Enterprise Cybersecurity Architecture With Solutions & Best Practices
Pansy
Dec 30, 2024
As your business scales, the risks you face and the threat landscape you get exposed to expand. Conventional cybersecurity practices may not make the cut anymore, given your organization’s maturity.
An enterprise cybersecurity program calls for a more sophisticated and integrated architecture with top-notch solutions. This blog talks about how your program needs to evolve, along with the best practices you must follow.
| TL;DR The core architecture of an enterprise cybersecurity strategy can be categorized as per governance, risk and compliance with seven main core components. Enterprise cybersec uses tools like IDS, and threat intelligence platforms provide centralized risk tracking, real-time monitoring, and predictive threat analysis. Regular risk assessments, multi-layered security, employee training, and robust incident response plans are foundational to safeguarding enterprise systems. |
What is enterprise cybersecurity? Why is it crucial?
Enterprise cybersecurity is a holistic approach to creating a strong security architecture to reduce vulnerabilities and ensure business continuity even in complex threat landscapes. It protects an organization’s digital assets, networks, systems, and data from cyber threats, unauthorized access, and potential breaches.
Enterprise cybersecurity isn’t about doing “more of the same” as you as a mid-market or small business. It’s about designing a cohesive strategy to unify protection, compliance, and resilience across every layer of an organization’s operations.
For example, enterprises often juggle multiple frameworks (SOC 2, ISO 27001, HITRUST) across geographies and industries, calling in the need for powerful tools that can integrate with a large environment.
Why is it crucial?
Enterprise cybersecurity prevents potential financial, reputational, and operational damage from cyberattacks and data breaches by setting the appropriate security measures in place.
Furthermore, enterprises get the attention of a great deal of security vulnerabilities. But, threat detection alone isn’t enough. Big companies require automated incident responses to mitigate risks quickly and consistently across their entire infrastructure.
What does enterprise cybersecurity architecture look like?
The architecture of an enterprise cybersecurity program can be categorized into the following seven core components closely linked with GRC (Governance, risk, and compliance):
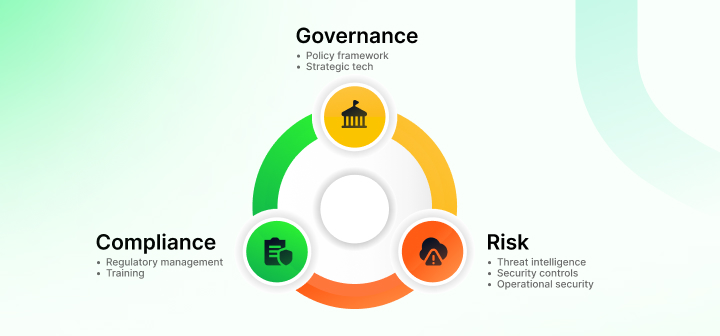
1. Governance and policy framework: Everything from setting up policies, processes, and documents to defining your cybersec program falls under governance. It aligns with regulatory requirements, sets clear roles and responsibilities, and holds accountability for respective personnel.
2. Risk management and assessment: You need to constantly scan for potential vulnerabilities, gather intelligence about emerging threats, and systematically evaluate risks. Conduct both deep numerical analyses and qualitative assessments to stay ahead of cyber threats.
3. Technical security controls: These defensive mechanisms protect networks, devices, and data from unauthorized access and malicious activities. They include
- Firewalls that block suspicious traffic
- Endpoint protection that shields individual devices
- Cloud security that protects remote resources
- Identity management that ensures only authorized personnel can access critical systems.
4. Operational security: This includes having a well-prepared incident response plan, maintaining detailed logs of all system activities, conducting threat hunting to uncover hidden risks, and continuously training employees to recognize and prevent potential security breaches.
5. Compliance and regulatory management: You need to align everything you do to industry cybersecurity standards and complex regulatory requirements. This function tracks adherence to frameworks like NIST and ISO 27001, prepares for rigorous audits, and maintains detailed documentation.
6. Strategic technology integration: Enterprise cybersecurity is also about ensuring that different security tools work together while eliminating gaps and redundancies. This creates a scalable and adaptable security infrastructure while keeping up with emerging technologies.
7. Human capital and skill development: You need to create a knowledgeable cybersecurity workforce through targeted training, continuous learning, and skill enhancement. It involves identifying skill gaps, developing professional growth programs, and creating a culture where every employee understands their role.
How to create your enterprise cybersecurity solutions stack?
Enterprise cybersecurity is incomplete without high-end software. These advanced tools go beyond traditional security measures and offer intelligent and adaptive protection across your entire digital ecosystem.
Here are five cybersecurity solutions an enterprise needs:
1. Governance, risk, and compliance (GRC) software
GRC solutions integrate policy management, risk assessment, and regulatory compliance into a unified framework. You can automate compliance tracking, get access to comprehensive risk dashboards, manage policy workflows, and have detailed reporting capabilities.
These are some features you must have at an enterprise level:
- Centralized risk register and assessment dashboards
- Automated compliance documentation
- Integration with multiple regulatory cybersecurity frameworks
- Real-time risk control, scoring, and prioritization
Two widely known examples of GRC software include Sprinto and Vanta. These solutions provide you with AI-assisted security control mapping to risks & policies to make things even simpler for large organizations.
2. Security incident and event management tools (SIEM)
SIEM platforms collect, aggregate, and analyze log data from across your entire IT environment. You can expect real-time monitoring and advanced threat detection. They fundamentally transform raw security data into actionable intelligence.
SIEM tools are especially beneficial for security and GRC teams to identify, investigate, and respond to potential security incidents quickly and effectively. SIEM use cases can be expressed with feature like:
- Detailed log management
- Real-time threat detection
- Advanced correlation and analytics
- Automated incident response workflows
- Detailed forensic investigation tools
The best two SIEM tools worth mentioning are SolarWinds Security Event Manager and Graylog. They cover all the features mentioned above along with data visualization and historical analysis.
3. Intrusion detection systems (IDS)
The global market for intrusion detection systems is expected to surge to $16.42 billion by 2031 with a compound annual growth rate (CAGR) of 12.7% over the forecast period (2024–2031).
The analysis points to the importance of continuously monitoring enterprise network traffic for suspicious activities and potential breaches with IDS tools. These systems can be network-based, examining entire network traffic, or host-based, focusing on individual device activities.
IDS software provide critical insights into potential threats, generating immediate alerts when unusual or malicious patterns are detected.
Some of the best IDS tools in the market include AIDE, Cisco NGIPS, Palo Alto Networks, and BluVector Cortex.
4. Endpoint security tools
Endpoint security tools would be like your frontline defenders that protect individual devices within your enterprise’s network. These tools monitor endpoint devices of your employees, vendors, contractors etc including laptops, smartphones, and tablets against a wide range of cyber threats.
Endpoint security tools include solutions like antivirus protection, anti-malware capabilities, firewall management, and advanced threat prevention. The prominent features of such solutions include:
- Real-time threat protection
- Machine learning-powered detection
- Remote device management
- Automated threat response
- Comprehensive device visibility
As per Gartner, the best endpoint security tools include Sentinel One, Crowdstrike Falcon, Microsoft Defender, Trellix, and Sophos.
5. Threat intelligence software
One of the most common challenges in enterprise businesses is continuously gathering and analyzing data about potential cyber threats from global sources. Due to the magnitude of the sources, it is absolutely necessary that you take help from a threat intelligence software.
Threat intelligence provides you with predictive insights that will help you understand emerging risks, anticipate potential attacks, and proactively strengthen your security posture.
While evaluating tools, look for features like:
- Global threat data aggregation
- Contextual threat analysis
- Predictive risk scoring
- Automated threat correlation
- Strategic threat insights
As per our research, the best cyber threat intelligence software in the market currently are Anomali, Kaspersky, Cisco Umbrella, and Threatconnect.
Best practices for your enterprise cybersecurity strategy
A cybersecurity strategy is not merely a one-time effort but an ongoing commitment that requires the adoption of best practices. Here are some essential practices every organization should implement:
1. Conduct regular risk assessments
In enterprises, risk assessments must account for a far more extensive attack surface, including hybrid cloud environments, globally distributed teams, and third-party vendors. You may often deal with overlapping compliance mandates (e.g., GDPR, CCPA, and HIPAA) which makes assessments more complex.
One solution would be to use frameworks like FAIR or NIST CSF that are often employed to quantify risks in monetary terms and drive executive buy-in.
2. Implement a multi-layered security architecture
With an enterprise, you cannot have a security architecture with a single layer; employing multiple defenses is crucial. A multi-layered approach incorporates firewalls, intrusion detection systems, endpoint protection, and more. An approach like this ensures that if one layer fails, the others will remain intact to thwart attacks and protect your business.
3. Mandate MFA (multi-factor authentication)
In mid-market environments, MFA implementation is straightforward. Enterprises, however, must enforce MFA across various entities like employees, contractors, and privileged accounts. This is true across multiple geographies.
Additionally, if you’re using adaptive MFA, consider implementing AI-driven risk assessments to ensure usability without compromising security.
4. Scale your security awareness and training program
Employees are often considered the weakest link in an organization’s cybersecurity chain. Regular security awareness and compliance training are essential to motivate your workforce to recognize potential threats, such as phishing attempts or social engineering attacks.
As an enterprise, leverage gamified platforms, multilingual content, and role-based scenarios to achieve engagement at scale. You must also use advanced KPIs, such as phishing simulation success rates, to measure effectiveness.
5. Prioritize incident response and recovery plans
Going through a breach is not actually the worst thing that could happen to your business. Not having a response plan is the ultimate down-bad.
Your incident response and recovery plan should outline the steps to take in the event of a breach, from detection and containment to recovery and communication. Also, consider external dependencies like regulatory reporting and public relations strategies to mitigate reputational damage.
Future of your enterprise cybersecurity program
Like all other spaces and evolving industries, the future of enterprise cybersecurity too, lies with AI and ML capabilities. Although most businesses are only experimenting on this front, the cybersecurity industry is quite ahead of its time. For example, there are already frameworks and standards like ISO 42001 that outline best practices you should incorporate into your workflow while working with AI. However, there are concerns.
AI systems, while transformative, can amplify risks if not managed thoughtfully. Enterprises must adopt clear policies that use ethical AI, data transparency, and accountability. Missteps, here, could lead to biased decision-making, compliance violations, or even reputational harm.
A cautious approach to AI starts with embedding governance frameworks and aligning them with compliance and risk management strategies. This foundation not only reduces immediate risks but also ensures your cybersecurity program evolves responsibly as AI capabilities expand.
GRC programs built for fast-growing companies
Frequently asked questions
1. What common problems do enterprises face in cybersecurity?
The most common problems faced by enterprises in cybersecurity are:
- Phishing and social engineering attacks.
- Weak or reused passwords.
- Insider threats.
- Lack of employee training.
- Outdated or unpatched systems.
- Compliance challenges
2. What is an enterprise firewall?
An enterprise firewall is a security device or software that monitors and filters incoming and outgoing network traffic based on pre-defined rules. It protects the enterprise network from unauthorized access and threats.
3. What is the role of enterprise security?
The role of enterprise security is to protect an organization’s data, systems, and networks against breaches, ensuring confidentiality, integrity, and availability while supporting compliance and business continuity.
4. What are best cybersecurity tools?
The best cybersecurity tools include:
- Antivirus: Norton, Bitdefender.
- Firewalls: Palo Alto Networks, Fortinet.
- SIEM: Splunk, IBM QRadar.
- IAM: Okta, Ping Identity.
- Endpoint Protection: CrowdStrike, SentinelOne.
- Compliance: Sprinto, Vanta.


Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.


























