NIST Asset Management Beginners Guide
Meeba Gracy
Oct 16, 2024
The biggest challenge that large organizations face is the handling of resources. This can include everything from computers, mobile devices, and other endpoint devices to operating systems, applications, data, and networks. Not knowing where each asset is or knowing how they function can prove problematic.
Even more so when all of this is handled with legacy tools and processes. And this is precisely where NIST asset management comes into play.
In this article, we take a detailed look into NIST asset management and how you can streamline your approach while staying compliant with the NIST framework.
What is NIST asset management?
The NIST Asset Management is a way of managing a company’s digital resources. Unlike physical asset management systems that only track the location of hardware like computers, NIST asset management goes further.
It helps answer critical questions such as:
- What operating systems are our laptops running?
- Which devices are vulnerable to the latest threats?
Hence, when you connect both physical and virtual assets, an effective NIST Cybersecurity IT asset management (ITAM) solution offers a complete view of what assets exist, where they are, and how they are being used.
This way, you get greater visibility on your security measures.
Why is NIST asset management important?
NIST asset management is not only a great approach to tracking your assets, but it significantly improves your cybersecurity resilience. Implementing NIST asset management helps you control access to your assets at a granular level while establishing best practices to help you safeguard sensitive data across processes.
Here are some other advantages that NIST asset management affords:
- It improves your visibility on your assets, so you know exactly what you’ve got and where they are
- You can identify vulnerable assets and beef up their defenses
- It also acts like a spotlight on your applications – you’ll see which ones are being used, saving you time and resources
- It provides detailed system information to auditors
- Determines how many software licenses are used and how many have been paid for
- Reduces the attack surface of every device by ensuring that the software is correctly patched
How to set up the NIST asset management process?
Now, when it comes to setting up the NIST asset management process, you need to put in a lot of manual effort.
Implementing the NIST asset management process is arduous, often requiring much manual work. However, as an enterprise with greater business objectives, it’s high time you find a simpler solution.
Here’s a step-by-step guide to help you get started:
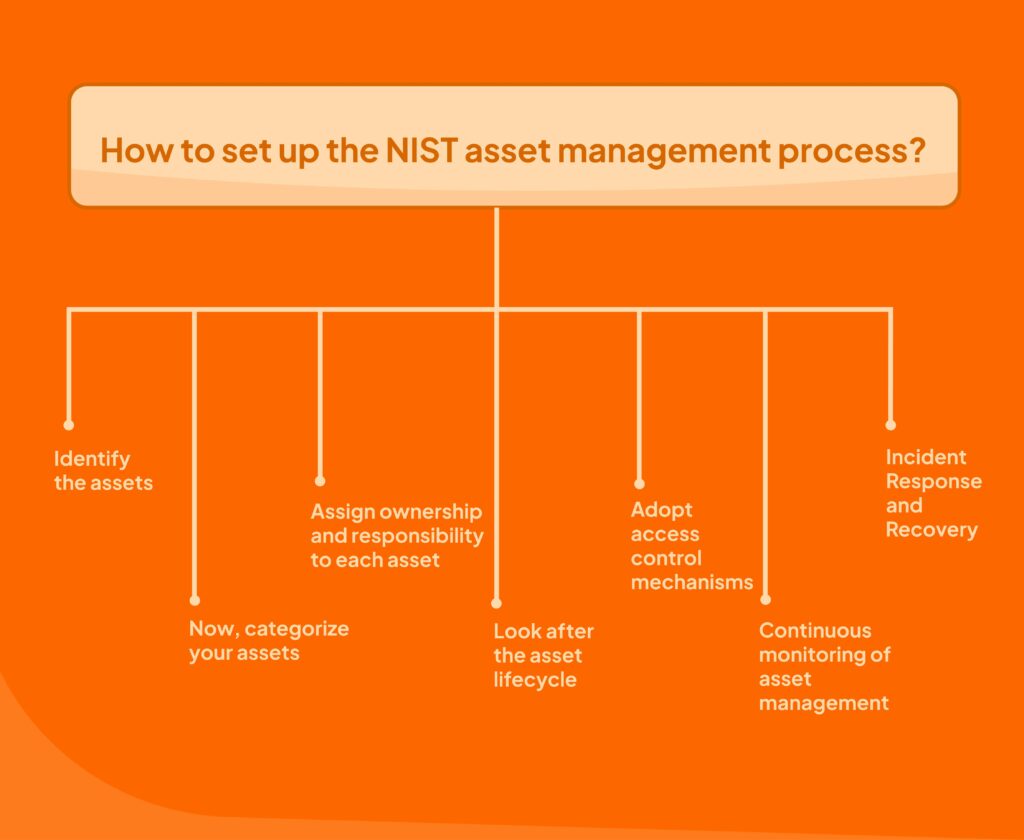
Identify the assets
This is the first step towards asset management, and it involves the meticulous identification of all entities existing within your company’s network. Asset identification helps you build your digital inventory and gives detailed descriptions of each asset and its function.
Asset categorization
Guided by the principles outlined in NIST 800-53, you have to divide your assets based on their importance and sensitivity within your organizational framework. There are three tiers of categories—high, moderate, and low.
These categories tell you which assets are extremely important and must be safeguarded at all costs, which are important and must be granted strictly authorized access, and which are somewhat important.
Assign ownership and responsibility to each asset
For effective asset management, each asset must have an owner who is responsible for everything concerning the asset. This means that you should choose specific people in charge of looking after certain assets.
They are responsible for ensuring the appropriate security rules are followed, and data is kept secure. However, manually compiling this process takes a lot of time.
The Sprinto advantage:
Sprinto simplifies asset management by allowing you to assign an owner to each of your assets. When an asset has an assigned owner, it becomes responsible for addressing any issues detected from the specified source within the defined Service Level Agreement (SLA). This approach ensures accountability and efficient issue resolution for your assets.
Manage the asset lifecycle
Every asset you install in your organization has a lifecycle. This includes procurement, deployment, maintenance, and eventually retirement. NIST 800-53 specifically underscores how to manage this journey diligently.
It often involves anticipating what could go wrong at each step and placing preventive measures to help eliminate possible vulnerabilities.
Enable access control
Asset control measures can prove invaluable in eliminating unauthorized access and potential data breaches. NIST asset management helps adopt an access control mechanism based on the principle of least privilege.
This principle restricts users’ access rights to only what is absolutely necessary to perform their job. When you follow this principle, your users will have only the minimal access required for task completion.
As a bonus, we have collated the NIST 800-53 Controls List to help you with the risk assessment. Take a look:
Download Your NIST 800-53 Controls List
Continuous monitoring of asset management
The next step is to monitor your assets and check how well your asset management system works. As time passes, risks can change—your risk surface can increase, decrease, or even disappear. However, constantly monitoring the assets is a process companies must have in place.
How does Sprinto help in continuous monitoring?
Sprinto handles all your compliance-related tasks, such as continuously monitoring your assets and alerting you of any misses or anomalies. It also keeps track of your controls in real-time and gives you a bird’s eye view of your compliance and security posture to help you make better decisions.
Incident response and recovery
Even if you have the most powerful security infrastructure, the possibility of threats from malicious actors will always be high. NIST asset management advocates creating incident response and recovery strategies to mitigate such risk’s impact.
How does Sprinto handle this?
- Sprinto provides you with out-of-box policy templates that can easily be replicated and deployed
- You can conduct a precise risk analysis that integrates with your cloud, swiftly identifying and fixing security gaps
- The built-in notification system alerts you when controls are about to fail
- Sprinto also provides training to enhance your team’s ability to handle sensitive assets, strengthening your security posture
So, why don’t you give it a try? Talk to our experts here!
Benefits of NIST Asset Management
NIST asset management provides a centralized overview of your networked software and hardware, and always works to reduce vulnerabilities. There are several benefits of NIST asset management, like transparency, and visibility.
Let’s break it all down:

Collecting data
This process focuses on cataloging and reporting unique software and system details, creating a list of crucial asset attributes. With data collection, your business will better understand its digital space, enabling you to make data-driven choices and enhance overall operational efficiency.
Get security visibility
Security visibility is another benefit of NIST asset management. Being well-prepared to respond effectively is beneficial. An inventory of assets and associated risks becomes invaluable when security incidents occur.
Your team can use this inventory to gain context about the nature of the attack and its timeline. Instead of dealing with the arduous task of investigating the origins of a breach or vulnerability, you can turn to your up-to-date records for immediate insights by looking at the inventory.
Get proactive response
Proactive response is an important aspect of NIST asset management. It revolves around early threat detection and ensures that your security teams can identify potential risks and vulnerabilities before they escalate into security incidents.
The key to getting a proactive response is continuously monitoring your IT estate and actively scanning for new deployments and potential threats. Unlike reactive measures that wait to detect an ongoing attack, proactive response helps your teams to take action swiftly.
NIST with Sprinto
Managing your IT assets with the NIST Cybersecurity Framework may present challenges, but the effort is undoubtedly worth it. This framework focuses on outcomes instead of specific controls, thus enabling organizations to establish a solid foundation to adapt to new regulations.
Doing this manually can be expensive, time-consuming, and error-prone. As a business owner, you’d rather channel your time and effort on business development and expansion rather than on repetitive, monotonous, compliance-related tasks.
Sprinto is a compliance automation platform that helps you simplify this process. Our compliance automation engine automates most compliance activities, allowing you to focus on running your business better.
Not only can you align your organization with any compliance framework, but Sprinto helps you bring down the time you need to become compliant from months to weeks.
Book a demo today to discover how to streamline your compliance journey.
FAQs
What are the 5 components of the NIST framework?
The NIST framework consists of five key components known as the Framework Core. These components encompass the following core functions: Identify, Protect, Detect, Respond, and Recover.
What is the NIST checklist?
The NIST checklist refers to the National Checklist Repository maintained by the NIST. It serves as an openly accessible repository that houses a wealth of information about security configuration checklists designed for specific IT products or categories of IT products.
What is the NIST definition of assets?
According to NIST, assets can be classified into tangible and intangible. Tangible assets refer to physical items like hardware, firmware, computing platforms, network devices, and other technology components. On the other hand, intangible assets encompass humans, data, information, software, capabilities, functions, services, trademarks, copyrights, patents, intellectual property, images, and reputations.


Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.


























