
HIPAA (Health Insurance Portability and Accountability Act) is a federal law that the U.S. passed in 1996 for the healthcare industry. Its main aim is to protect the privacy and security of a patient’s health information.
HIPAA has two main rules: the privacy rule and the security rule. The security rule enforces the privacy rule by stating that covered entities (hospitals and health institutions alike) should take technical and non-technical measures to protect the confidentiality, integrity, and availability of all ePHI.
Another rule, the Breach Notification Rule, urges HIPAA-covered entities to notify affected patients and other parties in case of a breach or attack.
What is considered a HIPAA violation?
A HIPAA violation refers to any instance of an organization failing to comply with HIPAA standards and rules. A HIPAA violation indicates that Protected Health Information (PHI) has been compromised, exposed, accessed by an unauthorized person, or mishandled, whether willfully or unintentionally.
The Office of Civil Rights (OCR) investigates HIPAA violations, and depending on the severity of the violation, there can be fines, penalties, and legal consequences.
To learn more about HIPAA violations, watch our video
Top 10 Examples of HIPAA Violations With Real Cases
Most HIPAA violations take place because employees working in hospitals or medical institutions aren’t aware of its rules and what breaks them. In fact, a 2021 survey says that 24% of employees were not trained in security awareness in the healthcare sector.
This can have serious consequences like huge financial losses and even imprisonment. Here’s the list of examples of HIPAA violations:

1. Healthcare employees divulging patient information
The privacy rule of HIPAA covers all kinds of patient information, whether written, oral, or electronic. It gives individuals the right to set limitations on who can look at their health information and requires consent to do so.
So, if anyone looks at, talks about, or shares patient information, they are committing a privacy breach of patient privacy. This is one of the most common violations of HIPAA committed by healthcare professionals and can also lead to potential jail time. The following case explains how.
Case 1: Snooping on Britney Spears’s medical information
In 2008, Britney Spears was admitted to the Los Angeles (UCLA) Medical Center where 13 employees were fired for looking at her medical records without consent. Apart from that, 6 physicians were also suspended.
After this happened, UCLA released a statement:
“All staff members are required to sign confidentiality agreements as a condition of their employment and complete extensive training on HIPAA-related privacy and security issues.”
2. Medical records falling into the wrong hands
Physicians and hospital employees may have to carry patients’ health information on their laptops, mobile devices, tablets, etc. It is unavoidable for daily operations, but is it safe? A very common HIPAA violation example is assets getting stolen and patient information getting disclosed to unwanted parties.
There is no liable insurance for theft, but there are ways to protect the information contained in these assets through encryption, password protection, multi-factor authentication, etc. Let’s understand this better with a case.
Case 2: Children’s Medical Center in Dallas suffered a loss of $3.2 million
There were several incidents of HIPAA violations in the Children’s Medical Center of Dallas as reported by Health Care IT News. In one of these incidents, there was a loss of 3,800 PHI data from a stolen Blackberry device that had no password protection or encryption.
The center had to pay the full fine because it mishandled patient information and continued to let employees use electronic devices without sufficient protection. This is one of the worst breaches in US healthcare history.
During the case, the Acting Director of OCR said
“Ensuring adequate security precautions to protect health information, including identifying any security risks and immediately correcting them, is essential.”
Save 80% of man hours spent on HIPAA
3. Sharing PHI using non-secure methods
According to HIPAA’s security rule, you must use or share patient information securely that upholds its privacy. Hackers and other unauthorized individuals can easily access information that is passed over any unsecured network.
Hence, sharing patients’ health information through texting, video conferencing applications, phone calls, personal emails, and common file-sharing services counts as a HIPAA violation. This can result in e-PHIs being readily available on the network for security breaches and attacks. Here’s a close case to this.
Case 3: Non-secure file-sharing exposed 11k patients’ information
Lanap & Dental Implants of Pennsylvania violated HIPAA rules by posting about 11,000 dental records on a torrent site for file sharing. These records were available online for four years. The data wasn’t encrypted, just obfuscated, which means anyone with basic technical skills could access it.
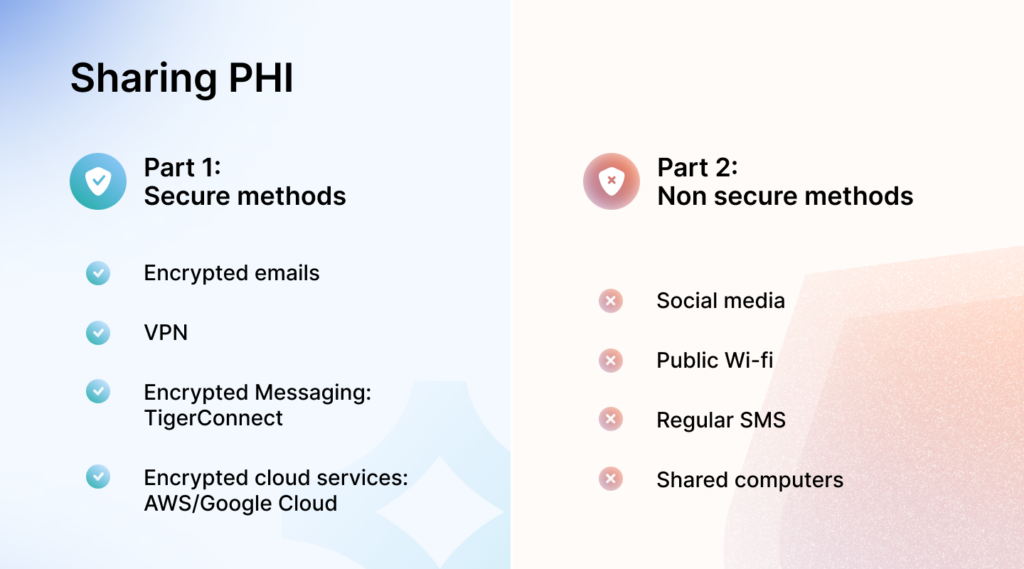
Know more about HIPAA-compliant text messaging applications.
4. Posting PHI on social media
Under no circumstances can healthcare facilities or other individuals post any health information about patients on social media, including online reviews, LinkedIn, rating platforms, etc. Even if the individual does not mention the patient’s name, this is not allowed and falls under unauthorized disclosure of PHI.
Melanie Fontes Rainer, Director of OCR (2023) explains:
“OCR continues to receive complaints about health care providers disclosing their patients’ protected health information on social media or the internet in response to negative reviews. Simply put, this is not allowed,”
Case 4: Health Center responded to a negative online review with PHI
Manasa Health Center is a psychiatric service provider in New Jersey. They had disclosed a patient’s protected health information in response to a negative online review.
Following an OCR investigation, it was found that Manasa Health Center violated HIPAA Privacy Rules by disclosing patient information and failing to implement proper policies. They paid $30,000 to settle the case with HHS and agreed to a corrective action plan.
5. Accessing patient files without authorization
Under HIPAA, no one has the right to access health records without patient authorization or under false pretenses. Even if the information is not used for any wrong reasons, stolen, or sold, it cannot be accessed. This holds true for doctors or healthcare staff, too.
Individuals must remember that written consent is required to access PHIs, and without it, access will be regarded as a HIPAA violation. Let’s look at an example that highlights this.
Case 5: Doctor H suffered prison time for unauthorized access
Dr. H immigrated to the States from China, did some research in the country, and had access to patient records. He was serving his notice period during the violation and accessed personal health records in the state healthcare system during his free time as he was curious about colleagues, celebrities private lives.
He was unaware of the rules of HIPAA at the time and did not know he couldn’t access health records without proper authorization. However, he didn’t use any information for personal gain or share it with anybody. After his termination, he was charged with HIPAA and had suffered four months of jail time with a $2000 fine.
6. Using weak third-party technology
A large number of healthcare providers use third-party tracking applications to collect user data and track their online activities. The company later uses this information to provide a better patient experience.
However, if the third-party applications used in this scenario are not secure enough, it can lead to identity theft, user harassment, stalking, and even data leaks containing patient activity. Here’s a similar case.
Case 6: Hospital websites sent patient data to Facebook
The Markup found that 33 of Newsweek’s top 100 hospitals in America used a tracker called Meta Pixel, which sent Facebook data whenever someone clicked to schedule a doctor’s appointment.
This tracking tool collected sensitive, identifiable health information, including details about medical conditions, prescriptions, and appointments labeled with IP addresses, and shared it with Facebook.
David Holtzman, a health privacy consultant and former senior privacy adviser at HHS, said on this “I cannot say [sharing this data] is for certain a HIPAA violation. It is quite likely a HIPAA violation.”
Keep in mind:
The IP address is one of the 18 identifiers of PHI under HIPAA. Learn about the 18 identifiers of HIPAA.
7. Delaying breach notification
The HIPAA Breach Notification rule clearly says that all affected parties should be notified about a breach without delay and within 60 days of discovering any incident.
The covered entities should provide them details like the type of information leaked, protective measures taken, and contact information. Failing to do so qualifies as a HIPAA violation and can incur substantial fines. Below is a similar example.
Case 7: OSU-CHS paid $875,000 for failing to provide notification
On January 5, 2018, Oklahoma State University—Center for Health Sciences (OSU-CHS) reported a HIPAA breach in which a hacker accessed a web server containing the ePHI of 279,865 individuals.
The breach was initially reported to have occurred on November 7, 2017. However, under investigation, it was revealed that it began on March 9, 2016. This was marked as a HIPAA violation for delayed notification of affected individuals and HHS, among other violations.
As a result, OSU-CHS had to settle with the HHS by paying $875,000 and including a strong corrective action while being monitored for two years.
8. Absence of risk management
A powerful risk management process is necessary for healthcare organizations. If you do not conduct thorough, regular risk assessments and internal audits of your access controls and processes, you’ll never know where your vulnerabilities lie, which creates an open field for attackers.
Under HIPAA’s security rule, all covered entities are required to conduct an organization-wide risk analysis. As stated in the HHS website, the process requires you to:
- Assess potential risks to e-PHI;
- Implement suitable security measures to mitigate identified risks;
- Document the security measures and their justifications; and
- Ensure continuous, adequate security protections.
What are the consequences of not having a HIPAA risk management plan? The next case.
Case 8: DHH paid $1.7 Million for not managing their security risks
The Alaska Department of Health and Social Services (DHSS) faced several HIPAA violations from the U.S. government in 2012 for risk management failures. As a result, they had to settle the dispute by paying a $1.7 million fine.
During the investigation, OCR discovered that DHSS lacked proper policies and security protocols to protect patient’s health information. Among other things, the main issue was that they had not done a risk analysis or put enough measures in place to manage risks.

9. Not having an incident response plan
The HIPAA security rule requires you to respond with reasonable steps to fix issues or stop a violation if they feel their e-PHI is compromised in any way during an incident. They must promptly address any security measures lapses to ensure patient information is protected.
Imagine facing a data breach without a clear plan. Panic sets in, response times are slow, and the breach could spread further, affecting more patients and potentially leading to legal trouble.
An effective incident response plan ensures timely notification of the breach while enabling measures to minimize its damages.
Case 9: UMMC failed to respond to breaches & paid $2.75 Million
The University of Mississippi Medical Center (UMMC) faced a $2.75 fine for a HIPAA breach involving unsecured ePHIs of approximately 10,000 individuals. The investigations discovered that they knew about risks since long but failed to address them until after the breach.
Furthermore, UMMC did not notify affected individuals whose ePHI was believed to have been accessed or disclosed, causing another violation.
10. Disposing of e-PHI improperly
“Even in our increasingly electronic world, it is critical that policies and procedures be in place for secure disposal of patient information, whether that information is in electronic form or on paper.”
– Director, OCR
When medical records of patients expire their retention date, or they are no longer required, medical institutions are supposed to remove them permanently and securely. By securely, we mean they should not be readable or accessible, regardless if they are digital or paper records.
For hard copies, methods like shredding or pulping may be used and for e-PHI, degaussing, physically destructing portable devices, or data wiping may be used.
Failing to do so may result in expensive violation fines like the ones discussed below.
Case 10: A small pharmacy paid $125,000
Cornell Prescription Pharmacy, a small pharmacy in Denver, settled with HHS for violations of the HIPAA Privacy Rule for improper disposal of PHI. They paid $125,000 as monetary penalties and agreed to adopt a corrective action plan to address deficiencies in their HIPAA compliance.
The Office for Civil Rights (OCR) found that Cornell failed to implement required written policies and procedures on the disposal of patient information. The investigation found documents containing the PHI of 1,610 patients disposed of unsecurely.
Ready to get HIPAA certified? Download our “How to Get HIPAA Certification – A Short 7-Step Checklist!” This easy-to-follow guide breaks down the process into seven simple steps, making your path to compliance straightforward and stress-free.
Download Your HIPAA Certification Checklist
Don’t become a HIPAA violation statistic, Choose Sprinto
By now, we know that not being compliant with HIPAA and violating its rules can have serious repercussions. In the examples and cases above, we have talked about financial penalties and jail terms, but severe reputational damage also happens.
So if you’re not yet compliant with HIPAA, you should seriously consider it your top priority. And if you are, then you should conduct a HIPAA risk assessment to understand your posture.
Remember:
Compliance shouldn’t get in the way of your business, it should keep up with it.
With Sprinto, you opt in not just to become HIPAA compliant but to stay compliant for the long run. The platform is built for compliance automation and continuously monitors everything: your risks, controls, assets, workflows, and more.
For examples, in the below image, you’ll find a comprehensive health summary of HIPAA framework with the number of controls implemented. It also shows you the individual status of the controls mapped according to various compliance activities.
Once you start executing all the checks, you’ll find that your HIPAA health trend grows. As such, Sprinto lets you get a real-time view of your security posture while staying compliant.
Frequently asked questions
1. What are HIPAA violation email examples?
The seven most high-impact HIPAA violation email examples would be:
- You share patient information without getting their consent.
- You don’t have a Business Associate Agreement (BAA) in place.
- Your BAA is incomplete and doesn’t meet all HIPAA requirements.
- You haven’t implemented necessary technical protections within your organization.
- You haven’t ensured that third parties have necessary technical protections.
- You share patient information without realizing it.
- You send emails containing patient information to someone other than the patient.
2. What are some penalties for violations of HIPAA rules?
Penalties for HIPAA violations include fines ranging from $100 to $50,000 per violation, with an annual maximum of $1.5 million for repeated violations. Depending on the severity and nature of the violation, criminal penalties can involve fines up to $250,000 and imprisonment for up to ten years.
3. How do organizations avoid HIPAA violations?
HIPAA violations can be avoided by providing sufficient HIPAA compliance training to employees in a healthcare entity. As long as everyone is aware of the PHI responsible for violations, they can be mitigated. Apart from this, having a proper risk management system should be a priority for healthcare operations to avoid further financial penalties.
4. What is the cost of being HIPAA compliant?
For small companies, the cost of being HIPAA compliant can be around $15,000 to $50,000 and for large companies, it is the cost is up to $200,000. The cost depends on the organization’s type, size, amount of data, employee training, current compliance posture, and the state of IT infrastructure.
5. Does HIPAA fall under civil violations?
Yes, HIPAA falls under civil violations. It can have civil penalties (authorized by the Office of Civil Rights) and criminal violation penalties (authorized by the Department of Justice).
6. Do healthcare insurance companies need HIPAA?
Yes, a healthcare insurance company must comply with HIPAA as they fall under covered entities, as stated by the Department of Health and Human Services, U.S.
7. What are the HIPAA identifiers?
Common HIPAA identifiers are the patient’s phone number, email address, social security number, IP address, account number, and medical record number.
Pansy
Pansy is an ISC2 Certified in Cybersecurity content marketer with a background in Computer Science engineering. Lately, she has been exploring the world of marketing through the lens of GRC (Governance, risk & compliance) with Sprinto. When she’s not working, she’s either deeply engrossed in political fiction or honing her culinary skills. You may also find her sunbathing on a beach or hiking through a dense forest.
Related blogs
research & insights curated to help you earn a seat at the table.











![HIPAA Certification Cost [Updated 2024 + Free Checklist]](https://sprinto.com/wp-content/uploads/2024/04/HIPAA-Certification-Cost-Updated-2024-Free-Checklist-1024x675.jpg)











