Cybersecurity Framework: All You Need To Know In 2024
Meeba Gracy
Apr 06, 2024
Hackers are becoming increasingly creative. They now use sophisticated wares to access and steal sensitive information.
Irrespective of whether we’re referencing sophisticated groups hacking computers for fun or agencies looking to access and steal information, it is crucial that you have a strong cybersecurity framework that thwarts such attempts.
In this blog post, we’ll explore cybersecurity frameworks and how they help in keeping your data safe in 2023.
What is Meant by Cybersecurity Framework?
Cybersecurity frameworks are an essential set of documents that help reduce the risk of cyber attacks. These guidelines, standards and best practices ensure that any vulnerabilities or weaknesses present can be managed proactively in order to protect against malicious hackers and other criminals who may attempt to exploit them.
It has three parts, namely:
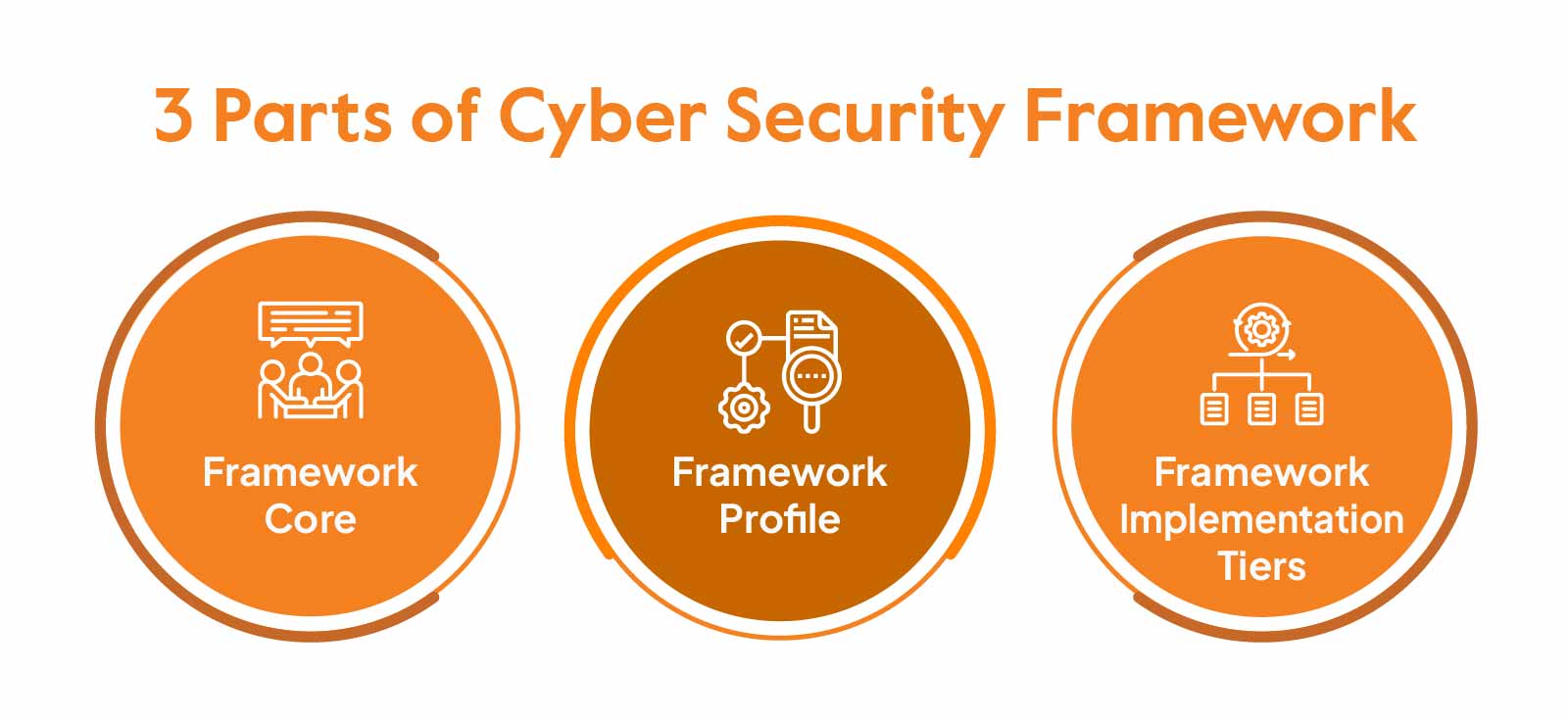
- Framework core
- Framework Profile
- Framework Implementation Tiers
Let’s go into this in detail.
Cyber security frameworks may seem like daunting, complex jargon; however, they are actually quite straightforward. These guidelines help organizations reduce their risk of cyber-attack exposure and keep their data secure.
Visualize it as a resilient structure that reinforces the stability of your building or bridge. It stands strong and unyielding, serving as an ideal base for your business to combat any faults or vulnerabilities cyber attackers may try to exploit in order to penetrate into your system.
In simpler words, this is an assemblage of best practices engineered towards safeguarding the digital infrastructure within your organization from potential threats.
Why Do Organizations Require a Cybersecurity Framework?
Cybersecurity frameworks provide organizations with detailed documents outlining guidelines, standards and best practices for managing cyber security risk.
When you use these frameworks to address vulnerabilities that hackers may exploit, you can reduce your exposure to malicious activities and protect yourselves against digital threats.
Cybersecurity frameworks provide organizations with an invaluable advantage— they can accurately assess their current security stance and pinpoint any potential weaknesses. This allows you to make informed decisions on where to allocate resources for enhancing safety.
The cybersecurity frameworks typically follow five main processes defining the security approach. These processes are Identity, Protect, Detect, Respond, and Recover.
- The Identity process helps identify and understand the assets that need to be protected, while the
- Protect process identifies the controls needed to secure the assets
- The Detect process focuses on identifying any threats, and the
- Response process outlines the steps to be taken in the event of a security incident
- Recover process aims to recover the systems and data after an attack or a breach
So, if you haven’t already, it’s time to start implementing cybersecurity frameworks to avoid risks and stay secure.
Also, check out a detailed guide to cyber security compliance.
Types of Cybersecurity Frameworks
Now, you might be interested in picking out a perfect cybersecurity framework that will suit your company. Again, your choice should ultimately depend solely on your organization’s needs. Here are some cyber security frameworks examples you should keep an eye on to comply with standards:
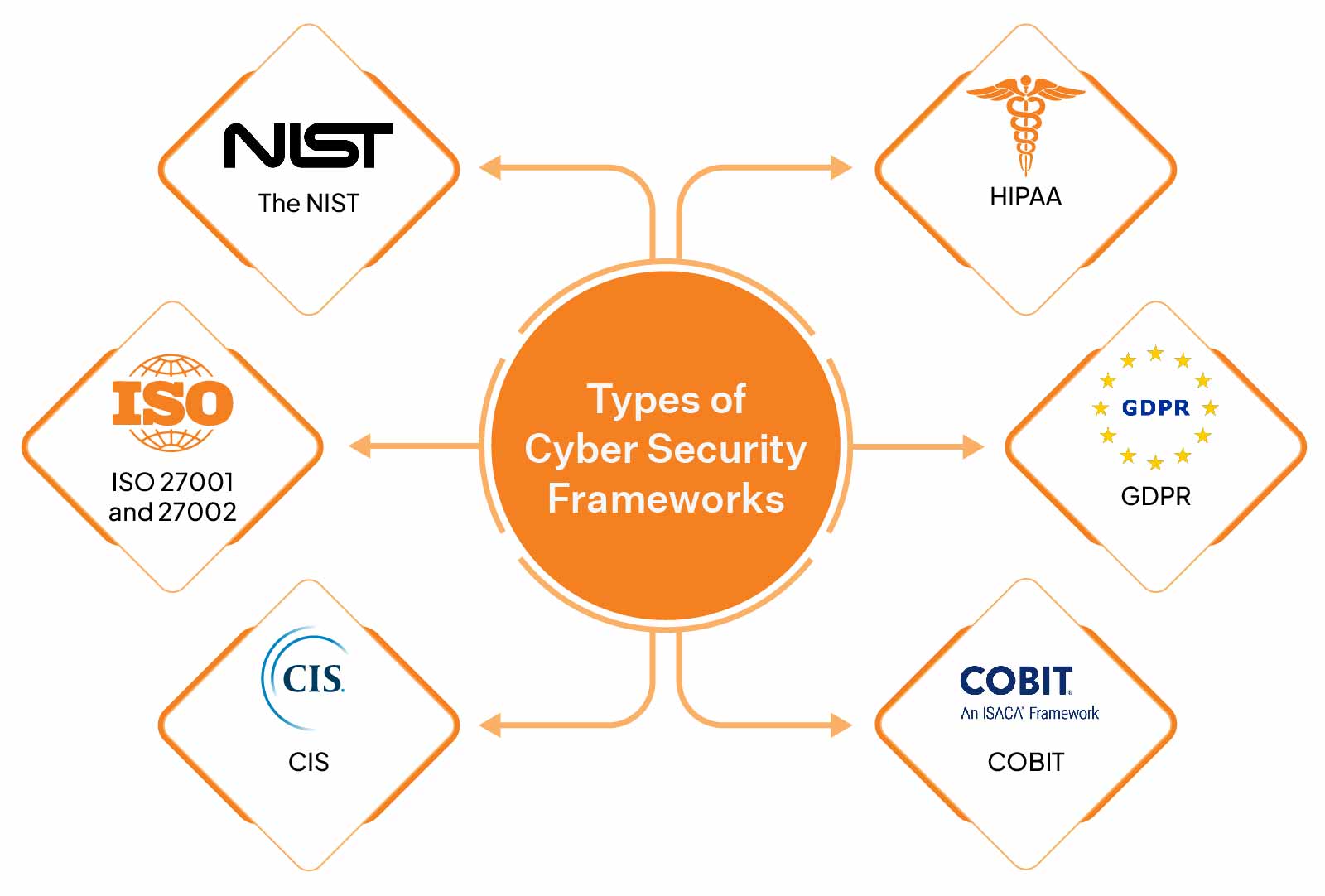
NIST
The NIST framework, designed to protect America’s critical infrastructure from cyberattacks, was the answer to an Executive Order issued by the Obama Administration. A tool for private sector companies to detect, respond to, and recover from cyber threats, it features five key functions:
- Identify
- Protect
- Detect
- Respond
- Recover
These functions are carefully crafted guidelines that allow your company to take preventive cyberattack measures. This framework also indicates how you should conduct yourself during a cyber incident. This voluntary framework is a step forward in bettering your cybersecurity defenses.
But one of the common questions many companies have is, “why should I comply with the NIST framework out of all the cyber security framework list?”
The main reason is that because of the amount of testing that goes into the publication they release. It involves months, weeks, and sometimes years of testing under the radar for a long time. A team of prominent professionals in the field will do the research. Hence the publications are accurate both technically and informationally.
ISO 27001 and 27002
For those looking to up their cyber security game, there’s ISO/IEC 27001 and 27002, otherwise known as the ISO 270K framework. It’s a globally accepted standard for managing information security across internal situations and third parties.
To use it, you must have an Information Security Management System set up – it includes 114 super stringent controls divided into 14 categories. That might sound daunting (and it is!), but once implemented, these standards can act as a huge selling point for your organization and help draw in new customers who want to feel protected against potential threats.
The Center for Internet Security Critical Security Controls (CIS)
CIS is the perfect level to start from if your company wants to increase cybersecurity step by step. Developed in the late 2000s, it provides 20 carefully-selected controls updated regularly by professionals from various industries like academia, government, and industry.
These controls span fundamental, foundational, and organizational levels mapped to common standards like HIPAA and NIST. Even those organizations not subject to particular protocols can benefit from its configurations that ensure their cyber security is up to scratch.
The Health Insurance and Portability and Accountability Act (HIPAA)
HIPAA is vital to the healthcare industry, serving as a defense against potential data breaches. This critical cyber security framework safeguards patient records and other confidential information, ensuring that all personal data remains secure.
Compliance with HIPAA ensures that all healthcare operators will provide their patients with the necessary privacy protocols to keep them relaxed and confident in their healthcare choice. Without it, individuals’ delicate healthcare data could be exposed quickly and without notice, leading to severe consequences for companies and consumers alike.
The General Data Protection Regulation (GDPR)
GDPR — the General Data Protection Regulation — is widely seen as one of the most stringent and secure programs for data privacy worldwide. It was developed by the European Union to better protect the data held by EU citizens, from SMEs to large organizations.
Its reach extends across borders, too; even companies based elsewhere but still offer services or products in Europe must abide by its rules when handling sensitive data in online transfers. This shows just how seriously they take protecting their citizens’ digital privacy – something we can all learn from.
Control Objectives for Information and Related Technologies (COBIT)
The COBIT cybersecurity framework was created by the ISACA (Information Systems Audit and Control Association) to introduce a comprehensive IT governance and management system.
When implementing COBIT, organizations can take the necessary steps to protect data from all potential vulnerabilities, allowing them complete end-to-end coverage. It was an ambitious move, as the world has become increasingly reliant on technology, and large companies carry hefty amounts of sensitive data stored in cloud computing systems and social media accounts.
Although it may not seem evident initially, COBIT can provide a way for your organization to defend your information through proactive measures to enhance enterprise security.
A Smarter Path to Compliance
As 2023 rolls on, the importance of secure cyberspace has never been higher. Companies are now willing to invest in top-of-the-line cyber security frameworks to protect their data and customer information from malicious intrusions.
We’ve explored various aspects of cyber security frameworks in this blog post and laid out some key points that can help shape your understanding of them. Looking at all entities, be it government organizations or private enterprises; they are all taking steps to enhance their infrastructure and reduce their attack surface area.
For easier ways to handle compliance requirements, contact Sprinto—our automated platform that will do the work for you! With a few clicks, you can quickly deploy better cyber security practices and ensure you don’t leave your systems vulnerable to potential cyber threats. Speak to our experts today.
FAQs
Which cyber security framework is the best?
When it comes to cybersecurity, few frameworks compare to the widely-recognized ISO/IEC 27001 and 27002. Affectionately dubbed ‘ISO 270K’, this framework is an international benchmark for safeguarding information security both internally and externally with third parties.
Is ISO 27001 a cyber security framework?
Absolutely! This international Standard is the gold standard for information security management systems. By following its principles of confidentiality, integrity, and availability you can effectively safeguard your data from potential threats.
What are the 6 Ds of cyber security?
The 6 D’s of cyber security to bolster your digital defense strategy — Deter, Detect, Defend, Deflect, Document and Delay. With these measures in place you can ensure top tier protection from malicious forces on the web.
Meeba Gracy
Meeba, an ISC2-certified cybersecurity specialist, passionately decodes and delivers impactful content on compliance and complex digital security matters. Adept at transforming intricate concepts into accessible insights, she’s committed to enlightening readers. Off the clock, she can be found with her nose in the latest thriller novel or exploring new haunts in the city.
Grow fearless, evolve into a top 1% CISO
Strategy, tools, and tactics to help you become a better security leader
Found this interesting?
Share it with your friends
Get a wingman for
your next audit.
Schedule a personalized demo and scale business

Sprinto: Your growth superpower
Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.


