Cybersecurity doesn’t just need more money; it needs better direction. Misaligned priorities cost more than tight budgets ever will.
Despite increased involvement from executives and boards, many cybersecurity teams still struggle to communicate risk in business terms. Misalignment persists between CISOs and CFOs, in terms of compliance and strategy, and between the reality of market threats and the budget decisions to defend against them.
We recently spoke with Alex Sharpe, GRC top voice and Business Resilience Council at Global Resilience Federation, to break down the key forces at play and explain why stakeholder alignment is now the most critical aspect of the regulatory landscape.
Understanding stakeholder alignment
Stakeholder alignment in cybersecurity means that all key parties, like IT, security teams, executives, board members, and founders, have a shared understanding of cybersecurity goals, risks, and priorities. This alignment helps drive coordinated decisions, secure necessary resources, and maintain a unified response to threats.
What causes misalignment between IT team members (aka cyber folks) and executives?
The misalignment mentioned here mostly revolves around the challenge that IT and security teams speak a different language as compared to board members and executives. Alex Sharpe, drew a clear picture of this:
“The cyber folks—the folks that have normally handled these cyber issues—have no idea about the other world. They don’t understand business concepts or business terms. They don’t understand risk management.
They have historically focused on investing in technical defenses, whereas now we have to look at not only defenses, but we have to look at the detection and the response phases. We also need to look at the people, the process, and the organizational defenses—not just technology.”
In essence, on the one hand, we have technical issues and quick fixes, and on the other, we have business defences and organizational strategy. The two have similar objectives but operate on different timelines, and often fail to connect, resulting in misaligned priorities and missed opportunities to manage risk effectively.
Where is the conflict happening? What are the focus points?
During our conversation with Alex, we discovered five focal points where the conflict happens around stakeholder alignment:
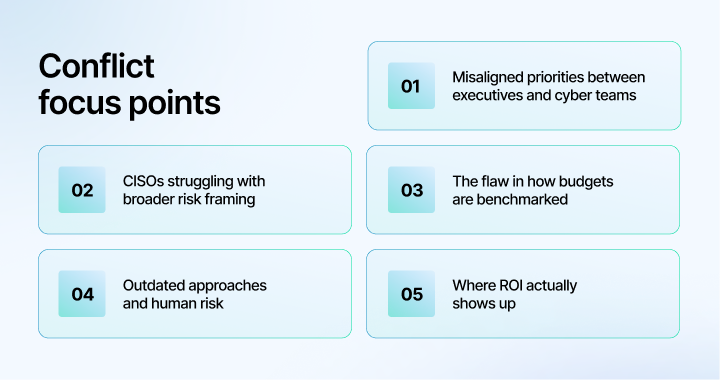
1. Misaligned priorities between executives and cyber teams
“Senior executives want to allocate the right amount of resources in the right areas to get the desired result. But, they are struggling to have that conversation with their own staff because the staff doesn’t understand the discipline. So we have two groups… that are just missing each other.”
2. CISOs struggling with broader risk framing
“The folks in the CISO organization, they’re good people. They’re struggling to learn these traditional GRC practices. And in some instances, they just don’t know what they don’t know.”
3. The flaw in how budgets are benchmarked
“The only metrics they have are, ‘How much is everybody else spending?’ Well, their budget went up by 15%, our budget should go up by 15%… That’s a great way to start. But over time, you gotta figure it out.”
4. Outdated approaches and human risk
“If you spent the past couple of decades buying products and implementing technical defenses and it’s worked. That’s what you’re going to continue to do. It’s human nature. Social engineering is purely leveraging human nature… You could do whatever you want with technology, but humans are not going to stop clicking anytime soon.”
5. Where ROI actually shows up
“Where you get the greatest bang for the buck in any of your security controls is going to be training and awareness of your staff. If you prevent one click that would have led to ransomware, you save millions of dollars.”
Compliance fatigue and regulatory confusion: The upper hand
Cyber folks and the senior leadership or board members have one priority in common: Regulatory compliance. However, the purpose of complying with regulatory standards may have different meanings for both parties.
More often than not, compliance is reduced to a check-box exercise, losing its strategic intent: to build trust, improve sector-wide cyber hygiene, and manage interconnected risks. Alex describes the importance of compliance as: “These regulations are not only a burden on us, but they give us confidence in the other players in the supply chain.”
When it comes to the regulatory landscape, who usually gets to call the shots?
“Boards and senior executives understand legislation, regulation, and compliance far better than the cyber folks do. They know how much trouble they can get in and the business impacts if they don’t comply.”
“Cyber folks really look at a checklist they have to march through. They don’t understand the compliance process. They don’t understand how to produce evidence. They don’t know how to run an audit.”
“I deal with people in finance every day, they know how to run an audit. I deal with people in cyber all the time, more often than not, they don’t.”
Misalignment = A storm ahead (Evolving threat landscapes)
The cost of stakeholders’ misalignment can manifest in different forms, like slow incident response, increased risk exposure, talent drain, inefficient spending, etc. A great example of this comes to light when organizations face external pressure but lack internal clarity. It becomes especially dangerous during periods of broader instability.
Let’s understand this better with a very relevant example.
External forces like market volatility and its cyber fallout on businesses
As Alex Sharpe warns, escalating tariffs and geopolitical tensions have historically led to spikes in cyberattacks, and today’s digital-first world only intensifies that trend. “As one country increases the tariffs, there’s also a force on the increase in cyber attacks. Now that the world is so much more digital. I would expect that trend to increase.”
And we have numbers to support this:
- 42% of mid-market firms delayed security upgrades due to tariffs (Marketsandmarkets)
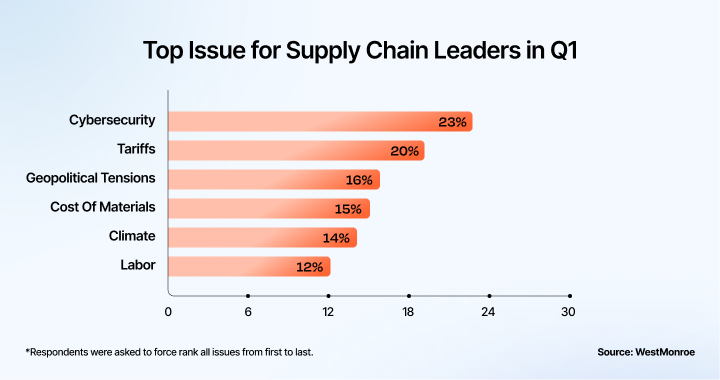
- 23% of manufacturing leaders cite cybersecurity as top supply chain concern (Q1 2025) (WestMonroe)
- Documented increase in nation-state cyberattacks during trade wars (Secureworld)
Add to that the growing perception of weakened U.S. cyber retaliation capabilities, and “we’ve really got a perfect storm forming,” where malicious actors feel emboldened to strike.
Companies are facing tighter margins, shrinking cyber budgets, and a talent pipeline that simply doesn’t match real-world needs.
“We are short-staffed somewhere between half a million and 1.5 million cyber positions, and the available cyber resources don’t fit the needs.”
Imagine such bad external actors, and your business ends up reacting instead of preparing due to stakeholder misalignment. This means missed signals, delayed responses, and wasted resources, leaving your organization not just vulnerable, but uncoordinated in the face of attack.
How do we move ahead?
Risk management investments are fundamentally about prevention. It’s hard to prove that something bad didn’t happen. “You can’t argue the counterfactual,” said Alex. So even when investments are working as intended, it’s not obvious how to tie them to outcomes the board and business care about.
One fix? Sharpe believes cyber needs to stop being treated as a standalone technical problem and start being treated like any other form of risk. This means businesses need to:
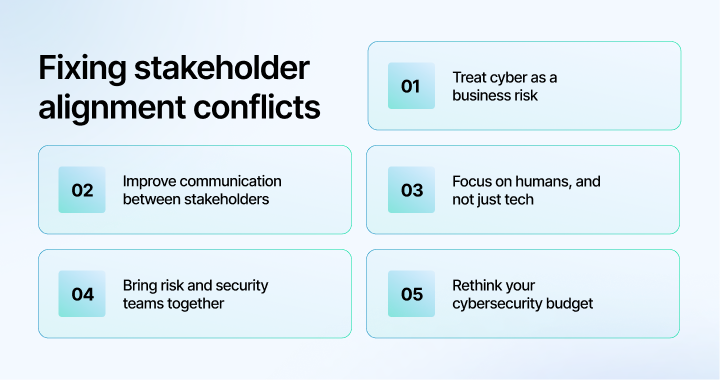
1. Treat cyber as a business risk: Cybersecurity needs to be integrated into a business’s overall strategy and enterprise risk management process. This would align cybersecurity with business value and priorities.
2. Improve communication between stakeholders: Cyber or IT teams need to translate technical controls into business outcomes. For example, MFA isn’t just a tech measure—it prevents invoice fraud.
3. Focus on humans, and not just tech: Businesses spend a lot on their tool stack and less on human resources, while cybercriminals mostly target people. Training and awareness are high-ROI investments. They’re simple and cost-effective but often overlooked.
4. Bring risk and security teams together: Risk managers usually have a better grasp of prioritization and resource alignment. They need to be integrated into cyber planning and budgeting.
5. Rethink your cybersecurity budget: Security budgets are often based on what others are spending. Instead, it should focus on your own risk profile and business priorities, along with desired outcomes, not just peer benchmarks.
In the end, we can conclude with the notion that a good cybersecurity posture is built on clarity, alignment, and accountability. You must stop chasing the latest tools and instead focus on defining risk appetite, aligning priorities across stakeholders, and holding leaders responsible for outcomes.
When cybersecurity becomes a strategic enabler, not merely an IT concern, businesses can make smarter decisions, spend more wisely, and build real resilience.

Pansy
Pansy is an ISC2 Certified in Cybersecurity content marketer with a background in Computer Science engineering. Lately, she has been exploring the world of marketing through the lens of GRC (Governance, risk & compliance) with Sprinto. When she’s not working, she’s either deeply engrossed in political fiction or honing her culinary skills. You may also find her sunbathing on a beach or hiking through a dense forest.
Explore more
research & insights curated to help you earn a seat at the table.






















