A Cautionary Tale: Lessons from the Star Health Insurance Data Breach
Heer Chheda
Jan 31, 2025
In August 2024, a cyberattack on Star Health Insurance made headlines by becoming the victim of a staggering data breach. Over 31 million customers—roughly the population of Malaysia—saw their personal data exposed. Names, addresses, tax records, medical histories—information meant to remain private was suddenly at the mercy of threat actors.
This incident isn’t an anomaly. In fact, it’s part of a troubling trend. Cybercriminals are increasingly zeroing in on healthcare and insurance companies. Why? Because these organizations hold some of the most sensitive, high-value data, they often lack the ironclad defenses to protect it.
According to a report by IBM, the healthcare industry has ranked as the most costly sector for data breaches for 13 consecutive years, with the average breach cost reaching $10.93 million in 2023.
TL;DR
| The Star Health breach exposed the sensitive data of over 31 million customers due to vulnerabilities like IDOR, credential misuse, and insider risks. |
| Organizations must prioritize verification, continuous risk monitoring, secure API practices, and fostering a security-driven culture involving leadership and employees. |
| For Indian businesses, adopting global security frameworks, empowering CISOs, and leveraging local threat intelligence are critical steps forward. |
A brief overview of what happened
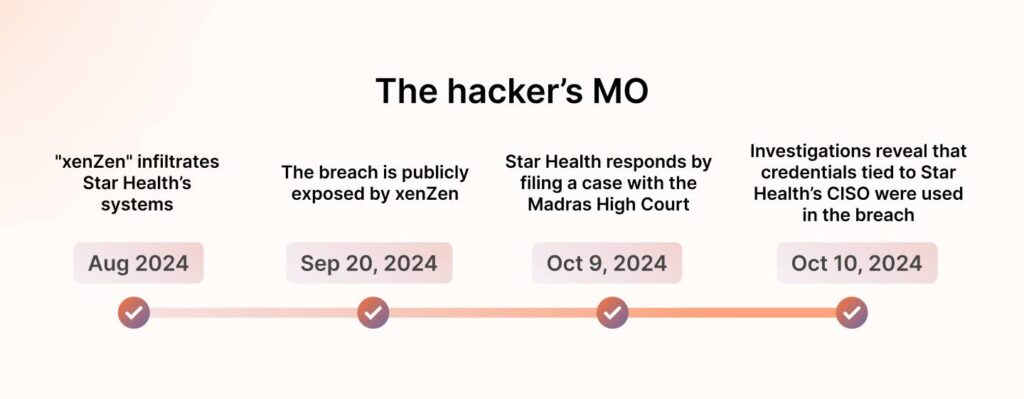
A hacker using the moniker “xenZen” claimed to have infiltrated their systems, exfiltrating 7.24 terabytes of sensitive data. Here’s where things get interesting, for the lack of a better word. The breach only gained visibility on September 20, not through Star Health’s disclosure but via the hacker’s tactics.
The hacker’s MO
What made this breach stand out wasn’t just the scale or the data stolen—it was the hacker’s approach. XenZen didn’t just take what wasn’t theirs; they turned it into a weapon. Using Telegram chatbots, they created a disturbingly simple interface that allowed anyone to retrieve sensitive personal details.
To cap it off, the hacker attached a ransom demand of $68,000—a figure so trivial it underscored the disregard for the scale of the devastation inflicted.
The impact of the breach on Star Health
The breach sent Star Health’s shares tumbling by 11% after the news broke. But the financial hit was just the beginning. Trust—a currency far harder to regain—was severely compromised. And then there’s the fallout you can’t quantify: potential business deals that won’t materialize, opportunities quietly slipping away as customers and partners think twice about aligning with an organization in the midst of such a crisis.
This begs the question: What went unchecked?
The Star Health breach didn’t just expose data—it laid bare glaring vulnerabilities that went unchecked for far too long. Each one tells a story of missed opportunities to tighten the reins and build better defenses.
Impersonation and credential misuse
One of the most shocking revelations came from how the hacker operated: impersonating the company’s CISO. Using the CISO’s official email credentials, the attacker spun a web of deceit that dragged the security chief into the spotlight. But as cybersecurity experts pointed out, the narrative doesn’t add up. The credentials tied to the breach were traced to a leak from 2022—an incident involving infostealer malware.
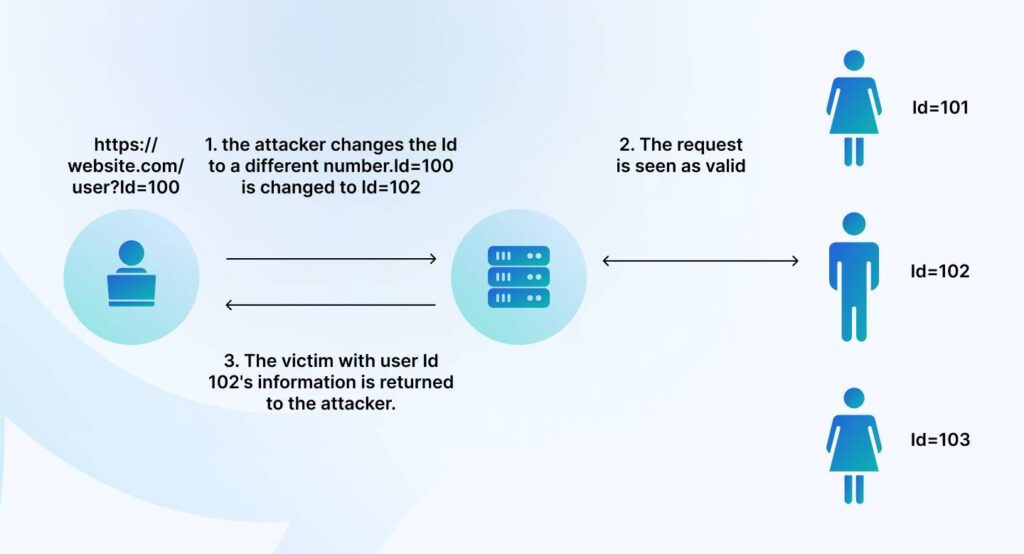
Exploitation of IDOR
At the heart of the breach was a weakness in Star Health’s API—a vulnerability known as an Insecure Direct Object Reference (IDOR). Once inside, the hacker exploited this flaw to access sensitive data, bypassing layers of security. IDOR issues aren’t new, but their continued presence in systems shows how much can slip through the cracks when APIs aren’t rigorously tested.
Insider risk issues
The hacker’s claims of insider involvement, though unsubstantiated, still highlight a major concern: how companies manage privileged accounts. Whether it was a case of compromised credentials or an insider exploiting access, the breach underscores the need for constant monitoring of who has access to what—and how that access is being used.
Delayed response
Perhaps the most damning aspect was how long it took for the breach to be detected. By the time Star Health knew what had happened, the damage was already spiraling out of control. The hacker had set up Telegram chatbots and a website to distribute data, leaving the company to chase the fallout rather than prevent it.
The Star Health breach is a stark reminder that compliance alone doesn’t equal security.
What should you take away from this?
Passing an audit or hanging a compliance certificate on the wall won’t stop hackers. True security is about building resilience, adapting to threats, and constantly re-evaluating your defenses. It’s about embedding a mindset of verification, vigilance, and proactive measures into every layer of your organization.
Verification over assumption
For too long, businesses have treated compliance as a guarantee of safety. The truth is that compliance frameworks offer guidance, not protection. A SOC 2 certification, for instance, ensures you have controls in place at one point in time. But what happens when those controls fall out of sync with evolving cyber threats?
Reinventing password hygiene
Let’s address the elephant in the room: passwords are still a major weak link. The Star Health breach traced its roots back to leaked credentials from a 2022 malware attack. That’s three years of those credentials floating around the dark web, waiting to be exploited.
Businesses need to overhaul how they manage passwords:
- Employees shouldn’t be juggling a hundred variations of “Password123.” Password managers generate and store complex, unique passwords for every account. Tools like LastPass, Dashlane, or Bitwarden can reduce human error and ensure that no two passwords are identical.
- MFA adds a critical second layer of protection. Even if a password is compromised, the attacker still needs access to a physical device or biometric data to breach the account.
- Make it a policy that no password is ever recycled, and implement checks to ensure old credentials tied to breaches (like those in 2022) are immediately retired.
Continuous risk monitoring
Cyber threats don’t operate on your timeline. They’re relentless, evolving, and opportunistic. If you’re relying on periodic security assessments, you’re always playing catch-up.
Here’s what continuous risk monitoring looks like in practice:
- Real-time threat intelligence: Invest in tools that gather and analyze data about emerging threats.
- Behavioral analytics: Look for anomalies in user activity. If an employee suddenly downloads gigabytes of data at midnight or logs in from an unrecognized device, your system should flag it immediately.
- Endpoint Detection and Response (EDR): Traditional antivirus software won’t cut it. EDR solutions provide real-time monitoring and automated responses to suspicious activities on endpoints like laptops and servers.
“Most of the times, security is about discipline and processes around crucial activities that you do continuously. These include common things such as how you onboard or offboard employees or how you just push code to production.”
Girish Redekar, Co-Founder at Sprinto
Great advice adds up. Get more from the brightest minds in GRC — join now
If this makes you interested in continuous monitoring and wanting to safeguard your organization’s data, you should check out Sprinto. Here’s how we can help you:
- Sprinto continuously scans your systems for vulnerabilities, ensuring you catch potential threats before they escalate into breaches.
- Get notified instantly when something unusual occurs, so you can respond swiftly and minimize damage.
- Our platform automates compliance while actively monitoring your security posture, so you don’t have to choose between meeting standards and staying secure—they go hand in hand.
And with Sprinto, your security evolves as your business does, ensuring you stay protected even as new threats emerge.
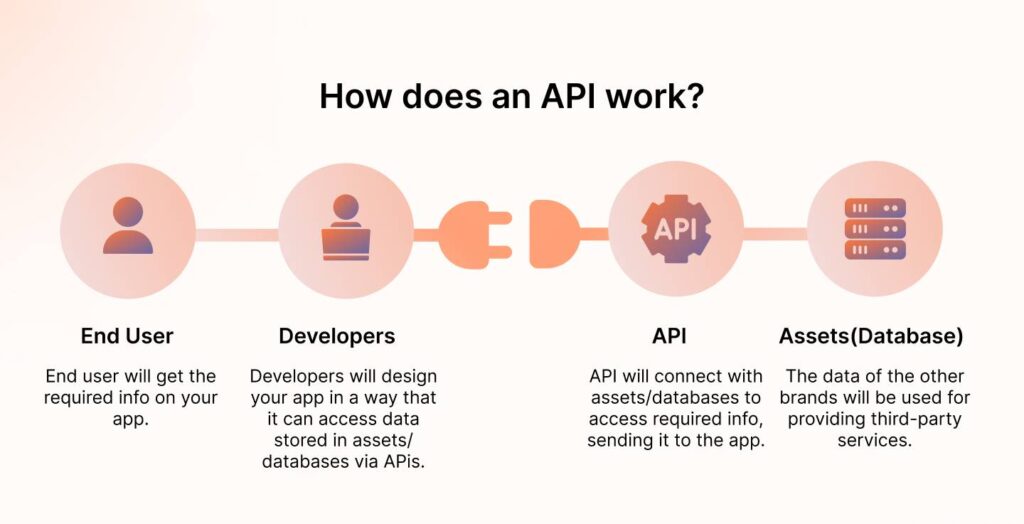
Securing APIs
APIs are everywhere. They power integrations, connect systems, and share data—but they’re also an open invitation for attackers if left unsecured. The Star Health breach exploited an API vulnerability (IDOR) to access sensitive data.
- Ensure every API is protected with strong authentication and rate limiting. Don’t let attackers brute-force their way into your systems.
- APIs evolve over time, and the risk of new vulnerabilities comes with each change. Regularly audit and test your APIs to identify weaknesses like IDOR or broken object-level authorization.
- Implement Zero Trust Network principles. Never assume trust between systems. Authenticate and validate every request, even if it originates from within your network.
Managing insider risks with precision
At the risk of sounding dramatic, there’s a saying in Hindi that loosely translates to “It’s your own people who wound you the most.” Even if the actions aren’t deliberate, humans cause 90% of the data breaches.
And you mitigate that by:
- Role-Based Access Controls (RBAC): Limit access to sensitive data based on job roles. An employee in marketing doesn’t need access to financial databases, and even IT staff should have segmented permissions.
- Privileged account monitoring: Track and log the activities of privileged accounts. If an admin account suddenly starts accessing unrelated systems, investigate immediately.
And, most importantly, culture—a word that often gets diluted into lifeless PowerPoint slides, check-the-box security checks, or occasional talks and webinars. But culture isn’t something you can mandate through a presentation or a quarterly training session. True security culture is built over time through actions that resonate, behaviors that inspire, and values consistently upheld.
It starts at the top, with leadership that leads by example, weaving security into the organization’s DNA. It’s reinforced by creating an environment where employees feel accountable but not afraid—where they’re empowered to report a phishing attempt without fear of reprimanding. Culture is set when security becomes part of daily workflows, not an afterthought. It’s built through continuous engagement, real conversations about risks and responsibilities, and gamified initiatives that make participation enjoyable, not tedious.
Most of all, it’s about trust—ensuring everyone understands their role in protecting the organization without feeling overwhelmed by jargon or policy-heavy lectures.
Building on top of the basics
The Star Health breach wasn’t just a failure of technology—it was a failure of mindset. Too often, organizations focus on being compliant rather than being secure. Compliance looks good on paper, but it doesn’t stop attacks. What truly makes a difference is adopting a security-first mindset, a shift that requires organizations to move beyond checkboxes and audits and look at the hard truths of their vulnerabilities.
Security by design
But security needs to be built into the DNA of your organization. Every decision—whether it’s about infrastructure, APIs, or third-party integrations—needs to be made with security in mind.
This means:
- Designing systems where sensitive data is segmented, encrypted, and protected with multiple layers.
- Regularly scrutinizing even “trusted” internal processes to identify blind spots. For example, had Star Health conducted routine API security reviews, they might have caught the IDOR vulnerability before it was exploited.
Security by design isn’t about making things airtight (because no system ever is); it’s about ensuring that, even if someone breaks in, they don’t have free rein. Good security architecture introduces layers of friction, making the attacker’s job exponentially harder.
Introducing good friction
For years, businesses have been obsessed with minimizing friction—for customers, employees, and vendors. But in security, a little friction is a good thing. When processes are too smooth, systems become more straightforward to exploit.
Take internal access controls as an example:
- Bad Friction is forcing employees to go through unnecessary steps for routine tasks, which leads to workarounds and non-compliance.
- Good Friction requires approvals, monitoring high-risk actions, and ensuring sensitive actions (like API modifications) trigger alerts or multi-layered authentication.
Rethinking prevention
The Star Health breach is proof that prevention isn’t always possible. A sophisticated attacker will eventually find a way in. The real question is: how easy did you make it for them?
If your systems are designed to hand over sensitive data the moment someone gets through one layer of defense, the problem isn’t just the breach—it’s your architecture. The attacker’s journey from initial access to data exfiltration should be long, painful, and full of traps. For example:
- Why was the hacker able to access sensitive customer data without triggering immediate red flags?
- Why weren’t outdated credentials retired or flagged in their systems?
- Why wasn’t API traffic monitored for unusual patterns, like the volume of data being accessed?
You can’t stop every breach, but you can make sure it doesn’t blow up into a catastrophe.
Accountability and not complacency
The biggest change organizations need isn’t technical—it’s psychological. Too many businesses treat security as a PR exercise, a badge they can flash during sales pitches. ISO-certified? SOC 2-compliant? Great. But are you actually secure?
Being secure means asking tough questions:
- Have we tested our systems for failure? Not just a penetration test but a full-blown failure simulation—what happens when a credential is compromised, or an API is misused?
- Do employees understand their role in security? Culture isn’t built-in PowerPoints. It’s built by showing employees why security matters, not just to the company but to them personally. If a phishing simulation feels like a “test” rather than a learning moment, you’re doing it wrong.
- Are we addressing systemic vulnerabilities, not just symptoms? Fixing one vulnerability after a breach is like patching a hole in a sinking ship. You need to look at the root causes, whether it’s a lack of monitoring, poor password hygiene, or insufficient training.
For those in India, here are a few additional tips:
India is still catching up in terms of cybersecurity awareness and readiness. Breaches like Star Health highlight systemic gaps that Indian businesses must address to build stronger defenses. Here’s what needs to change:
CERT-In’s guidelines
CERT-In’s guidelines are the floor, not the ceiling. Reporting breaches within six hours is fine, but what about detecting the breach in the first place? Businesses need to:
- Conduct frequent audits of their systems and processes.
- Go beyond regulatory compliance to adopt globally recognized frameworks like NIST CSF or CIS Controls.
Local threat intelligence
India-specific threats, like the misuse of Aadhar or targeted phishing scams, require localized intelligence. You need to invest in tools and teams that understand these nuances rather than relying solely on global solutions
And here’s to the board: give CISOs the authority they deserve.
In India, CISOs often lack the authority and resources to enforce meaningful change. Companies need to treat CISOs as strategic partners, not just compliance officers. This means:
- Giving them a seat at the table in board meetings.
- Allocating sufficient budgets for proactive security measures.
- Holding them accountable for long-term security, not just reactive fixes.
The way forward…
The way forward demands more than tools or frameworks—it requires a shift in mindset. Organizations need to embed security into their culture, adopt proactive measures like continuous monitoring, and rethink how they empower leaders like CISOs. It’s about asking hard questions, introducing good friction, and designing systems that not only prevent breaches but can withstand them when they happen.
FAQs
What happens if you are in a data breach?
If your personal information is compromised in a data breach, it can lead to several risks, including identity theft, financial fraud, and unauthorized access to your accounts.
Who is the owner of Star Health Insurance?
Star Health and Allied Insurance Company Limited is a publicly listed company in India. As of the latest available data, the ownership structure is as follows:
- Promoter and Promoter Group: Approximately 57.69%
- Public Shareholding: Approximately 42.31%
The promoter group includes a consortium led by WestBridge Capital, Madison Capital, and the late Rakesh Jhunjhunwala


Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.





















