How to effectively plan your Cybersecurity budget for 2025?
Payal Wadhwa
Mar 26, 2025
Gartner predicts global information security spending will rise by 15% in 2025. According to Forrester, 2025 will be the year of CISO fiscal accountability, with organizations worldwide expanding their budgets and demanding justification for past investments. As AI, ML, and quantum computing make waves this year, businesses are also under pressure to balance risk management, innovation, and efficiency. Cybersecurity budgets are the key focus not only to enhance security but also to maximize business outcomes.
If you are a seasoned professional working on your 2025 cybersecurity budget and identifying key investment areas to stay ahead, this blog is for you.
| Allocate cybersecurity funds strategically across software, hardware, services, personnel, training, compliance, cyber insurance, incident response, and contingency planning for comprehensive protection |
| Base your budget on current state and security priorities and categorize funds across key components before presenting it to the board |
| Optimize your existing budgets by taking a risk-based approach, reducing tool sprawl, retiring legacy tools, using automation, and continuously monitoring and adjusting your budgets |
Why is allocating a cybersecurity budget crucial for organizations?
Allocating a cybersecurity budget is crucial for organizations to keep their businesses up and running when threats strike and to ensure risk reduction. 60% of small businesses shut down within six months of a cyberattack, and it’s not just the breach that hurts—it’s the aftermath. Recovery costs, fines, and legal penalties can shake a company’s finances, sometimes beyond repair.
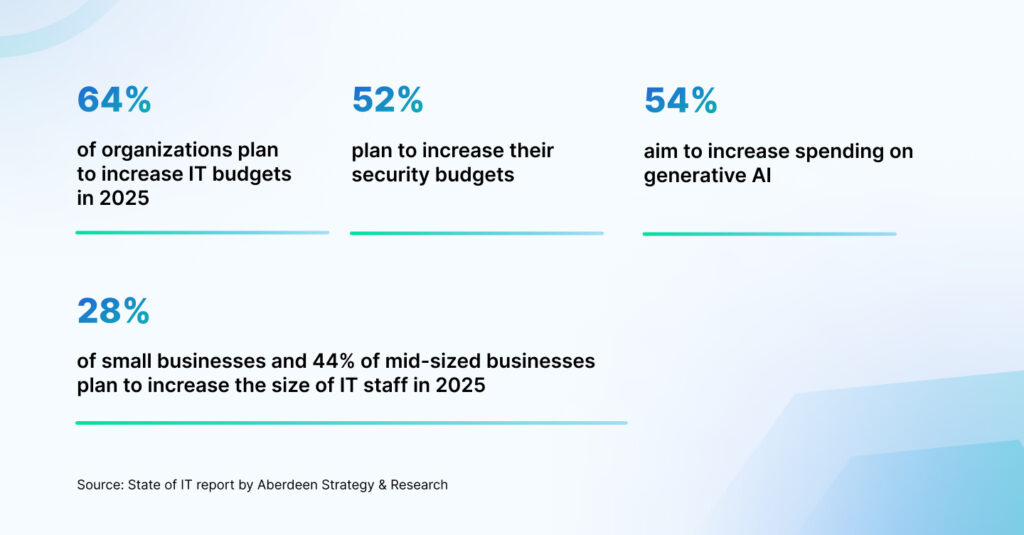
As cybercriminals get creative with their attacks, the defenses must evolve, too. The increased adoption of AI technologies and growing cloud complexities need preparation. A dedicated cybersecurity budget helps businesses stay ahead of uncertainties and ensures that the investments make a difference to the overall security stance. In 2020, organizations dedicated an average of 13% of the IT budget to cybersecurity. This number has gone up to 20%, and for good reason. In fact 64% of businesses are planning to increase IT budgets in 2025 while 52% are aiming to increase their security budgets. It reflects the growing recognition that cybersecurity protects systems, builds resilience, and enhances customer confidence by demonstrating your commitment to data protection.
What are the key components of a cybersecurity budget?
In 2025, software, hardware, services, personnel, and training will take up the major share of cybersecurity budgets for most organizations, but there are other crucial areas, too.
Here’s a list of key cybersecurity budget components:
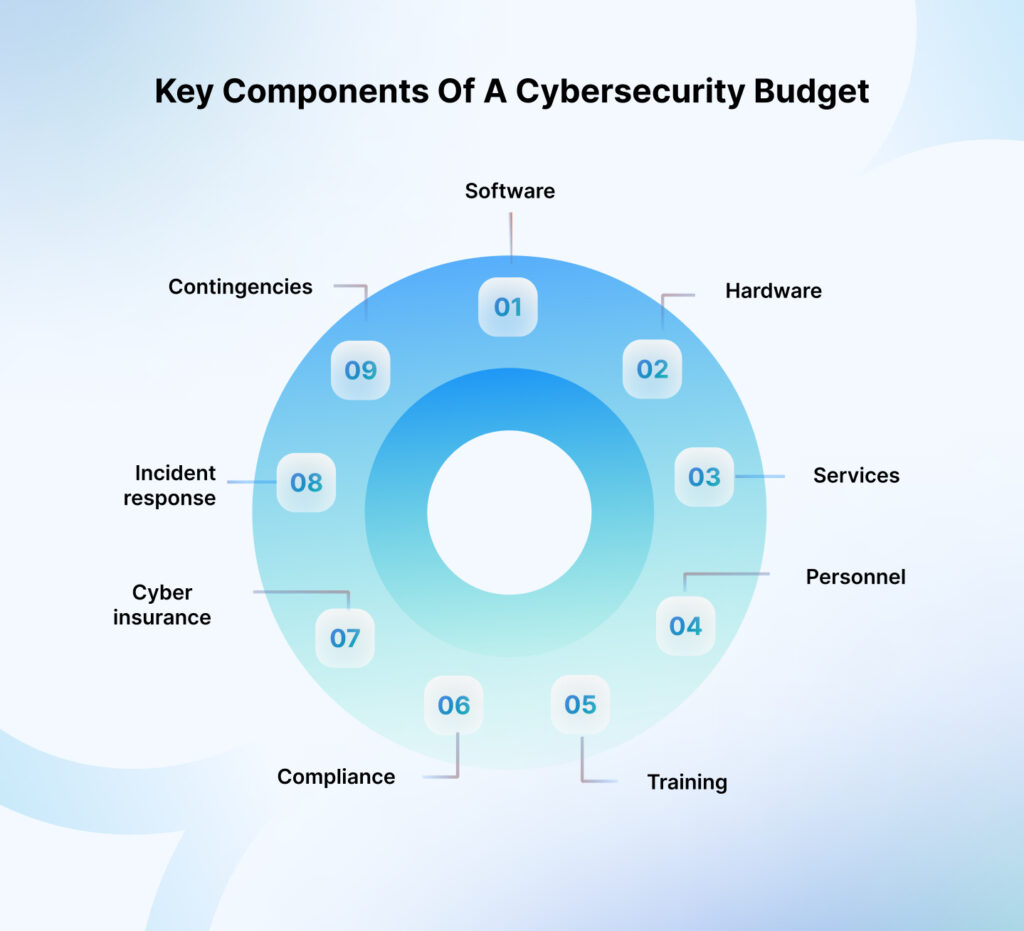
Software
Investing in security software creates the foundation for cybersecurity defense and includes various tools and technologies such as:
- Firewalls, antivirus, intrusion detection systems, and endpoint protection systems
- Identity and Access Management tools
- Cloud security solutions such as CASB (Cloud Access Security Broker)
Hardware
Organizations with on-premise setups require hardware investments to protect critical assets. These investments include:
- Keeping routers, servers, and workstations up-to-date
- Multi-factor Authentication Hardware, such as smart cards and security tokens
- Secure storage for backups
Services
Many organizations outsource some expertise for comprehensive and continuous protection, and these services are an essential component of the cybersecurity budget. Examples include:
- Managed Security Service Providers (MSSPs)
- Vulnerability scans and penetration testing
- Third-party risk assessments or audits
Personnel
Personnel costs take a significant share of the budget as these involve hiring skilled professionals to build a dedicated cybersecurity team. The costs include:
- Hiring and retaining top talent, including CISOs, security analysts or security engineers
- Security Operations Center (SOC) staffing
- Freelancer costs
Training
Training budgets are non-negotiable to build a security-conscious workforce and help employees identify and mitigate cyber threats. The cost components include:
- Security awareness programs such as phishing simulations, password strategy, etc
- Compliance training
- Role-based training sessions for IT teams
Compliance
If the organization is subject to regulatory frameworks, the organization must also budget for compliance. The expenses include:
- Compliance assessment costs
- Audit preparation and legal fees
- Certification costs
Cyber insurance
Cyber insurance helps reduce the financial burden in case of an event or disruption and should be a part of budget planning. The costs include:
- Coverage for data breaches and ransomware attacks
- Financial protection for losses due to cyber incidents
Incident response
The cybersecurity budget must account for creating a solid incident response plan to prepare for and mitigate cyber incidents. These costs cover:
- Developing and testing incident response plan
- Public relations effort costs
- Forensics costs
- Backup and recovery solutions
Contingencies
A contingency fund is necessary to help you respond to emergency situations without panicking about the finances. It includes:
- Funds for unexpected threats and disruptions
- Responding to zero-day vulnerabilities
- Geopolitical tensions and other contingencies
Save big on security and compliance with Sprinto
New considerations for 2025 budgeting
While the components above are standard in most security budgets, let’s discuss specific priorities that should be on the list for 2025:
Supply chain security
As software supply chain attacks rise, CI/CD pipelines must be secured, and well-assessed vendors must be onboarded. Set aside budgets for third-party risk assessments, continuous monitoring tools, open-source software scanning tools, automated patch management, and other enhancements to mitigate cyber risks from third-party dependencies.
Zero-trust Architecture implementation
NIST strongly recommends Zero Trust Architecture, which should be a key part of your cybersecurity strategy in 2025 and receive a significant share of budget allocations. Zero Trust thrives on continuous verification and the elimination of implicit trust. The key investments in this area include micro-segmentation to isolate sensitive systems, passwordless authentication, and secure remote access.
AI-driven threat detection
AI is increasingly becoming a key tool for cybercriminals, with many leveraging it for ransomware and other attacks. In 2025, forward-looking companies must invest in AI-powered threat detection and machine learning models to enable proactive threat response and reduce manual workload.
IoT and IoMT security
As the usage of IoT (Internet of Things) and IoMT (Internet of Medical Things) rapidly increases, the attack surface is expanding, making them a prime target for threats and attacks. Security researchers have revealed a surge of 400% in malware attacks on IoT devices, indicating that these are an easy entry point for hackers.
Similarly, the healthcare industry must prioritize the security of IoMT devices to protect sensitive data and ensure patient safety. Key investments in this area can include network segmentation for IoT devices, device discovery and risk assessment, secure access controls, and behavioral monitoring.
Post-quantum cryptography
2025 is the year of quantum computing, and quantum computer advancements will start breaking traditional cryptographic algorithms. For long-term security and compliance, organizations must begin preparing now and invest in the groundwork for post-quantum cryptography or PQC. NIST has finalized some quantum-resistant algorithms, and regulatory bodies are expected to mandate PQC adoption soon. Start investing in PQC-ready hardware and software and train the workforce for what’s coming next.
Steps to create an effective cybersecurity budget
When creating a cybersecurity budget, it is crucial to understand your current and desired state and then begin the groundwork. The budgeting process demands thorough research on risk areas and investment costs. You must then strategically present the budget to the board for approval.
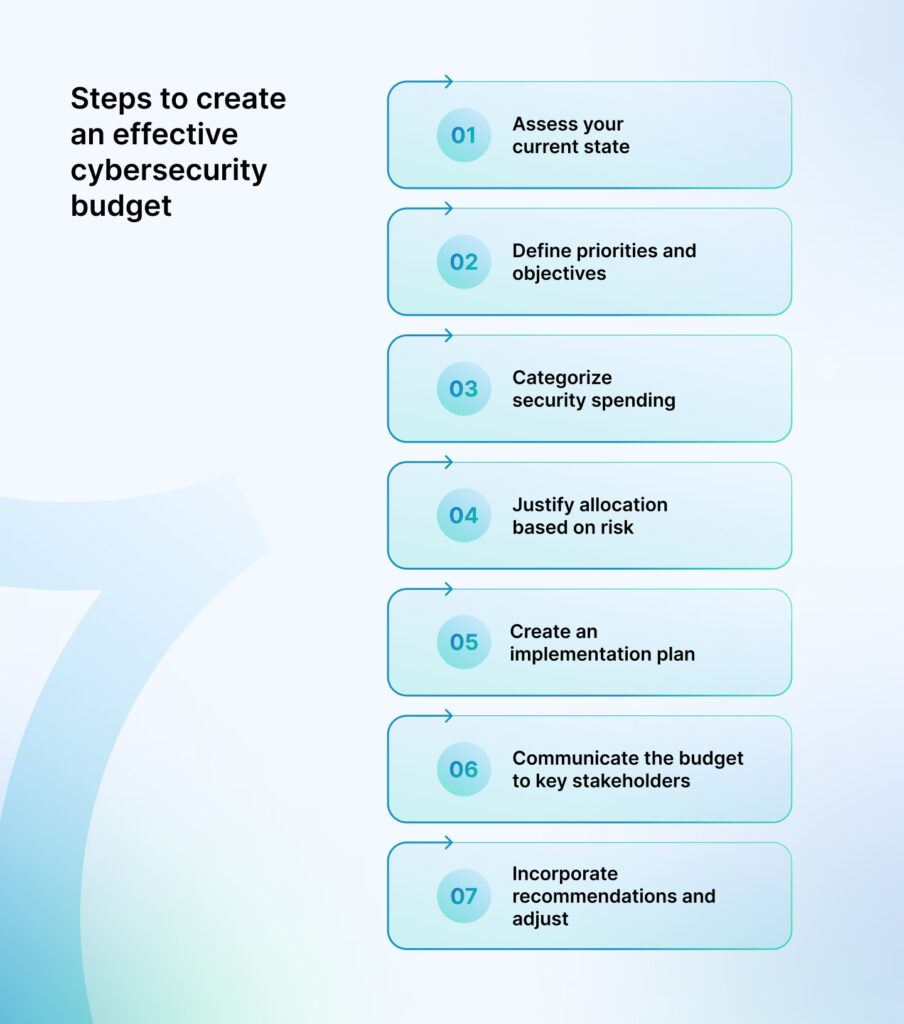
Here are the steps to create an effective cybersecurity budget:
Assess your current state
Start by assessing your current state and thoroughly auditing existing policies, procedures, security tools, and past security incidents. Conduct vulnerability scans to identify weaknesses and gaps in the workforce, compliance controls, and other areas. This will require involving key stakeholders from cross-functional departments and using risk assessments, interviews, observation, and feedback methods.
Define priorities and objectives
Once you have clarity on the existing security maturity, align cybersecurity priorities with business goals to decide budgeting objectives. These include improving cloud security, enhancing incident response times, compliance with applicable frameworks, and strengthening access controls. Also, knowledge from threat intelligence feeds, industry predictions, and trends can be used to allocate funds for AI, ML, and other new technological enhancements.
Categorize security spending
As the next step, break down the budget into key categories for better structure and easy expense tracking. These will include technology, personnel, training, incident management, compliance, contingency funds, and insurance. The best practice is to research the costs of tools, compare vendors, and give the nearest estimate.
Here’s an example:
| Category | Expense description | Estimate |
| Technology | Firewalls, endpoint protection, SIEM tools, encryption | $200000 |
| Personnel | Salaries for CISO, engineers, analysts, and managers | $500000 |
| Training | Security awareness training | $12500 |
| Compliance | GRC tools, audit prep, and certifications | $75000 |
| Incident response | Forensic tools, backups, incident response team | $100000 |
| Third-party services | VAPT scans | $50000 |
| Insurance | Coverage for unexpected incidents | $25000 |
| Contingency fund | Reserve for unplanned events | $25000 |
Justify allocation based on risk
It is equally important to clarify the rationale for why certain areas have more funds than others. Explain the risk reduction using quantifiable metrics, such as the cost of prevention versus the price of a breach or the number of hours saved using automation tools. Everything must be explained in non-technical language and translated into business impact.
Create an implementation plan
The cybersecurity budget should also include a roadmap for implementing initiatives with well-discussed timelines. Prioritizing projects based on urgency and organizational requirements and dividing them into milestones gives stakeholders more confidence and makes it easier for them to track progress.
Communicate the budget to key stakeholders
Present the budget to the board clearly, using examples and case studies to justify your points. Tie cybersecurity investments to business continuity and demonstrate how they can help unblock the sales cycle and win enterprise deals, increasing the chances of approval. Highlight areas where costs can be reduced, such as eliminating unnecessary or overlapping tools, while emphasizing the risks of underfunding cybersecurity. These strategies will help you secure leadership approval more quickly and effectively
Incorporate recommendations and adjust
Finally, use suggestions from the leadership and incorporate them into your budget for enhancements. Ensure that it is flexible, as cybersecurity is an ever-evolving space. Continuously monitor your spending and conduct yearly reviews to make any adjustments.
How to optimize the existing cybersecurity budget?
It’s not about spending more but better. Even limited budgets, when optimized well, can deliver the required results and help you move toward security maturity.
Check out how you can optimize your cybersecurity budget:
Transition to risk-based budgeting
While spreading the budget evenly across initiatives may sound fair, it’s not the best approach for organizational resilience. Prioritize spending on critical areas based on risk impact to maximize protection where it matters the most. For example, a healthcare organization will prioritize EHR (Electronic Health Records) security, IoMT device security, and protecting remote access systems over marketing websites and non-critical storage systems, which have less sensitive data and are low-risk areas.
Reduce Redundant tools
Another area that needs optimization is tool sprawl. Many organizations today deploy multiple tools with overlapping functionalities, leading to increased costs and inefficiencies.
According to Richard Watson, global and Asia-Pacific cybersecurity consulting leader at Ernst & Young Global Ltd, only 10%- 20% of cybersecurity technology is used, and security leaders want to buy more.
Organizations must audit the current security stack and use consolidated platforms with integrated capabilities to combat this. For example, tools like Sprinto save you from add-ons like continuous monitoring, MDMs, training platforms, risk assessment tools, and other security investments while enhancing integration.
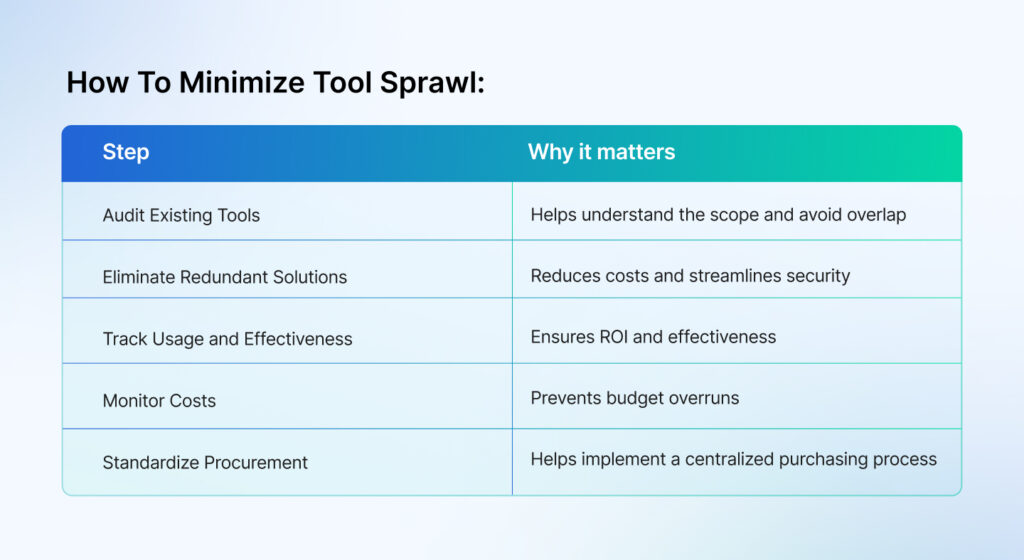
Automate wherever possible
Investing in automation tools with high ROI, such as Security Orchestration Automation and Response or SOAR tools, GRC tools, and cloud security posture management tools, can reduce workload and streamline operations to enhance efficiency. These can also minimize costly breaches, improve response times, offer comprehensive reports for well-informed decisions, and offer long-term benefits for the organization.
Monitor and adjust your spending
Reviewing your security spending and conducting a cost-benefit analysis for initiatives is equally crucial. Also, track KPIs and metrics such as incident response time, downtime reduction, policy adherence, and training completion rates to understand the return on investments. You can do this exercise quarterly and adjust the budgets to make it dynamic rather than fixed.
Retire legacy tools
Many organizations rely on legacy tools because of long-term vendor contracts, fear of switching costs, complexity, and resistance to change. But here’s the truth—these tools often require costly updates and struggle to protect against advanced threats. Gradually phasing out these tools and prioritizing upgrades based on risks is crucial to optimizing your cybersecurity budgets while moving towards enhanced protection.
Leverage next-gen GRC capabilities with Sprinto
How to avoid common mistakes in cybersecurity budgeting?
While there’s no one-size-fits-all template for cybersecurity budgeting, you can always learn to enhance yours by avoiding common mistakes.
Let’s discuss some of these mistakes and how you can avoid them:
View cybersecurity as a business enabler
Some organizations tend to treat cybersecurity as a cost center when it is, in fact, a business enabler. A mindset shift is crucial to align cybersecurity with business outcomes and maximize value. It helps you focus on risk reduction, compliance benefits, productivity gains, and better resilience in the long run.
Think about scalability
While cybersecurity budgets must be dynamic and revised often, the investments must not be made with a myopic vision. Instead of catering to short-term security needs, consider scalability and opt for solutions that can grow with you. An example could be investing in an on-premise solution with limited capacity instead of a cloud-based solution that scales as the business grows.
Don’t go for cheap alternatives always
When choosing tools, don’t consider cost alone, as it may lead to less comprehensive protection. The tool might lack some advanced features, may be less user-friendly, or may even require extra manual effort, which defeats the whole purpose of the tool in the long run. Look for customization, flexibility, feature capabilities, integrations, and vendor reviews before you make a selection.
Consider ongoing maintenance costs
Another common budgeting mistake is to consider only the upfront costs of purchasing security tools and not account for ongoing maintenance. These tools require regular patches and updates and continuous monitoring checks to ensure their effectiveness. Ignoring these expenses can increase risk exposure and eventually cost more than the maintenance expenditure.
Don’t underestimate threats to small business
Most SMBs think they are too insignificant to be the prime targets of cybersecurity threats and cut down on cybersecurity budgets. On the contrary, these businesses have weaker security controls and have easily accessible entry points for hackers. Setting aside a modest budget that is well-optimized is crucial to ensure business continuity and minimize the chances of costly breaches.
How does Sprinto fit into your cybersecurity budget?
Prioritizing security spending starts with knowing your requirements and risks, and execution flows smoothly when you invest in the right tools. Especially if you operate on limited budgets, consolidated tools like Sprinto offer a high ROI because they allow you to maintain strong cybersecurity defenses and a solid compliance posture while reducing overheads.
Sprinto does most of the heavy lifting for businesses by automating workflows, seamlessly integrating with tech stack for control monitoring and testing, and automatically collecting evidence. Features like built-in policy templates, training modules, role-based access controls, and automated vulnerability policing come at no extra cost and make it feasible to achieve the desired state without overspending. The comprehensive reports help you make data-driven decisions without technical jargon and provide real-time status of controls and readiness.
Ready to watch the platform in action? Take a tour and share your cybersecurity concerns with an expert today.
FAQs
What is a cybersecurity budget?
A cybersecurity budget allocates a proportion of the organization’s overall budget to protect digital systems and assets from threats and attacks. It covers expenses related to security tools, hiring, training, compliance, incident response, and contingencies.
How to justify cybersecurity budgets for approval?
To justify cybersecurity budgets for approval and secure leadership buy-in, security professionals must:
- Showcase current and potential threats to the organization using a risk assessment report
- Use non-technical language to explain how each investment helps minimize risk
- Demonstrate ROI by presenting KPIs and translating it into business impact
- Compare the organization’s spending to industry peers
- Present a clear plan of action
- Showcase efficiency gains
How can small businesses strengthen cybersecurity on limited budgets?
Small businesses can implement cost-effective measures to strengthen cybersecurity even when on budget. These include:
- Enforcing multi-factor authentication
- Using open-source or affordable tools with consolidated features
- Keeping systems updated
- Conducting regular employee training
- Leveraging managed services to outsource expertise


Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.





















