Guide to SaaS Security Posture Management
Payal Wadhwa
Feb 10, 2024
Most security solutions provide an initial layer of protection for threat detection and response. But they are limited in their ability to uncover security problems related to SaaS app usage at a granular level. Therefore, SaaS security posture management is becoming increasingly crucial to IT teams’ current tech stack.
An SSPM can address security holes left by previous employees retaining access to SaaS apps, third-party interactions, misconfigurations, and more. It must be a core part of the SaaS security strategy for every mature organization. In its 2021 research report for cloud security, Gartner named SSPM a must-have security tool and predicted its rising importance in the next 5-10 years.
So, if SaaS posture management is on your radar, read on to learn how it works, how it differentiates from CSPM tools, and how to select one.
What is SaaS security posture management (SSPM)?
SaaS security posture management (SSPM) is the practice of identifying and addressing security risks and vulnerabilities in SaaS applications. This is done through automated tools that help track activity, configuration, access, privileges, and other security events.
SSPM can protect applications across various industries for tools like email clients, messaging applications, CRM tools, HR applications, video conferencing tools, etc.
How does SaaS security posture management work?
An SSPM assesses the configuration settings, user permissions, compliance activities, and other security controls of sanctioned apps. These solutions provide real-time visibility into the SaaS posture and notify about any potential threats.
Let’s see how SaaS security posture management works:
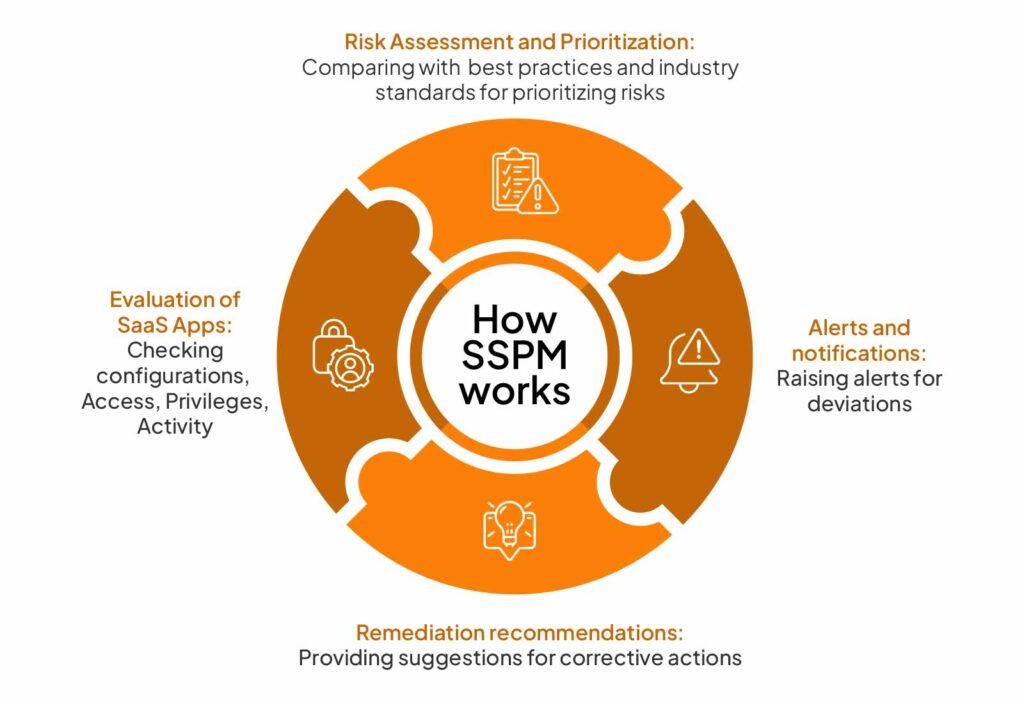
Evaluation of SaaS apps
SSPM tools are used for gathering and analyzing data from various sources across SaaS applications. These tools evaluate a wide range of areas for vulnerabilities.
Configurations: The applications are monitored for any misconfigurations or changes in configurations that are needed over time. These can be instances of sharing files that are not encrypted, lack of measures like Multi-factor authentication for critical accounts, unpatched systems, and the likes.
User access: This consists of controlling access for in-house users, third-party contractors, and integrated services that get access to data. The tools help detect dormant and unnecessary user accounts to reduce attack surface area.
Privileges: More often than not, SaaS applications have too many admins. These admins have the privilege to modify or delete sensitive data. SSPM tools monitor if the permissive settings are extended to the right people and whether they are executing the right actions with those privileges.
Activity: Monitoring of activities helps analyze unusual behavior across the SaaS applications. If any user, integration, or configuration poses a potential risk, activity monitoring will provide context that administrators can use to fix.
Risk assessment and prioritization
After data gathering and analysis, the tools assess risks by comparing data to best practices, security policies, and industry standards. Risks are then assigned scores and prioritized for initiating further action.
Alerts and notifications
Severe risks are notified through alerts on mail, chat, or other integrated channels. The alerts are enriched with details about the trigger, such as misconfiguration information, affected user/account, etc.
Remediation
Most tools offer recommendations and how-to-fix guides for initiating remediation measures. These could include actions like revoking access, reworking security misconfigurations, etc.
Recommended: Guide to SaaS compliance
What are the key features of SSPM?
SaaS posture management solutions look beyond default settings and analyze multiple SaaS interfaces, configurations, and controls. They are enriched with features to ensure protection from any security breach.
Here are the 6 features of SSPM you should be looking at:
Continuous monitoring: SSPM security ensures real-time monitoring of SaaS applications by running a standard list of checks. This helps in taking a proactive approach to risk by alerting security teams when threats are detected.
Also, refer to a complete guide to continuous monitoring
Risk assessments: Risks are identified and scored after vulnerability scanning, configuration analysis, and access management evaluation. All risks can be centrally managed from a single dashboard, providing a bird’s eye view of the risk profile.
Find out: How you can perform risk assessment
Remediation: Remediation assistance is provided to admins based on risk assessment findings. An audit trail of corrective actions initiated is also maintained for reference.
Integrations: SSPM tools support integrations with other IT solutions to ensure secure environments. These include messaging apps, ticketing solutions, IAM tools, HR tools, and other services that help maintain a robust SaaS security posture.
Compliance Management: SaaS posture management monitors adherence to regulatory and compliance standards like GDPR and HIPAA. They also help with addressing compliance deviations and maintaining documentation for audits.
However, the compliance management capabilities of SSPM can be limited. Coupling it with compliance automation tools like Sprinto is advisable to ensure both security and compliance posture are aligned with industry standards.
Reporting: SSPM solutions generate comprehensive reports on overall SaaS security posture. Additionally, there are customization options to create tailored reports as per business requirements.
How to select the right SSPM solution?
Selecting the right SSPM solution poses challenges of complex cloud requirements, an array of features to choose from, budgetary constraints, and more. The decision often involves critical members of the IT team and intensive research.
Here are the steps to select an appropriate SSPM solution for your business:
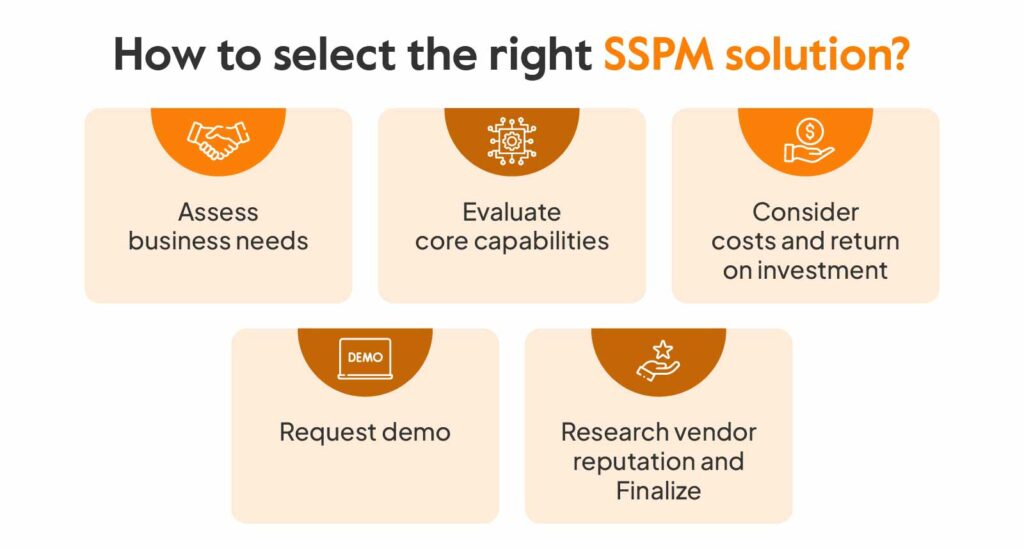
1. Assess business needs
Start by determining your organization’s extent of SaaS exposure by creating a list of SaaS apps and third-party integrations. Next, define the compliance requirements applicable to the business. This will give an overview of security and compliance needs and help you list some SSPM solutions supporting the objective.
2. Evaluate core capabilities
While automated security assessments, policy enforcement, and continuous monitoring will be key to most solutions, look for security features beyond that.
Scalability is essential to accommodate your increasing cloud usage with time without hindering performance quality. Also, look for breadth of integration for expanded coverage. Next, play with the product to understand the interface’s intuitiveness and flexibility.
Ease of use reduces the learning curve, and customization capabilities help accommodate new workflows effortlessly.
Lastly, check out the tool’s incident management capabilities and disaster recovery mechanisms for efficiently dealing with cyber threats.
3. Consider costs and return on investment
When comparing costs, consider the following:
- Total cost of ownership: This includes the cost of initial licensing/subscription, set-up costs, customizations, ongoing costs, and maintenance.
- Price for add-on features: Check if the proposed price is for a bundled solution or if additional features cost extra
- Return on investment: Analyze the long-term value the solution brings to the organization regarding cost savings, additional revenue, etc.
Make a well-informed decision aligning with the budget without compromising critical functionalities that should be a must-have.
4. Request demo
Set up some time for demos and trials to understand the capability spotlight and ease of navigation. Ask SSPM vendors how the product enables the discovery of SaaS apps, policy enforcement, identification of security gaps, and guided remediation.
5. Research vendor reputation and Finalize
Get more insights about the market reputation of SSPM vendors through customer references, reviews, and case studies. Check for experience working with similar businesses and industries. Refer to platforms like G2 and Capterra for pros, cons, and user ratings.
Also check out: Security audit checklist
What is the difference between SSPM and CSPM?
Cloud security posture management (CSPM) is identifying and managing security risks in the cloud infrastructure. CSPM provides visibility across multi-cloud environments, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
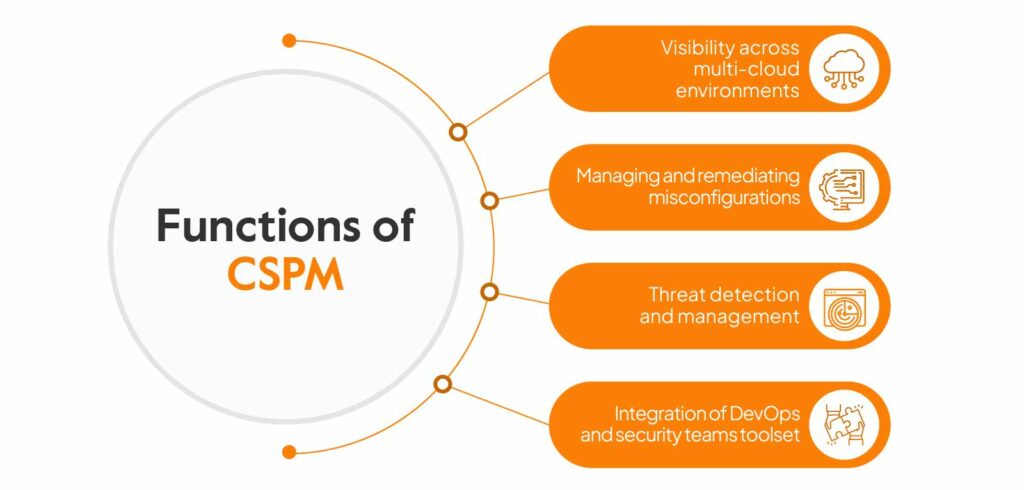
SSPM, on the other hand, focuses only on SaaS security. It ensures data security and compliance for SaaS apps and is narrower in scope.
Here’s a detailed difference between SSPM and CSPM:
| SSPM | CSPM | |
| Scope | Covers only the security of SaaS applications | Covers the security of cloud environment |
| Focus | Identifying and addressing SaaS security risks because of misconfigurations, unauthorized access, overextended privileges, and other suspicious activities | Detecting and managing hidden security threats, misconfigurations, compliance deviation and other security risks in the cloud infrastructure |
| Use Case | Applicable to organizations using a number of SaaS apps like Microsoft Office 365, ServiceNow, Google Workspace etc. | Applicable to organizations using multi-cloud environments like AWS, Microsoft Azure etc. |
| Capability differentiation | More coverage on SaaS security with add-on features like managing third-party applications integrated with the platform | Granular visibility across IaaS, PaaS, and SaaS but less extensive coverage for SaaS security (like user permission settings monitoring) |
| Examples of tools | Push, AppOmni, Zscaler etc. | Microsoft defender for cloud, Wiz, Lacework etc. |
Recommended: Guide to cloud compliance
Benefits of SaaS security posture management
SaaS security posture management constantly tracks SaaS behaviour to provide insights for any risks, compliance deviations or faulty settings.
This helps in establishing SaaS best practices and fosters a culture of improvement.
Here are some benefits of SSPM:
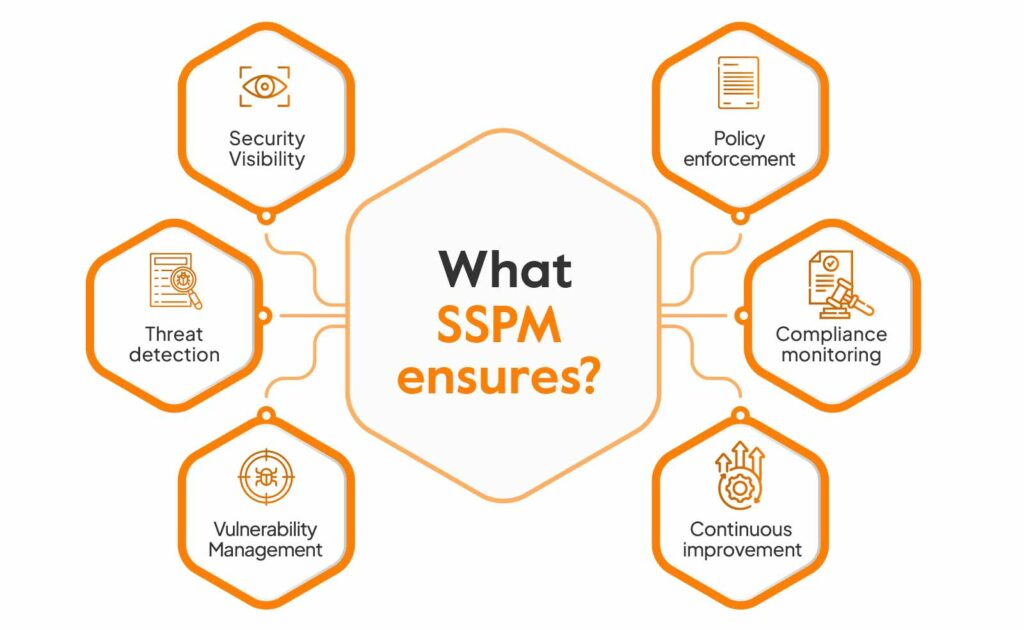
Visibility across the SaaS environment
SSPM solutions keep an eye on configuration changes, access controls, and compliance activities, thereby providing a comprehensive security review of SaaS apps. There’s centralized visibility across the SaaS environment from a consolidated platform.
Discovers faulty and relaxed settings
Any permission settings that are overly relaxed or configurations that are faulty are automatically detected by SSPM solutions. This is especially crucial for businesses depending on a number of SaaS apps and having a large employee base.
Time and cost savings
SSPM tools help minimize the occurrence of unauthorized access, data loss, theft, and breaches. This saves the organizations thousands of dollars and hundreds of man-hours that would otherwise go into mitigating the damage caused.
Enhanced incident preparedness
SaaS security posture management solutions enable round-the-clock monitoring and real-time risk assessments. The contextual alerts at the time of threat detection, enhance the response timing and incident preparedness.
Scalable Framework
As an organization expands its cloud environment and adds more security layers and SaaS apps, SSPM can accommodate a large volume of data. Automated assessments, pre-defined workflows, integrations, and other features bring this scalability. The confidentiality, privacy, and security of sensitive data is maintained even with the growing user base.
How is SSPM related to SASE?
Secure Access Service Edge (SASE) is a cloud-based framework that unifies network security services and Wide-area networks into one deliverable service. These services include FWaaS (firewall as a service), CASB, SWG (secure web gateways), and more.
Gartner predicts 40% of enterprises will have strategies for adopting SASE by 2024. With the increased adoption of remote work and cloud provider services, this model came as an advancement to traditional network perimeter-based models. It eliminates the need to manage multiple cloud applications, solutions, and networks across a diverse threat landscape.
SSPM will be a crucial component of the broader SASE model with rising demand to manage SaaS security posture.
According to a report by Productiv, 53% of enterprise apps are not managed for renewals, compliance, security, etc., while 97% of IT staff need continuous visibility into the usage of SaaS apps.
This highlights the need for more SSPM vendors in the market to contribute to comprehensive cloud security.
Final thoughts
As the SaaS era continues to bloom, applications have become an attractive attack surface for getting business-critical information. Organizations are, therefore, heading to a proactive approach to managing SaaS risks by integrating SSPM security in their incident response strategy.
Sprinto facilitates this journey by becoming a comprehensive security and compliance solution. While SSPM only focuses on SaaS security, Sprinto oversees cloud compliance risks and ensures compliance across various regulatory standards. The platform greatly enhance incident preparedness and response capabilities with autoamted compliance checks and actions while enabling faster remediation.
Talk to our experts if you’re looking for a compliance automation tool that can complement SSPM’s strengths. Ensure overall business success with Sprinto.
FAQs
What is the difference between SSPM and CASB?
Cloud Access Security Brokers (CASB) are intermediaries between cloud service providers and users, ensuring secure cloud usage. CASB provides visibility and control over cloud environments, including IaaS, PaaS, and SaaS, while SSPM focuses extensively on the security of SaaS apps.
Do SSPM solutions secure every SaaS app?
No, every SSPM solution cannot secure every app. The extent of coverage depends on integrations, API capabilities, customization capabilities, and other factors.
What kind of security actions do SSPM tools automate?
SSPM tools automate various security actions, policy enforcement, alerting, access revoking, managing third-party apps, reporting, and more.


Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.

























