According to a study conducted in 2024, the global average cost of a data breach was $4.88 million, making a strong case for robust cybersecurity frameworks. The NIST Cybersecurity Framework (CSF) provides a systematic means of mitigating such risks by providing guidelines to help organizations protect their valuable assets.
While the NIST cybersecurity controls offer a robust cybersecurity foundation, businesses may not be sure where to begin, how its controls map to previous risk assessments, and what they need to do in real terms to enhance data and system integrity.
Moreover, the issue of compulsory compliance vs. voluntary adoption exists. This blog charts the cybersecurity strategy from a mandate to a working handbook for building a safer, better digital world.
TL;DR
| The NIST CSF, developed by the National Institute of Standards and Technology (NIST), whose mission is to enable U.S. innovation and competitiveness in industry, provides a voluntary yet systematic framework for cybersecurity risk management. |
| Effective deployment of the NIST CSF entails tailored application of its core functions, maturity tiers, and profile tailored to the organizational specifics, avoiding generic application for risk management and strategic alignment. |
| The typical error is to treat the NIST CSF as a static compliance checklist rather than a dynamic, risk-based methodology that must be continually tailored and adapted to an organization’s particular context and evolving threat environment. |
What are NIST Cybersecurity Framework Controls?
The NIST Cybersecurity Framework (CSF) is a voluntary collection of standards, guidelines, and best practices developed by the National Institute of Standards and Technology (NIST) to help organizations of all sizes and types manage and reduce cybersecurity risk.
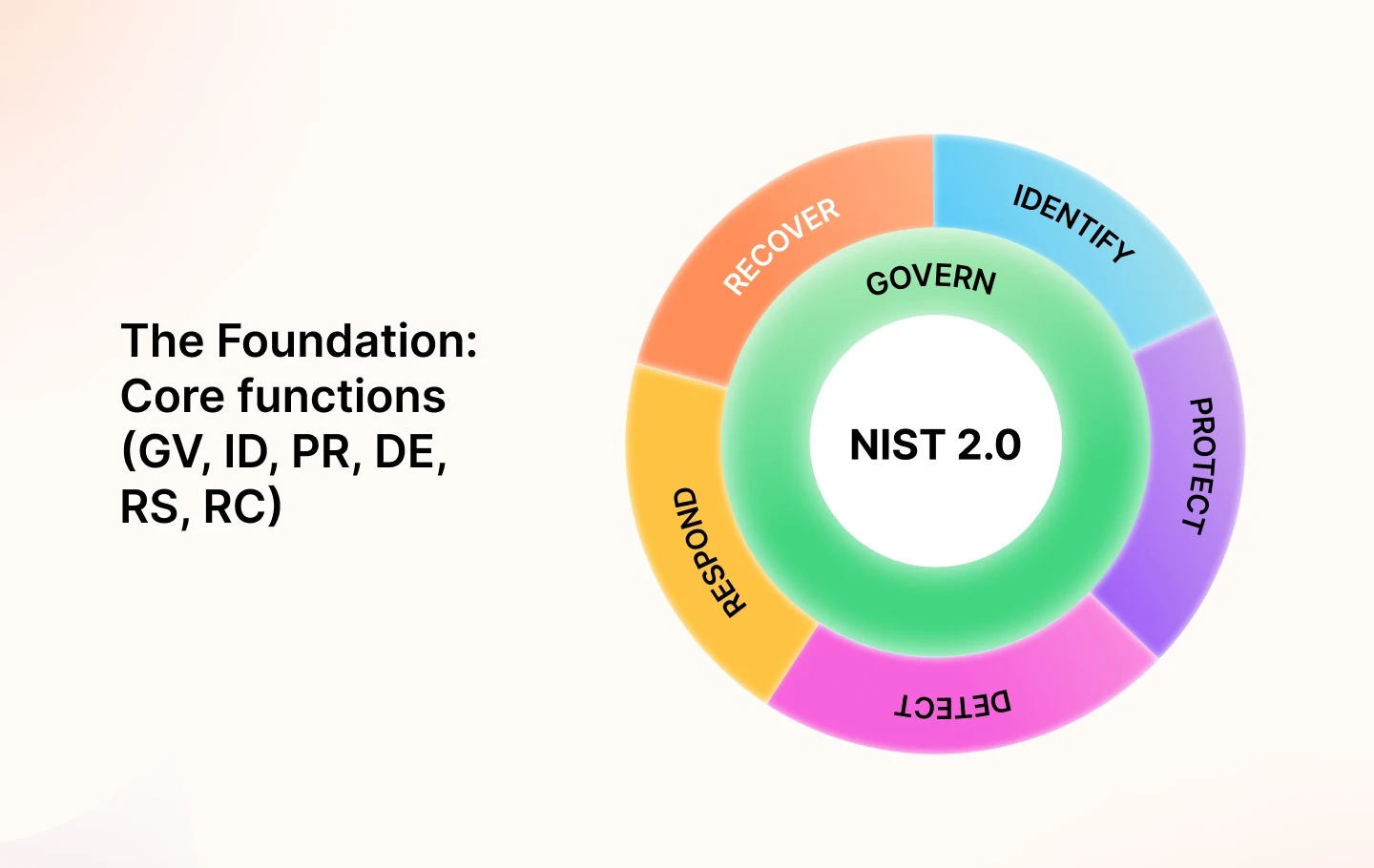
Initially, NIST cybersecurity controls were focused on critical infrastructure, but CSF 2.0 extends this to organizations. It takes a multi-layered cybersecurity architecture approach to six main functions: Govern, Identify, Protect, Detect, Respond, and Recover.
The framework offers a systematic approach to strengthening data protection, implementing cybersecurity within enterprise risk management, supply chain risk management, privacy, and IoT security, and conforming to global standards.
List of NIST CSF controls
When we talk about “NIST CSF controls,” it’s important to clarify that the NIST Cybersecurity Framework (CSF) does not provide a fixed list of prescriptive controls. Instead, it outlines a set of high-level functions, categories, and subcategories—essentially desired cybersecurity outcomes. These outcomes are designed to guide organizations in managing and reducing cybersecurity risk.
The CSF is organized around five core functions—Identify, Protect, Detect, Respond, and Recover—each broken down into 23 categories and 108 subcategories. If you’re looking for a control-level mapping, organizations typically use the CSF in combination with control catalogs like NIST 800-53 to derive specific actions.
From a security standpoint, NIST CSF is designed to help you manage risks and identify where your risks are. And as a business driver, if your clients are in the critical infrastructure space, all of them will have some requirements around the NIST standards.
Steve Siedeman, Director of Innovation, Prescient Security
Great advice adds up. Get more from the brightest minds in GRC — join now
Here is a summary of how the NIST CSF 2.0 organizes cybersecurity, a detailed explanation of the NIST CSF controls list, highlighting the relationship between functions, categories, subcategories, and where the controls are implemented:
The Foundation: Core functions (GV, ID, PR, DE, RS, RC)
The NIST Cybersecurity Framework (CSF) provides a good foundation for cybersecurity risk management. Its six core functions — Govern(GV), Identify(ID), Protect(PR), Detect(DE), Respond(RS), and Recover(RC)—manifest as actionable security processes.
| Function | Category | Subcategory |
| Govern (GV): Establishing Strategic Oversight Governance establishes the organization’s cybersecurity policies and aligns risk tolerance and strategy. Roles, policies, and compliance connect cybersecurity with enterprise risk management. | Organizational context: The organization knows the mission, stakeholder expectations, dependencies, and legal/contractual requirements that influence its cybersecurity risk management decisions. | GV.OC-01: Understanding the organizational mission and how it drives cybersecurity risk management GV.OC-02: Internal and external stakeholders’ knowledge and their expectations of cybersecurity GV.OC-03: Management of legal, regulatory, and contractual cybersecurity requirements (civil liberties and privacy included) GV.OC-04: Critical objectives, capabilities, and services on which external stakeholders depend and communicate GV.OC-05: Determining and describing the organization’s dependencies on external outcomes, capabilities, and services |
| Risk management strategy: The organization establishes, communicates, and uses its priorities, constraints, and risk appetite to guide operational risk decisions. | GV. RM-01: Establishing and agreeing to risk management objectives with stakeholders GV. RM-02: Establishing, communicating, and revising risk appetite and tolerance statements GV. RM-03: Aligning cybersecurity risk management activities and results with enterprise risk management processes GV. RM-04: Establishing and communicating a strategic direction for appropriate risk response options GV. RM-05: Establishing communication lines for cybersecurity risks across the organization, including third-party and supplier risks GV. RM-06: Standardizing and communicating the framework for calculating, documenting, categorizing, and prioritizing cybersecurity threats GV. RM-07: Discovering and integrating strategic opportunities (positive risks) into organizational cybersecurity risk assessments | |
| Roles, responsibilities, and authorities (GV. RR): The organization establishes and communicates cybersecurity roles, responsibilities, and authorities for accountability and improvement. | GV.RR-01: Establishing organizational leadership’s responsibility and accountability for cybersecurity risk and fostering a risk-aware, ethical, and continuously improving culture GV.RR-02: Defining, distributing, understanding, and executing cybersecurity roles, responsibilities, and authorities GV.RR-03: Allocating adequate resources by the cybersecurity risk strategy, roles, responsibilities, and policy GV.RR-04: Integrating cybersecurity in human resource practices | |
| Policy (GV. PO): Establishing and enforcing the cybersecurity regulations | GV.PO-01: Creating, informing, and applying a policy on cybersecurity risk management based on organizational context, strategy, and priority GV.PO-02: Reviewing, revising, communicating, and implementing the information security risk management policy to mitigate changes in requirements, threats, technology, and organizational mission | |
| Oversight (GV.OV): Monitoring and improving the cybersecurity program | GV.OV-01: Examining cybersecurity risk management strategy results to influence and modify strategy and direction GV.OV-02: Reshaping and enhancing the cybersecurity risk management approach to offer organizational requirements and risk coverage GV.OV-03: Evaluating and monitoring organizational cybersecurity risk management performance for determining required modifications | |
| Cybersecurity Supply Chain Risk Management (GV. SC): Risk management of third-party relationships | GV.SC-01: Establishing and agreeing on a cybersecurity supply chain risk management program, strategy, objectives, policies, and processes GV.SC-02: Establishing, communicating, and coordinating cybersecurity roles and responsibilities of suppliers, customers, and partners internally and externally GV.SC-03: Integrating cybersecurity supply chain risk management into cybersecurity and enterprise risk management, risk assessment, and improvement processes GV.SC-04: Prioritizing and identifying suppliers based on criticalityGV.SC-05: Developing, prioritizing, and including requirements to address supply chain cybersecurity risks in agreements and contracts GV.SC-06: Performing planning and due diligence to prevent risks before engaging in formal supplier or third-party relationships GV.SC-07: Identifying, documenting, prioritizing, assessing, responding to, and monitoring the risks posed by suppliers and other third parties during the relationship GV.SC-08: Integrating relevant suppliers and third-party organizations into incident planning, response, and recovery activities GV.SC-09: Integrating supply chain security controls into cybersecurity and enterprise risk management programs and managing their performance throughout the technology product and service lifecycle GV.SC-10: Including considerations for the activities at the end of a partnership or service agreement in cybersecurity supply chain risk management plans | |
| Identify (ID): Mapping Risks and Assets Identifying controls requires an asset inventory and risk assessment to determine security action priorities. It requires a profound understanding of the business arena and potential threats. | Asset Management (ID.AM): Identifying and managing business-critical assets (data, hardware, etc.) based on their importance and risk | ID.AM-01: Hardware inventories are maintained ID.AM-02: Software, services, and systems inventories are maintained ID.AM-03: Representations of authorized network communication and data flows are maintainedID.AM-04: Inventories of supplier-provided services are maintained ID.AM-05: Assets are prioritized based on classification, criticality, resources, and mission impact ID.AM-07: Inventories of data and associated metadata are maintained ID.AM-08: Managing systems, hardware, software, services, and data across their lifecycle |
| Risk Assessment (ID.RA): Understanding of cybersecurity threats to the organization | ID.RA-01: Discovery, confirmation, and documentation of asset vulnerabilities ID.RA-02: Receipt of cyber threat intelligence from information-sharing sources and groups ID.RA-03: Discovery and documentation of threats, internal and external ID.RA-04: Discovery and documentation of possible threat impacts and probabilities of exploitation ID.RA-05: Using threats, vulnerabilities, probabilities, and impacts to inform understanding of inherent risk and to guide risk response priority ID.RA-06: Choosing, prioritizing, planning, tracking, and communicating risk responses ID.RA-07: Administration, risk impact analysis, recording, and monitoring changes and exceptions ID.RA-08: Conducting processes to receive, analyze, and respond to vulnerability disclosures ID.RA-09: Assessing the authenticity and integrity of hardware and software before acquisition and use ID.RA-10: Assessing critical suppliers before acquisition | |
| Improvement (ID.IM): Recognizing opportunities for enhancing cybersecurity risk management | ID.IM-01: Recognizing improvements from assessments ID.IM-02: Identification of improvements from security training and testing, including vendorsID.IM-03: Identifying enhancements from the running of operational processes ID.IM-04: Developing, maintaining, and enhancing incident response and other security plans | |
| Protect (PR): Implementing Preventive Measures Protect integrates controls to decrease risks, from identity administration, training, and data security to defense tools in technical, physical, and administrative domains. | Identity Management, Authentication, and Access Control (PR.AA): Access control to assets | PR.AA-01: Administrating authorized users’ services and hardware identities and credentials PR.AA-02: Proofing and binding interaction context-based identities to credentials PR.AA-03: Verifying users, services, and hardware PR.AA-04: Protecting, sending, and verifying identity assertions PR.AA-05: Defining, managing, enforcing, and auditing access permissions, entitlements, and authorizations, including least privilege and separation of duties PR.AA-06: Administrating, monitoring, and enforcing physical access to assets |
| Awareness and Training (PR.AT): Training employees on cybersecurity procedures | PR.AT-01: Basic cybersecurity awareness and training for all employees PR.AT-02: Providing targeted cybersecurity awareness and training to individuals holding specific roles | |
| Data Security (PR.DS): Preserving data confidentiality, integrity, and availability | PR.DS-01: Protecting data confidentiality, integrity, and availability at rest PR.DS-02: Maintaining data confidentiality, integrity, and availability in transit PR.DS-10: Keeping data in use confidential, available, and complete PR.DS-11: Creating, protecting, maintaining, and authenticating data backups | |
| Platform Security (PR.PS): Hardware, software, and service protection | PR.PS-01: Putting into practice and enforcing configuration management measuresPR.PS-02: Maintaining, replacing, and removing software about risk PR.PS-03: Maintaining, replacing, and removing hardware about riskPR.PS-04: Generating and making log records accessible for continuous monitoring PR.PS-05: Preventing installation and execution of unauthorized software PR.PS-06: Integrating secure software development practices and assessing their effectiveness | |
| Technology Infrastructure Resilience (PR.IR): Ensuring the resilience of technology infrastructure | PR.IR-01: Protecting networks and environments from unauthorized logical access and use PR.IR-02: Protecting technology assets from environmental threats PR.IR-03: Executing resilience mechanisms in normal and unfavorable conditions PR.IR-04: Possessing adequate resource capacity to deliver availability | |
| Detect (DE): Sustained Threat MonitoringDetect focuses on security monitoring and analyzing anomalies for real-time threats to enable immediate security. | Continuous Monitoring (DE.CM): Regularly monitor assets for adverse and negative events | DE.CM-01: Monitoring technology services and networks DE.CM-02: Monitoring physical space DE.CM-03: Monitoring technology and human activity DE.CM-06: Monitoring external service provider activities and servicesDE.CM-09: Monitoring hardware, software, and data employed in computing |
| Adverse Event Analysis (DE.AE): Investigating events to establish if an incident exists | DE.AE-02: Investigating potential adverse events to understand more about the related activity DE.AE-03: Correlating information from multiple sources DE.AE-04: Determining the estimated scope and effect of adverse events DE.AE-06: Providing adverse event data to authorized personnel and equipment DE.AE-07: Including cyber threat intelligence and other situational information in the analysis DE.AE-08: Reporting incidents when adverse events reach specific criteria | |
| Respond (RS): Incident Action and MitigationResponse delineates incident management from planning to communications, analysis, and mitigation so that quick response and learning can be obtained from incidents. | Incident Management (RS.MA): Responding to detected incidents | RS.MA-01: Executing the incident response plan in coordination with relevant third partiesRS.MA-02: Triage and verification of incident reportsRS.MA-03: Categorization and prioritization of incidentsRS.AN-04: Escalation or elevation of incidents as requiredRS.MA-05: Employing criteria for activating incident recovery |
| Incident Analysis (RS.AN): Analyzing incidents | RS.AN-03: Performing analysis to establish incident occurrence and root cause RS.AN-06: Recording actions taken during an investigation and preserving their integrity RS.AN-07: Collecting and preserving incident data and metadata integrityRS.AN-08: Estimating and confirming an incident’s magnitude | |
| Incident Response Reporting and Communication (RS.CO): Reporting and communicating incidents | RS.CO-02: Notifying internal and external stakeholders of incidents RS.CO-03: Supplying information to designated internal and external stakeholders | |
| Incident Mitigation (RS.MI): Taking actions to reduce the impact of incidents | RS.MI-01: Containing incidents RS.MI-02: Eradicating incidents | |
| Recover (RC): Restoring Operating ResilienceRecovery focuses on restoring systems and operations post-incident, emphasizing planning, communication, and improvement to minimize disruption. | Incident Recovery Plan Execution (RC.RP): Performing restoration activities | RC.RP-01: Executing the recovery part of the incident response plan RC.RP-02: Selecting, scoping, prioritizing, and performing recovery actions RC.RP-03: Verify the integrity of backups before restoration RC.RP-04: Considering critical mission functions and cybersecurity risk management in planning post-incident operation RC.RP-05: Verify the integrity of restored assets and testify to regular operation RC.RP-06: Notifying incident recovery termination and wrapping up related documentation |
| Incident Recovery Communication (RC.CO): Restoration activity coordination | RC.CO-03: Informing recovery progress to designated internal and external stakeholders RC.CO-04: Distributing public recovery updates through authorized channels |
The interconnectedness of core functions
These core functions are interdependent and collectively form an end-to-end cybersecurity framework. By knowing and applying these fundamental functions, organizations can establish a strong security stance that efficiently addresses risks and protects their assets.
Importance of NIST CSF controls:
The NIST Cybersecurity Framework (CSF) is important because it provides a structured, flexible, and widely accepted approach to managing cybersecurity risk. It helps organizations of all sizes understand their current security posture, identify gaps, and prioritize improvements based on business needs and risk tolerance.
Risk management: The CSF provides a structured way to define, analyze, and prioritize cybersecurity risk so that organizations can speak with a unified voice internally and externally. Transparency enables organizations to link cybersecurity efforts to enterprise business strategy, improving prioritization and risk analysis.
Continuous improvement: Organizational profiles enable companies to track gaps and improve. The framework’s methodical nature makes repeated review and calibration easy. Assurance of integration facilitates constant feedback-driven improvement from various sources, including business processes and security testing.
Flexibility: The NIST CSF controls list is designed in a non-prescriptive, sector-, country-, and technology-agnostic way so that organizations may implement it according to their particular needs. It can be combined with an organization’s existing risk management schemes and frameworks like ISO 27001 and HIPAA.
Integration: The CSF integrates other ICT risk management integration initiatives, like Enterprise Risk Management (ERM), and maps them to standard frameworks, thus enhancing holistic-level risk management.
Enhances communication: It provides a common language for describing cybersecurity risks, facilitating two-way communication among stakeholders. Organizational Profiles also facilitate easier communication about an organization’s cybersecurity posture.
The “Govern” feature within CSF 2.0 demonstrates the expanding importance of cybersecurity and how it corresponds to business objectives and regulatory standards. The system also enhances cyber resilience, incident response, recovery, and reporting to the board of directors, making it a vital information source for modern organizations.
NIST CSF control made easy with Sprinto:
Working with the NIST Cybersecurity Framework (CSF) will soon be an exercise in futility without its prescriptive language and application to concrete security practice. What if this were easy for you and transformed the intimidating task of implementing the NIST CSF into an effortless, streamlined process? Sprinto does just that.
Sprinto allows you to easily apply and map NIST CSF controls to your entire infrastructure, from tactical processes to technical assets. Good cybersecurity is not a box-ticking exercise; it’s about building a strong and resilient security position. Sprinto achieves that by streamlining the most critical processes for compliance, providing clear visibility of your risk profile, and driving sustained cyber readiness.
Sprinto streamlines NIST CSF compliance through automation and transparent risk management, smartly mapping controls, and providing ongoing monitoring. This allows tailored security beyond checklists, facilitates informed decisions through an entire risk register, and aligns with NIST CSF pillars for flexible, zero-trust security across frameworks.
FAQs
What is the difference between NIST and NIST CSF?
CSF is a voluntary standard for organizations, while NIST 800-53 is mandatory for US government contractors, federal information systems, and federal agencies. CSF is a framework, but NIST 800-53 is a collection of standards. CSF is risk management-oriented, but NIST 800-53 has comprehensive security controls.
What are the two NIST frameworks?
The two NIST frameworks are CSF and RMF.
NIST CSF is a voluntary cybersecurity framework for risk management using core functions. NIST RMF (risk management framework) is a process for implementing security into system development, specifically for federal systems.
How many NIST CSF 2.0 controls?
The NIST CSF 1.1 had 23 categories and 108 subcategories or controls. After much realignment, deletion, and reorganization of these categories and controls, the new version has 22 categories and 107 subcategories.
Heer Chheda
Heer is a content marketer at Sprinto. With a degree in Media, she has a knack for crafting words that drive results. When she’s not breaking down complex cyber topics, you can find her swimming or relaxing by cooking a meal. A fan of geopolitics, she’s always ready for a debate.
Explore more
research & insights curated to help you earn a seat at the table.


















