Key Points
- PCI DSS is a global cybersecurity standard that applies to any cloud-hosted company that stores, transmits, accepts, or processes cardholder data and sensitive authentication data. Depending on the annual Visa transaction volumes, companies are assigned different PCI compliance levels (Levels 1-4).
- PCI DSS protects two types of data: cardholder data that includes the cardholder’s name, primary account number, service code, and card expiration date, and sensitive authentication data that includes card validation codes (CVV, CVC2, CAV2, CID), tracking data from the magnetic stripe or card chip, and PIN and PIN blocks.
- PCI DSS was implemented by the PCI Security Standards Council founded by five major card payment companies (MasterCard, Visa, American Express, Discover, and JCB) to prevent cybercriminals from accessing personal consumer financial data throughout the card-processing ecosystem. Although not legally binding, it is adopted by financial entities worldwide as a security standard to prevent financial fraud.
Introduction
The Payment Card Industry Data Security Standard (PCI DSS) was created by the PCI Security Standards Council (PCI SSC) to protect sensitive transaction data and keep it secure from cybersecurity threats. The PCI SSC is an independent organization founded in 2006 by major payment card companies like American Express, MasterCard, Visa, JCB International, and Discover Financial Services. Its primary job is to supervise the establishment and evolution of the PCI DSS.
The PCI DSS is a set of security standards meant to protect payment systems from financial fraud, data breaches, and theft of cardholder data (CHD). The primary players in the payment card industry needed a way to align and standardize their security requirements, hence the birth of PCI DSS.
The latest version 4.0 was rolled out on March 31st, 2022, which has made automated mechanisms to prevent phishing compulsory. The previous PCI DSS version 3.2.1 will cease to be active on March 31st, 2024—which means you have two years to comply with the latest requirements.
To whom does PCI DSS apply? Let’s explore the security standard in detail in this article.
Who does PCI-DSS apply to?
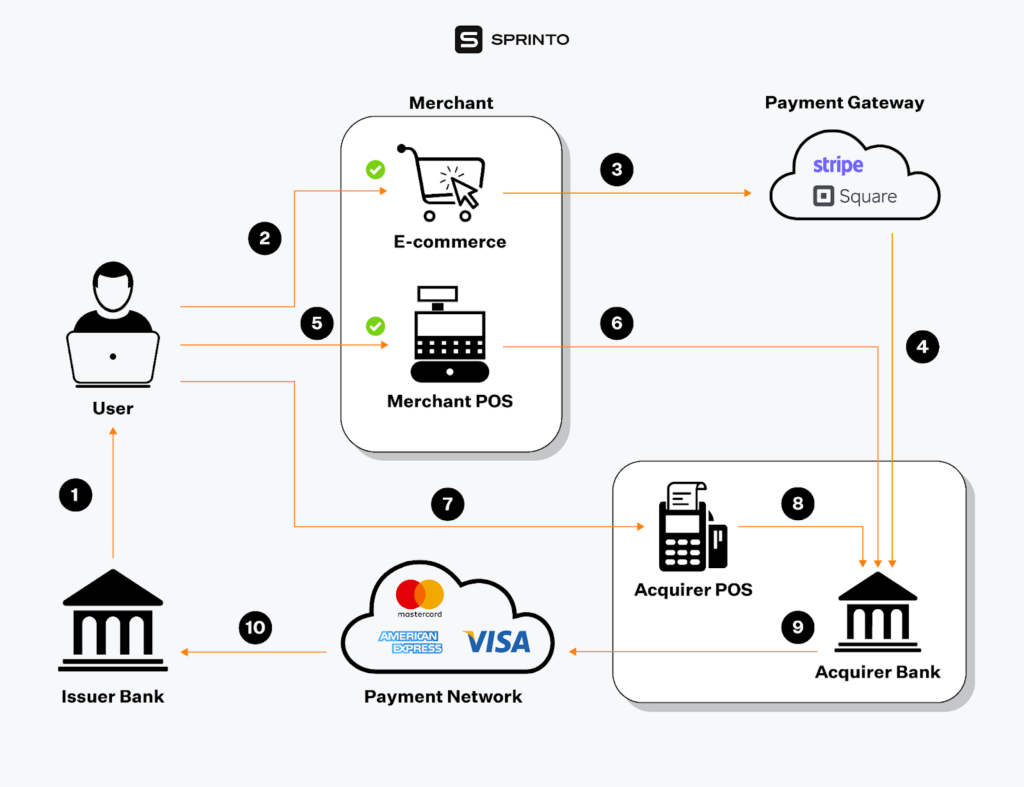
The PCI DSS applies to a wide range of entities involved in payment card processing; specifically, all organizations that store, process, and/or transmit cardholder data must comply with PCI DSS. This includes:
- Merchants: Businesses that accept payment cards for goods or services
- Issuers: Financial institutions that issue payment cards to consumers
- Acquirers: Banks that process payment card transactions for merchants
- Processors: Entities that handle payment card transactions on behalf of merchants or banks
- The standard covers both technical and operational system components that are included in or connected to cardholder data environments.
Third-party service providers that could impact the security of payment card data must also comply with relevant PCI DSS requirements.
PCI DSS applies regardless of an organization’s size or transaction volume. Even small businesses that process a low volume of transactions must comply.
The standard is applicable to all payment channels, including:
- In-person transactions
- Online payments
- Phone orders
- Mail orders
Importantly, PCI DSS applies even if an organization doesn’t store cardholder data. Simply processing or transmitting this data necessitates compliance.
To see where you are in terms of getting PCI DSS complaint, first check your eligibility. Download the questionnaire below:
Download your PCI DSS Self Assessment Questionnaire
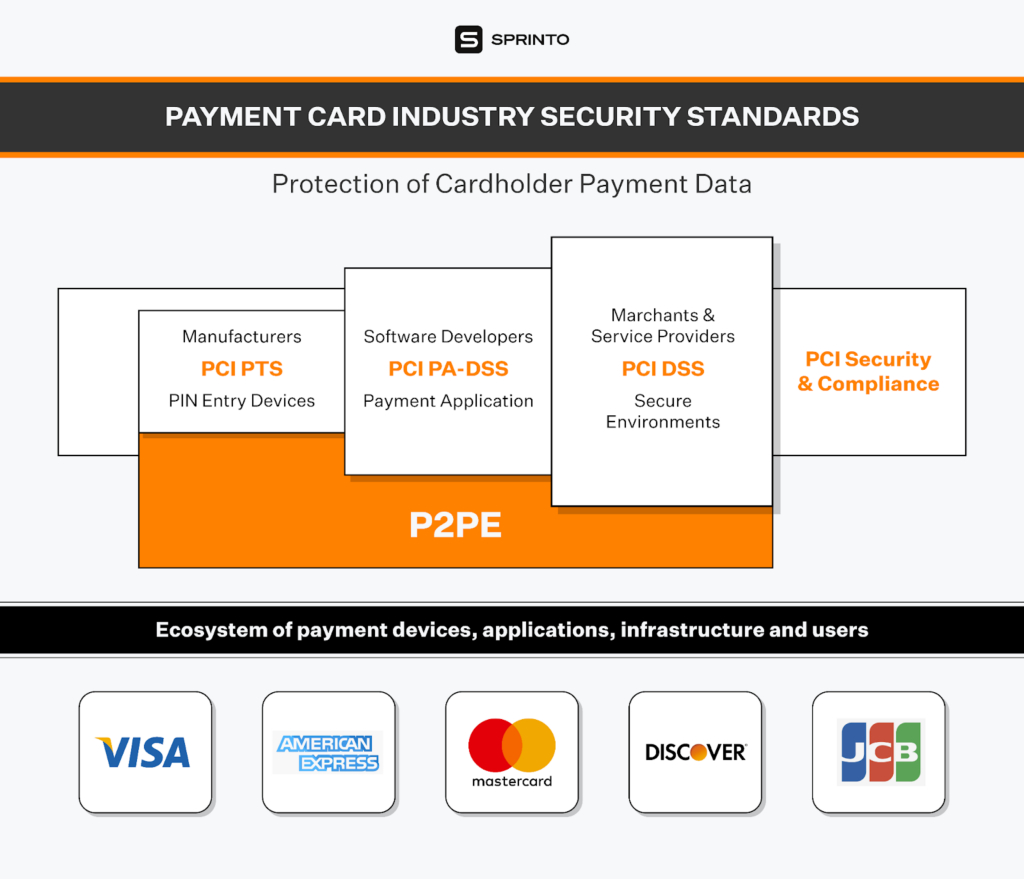
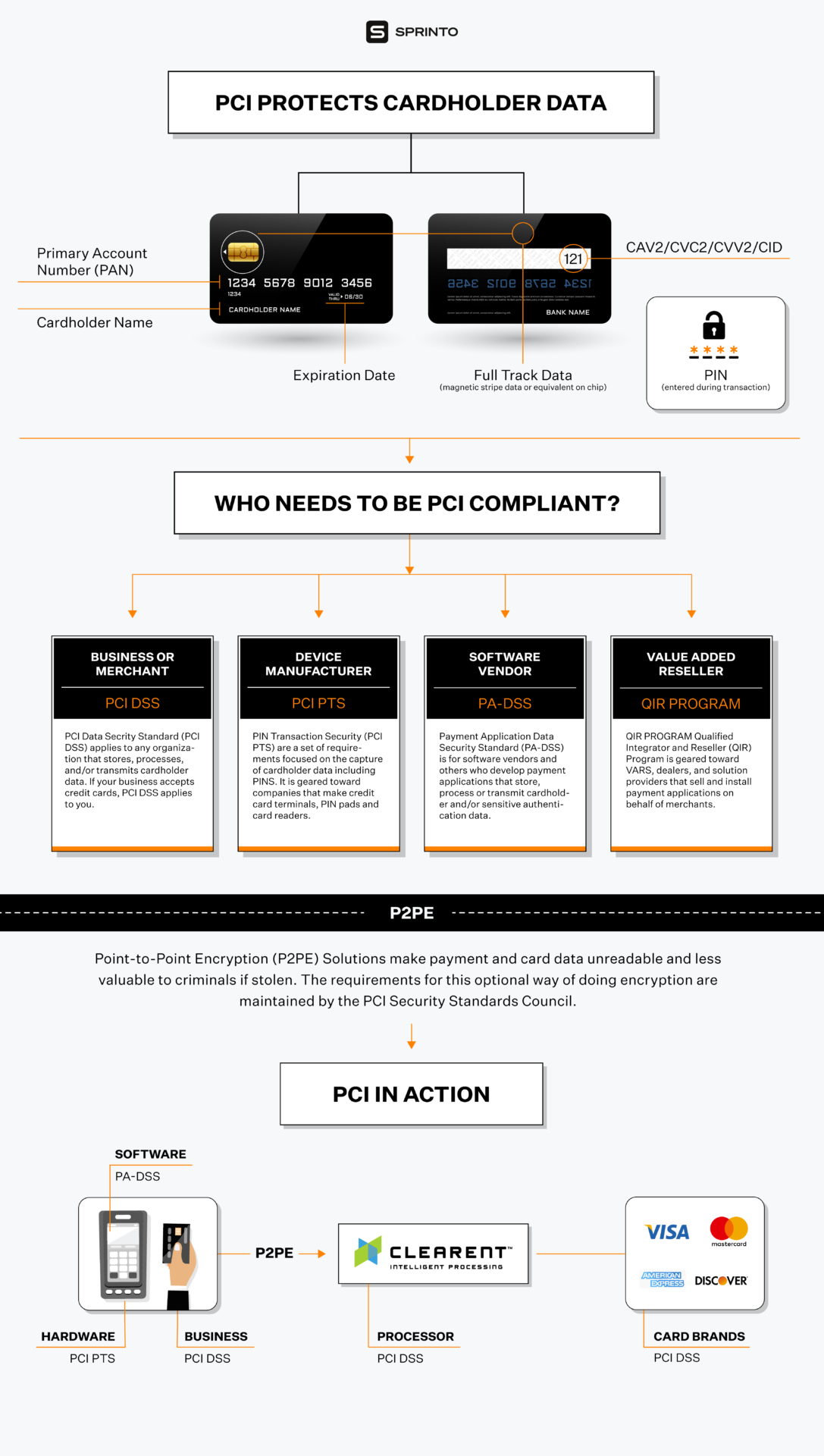
What type of data does PCI DSS protect?
The PCI Data Security Standard (PCI DSS) aims to safeguard sensitive authentication data and cardholder data wherever they are processed, stored, or transmitted. CVV, Card Number, PAN, and other pieces of information that can connect an attacker to a user’s bank information are included in it.
PCI DSS protects two types of data:
Cardholder data
Includes the full Primary Account Number (PAN) along with expiration date, cardholder’s name, and service code.
PCI DSS version 3.2 allows cardholder data to be stored and doesn’t mandate that it be made unreadable. But it requires you to minimize storage and implement clear disposal and data retention policies.
Sensitive authentication data
Includes PIN and PIN blocks, card validation codes (CVC2, CVV, CAV2, CID), and tracking data from a card chip or magnetic stripe.
PCI DSS version 3.2 mandates that sensitive authentication data should not be stored, even if it is encrypted. Once authorization is done, all such data should be unrecoverable.
You may store PAN data but it must be unreadable in every storage location such as logs, backup files, and portable digital media. According to PCI SS, you can use one-way hashes, truncation, index tokens and pads, and key-based encryption to make sensitive authentication data unreadable.
Since a hashed and truncated version of the same PAN can be used to reconstruct the data, if your cloud-hosted company uses both, you must implement additional security measures to prevent hackers from retracing the PAN data.
What is the purpose of PCI-DSS?
Merchants, or entities that accept payment cards with the logo of the five members of the PCI SSC (MasterCard, Visa, American Express, JCB, and Discover), are low-hanging fruit for perpetrators of financial fraud.
Each time a merchant processes, accepts, or transmits payment data, it exposes itself to a potential data breach. Often, such merchants have poor security systems that enable cybercriminals to easily steal sensitive consumer financial data.
Vulnerabilities may exist in several areas of the card processing ecosystem:
- Point-of-sale (POS) devices
- Wireless hotspots
- Personal computers
- Unsafe transmission of card data to service providers
- Paper-based storage
PCI DSS ensures that payment card transactions are as secure as possible. Since credit card issuers and banks typically refund customers in case of fraudulent purchases, they have a vested interest in backing this cybersecurity standard.
Thus, even though PCI DSS is not legally binding nor does it supersede any national or local laws, it is uniformly adopted by in-scope organizations all over the world.
Also check out: How to perform a PCI vulnerability scan.
When did PCI DSS become mandatory?
PCI DSS became mandatory after version 1.0 was released on December 15, 2004. However, we have already noted that it is not a legal requirement but a security standard.
So, “mandatory” here means that when cloud-hosted companies or merchants sign contracts with payment card companies and banks that handle payment processing, being PCI DSS compliant is a prerequisite.
For cloud-hosted companies like you, PCI DSS compliance and cardholder information security are assessed via a self-assessment questionnaire (SAQ), which also includes an Attestation of Compliance (AOC). The AOC attests to your company’s compliance with PCI DSS.
If a data breach occurs in your transaction systems that is deemed to be caused by a failure to implement the PCI DSS correctly, your card company or payment processor may impose sanctions. You could be required to pay a hefty fine or pay for an assessment to prove that your security systems have been improved.
PCI DSS Who Does It Apply To?
PCI DSS applies to any your cloud-hosted company that accepts card payments. There’s no “certification” for PCI DSS compliance, instead, you prove your compliance through self-assessment i.e. by completing the SAQ and the AOC.
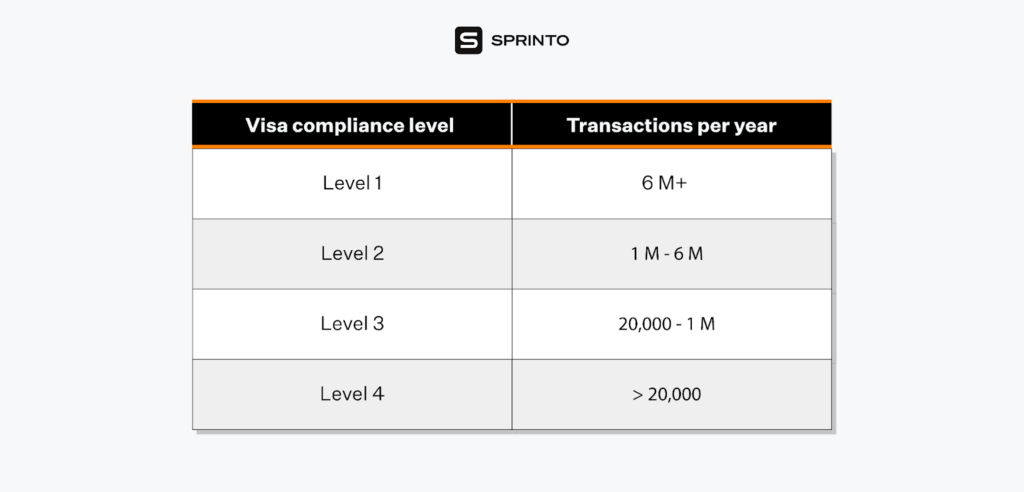
There are four PCI compliance levels determined by your Visa transaction volumes over a 12-month period:
- Level 1 companies must provide an annual Report on Compliance (RoC) that includes an audit by a Qualified Security Assessor (QSA) or Internal Security Assessor (ISA).
- Level 2-4 companies may complete the SAQ that has different versions to cater to different businesses and payment processing methods.
Note that compliance level requirements may slightly differ based on card schemes. For instance, MasterCard requires level 2 companies to complete the SAQ with the help of a QSA or ISA.
Non-compliance with PCI DSS attracts fines, but not in the general sense of the word. Instead of forking out separate fines for violations, penalties are baked into contracts between cloud-hosted companies and card payment companies or payment processors.
Penalties are levied per month of non-compliance and may increase with increasing periods of non-compliance. Amounts could go up to $100,00 per month and card payment companies may choose to terminate their contracts with you. If you face a data breach, your compliance level could be increased.
Worse still, you could be put on the Merchant Alert to Control High-Risk (MATCH) list that bans you from processing card payments anymore.
How do I know if I am PCI compliant?
You can confirm PCI compliance by completing the required Self-Assessment Questionnaire (SAQ) or undergoing an audit by a Qualified Security Assessor (QSA), depending on your PCI level. Once completed, you must submit an Attestation of Compliance (AOC) to your acquiring bank or payment processor. If you pass these steps, your business is considered PCI compliant.
Steps to check PCI compliance:
- Identify your PCI merchant level (based on annual transaction volume).
- Complete the correct Self-Assessment Questionnaire (SAQ).
- Conduct quarterly network scans (if required).
- Submit an Attestation of Compliance (AOC) to your bank or processor.
- For Level 1 merchants: Complete an annual Report on Compliance (RoC) through a Qualified Security Assessor (QSA).
Conclusion
Now that you’re clear about who PCI DSS applies to, your cloud-hosted company must meet cardholder security standards to ensure that your transactions are secure.
PCI DSS compliance requirements may seem overwhelming but they can be boiled down to three steps performed regularly—assess, remediate, and report. By adopting a proactive approach to mitigating potential network security concerns like data breaches, you can easily unlock your company’s growth.
Let Sprinto help you with PCI DSS preparations that include automated evidence collection, a clear checklist of requirements, security monitoring, managed implementation, and zero-touch audits.
FAQ
There are four PCI DSS levels determined by the volume of transactions processed each year:
– Level 1 = Companies that process over 6 million transactions per year
– Level 2 = Companies that process 1 million – 6 million transactions per year
– Level 3 = Companies that process 20,000 – 1 million transactions per year
– Level 4 = Companies that process less than 20,000 transactions per year
Card data covered by PCI DSS includes the primary account number (PAN), the cardholder’s name, the card expiration date, and the security code.
Pritesh Vora
Pritesh is a founding team member and VP Growth & Marketing at Sprinto. He comes with over a decade of experience and is a data-driven dynamo in growth strategy, sales, and marketing! His strategies have crafted the success of not one, but two early-stage SaaS startups to 7-digit revenues within a year – he’s your go to guy for all things growth.
Explore more
research & insights curated to help you earn a seat at the table.
























