When Cyber Threats Outrun the Playbook: The Limits of NIST CSF
Heer Chheda
Jan 31, 2025
A compliance framework isn’t a shield.
It’s more like a recipe. Follow it closely, and you’ll get something that looks pretty good on paper. But just because you’ve got the ingredients for a strong security posture doesn’t mean the kitchen isn’t on fire.
NIST CSF lays out the essentials—it tells you how to organize your defenses, where to put the locks, and how to check if they’re working. But cybersecurity frameworks like these aren’t fortune tellers. They’re built on past breaches, not future ones. And while that hindsight is helpful, it’s also the reason cybersecurity frameworks tend to lag behind the cybersecurity threats they’re supposed to guard against.
TL;DR
| NIST CSF is invaluable for establishing cybersecurity hygiene, including patching, access control, and asset management. It simplifies complex security practices and bridges communication gaps across industries. |
| Compliance doesn’t equal security. Cybersecurity frameworks reflect past threats, but attackers innovate constantly. British businesses lost $55 billion over five years—not from a lack of frameworks but from failing to evolve with emerging cybersecurity risks. |
| To stay ahead, you should treat NIST CSF as a foundation and enhance it with Zero Trust, real-time threat intelligence, automation, and regular red teaming to keep defenses sharp and adaptive. |
You don’t build today’s defenses on yesterday’s threats
That’s the risk of over-relying on NIST CSF. Attackers don’t wait for the next version update. They’re busy poking at the gaps in today’s defenses. The cybersecurity framework can steer you in the right direction, but if you’re not adapting beyond what’s written down, you’re playing a game of catch-up with opponents who aren’t playing by the same rules.
Frameworks age. Cyber threats don’t.
Cyber threats are evolving – It’s axiomatic to say this
A report by VPNRanks predicts that in 2025, there will be approximately 1.31 million complaints of AI-powered cyberattacks, potentially leading to losses of $18.6 billion. Then there are zero-day vulnerabilities—the ones no one sees coming.
By the time cybersecurity frameworks like NIST CSF acknowledge them, the damage has often already been done. Add to that the growing wave of supply chain attacks, where the weak link isn’t your system but a vendor’s, and it starts to feel like chasing shadows.
We are not devaluing the idea of frameworks—far from it. NIST CSF, ISO 27001, CIS, and others like them are invaluable—without them, cybersecurity would be a disorganized mess of trial and error. The problem isn’t the framework itself. It’s how we treat it.
Just because you’re compliant doesn’t mean you’re secure.
NIST CSF is still relevant; here’s why
NIST CSF is the simple truth that good cybersecurity starts with good hygiene. Patching vulnerabilities, tightening security controls, and keeping tabs on critical assets aren’t flashy, but they often stand between you and your next breach.
For businesses starting to formalize their security practices, NIST CSF is a godsend. It lays out the essentials in clear, manageable steps, making it easier to spot weak points and reinforce them before attackers do. Without this baseline, even the most sophisticated defenses crumble.
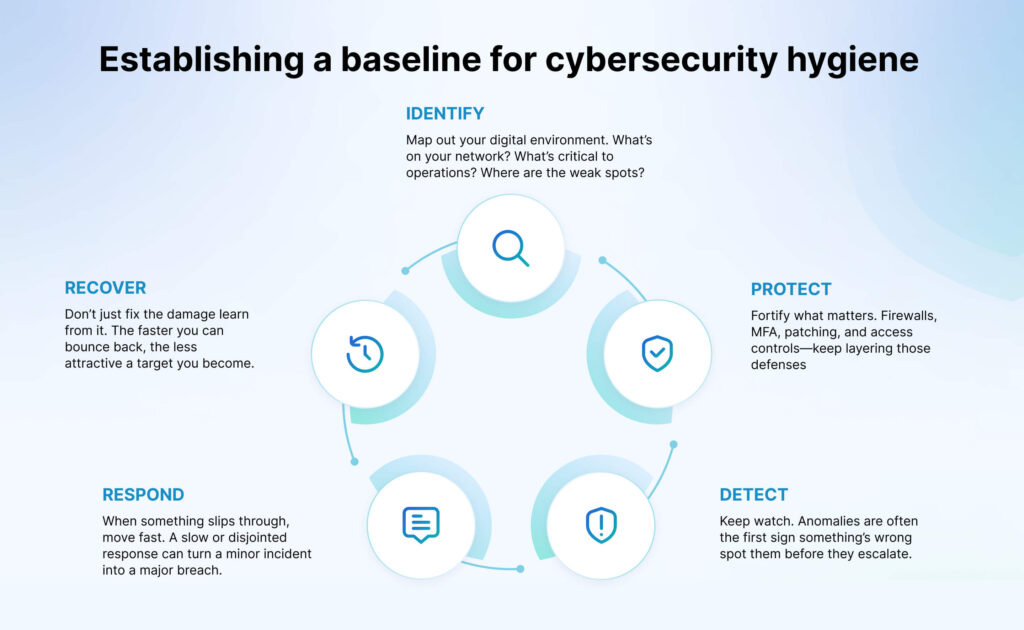
Establishing a baseline for cybersecurity hygiene
We all know cybersecurity incidents or security breaches don’t stem from sophisticated, nation-state attackers exploiting never-before-seen vulnerabilities. They happen because someone forgot to patch an old server or because a reused password opened the door.
NIST CSF was designed to help organizations avoid exactly that. It creates structure around the core security functions that, when consistently applied, can stop the majority of threats in their tracks:
Providing common language
Security, IT, and cybersecurity are complex sectors that contain a lot of jargon. One of the most underrated contributions of NIST CSF is its ability to bridge communication gaps—not just between departments but across entire industries.
NIST CSF translates technical cybersecurity concepts into business language that leadership can digest. This helps justify investments, prioritize cybersecurity risks, and get buy-in for new initiatives.
It also serves as a foundation for many other regulatory frameworks, including GDPR, HIPAA, and ISO 27001. By aligning with NIST, companies often cover the basics for multiple standards simultaneously, reducing redundancy.
Formalized security practices
Not every company starts with a mature security program. Many small to mid-sized businesses are just beginning to move away from ad-hoc defenses to something more structured. NIST CSF acts as a north star for these organizations, offering clear, manageable steps without overwhelming them.
NIST CSF’s adaptability lies in its risk-based, outcomes-driven approach. Rather than prescribing specific tools or technologies, the framework focuses on guiding principles and flexible categories like Identify, Protect, Detect, Respond, and Recover.
Depending on the organization’s size, resources, and threat landscape, these core functions can be scaled up or down. For a small business with limited cybersecurity staff, the framework might emphasize essential asset management and access controls. A large enterprise, on the other hand, might layer in advanced threat detection, continuous monitoring, and incident response simulations.
The double-edged sword of compliance
The fact that NIST allows for adaptability is also its Achilles heel. Without regular adjustments, the framework’s effectiveness frays at the edges.
Take, for example, a mid-sized company that implements NIST CSF by focusing on basic access controls, asset inventories, and endpoint protections. At the time, this setup might seem like enough. But as the company scales—adding new cloud services, remote employees, and third-party vendors—the original framework starts to lag behind the reality of its risk environment.
At first, everything seems secure—audits are clean, controls are in place, and confidence is high. However, as the company scales, relying on cloud services and third parties, those initial safeguards no longer keep pace with evolving risks.
Complacency trap
It’s easy to assume compliance equals security, but attackers aren’t following the same playbook. AI-driven phishing campaigns, for example, have surged by over 1,265% in the past year alone.
What about zero-day exploits? In 2023, 53% of widely exploited vulnerabilities were zero-day, meaning organizations were hit before frameworks even recognized the threat. How many systems are running on the assumption that their current defenses will hold up until the next NIST update?
The cost of complacency
Consider this—British businesses lost $55 billion to cyberattacks over the past five years. Was it because they lacked frameworks or because those frameworks were left static while threats evolved?
The uncomfortable truth is that complacency isn’t just an internal problem. It becomes a vulnerability that adversaries exploit. And often, organizations don’t realize it until the breach is already underway.
Neglected gaps
Frameworks, by design, reflect what’s already known—they distill lessons from past breaches, codifying best practices to guard against familiar threats. However, this reactive nature creates an unavoidable lag in a field as dynamic as cybersecurity.
AI-powered malware can rewrite its code mid-attack to avoid detection, while advanced phishing campaigns leverage machine learning to bypass the very filters organizations installed to stay compliant. These threats operate in a grey area, falling outside the scope of static frameworks until they become so prevalent that exclusion is no longer an option.
Delayed response to Zero-day
Zero-day vulnerabilities epitomize this gap. By their nature, zero-days are vulnerabilities that no one—not even the software vendor—is aware of until they’re exploited. Attackers capitalize on this window of exposure, often for months before a patch is developed and disseminated.
Frameworks like NIST CSF can only recommend general best practices—such as rigorous patching schedules or system segmentation—to mitigate risk, but they can’t anticipate or defend against unknown vulnerabilities in real-time.
This creates a dangerous paradox. Companies that rely too heavily on frameworks assume that compliance equates to comprehensive security. Yet, when zero-day exploits emerge, even those who strictly adhere to NIST CSF can find themselves vulnerable, waiting for guidance that comes after the fact.
So, how do you stay agile?
The idea is not to abandon NIST or any other frameworks for that matter. While these frameworks form the foundation, you will have to build the walls and the windows.
| Component | Purpose | Ties to NIST CSF | Actionable Step |
| Zero Trust Architecture (ZTA) | Limit lateral movement, enforce least privilege | Protect, Detect | – Enforce MFA and continuous identity checks- Segment networks (micro-segmentation)- Apply strict access policies based on roles |
| Threat Intelligence Integration | Adapt defenses to emerging threats | Identify, Detect, Respond | – Subscribe to threat feeds (ISACs, OSINT)- Automate ingestion of threat intel- Develop adaptive IR playbooks |
| Automation (AI + SOAR) | Accelerate response, reduce manual effort | Protect, Detect, Respond, Recover | – Automate asset discovery and patching- Deploy AI-driven anomaly detection- Use SOAR for automated incident response |
| Red Teaming/Simulations | Identify hidden vulnerabilities | Detect, Respond, Recover | – Conduct biannual red team exercises- Simulate phishing and social engineering attacks- Test supply chain resilience |
| Continuous Risk Assessment | Adjust posture as business environments evolve | Identify, Protect, Detect | – Perform quarterly reviews- Monitor third-party risks dynamically |
| Micro-Segmentation | Contain breaches within isolated zones | Protect, Detect | – Segment sensitive workloads- Apply the least privilege to segmented areas |
In the end, this needs to be etched in everyone’s mind.
FAQs
What is the difference between ISO 27001 and NIST CSF?
ISO 27001 and NIST CSF are both frameworks for managing cybersecurity, but they differ in scope and focus:
- ISO 27001: A globally recognized standard for establishing, implementing, maintaining, and continuously improving an Information Security Management System (ISMS). It provides a comprehensive set of controls and requires organizations to undergo audits for certification.
- NIST CSF: A voluntary framework focused on improving cybersecurity resilience. It’s tailored for organizations in the U.S. but widely used globally. Unlike ISO 27001, it doesn’t have a certification process but offers a flexible structure for identifying, protecting, detecting, responding to, and recovering from cybersecurity risks.
What is the difference between NIST 800-53 and CSF?
NIST 800-53 and NIST CSF are both developed by the National Institute of Standards and Technology (NIST), but they serve different purposes:
- NIST 800-53: A detailed catalog of security and privacy controls designed for U.S. federal information systems and organizations. It provides specific, prescriptive controls for compliance with federal regulations like FISMA.
- NIST CSF: A high-level, voluntary framework intended to guide organizations in improving their cybersecurity posture. It’s more flexible and focuses on outcomes rather than specific controls.
What are the objectives of NIST CSF?
The NIST Cybersecurity Framework (CSF) enhances resilience by helping organizations protect critical infrastructure and manage cybersecurity risks. Flexible and adaptable for all industries, it fosters cross-industry communication, emphasizes continuous improvement, and promotes a proactive approach to identifying, protecting, detecting, responding to, and recovering from threats.


Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.





















