For every lock, there is someone out there trying to pick it and break in. – David Bernstein.
We check our home’s lock twice before leaving. Do you ensure the same thing in maintaining your customer data? Yes, we are talking about the PCI penetration testing.
Organizations that store, process, and handle credit cards and payment information need to be PCI DSS (Payment Card Industry Data Security Standards) compliant.
To become PCI DSS compliant, you need to meet many technical requirements, like penetration testing. What is it, who needs to perform it, and how is it done? Let’s get into it.
TLDR
A PCI pen test is typically conducted by a qualified third-party security expert or a certified internal security assessor with expertise in penetration testing.
The steps include scoping the environment, identifying vulnerabilities, exploiting weaknesses, analyzing findings, and reporting results to help remediate identified risks.
A PCI pen test actively exploits vulnerabilities to assess risks, while vulnerability scanning identifies potential weaknesses without exploiting them.
What is PCI Penetration Testing
A PCI penetration testing is the process of evaluating and identifying vulnerabilities and threats in the systems that process and store cardholder information. The card holder environment (CDE) perimeter may include applications, third party services, IP addresses, and networks.
PCI pen testing aims to mimic the attackers’ activity in the CDE and identify and exploit the vulnerabilities that give unauthorized access to the cybercriminals into the system.
Why is PCI Penetration Testing Important?
Credit card fraud is one of the most prevalent issues affecting millions of cardholders across the globe. When dealing with cardholder data, having a protective card environment should be at the top of the list considering security.
Within the PCI DSS requirements, 11.3.1 and 11.3.2, you are required to perform penetration testing at least once annually or after any significant changes in your systems (segmentation controls) to avoid problems such as
- Non-compliance penalties
- Data breaches
- Financial and reputational damage
PCI pen tests help you identify your security gaps and vulnerabilities and enable you to act on them before bad actors and hackers exploit them. This is why it is crucial to perform regular pen tests from both security and compliance points of view.
Who Needs To Perform a PCI Penetration Test
As per the PCI DSS 11.3 requirements, the PCI Council specifies that a penetration test needs to be performed by a qualified internal resource or third-party professional. Also, the tester needs to be independent of the systems on which penetration tests will be performed. This means that they should not be involved in the setup, support, and management of the CDE systems.
There are guidelines specified for assessing the past experience of the pen tester. Below are some certifications mentioned in the guideline which may validate that professionals are qualified.
- Offensive Security Certified Professional (OSCP)
- Offensive Security Certified Expert (OSCE)
- Certified Ethical Hacker (CEH) – EC Council
- GIAC Exploit Research and Advanced Penetration Tester (GXPN)
- GIAC Certified Penetration Tester (GPEN)
- GIAC Web Application Penetration Tester (GWAPT)
- CREST Registered Penetration Tester
It is important to note that certifications alone are not enough and you need to follow other guidelines as well like looking at past experiences, projects, tests performed, and more while choosing the pen tester.
Also check out details on Penetration Testing for PCI DSS 4.0
How to perform PCI Penetration Testing?
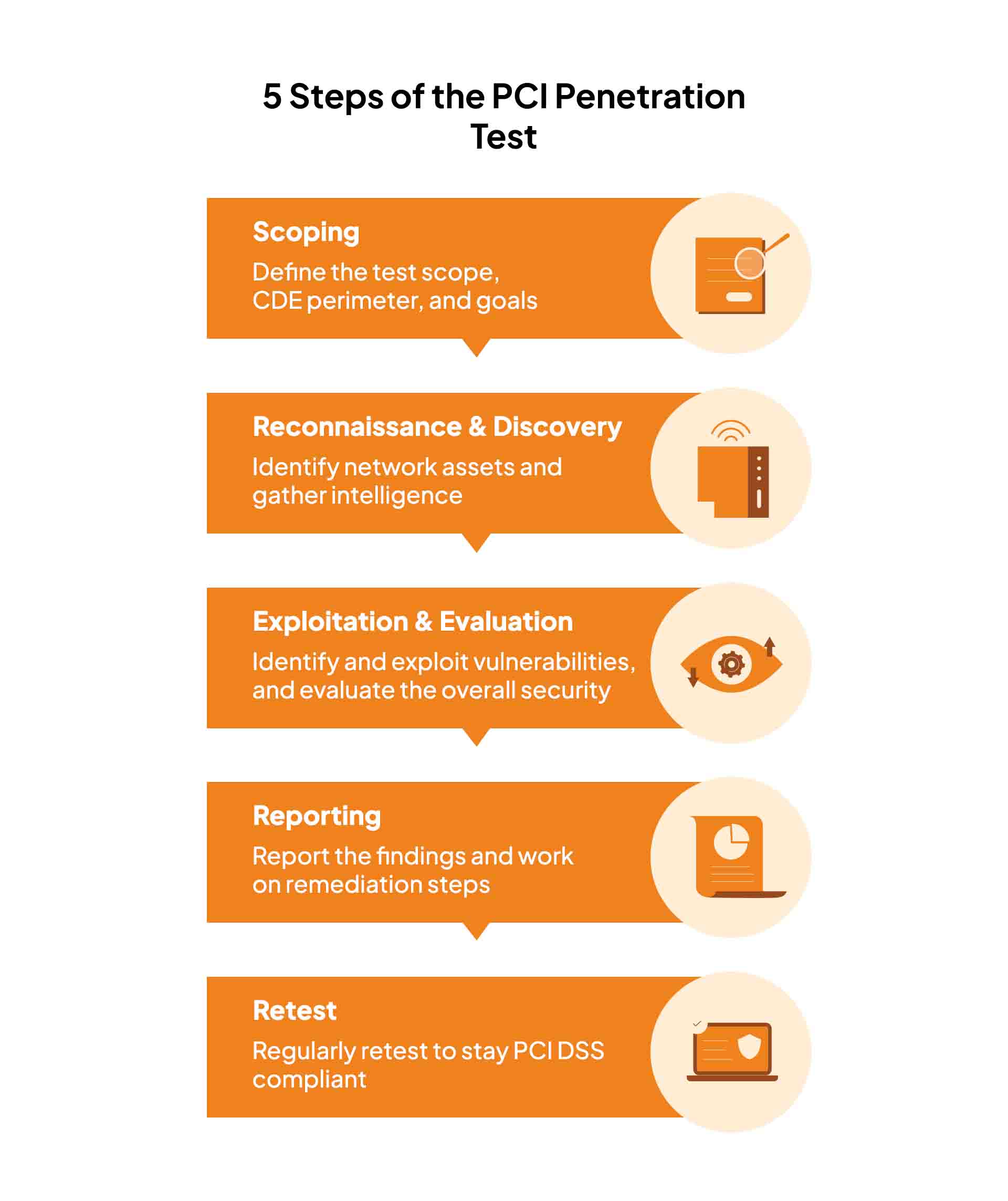
A PCI DSS penetration test consists of 5 steps, each broken into three phases: pre-engagement, which involves the planning of scoping and information gathering; engagement, the evaluation process; and post-engagement, which involves reporting and retesting. Let us briefly elaborate on each step below.
1. Scoping
Before getting into the pen test, the scope (including details on objectives, assets, or environments that need to be tested) and the required approvals, are determined using PCI DSS requirements. This includes the entire CDE perimeter (both external and internal).
Any critical systems in the organization, like network connections, access points, and applications/servers that store, process, and transmit cardholder data come under the scope. All systems not connected with the CDE are considered out of scope for PCI penetration testing.
2. Reconnaissance & Discovery
Once the scope is defined, the pen tester will identify your network assets within the specified scope of the CDE. During this step, they try to gather information on the target through various reconnaissance techniques.
Also, the tester will identify all the hosts in the target network and their services. This can be done using various techniques, such as banner grabbing, port scanning, and social engineering.
3. Exploitation & Evaluation
Using the scope and discovery, the penetration testing team now evaluates all your systems and applications for entry points and vulnerabilities. This is generally done using manual techniques and automated tools.
The pen tester tries to exploit the identified vulnerabilities to gain access to the organization’s systems and cardholder data. Furthermore, they try to explore the CDE to identify additional attack vectors and evaluate the overall security parameters.
4. Reporting
After the evaluation, the pen testing team compiles a detailed report of the penetration testing methodology, the vulnerabilities discovered, the severity of each vulnerability, and the recommended remediation steps.
Generally, a clear flow of the penetration testing steps to provide evidence is also mentioned in the report for the stakeholders. Based on the report, the relevant team addresses the identified vulnerabilities and implements the recommended remediation steps.
5. Retest
In the final phase, the company tests its systems again to ensure that it appropriately addresses the identified vulnerabilities and complies with the PCI DSS.
The pen test process is repeated regularly or whenever there is a change in your network or system infrastructure. This ensures that your previous pen testing efforts were effective and maintained the security of CDE in place.
Before we get to the top PCI penetration testing tools, let’s look at the difference between PCI pen testing and vulnerability scanning.
We have a free resource for you if you want to check how risk assessment approach works:
Download Your PCI DSS Risk Assessment Report
Difference Between PCI Penetration Testing and Vulnerability Scanning
Vulnerability scanning utilizes software applications for testing and identifying vulnerabilities in your network and applications. The scanner looks for known vulnerabilities in your software and reports those that need to be fixed.
While PCI penetration testing simulates an attack by hackers and identifies vulnerabilities in your network and applications. A pen tester uses manual and automated tools to identify and exploit vulnerabilities. Unlike vulnerability scanners, it also tests the security control of the organization, policies, and procedures with a comprehensive report.
To sum up, both penetration testing and vulnerability scanning are essential for PCI compliance, and they have certain similarities. But penetration testing proves to be more efficient as it follows a more comprehensive approach to the organization’s security posture, while vulnerability scanning is targeted for testing specific vulnerabilities.
How does a PCI penetration test differ from a regular penetration test?
While both aim to identify vulnerabilities, a PCI penetration testing differs from a regular pen test in terms of audit requirements, scope, frequency, process, and objectives. Let’s break these down:
| PCI pen test | Regular pen test | |
| Objective | The PCI penetration scope is a key differentiator with a regular pen test. A PCI pen test involves assessing the security posture and potential vulnerabilities in the cardholder data environment that includes the systems, applications, networks, and sensitive data. | Includes a broader scope; the test assesses the security weaknesses in the entire IT infrastructure encompassing networks, operating systems, and threats posed by humans. |
| Compliance process/ requirements | A PCI compliance test is not optional if your business processes cardholder data. The test result is required for passing audits. You can hire a penetration testing company or conduct it internally. | An internal or external penetration testing is not mandatory if PCI does not apply to your business. In such a case, it is merely a best practice that adds resilience to the security posture or improves brand reputation. |
| Risk remediation | If you find any exploitable vulnerabilities in the CDE, remediation actions are necessary to meet pass audits and ensure compliance with PCI DSS penetration testing requirements. A retest may be required to measure the effectiveness of the control measures. | There is no hard and fast penetration testing requirement to remediate risks. However, much like the compliance requirements, it is a good practice to have vulnerability mitigation and implementation measures to avoid breaches. |
| Consequence of non compliance | If a breach occurs due to non compliance, merchants can expect to pay anywhere between $5,000 to $100,000 as penalty while for larger businesses, the fine amount can even reach $1 million. | If you don’t conduct a pen test, a wide range of security threats can impede your key operations. While no authorities can impose penalties on your business, you pay in terms of loss of customer trust and to recover from the damages. |
| Frequency | PCI DSS requirements 11.3 mandates pen testing at least once a quarter or once every 90 days depending on your card vendor and number of transactions. | A regular internal penetration testing does not fall within the scope of mandatory regulations, and therefore has no hard and fast rules on the frequency. |
PCI penetration testing costs anywhere between $10,000 to over $100,000, depending on the complexity of your environment and number of transactions. When you partner with an end-to-end PCI compliance solution provider like Sprinto, you not only automate the complete process from start to certification but pen test tools are included in the bundle, significantly reducing your overall expense. Get a demo now.
Tools to Perform PCI Pen Test
Let us look at the top three tools that will help you perform PCI penetration testing to become PCI compliant.
Acunetix
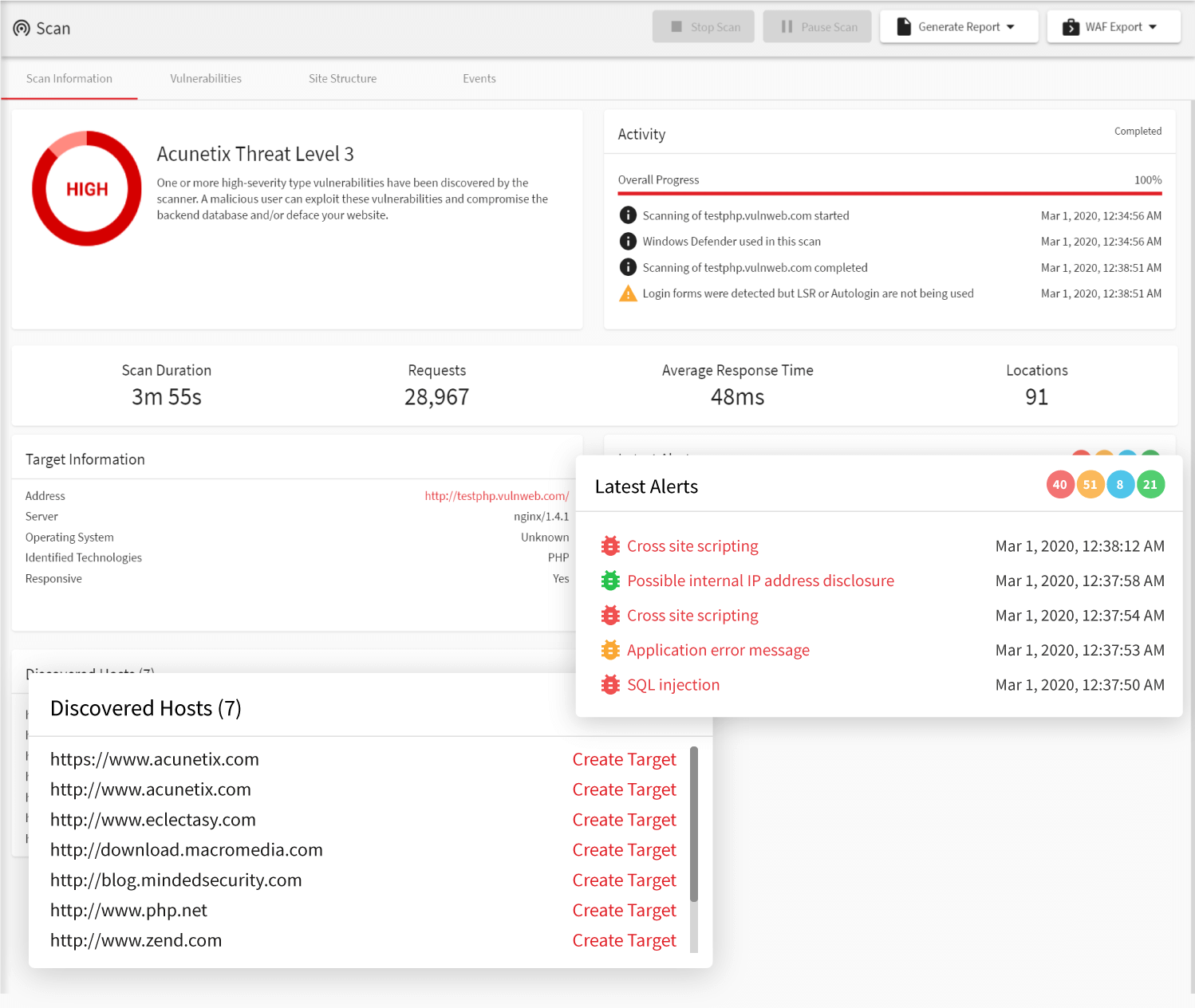
Acunetix is a powerful web vulnerability scanner and penetration testing tool that can perform checks automatically to identify over 4500+ vulnerabilities. The tool uses automated and manual testing techniques to identify security vulnerabilities. Acunetix is helpful for PCI penetration testing as it focuses on different website potential security risks such as SQL injection, cross-site scripting (XSS), and other web-based attacks.
Key Features
- Built-in PCI DSS vulnerability scanner
- Quick Scan and Full Scan options for regular penetration testing
- Team collaboration features for organized security management
- Seamless integration to connect with your existing cloud system
- Comprehensive reporting that highlights vulnerabilities and provides recommendations for remediation
Intruder
Intruder is a security testing tool that helps organizations identify and remediate potential security risks in their network infrastructure and web applications. The tool provides an easy-to-use interface that allows users to quickly and easily scan their assets for vulnerabilities. With manual testing features, testers can look for vulnerabilities that are not identified through Intruder’s automated scanning. It also has a separate PCI Compliance & Vulnerability Management module to meet the security requirements.
Key Features
- User-friendly dashboard to check PCI security controls
- Automated and manual penetration testing features
- Continuous scanning features to stay risk-free
- Integration with issue-tracking systems to efficiently manage risks
- Intelligent, audit-ready report generation
Nessus
Nessus is an industry-standard vulnerability assessment and penetration testing software that helps you automate PCI pen tests to look for basic and advanced vulnerabilities on both network and application levels. From software flaws and missing patches to malware and other vulnerabilities, Nessus identifies and reports different security issues to fix them.
As the tool covers different endpoints, servers, and virtualization platforms, pen testers often prefer it to perform PCI tests.
Key Features
- Comprehensive vulnerability scanning (both automated and manual)
- Extensive library of plugins to keep up with the latest threats and vulnerabilities
- Compliance monitoring mode to meet PCI requirements
- Integration with other security and pen testing tools
- Remediation guidance to fix severe security issues
Conclusion
That’s a wrap. Penetration testing is a necessity these days, not just from PCI DSS compliance point of view but also to ensure that your customers’ data is safe from cybercriminals. A single cyber attack can prove to be devastating to the organization’s reputation.
Compliance tools like Sprinto streamline PCI DSS penetration testing by automating key compliance tasks, such as tracking controls and monitoring for vulnerabilities in real time.
It helps you always stay audit-ready by providing continuous security checks, centralized management, and integrations with various systems. You can help track compliance progress and generate reports, reducing manual efforts during the pen test process and ensuring alignment with PCI DSS requirements.
The tool comes pre-built with vulnerability scanners and risk assessment systems to stay compliant without exceeding your budget.
In case you are wondering how to quickly secure your systems and strike all the requirements in the PCI checklist, feel free to talk to our PCI experts!
FAQs
1. Is penetration testing required for PCI?
Yes, penetration testing is required for companies that need to comply with PCI DSS as per PCI Requirement 11.3. You need to perform penetration tests regularly to protect customers’ sensitive data from cybercriminals.
2. When should PCI penetration testing be performed?
PCI penetration testing should be performed at least annually or after any significant changes to the network infrastructure, such as system upgrades, new applications, or configuration modifications. Regular testing ensures that any new vulnerabilities are identified and addressed, maintaining ongoing compliance with PCI DSS requirements..
3. How can I get PCI DSS compliant?
To get PCI DSS compliant, you need to first understand the 12 requirements of PCI security standards. Then, conduct risk and gap assessments, complete relevant questionnaires and perform penetration tests. For a detailed guide, click here.
4. Which tool best complies with PCI DSS Requirement 11?
Sprinto is the perfect PCI compliance automation solution that runs fully automated security checks and reports all the crucial security issues from a compliance point of view.
5. What are PCI internal and external network vulnerability scans?
The external network vulnerability scan looks for security threats in the company’s network perimeter or websites/apps through which cybercriminals could compromise the network. The internal scan looks for security issues and vulnerabilities inside the company’s network.
Gowsika
Gowsika is an avid reader and storyteller who untangles the knotty world of compliance and cybersecurity with a dash of charming wit! While she’s not decoding cryptic compliance jargon, she’s oceanside, melody in ears, pondering life’s big (and small) questions. Your guide through cyber jungles, with a serene soul and a sharp pen!
Explore more
research & insights curated to help you earn a seat at the table.
























