When Crisis Strikes, Be Ready: Creating a Business Continuity Policy That Works
Heer Chheda
Jan 02, 2025
In March 2024, AT&T experienced a massive data breach affecting 73 million customers. This incident has prompted companies across various sectors to reassess their continuity and disaster recovery strategies, underscoring the critical importance of having a robust business continuity plan in today’s digital landscape.
The breach that exposed users’ sensitive information, including SSNs, passcodes, and names, highlights the far-reaching consequences of data security failures. It must be understood that your measures are as strong as your weakest vulnerabilities (yes, we get the tautology). The idea here is to build resilience.
A well-crafted business continuity policy should outline procedures for preventing, detecting, and responding to data breaches, as well as strategies for maintaining critical business functions in the aftermath of such incidents.
“Everyone and anyone can be breached, but not all of them will have the mechanism to bounce back. And that separates you from the rest. To continue, with minimum disruption and downtime.”
Rajiv, our lead ISO auditor at Sprinto
Great advice adds up. Get more from the brightest minds in GRC — join now
TL;DR
| A Business Continuity Policy (BCP) is your organization’s resilience blueprint. It outlines strategies to maintain critical operations during disruptions, from cyber attacks to natural disasters |
| Effective BCPs are built on thorough risk assessment and business impact analysis. They prioritize critical functions, set recovery objectives, and allocate resources strategically. |
| Crafted effectively, a BCP can provide an edge over competitors. It reduces financial losses during disruptions, cultivates stakeholder confidence, and guarantees regulatory compliance. |
What is a business continuity policy?
A business continuity policy is a documented set of procedures and guidelines to ensure an organization can maintain or quickly resume critical business functions during and after a disruptive event. A business continuity plan often outlines the strategies, resources, and processes necessary to protect an organization’s assets, reputation, and ability to operate in the face of various threats.
While each business continuity policy will differ from one another, there are common components:
- Risk assessment and business impact analysis
- Critical function identification and prioritization
- Recovery time objectives and recovery point objectives
- Incident response plans
- Communication protocols
- Data backup and recovery strategies
- Alternative site operation plans
- Supply chain resilience measures
- Regular patch testing and software updates
- Roles and responsibilities of identified personnel
A business continuity policy should ideally address various potential disasters, including natural disasters, cyber-attacks, infrastructure failures, pandemics, and other unforeseen events. These often integrate with organizational policies like disaster recovery plans, crisis management, and information security.
Why does your business need a business continuity policy?
A business continuity policy is essential as it ensures revenue restoration with minimum downtime. Here are several other reasons as to why your business should have a business continuity policy:
- Risk mitigation: A business continuity policy provides a structured approach to identifying, assessing, and mitigating potential threats and vulnerabilities. It enables you to reduce the impact of disruptions when they occur, and potentially save you millions of dollars in losses.
- Regulatory compliance: Many industries are subject to mandatory regulations requiring a business continuity plan in place. For example, financial institutions need to comply with regulations like the Base III framework, which includes operational resilience as one of its requirements.
- Confidence among stakeholders: A well documented and tested policy instills confidence in stakeholders, including investors, business partners, and customers. It demonstrates that your organization is committed to resilience and can be a differentiator in competitive markets.
Let’s say planning is not your strongest skill and you decide to wing it… In that case, here’s the cost you’d have to pay:
- Without clear procedures, your organization can crumble under operational chaos. You could lose your business to a disaster that could have been easily mitigated.
- If your downtime is prolonged, you could lose substantial revenue, increasing recovery costs and potential legal liabilities. The Ponemon Institute reports that a large enterprise’s average downtime cost is around $9,000 per minute.
- Failure to contain and isolate disruptions, attacks, or even threats can result in irreparable harm to your organization’s reputation. This harm extends beyond the incident, affecting long-term customer trust and market position.
It isn’t a very rosy picture, is it? Well, it’s not meant to be. Think about it: your systems are down, your data is compromised, and your operations have stopped. Essentially, you are watching revenue slip away by the minute.
To mitigate this nightmare, here’s how to create your business continuity policy.
Is your business ready for the unexpected? Our Business Continuity Plan Template helps you design a solid framework for handling any disruption, from natural disasters to cyber incidents.
Download Your Business Continuity Plan Template
Creating a business continuity policy? Here’s how to get it right:
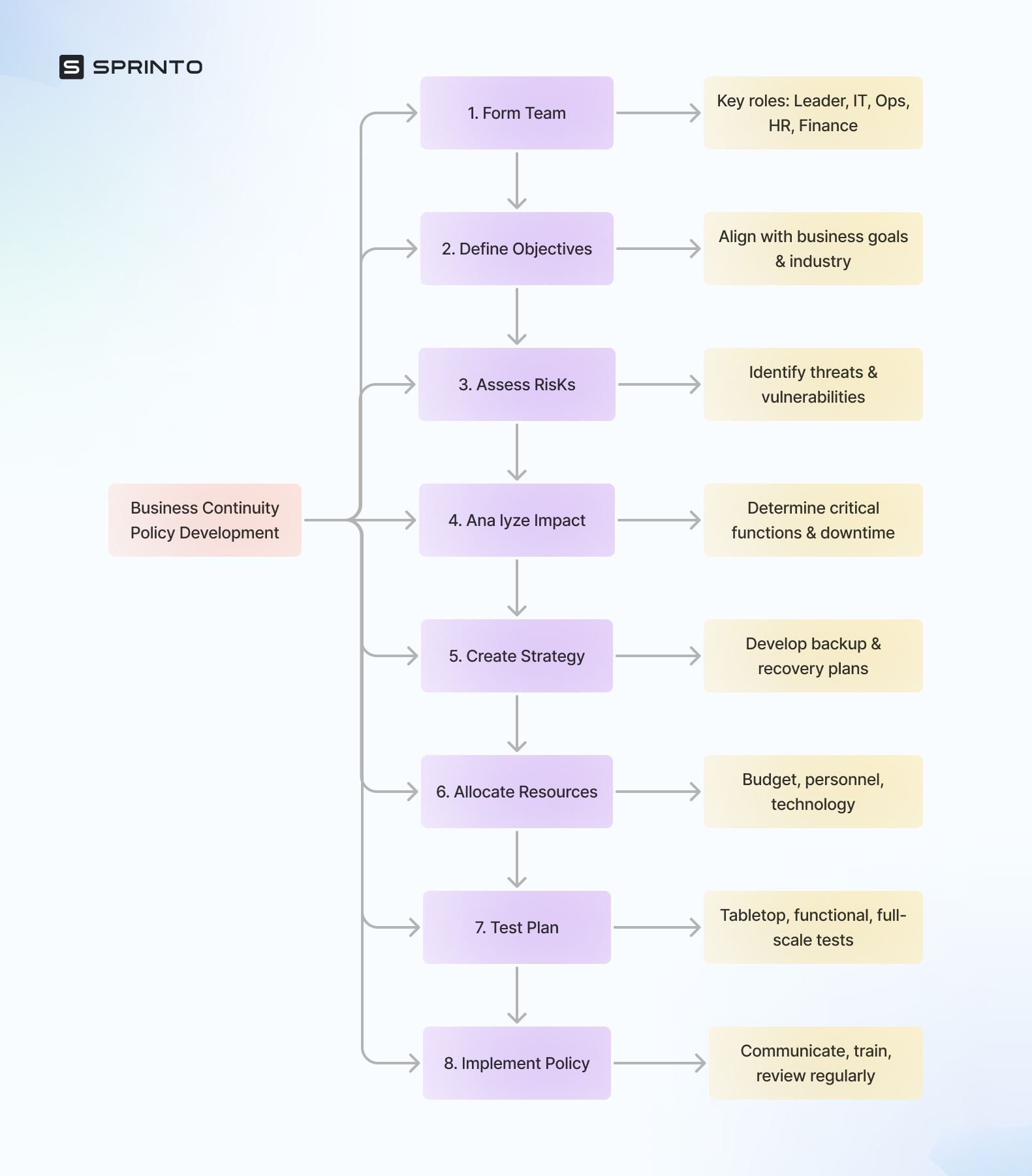
A good business policy hinges on the following:
- Comprehensiveness: Plan for everything but prepare for the worst.
- Realistic: Test out your plans and ensure they are grounded in reality.
- Efficient: How efficient are your controls? Do you need to revisit them?
- Adaptable: Prepare to change and adapt to circumstances.
“A strong business continuity policy is not a static document but a constantly evolving policy that anticipates and mitigates unforeseen challenges. It is the cornerstone of organizational resilience, transforming potential crises into opportunities for growth and innovation”
According to Rajiv, our lead ISO auditor at Sprinto
93% of companies without a disaster recovery plan that suffer a major data disaster are out of business within one year. To beat these odds, create a business continuity policy by following these eight steps.
Step 1: Form a team
It all starts with creating a dream team. This group is responsible for developing, maintaining, and implementing your business continuity strategy. Ideally, this team should consist of:
- A senior leader who can provide top-level support and resources.
- A POC responsible for coordinating the efforts.
- An IT rep to address the tech and data needs.
- An Ops manager to ensure that critical business functions are accounted for.
- An HR rep to handle employee related issues and communications.
- A finance rep to assess the financial impact and allocate resources.
- Unit heads or department leads to provide specific insight, if any.
If you fall short of these designated members, here’s what you can do instead:
- Assign key roles and responsibilities to existing staff members, allowing them to wear multiple hats.
- Prioritize having at least three core members: a leader (CEO, CTO), an operations manager, and an IT manager. If you don’t have an IT manager, you can get external consultation.
- If you lack other resources, you can focus on the most critical aspects of your business and then expand your plan as your resources allow.
- Leverage cloud-based tools and templates to streamline the process.
The idea is not to create the biggest team but the most efficient one. Start from what you have and build from there.
Step 2: Write down your objectives and reasoning
Your team should clearly define your aim with this policy and your reasoning for the same. Your objectives might vary based on your industry, business model, and risk appetite. Here’s how you can approach this:
- What are the objectives of this BCP that align with my overarching business goals?
- Minimize downtime of critical systems
- Protect sensitive data
- Maintain customer service levels
- Ensure employee safety
- Preserve supply chain operations
- Safeguard company reputation
- Tailor it to your industry: For instance, if you are a financial institution, you might want to focus on data integrity or transaction continuity. If you are a healthcare organization, you might want to prioritize patient care, ensure HIPAA compliance, etc.
- Quantify your goals: Set specific recovery times like:
- RTO for critical functions
- RPO for data backups
- Target uptime percentages for key systems.
- Align with your business strategy: Consider the impact of your objectives on customer retention and acquisition and factor in other overall goals.
- Document reasoning: Explain the rationale behind each decision and try to link your objectives to specific business risks or past incidents.
Rank objectives based on the criticality to business operations and consider interdependencies between objectives. This clarity will guide decision-making throughout the planning process and help justify resource allocation to stakeholders.
Step 3: Conduct risk assessment
Conduct a thorough risk assessment to ensure you prioritize risks and allocate resources effectively. A risk assessment involves identifying potential threats and vulnerabilities and evaluating their likelihood and potential impact.
Key aspects of conducting a risk assessment include:
- Threat identification
- Natural disasters – Earthquakes, floods
- Technological failures – System crashes, data breaches
- Human-caused events – Cyber attacks, sabotage
- Public health crisis – Pandemics
- Economic disruption – Market crashes. Supply chain failures.
- Vulnerability analysis: Assess any weak points in your current systems and processes and evaluate any dependencies on external factors.
- Impact assessment: Quantify potential loss from each threat and vulnerability, assess for reputational damage and factor in any legal and regulatory consequences.
- Estimate probability: Use historical data and industry trends to estimate the likelihood of risks materializing.
- Prioritize risks: Based on all the factors mentioned above, prioritize risks with the highest score that combines impact and probability. Focus on high-impact, high-probability risks first.
- Control evaluation: Assess your current risk mitigation strategies and identify gaps in your current controls.
Regularly assess risks and update your risk assessments based on new threats and vulnerabilities.
Move fast without breaking your stride with Sprinto
Risk assessment is a long-drawn procedure that is prone to errors if done manually. It is always advisable to automate this process. Modern Governance, Risk and Compliance platforms can offer powerful solutions that can automate and enhance the efficacy of these critical tasks.
Spinto is one such GRC tool that helps you manage risks with ease. Sprinto’s integrated risk management system provides tools that identify, assess, and mitigate risks efficiently.
Sprinto visualizes risks, giving you a birds-eye view of your threat landscape. It allows you to quickly prioritize areas that require your immediate attention. You can also deep-dive into each risk profile and view the associated controls, current treatment plans, real-time updates, and even track progress.
Sprinto continuously scans for new threats and vulnerabilities, providing you with up-to-date risk assessments. It also aligns with your compliance measures to ensure that your efforts work in concert.
Foresee, mitigate, remediate with Sprinto
Step 4: Analyze the business impact of these risks
The goal of a business impact analysis is to pinpoint specific impacts that these risks may have on your company’s operations. While business impact analysis (BIA) concentrates on “what would be the impact if it did happen,” risk assessments offer the “what could happen” scenario.
You begin by identifying critical components of your business and prioritizing these functions based on their importance. Establish the maximum downtime for each function and prioritize recovery based on the risk assessment. Define the maximum acceptable data loss for each system and backup your data accordingly.
Risks can significantly impact financial performance. Estimate for them and consider the direct and indirect costs associated with disruption. Determine the resources needed to maintain critical operations, from technology and personnel to facilities.
Analyze the operational impact and, based on this analysis, develop business continuity strategies that can help you weather the downtime.
Step 5: Create a recovery strategy
Develop a business continuity recovery plan to help you respond and recover from disruptions. When you are creating a recovery strategy, here are a few things to consider:
- Backup system: Implement redundant and geographically dispersed data backup solutions. Utilize cloud-based backup services for added resilience. Ensure that you regularly back up your data and test protocols.
- Remote working capacities: Ensure your VPN infrastructure can support the entire workforce. Provide hardware and software solutions to make remote possible and implement secure communication channels.
- Supply chain resilience: Diversify your supplier to reduce single points of failure and maintain buffer inventory for critical components.
- Crisis communication plan: Develop multi-channel communications for stakeholders and prepare pre-approved message templates for various scenarios.
- IT infrastructure: Implement failover systems for important applications and use load-balancing systems to enhance resilience.
- Employee training: Ensure that multiple employees can maintain key functions and document critical processes for easy handover.
For example, make sure you have a cloud-based backup and failover mechanism in case one of your IT systems fails. Continue to replicate data in real time to CSP, and in the event of a primary system failure, promptly switch to the cloud-based backup to minimize data loss and disruption.
Isolate backup and system restoration in case of a cyberattack. Keep air-gapped backups of your most important information and systems. Isolate the compromised systems in case of a ransomware attack. Establish procedures so that, for critical systems, data must be erased and restored from clean backups in “x” hours and, for noncritical systems, “y” hours.
Every strategy that you create should have the following:
- Clear activation controls
- Defined roles and responsibilities
- Step-by-step procedures
- Required resources and their location
- Communication protocols
- Testing and maintenance schedules
Step 6: Allocate resources based on the strategy
Allocate resources to implement the recovery strategy effectively. This step ensures that your plan is practically executable. Here’s how you can approach resource allocation:
- Establish a dedicated budget for business continuity. Allocate funds for:
- Tech investments like integrated and Infosec risk management software and data backups
- Training programs for employees
- External consultants or services
- Emergency funds for immediate crisis response
- Identify key personnel for each recovery strategy and consider creating a dedicated team.
- Invest in necessary hardware like generators or backup servers and acquire software licenses for important applications. Implement cybersecurity tools and other monitoring systems.
- Secure alternate work locations and arrange for backup power sources.
- If needed, engage with third-party recovery services and establish agreements with key suppliers for priority service.
- Schedule regular training sessions and drills and allocate time for periodic review and updating of the security and incident response plan.
While allocating resources, consider doing a cost-benefit analysis to ensure that your efforts are worth the time and money spent.
Step 7: Test the plan
To truly understand the efficacy of your plan, test the strategies you have created. This step validates your efforts and helps you familiarize yourself with the emergency procedures.
First of all, decide on the kind of test you want to do. There are three kinds of tests:
- Tabletop exercise: This is the most basic form of testing that involves key personnel in a discussion-based format. These exercises simulate various scenarios, allowing you to walk through response procedures verbally. They are an excellent way to address low-risk situations and test decision-making skills.
- Functional exercise: A functional exercise is a hands-on test that involves activities like recovering IT systems, activating emergency response protocols, or relocating to an alternate location. While these are more complex than tabletop exercises, functional drills allow you to understand the efficacy of your recovery strategies and recommendations and identify areas that need improvement in a controlled environment.
- Full-scale simulations: A full-scale simulation is the most comprehensive and realistic form of testing. This exercise involves all relevant staff and external stakeholders, simulating a real disaster scenario as accurately as possible. Your team is expected to execute the entire BCP, from response to full recovery. This test is most valuable for risk simulations, as you cannot afford to make mistakes in case of risks with critical impact on the business.
Once you assign a testing method to some or all of your risks, develop a regular testing calendar and ensure that all critical components are tested at least annually. Conduct additional tests if the business environment or infrastructure changes.
Once the stakeholders know their responsibilities, establish clear expectations and metrics for success. Measure against your defined RTOs and RPOs. Record all test outcomes and activities. Document any deviations from the plan and whether or not it worked.
Analyze your test results against the base metrics and identify any gaps or weaknesses. Account for any unrealistic expectations or assumptions in the plan. Test your tech tools to ensure they don’t break during an actual disaster.
Some possible weaknesses in your BCP that could be highlighted during the simulation are:
- Outdated information
- Inadequate risk assessment
- Unrealistic expectations
- Insufficient testing
- Over-reliance on either tech or human resources
- Inadequate resource allocation
- Poor communication protocols
- Neglecting the overarching business goals
- Insufficient scope
- Incomplete documentation
- Data recovery issues
- Compliance gaps
These risks could differ depending on your industry, but it is important to remember that the idea is not to “pass” the test but to look for areas of improvement. Encourage a culture where finding and addressing weaknesses is positively viewed.
Step 8: Roll out the policy
After addressing weaknesses identified during testing and making changes, it’s time to officially roll out the Business Continuity Policy. This step ensures that your organization is aligned and prepared to execute the plan when needed.
Here are a few things to keep in mind when rolling out the policy:
- Secure visible support from the top management
- Ensure that the documentation is clear, accurate, and, most of all, accessible.
- Communicate the policy and explain its purpose to everyone involved in the language they understand.
- For example, for investors, focus on ROI and business revenue, while for employees emphasize productivity.
- Consider a phased rollout, starting with critical departments.
- Update relevant business documents to reflect new continuity measures.
- Incentive adoption, if you can.
Rolling out the BCP is the beginning of an ongoing process. The goal is to embed business continuity thinking into your organization’s culture, ensuring preparedness becomes a natural part of your daily operations. The key is to review and update your policy regularly.
The rollout focuses on implementation and adoption; the policy’s content will guide your organization through potential crises. That brings us to an equally important question….
What should a business continuity policy include?
A well-crafted business continuity policy goes beyond addressing the procedure; it gives you a framework of resilience to be followed by the entire organization. Let’s look at what needs to be included so it can serve as a reference guide for your organization:
Introduction
The introduction to a business continuity policy should make clear how crucial the document is to the company. It establishes the tone for the entire document and gives some context on the importance of business continuity planning.
Policy statement
This section needs to be detailed and should answer the following questions:
- Why does this policy exist? Policies typically exist to:
- What is the scope of this policy? Essentially, which departments does it cover?
- Risk assessments
- What are the key objectives of this document?
Disaster definition
It’s critical to define a disaster for your organization. Your definition should be customized to your company’s specific needs, taking into account things like the length of the disruption, financial thresholds, and operational impact. It should also specify exactly when the business continuity strategy will go into effect.
Policy overseer
The policy must identify a Policy Overseer, typically a senior executive or dedicated business continuity manager. This person or group is in charge of upholding, amending, and enforcing the policy. They should clearly understand their roles and responsibilities, including the power to make decisions in emergencies.
Compliance
The compliance section of a business continuity policy is essential for ensuring that the organization’s continuity initiatives comply with all applicable laws, rules, and industry standards. This section, which addresses both internal governance and external obligations, should be thorough and precise.
Strategy
The strategy section of a business continuity policy is essential because it describes how the company will handle different types of unexpected disruptions or calamities. The policy should include a summary of these tactics and their significance, even though more in-depth plans should be kept in separate documents.
Confidentiality
The confidentiality section of a business continuity policy plays a critical role in safeguarding confidential data while guaranteeing that the appropriate parties can obtain the information they need in an emergency. Clear procedures for managing and sharing information about the business continuity plan should be established in this area.
Moving forward….
The digital transformation accelerated by recent global events blurs the lines between physical and cyber resilience. Future continuity plans must holistically address this interconnected landscape. Simultaneously, evolving regulatory environments will demand a more comprehensive approach to organizational resilience.
You can only hope to build a resilient company if you view business continuity as a part of your culture rather than a static activity.
FAQs
1. What is the main goal of BCP?
The primary objective of business continuity planning, or BCP, is keeping an organization’s vital processes running both during and after a disruptive incident. Its goals are to keep vital operations running smoothly, preserve assets, and reduce downtime to protect the company’s reputation, financial stability, and ability to serve its customers.
2. What is the difference between business continuity policy and business continuity plan?
A business continuity policy is a high-level document that establishes general goals, delineates roles and duties, prescribes risk mitigating controls, and demonstrates an organization’s commitment to business continuity. It offers a structure for ongoing initiatives.
A business continuity plan is an elaborate, implementable document that outlines the actions, protocols, and materials required to continue or resume essential operations during an interruption. It is the application of the policy’s guiding ideas in real life.
Essentially, the plan describes the “how” of business continuity, while the policy gives the “why” and “what.”
3. What are the key elements of business continuity policy?
The five elements of the business continuity policy are:
- Objectives
- Scope
- Roles and Responsibilities
- Risk Assessment
- Recovery Strategies


Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.





















