP standards, Amazon S3 requires data encryption at rest and in transit. Implement S3 bucket policies and server access logging to manage and track access while restricting public access and enforcing multi-layer security controls.
4. How does Amazon Inspector assist with FedRAMP compliance?
Amazon Inspector conducts automated security assessments of services like Amazon Elastic Block Store (EBS) and EC2 instances. Detecting vulnerabilities and misconfigurations ensures compliance with FedRAMP’s stringent security requirements.
5. How does Amazon Virtual Private Cloud (VPC) align with FedRAMP’s network security standards?
Amazon VPC enables FedRAMP-compliant networking by securing direct internet access, monitoring network access, and logging traffic through access log records. Features like private subnets and network ACLs help reduce the risk of malicious activity.


Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.





















