FedRAMP as a framework has always maintained the need to stay aligned with technological updates and stakeholder demands. To support this vision, the General Services Administration (GSA), which oversees FedRAMP, has developed a comprehensive cybersecurity roadmap. This initiative aims to reshape the future of cloud security services for federal agencies, with the latest updates reflecting its ongoing commitment to this goal.
With the introduction of new technical documentation hubs, pilot programs, and a streamlined authorization process, FedRAMP is working to make the path to authorization faster and more accessible for Cloud Service Providers (CSPs).
In this blog, we examine the key enhancements made to FedRAMP in 2024 and walk you through the updated authorization process.
TL;DR
| In 2024, FedRAMP replaced the Joint Authorization Board (JAB) with a FedRAMP Board, shifting authorization responsibility to individual agencies. This change simplifies and accelerates the path to an Authority to Operate (ATO) for Cloud Service Providers (CSPs) |
| Innovations like the Agile Delivery Pilot and Digital Authorization Packages aim to modernize the authorization process with real-time monitoring and machine-readable formats for security documentation |
| The four phases of FedRAMP authorization include preparation, initiation, security assessment, and authorization, followed by continuous monitoring to ensure ongoing compliance. |
FedRAMP at a glance
FedRAMP (Federal Risk and Authorization Management Program) is a US government program that aims to accelerate the adoption of cloud technologies within the federal government by setting stringent security standards for Cloud Service Providers (CSPs).
It offers a consistent and repeatable framework for CSPs to ensure the security of their products through:
- Security Assessments: Every CSP must undergo a security assessment conducted by a Third-party Assessment Organization (3PAO) to ensure the controls align with FedRAMP’s requirements.
- Authorization: The government-wide program offered two main types of authorization before 2024: Joint Authorization Board (JAB) and Agency Authorization to Operate (ATO), with the former reserved for CSPs offering services to multiple agencies and the latter issued by an individual federal agency. However, in 2024 FedRAMP introduced a single agency-driven path and replaced the JAB with FedRAMP board and the responsibility of authorization is now on individual agencies.
- Ongoing Monitoring: After receiving the Authorization to Operate, the CSP must continuously monitor the controls to remain secure over time
FedRAMP’s value in strengthening federal cloud security
One key challenge with Federal IT has been legacy systems and the slow down of digital transformation. Modernization and a switch to cloud technology are needed as agencies strive for scalable resources-on-demand, flexibility, and embracing new technologies such as AI and machine learning. It is also needed to save on-premise infrastructure and maintenance costs.
However, with cloud technologies comes the fear of data security and privacy, and considering how sensitive government information is, the concerns are valid. With FedRAMP, this problem has been significantly solved as it ensures that the CSPs follow the rigorous cybersecurity requirements of federal agencies. Not only has the program driven cloud adoption by federal agencies, but it has also led to the development of secure and compliant cloud solutions that also benefit the commercial sector.
What’s new with the 2024 single-path ATO Process?
The Authority to Operate (ATO) is a formal approval by the federal agency that allows a CSP to offer its services within the government’s environment. It demonstrates that the CSP has undergone a detailed security assessment and meets the compliance requirements as outlined.
Previously, FedRAMP had two distinct paths for the Authorization process: Joint Authorization Board (JAB) and agency authorization. However, to accelerate and modernize the process, FedRAMP has eliminated the separate JAB path and enhanced the process to a single agency-driven pathway. The key updates include:
A new FedRAMP board
The JAB, which was responsible for issuing a provisional ATO, has been replaced by the FedRAMP board comprising seven federal technology executives appointed by the Office of Management and Budget (OMB). The key responsibilities of the board include:
- Offer strategic guidance and provide policy approvals
- Enhance the ability of the program to process more authorizations effectively
- Ensure program oversight and suggest improvements
Agile delivery pilot
The Agile Delivery Pilot aims to streamline the approval process by removing traditional change management approval processes for new additions and features that do not impact security or privacy. To speed up the process, CSPs can deploy updates required to align with modern practices like CI/CD or DevSecOps without prior agency approvals. It also advocates for shifting from periodic reviews to real-time security monitoring for proactive risk management.
Six cloud services participated in the pilot, and their feedback, which is mostly positive, can make some permanent changes to processes.
Digital authorization packages
This is another pilot project launched by FedRAMP in August 2024 and hosted as an open-source project on GitHub. It aims to enable CSPs to create System Security Plans (SSPs) in the Open Security Controls Assessment Language (OSCAL) format. OSCAL is a standardized format developed by NIST to make the data machine-readable, thereby streamlining the authorization process.
The automated validation ensures faster reviews, and while it doesn’t change the current authorization process, the feedback and improvements can soon result in a technical platform.
Cryptographic modules policy
FedRAMP has also shared a draft policy to clarify the rules on certain encryption tools or cryptographic modules. It offers guidance on how FIPS 140 should apply, which ensures that encryption tools are fully secure to protect sensitive information.
We have already gathered feedback on the draft policy, and we expect it to be finalized by early 2025.
Technical advisory group
The Technical Advisory Group is another new addition, created to offer comprehensive advice on new technologies or any security challenges. The group members are chosen from various federal agencies, such as the Department of Homeland Security, CISA (Cybersecurity and Infrastructure Security Agency), and the Centers for Medicare and Medicaid Services. They also complement the work of the Federal Secure Cloud Advisory Committee (FSCAC) and help the FedRAMP to enhance their risk management processes.
Maximize output without breaking a sweat
What does it take to get FedRAMP compliant with the new upgrades?
The FedRAMP authorization process can be completed in four phases: Preparation, pre-authorization, security assessment, and ongoing monitoring. Depending on the organization’s maturity, the first two phases can take anywhere from 6 to 12 months, and the authorization can take another 3 to 8 months.
Here’s a breakdown of the implementation steps:
1. Preparation and readiness assessment
The preparation phase sets the foundation of the FedRAMP authorization process and requires you to address the following:
- Identify FedRAMP authorization boundary: Include physical infrastructure, software components, data flows, and even metadata associated with sensitive data management such as access control information or classification labels
- Establish a risk management strategy: Define a strategy to identify, assess, and manage risks as per FedRAMP’s requirements
- Identify security categorization: Classify systems according to Federal Information Processing Standards (FIPS) 199 and determine the impact level as low, medium, or high. Low-impact systems handle non-sensitive data, medium-impact systems handle sensitive but non-personally identifiable data, and high-impact systems handle highly sensitive information.
- Begin with control mapping: Select relevant NIST 800-53 controls as per the chosen impact level and FedRAMPs baseline requirements
- Complete documentation: Prepare essential documents such as a System Security Plan (SSP), incident response plan, continuous monitoring plan, and other policies and procedures
- Engage a 3PAO: Find a FedRAMP-accredited 3PAO to conduct readiness and security assessments
The 3PAO then validates the authorization boundary, security categorization, and documents and conducts a gap analysis to assess baseline compliance.
The analysis’s findings are documented in the Readiness Assessment Report (RAR), including strengths, weaknesses, and areas of improvement, which are addressed in the POA&M (Plan of Action and Milestones). If the CSP is ready for the formal assessment, the 3PAO awards the marketplace a FedRAMP-ready status.
2. Pre-authorization
The next step is to move from FedRAMP ready status to In-Process. This involves some pre-authorization activities;
Formalize agency partnership
The CSP establishes a formal partnership with the agency by securing a written communication. This demonstrates the agency’s intent to partner with the CSP for FedRAMP authorization. The agency looks for fully functional systems, mature security processes, a CSP leadership team and other certifications to determine CSP’s readiness before formalizing the partnership.
The agreement contains key details on CSP and CSO, security categorization, and points of contact from both parties. It also highlights CSP’s commitment to start the assessment within 6 months and the agency’s attestation to complete the process within 12 months.
Authorization planning
The CSP then collaborates with the agency to plan the authorization process. This step focuses on clearly defining roles and responsibilities, identifying authorization deliverables, understanding the process, and meeting any other FedRAMP requirements.
Work Breakdown Structure and In Process Request
Next, complete a Work Breakdown Structure (WBS) with milestones, responsibilities, and timelines and submit an In Process Request (IPR) to FedRAMP PMO. The email indicates that the CSP and the agency are beginning the authorization process. The email includes details such as impact level and assessment schedule. One of the following additional requirements must also be met for IPR:
- The agency provides proof of award for the use of cloud service offering
- The agency and CSP demonstrate that the agency is actively using the CSO
- The CSO is already listed as FedRAMP ready in the Marketplace
- A formal kickoff meeting has been completed with relevant stakeholders
Kickoff meeting
The kickoff meeting is the official beginning of the authorization process that brings together all key stakeholders, such as the CSP, agency, 3PAO, and FedRAMP PMO, to discuss:
- Background and technical aspects of the cloud service offering
- Security requirements and controls
- Roles and responsibilities, milestones and project timelines
- Any compliance gaps
- The approach and path to complete the ATO
3. Security assessment
Before running a formal security assessment, the 3PAO prepares a Security Assessment Plan (SAP), in agreement with the company, with details on the review process and the timeline. The 3PAO then conducts the assessment in 3 ways:
- Control review: This involves assessing the documentation and testing controls for operational effectiveness. The 3PAO may examine password configurations, logging capabilities, monitoring mechanisms, and other controls.
- Vulnerability scans: The vulnerability scans help understand weaknesses and patching frequency to secure systems
- Penetration tests: The penetration tests involve simulations of real-world scenarios to understand the organization’s ability to withstand attacks
The 3PAO then prepares a Security Assessment Report (SAR) with recommendations for improvement, which the team uses to update POA&M. While it’s normal to have some issues, the organization must ensure that none of those are high-risk findings.
As a next step, the SSP, SAP, SAR, and POA&M are bundled as a security authorization package for federal agency review.
The federal agency reviews the SAR and may choose to test any controls or analyze if the remaining risks are acceptable before issuing an Authorization to Operate (ATO). Post this, the package and the assessments are uploaded online and reviewed by FedRAMP PMO (Program Management Office).
Finally your service is listed as FedRAMP authorized on the FedRAMP marketplace and you can begin offering your services to the government.
4. Ongoing monitoring and maintenance
Also known as the post-authorization phase, this step involves continuously monitoring security risks and quick resolution. The CSP must upload Continous monitoring deliverables for the agency every month as per the template provided by FedRAMP.
The deliverables include documents such as continuous monitoring monthly executive summary, vulnerability and configuration scans, POA&M, incident response plan, and contingency plan test results. Here’s a link to the template.
To maintain FedRAMP authorization, annual security assessments are also conducted by the 3PAO to ensure that the CSP continuously meets FedRAMP requirements.
Get real-time view of controls with Sprinto
How does FedRAMP integrate with the broader compliance strategy?
FedRAMP is a scalable framework that can easily align with the broader compliance strategy by establishing baseline controls and offering reusable elements.
The NIST 800-53 Foundation
FedRAMP is built on NIST 800-53 controls, which aligns closely with other frameworks such as ISO 27001 and FISMA and can minimize redundancy in implementation.
Cloud-specific compliance controls
FedRAMP requires cloud-specific compliance controls, emphasizing encryption and access management. CSPs already undergoing the FedRAMP authorization process can easily leverage these controls for other cloud frameworks, such as SOC 2 or HIPAA
You can easily use the Common Control Mapping feature from Sprinto to map commonalities.
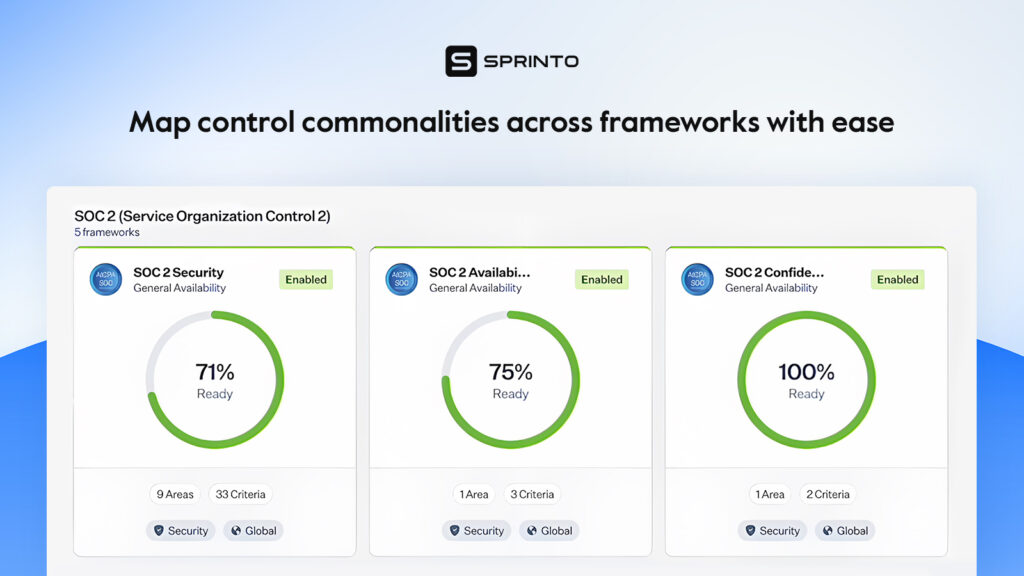
Continuous monitoring approach
The requirement to establish a continuous monitoring mechanism for FedRAMP aligns well with most frameworks, even if they do not directly complement each other. Say, for example, PCI DSS. The monitoring mechanism would still be require,d and you can use the element for the broader compliance strategy.
Enhanced governance
FedRAMP supports uniform security policies, centralized risk management, well-defined roles and responsibilities, and ongoing assessments for better oversight. These processes lead to enhanced governance practices, which support a comprehensive compliance strategy.
How can Sprinto be an enabler in the journey?
The FedRAMP process might seem like a lot to take on, but here’s the good news — you don’t have to go through it repeatedly to win federal contracts. It’s a ‘do once, use many times’ approach, meaning the hard work pays off by opening doors to more opportunities. With tools like Sprinto, you can make the process faster and more cost-effective, so you’re not stuck spending all your time and money on implementation.
The next-gen GRC tool lets you Bring Your Own Framework (BYOF) on the platform and automates most implementation tasks. Just integrate your tech stack, import your controls, and let the product do the heavy lifting. Leverage policy templates, training modules, role-based access controls, continuous control monitoring, automated evidence collection, and other capabilities to power your compliance program.
Take the platform tour today and kickstart your compliance journey. See Sprinto in action.
FAQs
How much does FedRAMP cost?
For small and mid-sized companies, FedRAMP can cost $45000-$2M+, and for larger companies, the cost can go up to $ 5 million. This includes costs of gap assessments, training, documentation, consultation, control implementation, third-party assessments and ongoing monitoring costs.
What are the different types of FedRAMP authorizations?
The three types of FedRAMP authorizations are:
- FedRAMP ready: Pre-authorization designation that indicates CSP’s readiness for FedRAMP security baseline
- FedRAMP In Process: Status that indicates that the CSP is actively working towards authorization
- FedRAMP Authorized: Indicates that CSP has successfully completed the FedRAMP authorization
Can a company lose FedRAMP authorization?
Yes, a company can lose its FedRAMP authorization if it fails to meet ongoing compliance and maintenance requirements such as non-compliance with continuous monitoring, failure to complete annual assessments, unresolved critical vulnerabilities, and any material changes without notification.
Are there any exceptions to FedRAMP?
Yes, FedRAMP compliance is not mandatory for private cloud services which are exclusively for a single federal agency and are fully deployed within its facilities.
Payal Wadhwa
Payal is your friendly neighborhood compliance whiz who is also ISC2 certified! She turns perplexing compliance lingo into actionable advice about keeping your digital business safe and savvy. When she isn’t saving virtual worlds, she’s penning down poetic musings or lighting up local open mics. Cyber savvy by day, poet by night!
Explore more
research & insights curated to help you earn a seat at the table.


















