Your software is like a set of instructions for your device, consisting of thousands of lines of code. Sometimes, there are mistakes or weaknesses in these lines of code. Bad actors use these weaknesses to hack into your systems, similar to a burglar finding an open window. Is there a way to
Without cybersecurity, it’s hard for your company to keep your data, devices, networks, or systems safe from harmful attacks. A “cyber essentials” certification proves that your business has a formidable security posture and is trustworthy. Implementing cyber essential controls and staying on top of it is the way to go.
This article covers everything you need about cyber essentials and their benefits. We explain how cyber essentials work and outline the cyber essentials controls list.
Let’s dive in…
What are Cyber Essentials?
Cyber Essentials is a cybersecurity initiative implemented in 2014 by the government of the United Kingdom. The singular agenda of this is to offer basic cybersecurity for all organizations, big or small.
This certification helps businesses assure their customers that they prioritize securing IT assets and data against cyber-attacks. This, in turn, helps attract new business and foster relationships with trusted IT suppliers. Also, certain government contracts necessitate Cyber Essentials certification, and in this age of trust-less commerce, one you must stay ahead.
It is designed to be a starting point that introduces businesses to the essentials of cybersecurity principles and paves the path for adequate cybersecurity measures.
The essential cybersecurity controls list guides businesses through the technical and administrative controls listed in the initiative and their implementation process. Also, it hands out a baseline certification to show that companies are dead serious about keeping things secure.
5 Cyber Essentials Controls List
Cyber Essentials controls consist of five main essential controls, each with unique characteristics and requirements demands that must be addressed.
The 5 cyber essentials controls are:
- Firewalls
- Secure Configuration
- User Access Control
- Malware Protection
- Security Update Management

1. Firewalls
Firewalls have been around for more than 25 years, serving diligently as the first defense in network security. A software firewall is a physical security guard that checks your incoming and outgoing traffic to decide what to allow or block based on the given security rules.
Now, your company should regularly do a few things to improve the software firewall protection:
- Change any default passwords to strong passwords
- Disable remote administrative access if you don’t need it in your cloud services
- Only let people access the administrative part from the internet if there’s a good reason, and make sure it’s protected by a second Multi-factor authentication factor or an IP whitelist that limits access to trusted addresses
- And as a rule of thumb, block any connections that aren’t authenticated
Experience the Power of Cyber Essentials Controls
2. Security update management
In the Cyber Essentials scheme, patch management is one of the requirements that help keep your devices and software safeguarded from security vulnerabilities. This includes a sweep of activities within your infrastructure management:
- IT admins or managers must identify patching needs based on the severity of security issues
- Once identified, patches or fixes are obtained and tested to ensure they address the vulnerabilities without causing any adverse effects
- Successful patches are then deployed to improve existing device code
For effective security update management:
- Remove old, unsupported software from devices or prevent it from connecting to the internet
- Apply ‘critical’ or ‘high-risk’ updates within 14 days of release
- Enable automatic updates whenever possible
- Ensure that all software on devices is licensed and actively supported by the supplier
- Apply updates promptly for vulnerabilities with a CVSS v3 score of 7 or above or in the absence of severity information from the supplier
3. User access control
The other control that is very important to add is User access control this helps in ensuring the safety of your data and external services. This will restrict special access privileges, so no unauthorized people such as hackers.
You can choose the four main access control types based on your security and compliance needs:
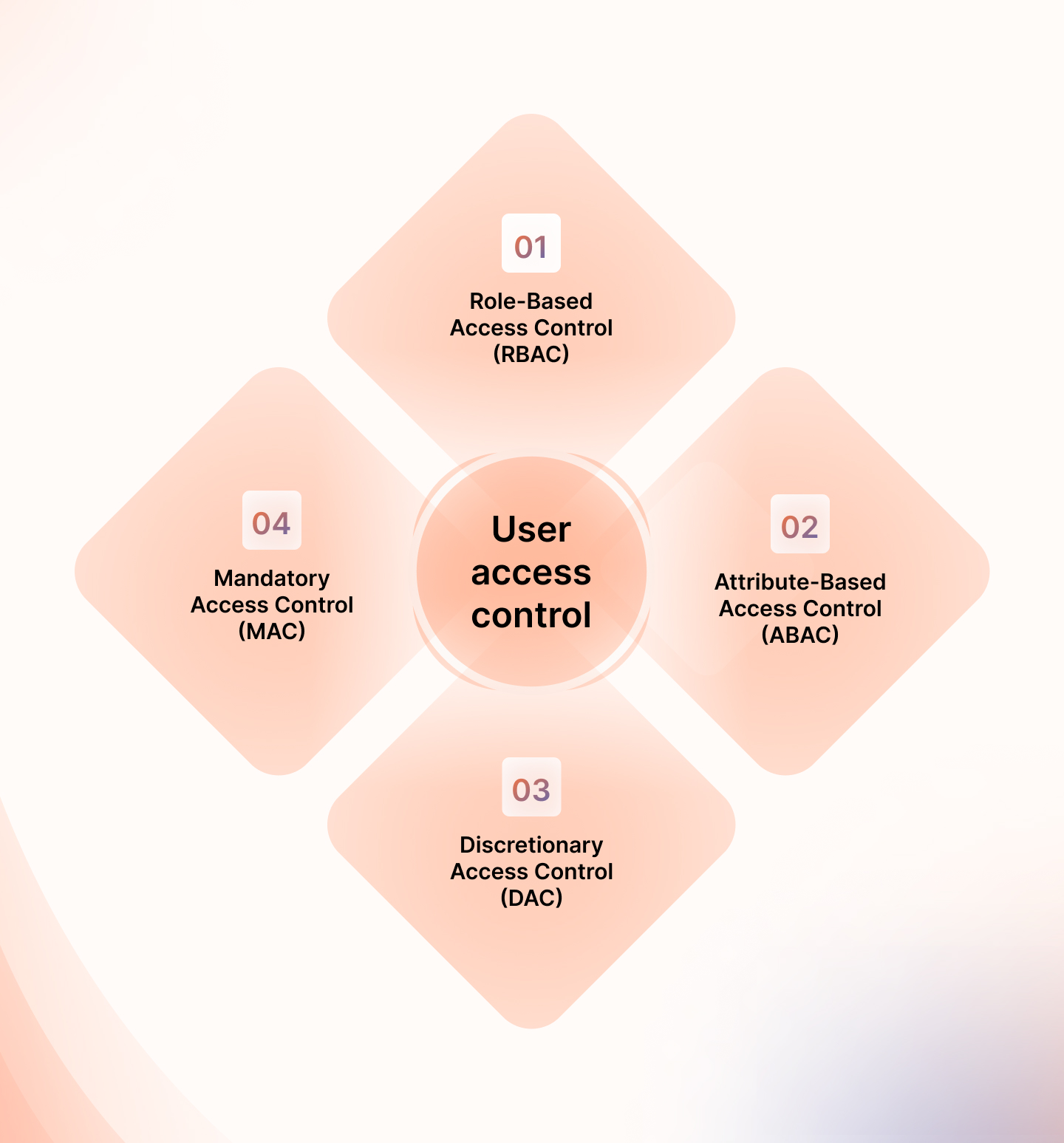
- Role-Based Access Control (RBAC): It is also aimed at users having access only to the relevant data based on their roles in an organization.
- Attribute-Based Access Control (ABAC): different attributes and conditions are used in determining access.
- Discretionary Access Control (DAC): It is an open approach where access depends on the owner or admin
- Mandatory Access Control (MAC): Access rights at various security levels are managed by a central authority in non-discretionary ways.
Or, you might use Sprinto along with user access and technical controls.
Sprinto smoothly combines with ACLs and does more than work in favor of role-based access controls. It allows you to specify certain individuals for every role, automates the circulation of these policy documents and makes sure that they are followed through acknowledgments. Hiring evaluations and offboarding are easier to manage so that ACLs can be accurately implemented.
When it comes to compliance, Sprinto stands out as the #1 rated tool on G2 in its category, boasting a 100% audit success rate. Using Sprinto with ACLs, you can establish a great approach to cyber essentials key controls, policy enforcement, and continuous monitoring for airtight security.
4. Malware Protection
Malware is a blend of “malicious software” that poses various cyber threats like viruses, worms, Trojans, and spyware. These harmful programs are created in a way that infects your computer and causes harm in horrific ways.
One of the biggest security risks is cybercriminals stealing your users’ confidential information, especially online banking details, which they can exploit to drain their accounts or create fraudulent credit card bills.
This is why Cyber Essentials lays down rules to minimize the risk of malware:
- Use reliable anti-malware software to detect and remove cybersecurity risk programs actively
- Employ cyber security measures that block connections to malicious websites, reducing the risk of encountering harmful content
- Regularly update your software, ensuring that signature files are updated at least daily to defend against the latest cyber threats
- Configure your software to automatically scan files upon access, including those downloaded, opened, or accessed from network connections
- Ensure that your software scans web pages automatically when you access through a web browser, which adds an extra layer of protection
Explore how our solutions align with your business needs
5. Secure Configuration
Insecure configurations are common pitfalls that criminal hackers exploit. And this is why secure configurations of web and application servers are an important requirement under Cyber Essentials. Failure to manage proper configurations properly can result in various security issues.
So, to improve your security regulations for computers and network devices, you should follow these routine practices:
- Make sure to review and eliminate unnecessary user accounts to minimize potential points of unauthorised access regularly (This has to be done regularly)
- Improve your security settings by removing any unnecessary software (This will reduce your attack surface and potential vulnerabilities)
- Change default or easily guessable account passwords to more complex and less predictable options
- Put your security first by authenticating users before granting Internet-based access to commercially or personally sensitive data
- Disable auto-run features that allow file execution without user authorization, preventing unauthorized access
Also Check: Cyber Essentials Checklist: The Complete List of Requirements
How can Sprinto’s reusable automation help?
Cyber Essentials certification is a need of the hour for your business’ overall functionality. And achieving it is straightforward, with the right IT infrastructure maintenance suite. That said, often, businesses are required to deploy near-similar processes over and over for different requirements.
With Sprinto’s reusable nodes, processes and functions can be reused without needing fresh implementation processes. This seamless functionality helps businesses save time and cost and is hassle-free.
Leveraging Sprinto’s security compliance automation platform helps you automate the repetitive and time-consuming manual activities in setting the foundation while laying the path for future compliance regulatory laws and global compliance frameworks(ISO 27001, SOC 2, HIPAA, GDPR, PCI DSS).
You can use Sprinto for implementing technical controls, running checks, triggering workflows, and real-time compliance monitoring. You can also stay proactive in audits to ensure nothing slips through the cracks.
Upon signing up with Sprinto, you can access:
- A full-stack, automation-first compliance management platform that will scale with your business in no time
- Built-in and customizable compliance programs that align with your audit objectives and business goals
- Get access to on-demand expert advisory to help you move swiftly
- A trusted network of legal advisors, tooling vendors, and security auditors to complete the compliance loop
- Full access to continuous control monitoring
Want to learn more?
FAQs
1. Is Cyber Essentials Mandatory?
No, Cyber Essentials certification is not mandatory. It’s a voluntary program guiding your security efforts, whether already in place or yet to be implemented. However, note that some government contracts may require this certification.
2. What does the certification process for Cyber Essentials look like?
The Cyber Essentials certification process comes in two types. The regular process starts with a simple self-assessment questionnaire. Cyber Essentials Plus involves a more technical and challenging test, including a vulnerability assessment.
3. What is the difference between Cyber Essentials and Cyber Essentials Plus?
The key difference lies in Cyber Essentials Plus going a step further with a technical audit of your IT systems, ensuring cyber security controls are in place for added compliance assurance. The pass bar is set slightly higher for Cyber Essentials Plus.
4. Does your business need Cyber Essentials?
The decision is yours. Cyber Essentials is a starting point to keep your security in check, providing a robust foundation to safeguard your systems against generic attacks and well-known external threats.
Meeba Gracy
Meeba, an ISC2-certified cybersecurity specialist, passionately decodes and delivers impactful content on compliance and complex digital security matters. Adept at transforming intricate concepts into accessible insights, she’s committed to enlightening readers. Off the clock, she can be found with her nose in the latest thriller novel or exploring new haunts in the city.
Explore more
research & insights curated to help you earn a seat at the table.





















