Cybersecurity Framework: All You Need To Know
Meeba Gracy
Sep 27, 2024
Hackers are becoming increasingly creative. They now use sophisticated wares to access and steal sensitive information. Cloud intrusions have increased by 75% while 72% organisations have faced ransomware attacks highlighting the urgent need for cybersecurity defenses. The financial impact of cybercrime is expected to reach $10.5 trillion in 2025!
These cybersecurity trends show that regardless of whether it’s cybercriminals, hacktivist groups, or even nation-state actors, attackers are constantly evolving their tactics. This makes cyber threat mitigation more important than ever. To protect your data, you need a strong cybersecurity framework that can effectively defend against these growing threats.In this blog post, we’ll explore cybersecurity frameworks and how they help in keeping your data safe.
What is a Cybersecurity Framework?
Cybersecurity frameworks are an essential set of documents that help reduce the risk of cyber attacks. These guidelines, standards and best practices ensure that any vulnerabilities or weaknesses present can be managed proactively in order to protect against malicious hackers and other criminals who may attempt to exploit them.
It has three parts, namely:
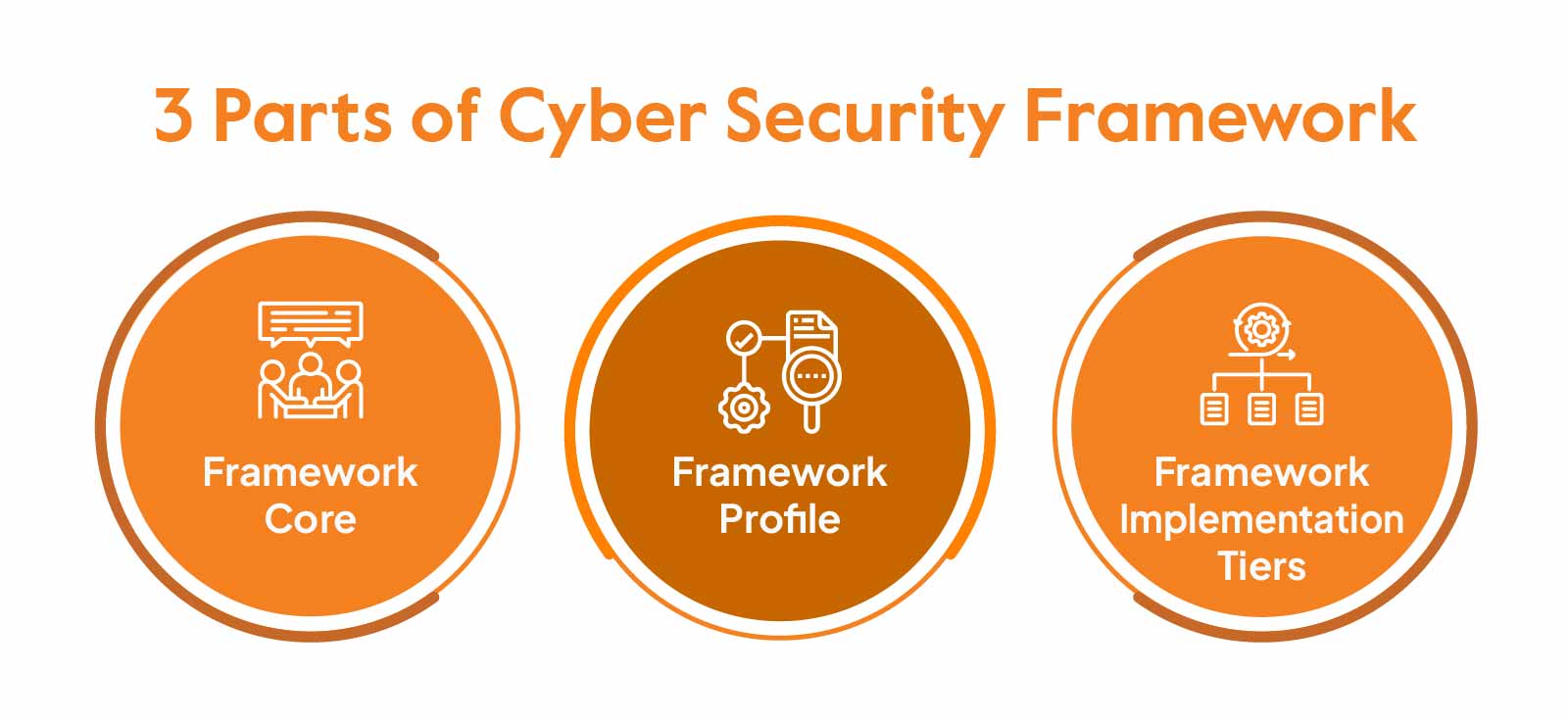
Let’s go into this in detail.
Cyber security frameworks may seem like daunting, complex jargon; however, they are actually quite straightforward. These guidelines help organizations reduce their risk of cyber-attack exposure and keep their data secure.
Visualize it as a resilient structure that reinforces the stability of your building or bridge. It stands strong and unyielding, serving as an ideal base for your business to combat any faults or vulnerabilities cyber attackers may try to exploit in order to penetrate into your system.
In simpler words, this is an assemblage of best practices engineered towards safeguarding the digital infrastructure within your organization from potential threats.
Why Do Organizations Require a Cybersecurity Framework?
Cybersecurity frameworks provide organizations with detailed documents outlining guidelines, standards and best practices for managing cyber security risk.
When you use these frameworks to address vulnerabilities that hackers may exploit, you can reduce your exposure to malicious activities and protect yourselves against digital threats.
Cybersecurity frameworks provide organizations with an invaluable advantage— they can accurately assess their current security stance and pinpoint any potential weaknesses. This allows you to make informed decisions on where to allocate resources for enhancing safety.
The cybersecurity frameworks typically follow five main processes defining the security approach. These processes are Identity, Protect, Detect, Respond, and Recover.
- The Identity process helps identify and understand the assets that need to be protected, while the
- Protect process identifies the controls needed to secure the assets
- The Detect process focuses on identifying any threats, and the
- Response process outlines the steps to be taken in the event of a security incident
- Recover process aims to recover the systems and data after an attack or a breach
So, if you haven’t already, it’s time to start implementing cybersecurity frameworks to avoid risks and stay secure.
Also, check out a detailed guide to cyber security compliance.
How to choose the right cybersecurity framework for your business?
You simply cannot choose a cybersecurity framework that’s popular or because your competition is also using it. The choice depends on several factors and it’s important to select a framework that not only aligns with your organization’s risk appetite and maturity but also evolves as the business grows.
Take these factors into account when choosing the cybersecurity framework:
Nature of business
Depending on the type of information you deal with and the nature of your business, there might be some industry-specific regulations that you must adhere to or some country-wise regulations applicable. For example, the PCI DSS framework is relevant for payment processing, while businesses in California must adhere to CCPA.
Framework scope and coverage
Different frameworks are ideal for different businesses based on context. For example, NIST CSF is ideal for businesses looking to improve their resilience by taking a risk-based and flexible approach. The ISO 27001 framework is best for organizations seeking to build a robust ISMS while SOC 2 is preferred by SaaS companies handling customer data.
Current security maturity
The choice also depends on your current security maturity. A small business lacking advanced measures might look for best practices and general guidance. An enterprise with some level of security maturity might look for a framework that helps enhance current practices.
Scalability and Flexibility
Choose a framework that aligns with your organization’s shifting priorities. For example, if you plan to eventually expand globally, a framework like ISO 27001, which is globally recognized, can be a good choice.
Availability of resources
Implementing a cybersecurity framework requires you to commit some resources for compliance tools, consultants, technological enhancements and process changes. Choose a framework that aligns with the availability of your resources and doesn’t burden the organization.
List of Cybersecurity Frameworks
Now, you might be interested in picking out a perfect cybersecurity framework that will suit your company. Again, your choice should ultimately depend solely on your organization’s needs. Here are some cyber security frameworks examples you should keep an eye on to comply with standards:
NIST
The NIST framework, designed to protect America’s critical infrastructure from cyberattacks, was the answer to an Executive Order issued by the Obama Administration. A tool for private sector companies to detect, respond to, and recover from cyber threats, it features five key functions:
- Identify
- Protect
- Detect
- Respond
- Recover
These functions are carefully crafted guidelines that allow your company to take preventive cyberattack measures. This framework also indicates how you should conduct yourself during a cyber incident. This voluntary framework is a step forward in bettering your cybersecurity defenses.
But one of the common questions many companies have is, “why should I comply with the NIST framework out of all the cyber security framework list?”
The main reason is that because of the amount of testing that goes into the publication they release. It involves months, weeks, and sometimes years of testing under the radar for a long time. A team of prominent professionals in the field will do the research. Hence the publications are accurate both technically and informationally.
ISO 27001
The ISO/IEC 27001 is a globally recognized standard for establishing, maintaining, and continuously improving an Information Security Management System (ISMS).
The standard requires organizations to undergo certification audits to demonstrate compliance. The latest version of the standard is ISO 27001:2022 which replaces the previous ISO 27001:2013 version while reducing the number of controls from 114 to 93 across 4 categories — Organizational controls, people controls, physical controls and technical controls.
ISO 27002
ISO/IEC 27002 provides implementation guidance for the controls outlined in ISO 27001. While it is not a certifiable standard, it is used alongside ISO 27001 to ensure comprehensive information security.
The standard enhances control categorization, supports effective selection, and offers best practices for establishing a robust ISMS.
The Center for Internet Security Critical Security Controls (CIS)
CIS is the perfect level to start from if your company wants to increase cybersecurity step by step. Developed in the late 2000s, it provides 20 carefully-selected controls updated regularly by professionals from various industries like academia, government, and industry.
These controls span fundamental, foundational, and organizational levels mapped to common standards like HIPAA and NIST. Even those organizations not subject to particular protocols can benefit from its configurations that ensure their cyber security is up to scratch.
The Health Insurance and Portability and Accountability Act (HIPAA)
HIPAA is vital to the healthcare industry, serving as a defense against potential data breaches. This critical cyber security framework safeguards patient records and other confidential information, ensuring that all personal data remains secure.
Compliance with HIPAA ensures that all healthcare operators will provide their patients with the necessary privacy protocols to keep them relaxed and confident in their healthcare choice. Without it, individuals’ delicate healthcare data could be exposed quickly and without notice, leading to severe consequences for companies and consumers alike.
SOC 2
Systems and Organizations Control 2 (SOC 2) is a voluntary compliance framework commonly used by SaaS providers, cloud companies and other businesses handling sensitive customer data to ensure the security, availability, processing integrity, confidentiality, and privacy–known as the five trust principles.
These 5 Trust Service Criteria (TSC) have been developed by American Institute of Certified Public Accountants (AICPA). The organizations undergoing SOC 2 are required to produce documentation and evidence to demonstrate the effectiveness of controls as per the chosen criteria.
A SOC 2 report is issued after a third-party validation of required controls and it helps businesses build trust among clients and partners.
PCI DSS
PCI DSS (Payment Card Industry Data Security Standard) is an information security standard that requires any organization that collects, stores or processes sensitive cardholder data to protect it against fraud and breaches. It has been developed by PCI DSS Council comprising major credit card brands.
The standard requires merchants of all sizes, payment processors and service providers to meet 12 major requirements such as building and maintaining strong networks, implementing access controls and running VAPT (Vulnerability Assessment and Penetration Testing) scans to minimize risks to payment information.
CMMC 2.0
CMMC 2.0 is a framework developed by the US Department of Defense (DoD) to enhance the cybersecurity posture of federal contractors that handle Controlled Unclassified Information (CUI). The framework is an iteration of CMMC 1.0 and aims to simplify requirements while ensuring stronger cybersecurity across the DoD supply chain.
The key changes from CMMC 1.0 to CMMC 2.0 include switching from 5 to 3 maturity levels, self-assessment for certain organizations, and better alignment with NIST SP 800-171.
The General Data Protection Regulation (GDPR)
GDPR — the General Data Protection Regulation — is widely seen as one of the most stringent and secure programs for data privacy worldwide. It was developed by the European Union to better protect the data held by EU citizens, from SMEs to large organizations.
Its reach extends across borders, too; even companies based elsewhere but still offer services or products in Europe must abide by its rules when handling sensitive data in online transfers. This shows just how seriously they take protecting their citizens’ digital privacy – something we can all learn from.
Control Objectives for Information and Related Technologies (COBIT)
The COBIT cybersecurity framework was created by the ISACA (Information Systems Audit and Control Association) to introduce a comprehensive IT governance and management system.
When implementing COBIT, organizations can take the necessary steps to protect data from all potential vulnerabilities, allowing them complete end-to-end coverage. It was an ambitious move, as the world has become increasingly reliant on technology, and large companies carry hefty amounts of sensitive data stored in cloud computing systems and social media accounts.
Although it may not seem evident initially, COBIT can provide a way for your organization to defend your information through proactive measures to enhance enterprise security.
Best Practices for implementing a cybersecurity framework
Once you’ve chosen a framework, follow these best practices to ensure smooth and effective implementation:
Align security with overall business objectives
A cybersecurity framework should enable cybersecurity integration with other business processes and not be implemented in isolation. Implement security by design principles and align security measures with people-ops and vendor management to support long-term business objectives.
Secure leadership buy-in
Leadership buy-in is essential to set the tone at the top. When executives recognize cybersecurity as a business enabler, they begin supporting necessary investments and reviewing the organization’s cybersecurity posture, performance, and threats. It also encourages security conversations among stakeholders and reinforces that this is not just a one-time initiative but a strategic priority.
Establish continuous monitoring
Implementing a framework is not a one-and-done task and neither does it guarantee security or compliance. As threats evolve every day, it is crucial to establish a continuous monitoring mechanism and track if the framework has been working effectively. Measure KPIs such as incident response time, audit success rate or MFA enablement to understand if there are any gaps and make improvements.
Promote a security conscious culture
Cybersecurity is a shared responsibility, and it is crucial to build a security-first culture that integrates it naturally into operations. Train your staff on cybersecurity practices, communicate the importance of frameworks, and use rewards or risk-adjusted profits to reinforce the right attitude.
Automate when possible
Agility is paramount in cybersecurity. Manual methods are error-prone and time-consuming, so you must automate whatever is possible. Compliance automation tools such as Sprinto can do most of the heavy lifting so you can concentrate on mission-critical tasks while ensuring continuous compliance and security.
A Smarter Path to Compliance
As 2025 rolls on, the importance of secure cyberspace has never been higher. Companies are now willing to invest in top-of-the-line cyber security frameworks to protect their data and customer information from malicious intrusions.
We’ve explored various aspects of cyber security frameworks in this blog post and laid out some key points that can help shape your understanding of them. Looking at all entities, be it government organizations or private enterprises; they are all taking steps to enhance their infrastructure and reduce their attack surface area.
For easier ways to handle compliance requirements, contact Sprinto—our automated platform that will do the work for you! With a few clicks, you can quickly deploy better cyber security practices and ensure you don’t leave your systems vulnerable to potential cyber threats. Speak to our experts today.
FAQs
Which cyber security framework is the best?
When it comes to cybersecurity, few frameworks compare to the widely-recognized ISO/IEC 27001 and 27002. Affectionately dubbed ‘ISO 270K’, this framework is an international benchmark for safeguarding information security both internally and externally with third parties.
Is ISO 27001 a cyber security framework?
Absolutely! This international Standard is the gold standard for information security management systems. By following its principles of confidentiality, integrity, and availability you can effectively safeguard your data from potential threats.
What are the 6 Ds of cyber security?
The 6 D’s of cyber security to bolster your digital defense strategy — Deter, Detect, Defend, Deflect, Document and Delay. With these measures in place you can ensure top tier protection from malicious forces on the web.


Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.

























