How to Perform Vendor Security Assessment with Questionnaire?
Payal Wadhwa
Oct 04, 2024
January 2022.On of the top-rated identity and access management organizations suffered a data breach impacting 2.5% of its customer base. The hackers infiltrated its sub-processors network and then gained access to the organization’s internal networks.
According to a report by Verizon, a staggering 62% of network intrusions are from third parties. The increasing reliance on vendors for critical functions has become a breeding ground for cyberattacks. This makes a strong case for companies to administer a mechanism to assess vendor security in order to foster a secure environment and minimize business disruptions.
This blog elaborates on the importance and methods of conducting a vendor security assessment to help you manage them efficiently.
What is a vendor security assessment?
Vendor security assessment is the process of evaluating a third-party vendor’s ability to protect sensitive data and eliminate risks that arise from exposure. It helps understand whether vendors are complying with necessary regulations and standards while maintaining a secure environment.
Importance of vendor security assessment
Vendor security assessments are important to address the inherent risk exposure with third-party associations that can lead to data breaches and non-compliance.
A recent report states that 98.3% of organizations worldwide have relationships with third-parties that have had a data breach in the last two years. Failing to gain clarity on a vendor’s security landscape can be exploited by attackers and cost millions.
Here’s why organizations should care about vendor security assessments:
Helps evaluate risks and decide risk appetite
Every organization has a risk appetite which is the ability to tolerate certain types of risks and a vendor’s risk profile must align with it.
Vendor risk assessments provide an overview of the nature of risks involved such as compliance risks, financial risks, operational risks and data security risks and help understand their likelihood and impact.
This becomes an important parameter for selecting the right risk treatment strategies and enhancing preparedness.
Facilitates better vendor selection process
Entrusting a vendor with your information assets requires a careful consideration of several factors. These encompass the presence of controls in place, robust security practices, adherence to laws, financial stability etc.
A well-structured vendor security risk assessment provides insights into these diverse areas, enhancing the selection process.
Ensures better defences for business continuity
Exercising vendor due diligence is crucial for business continuity management (BCM). No organization wants to get entangled in lawsuits and disrupt supply chains because a third-party failed to comply with the requirements.
Vendor assessments give visibility over vendor’s security capabilities enabling their integration with organization’s overall defenses.
Supports compliance reporting efforts
Vendor security assessments are compulsory for certain regulatory frameworks such as GDPR and HIPAA. However, even in cases where these assessments are not mandatory, having due diligence reports demonstrate the organization’s efforts in managing vendor risks and ensuring compliance.
It is a good practice to tie these reports to overall compliance reporting for comprehensive transparency.
How to perform vendor security assessment?
Vendor security assessments are performed by profiling vendors based on risks, evaluating their security posture through various approaches, developing risk response strategies, and reviewing improvements periodically.
These assessments are carried out throughout the lifecycle of vendor relationships from the pre-contract period to vendor onboarding to ongoing associations and offboarding. Each stage has a different set of risks involved and should be addressed accordingly.
Here’s a step-by-step guide to help you perform vendor security assessments:

1. Define security assessment criteria
The assessment criteria establish the foundation and direction of the evaluation process. It defines the compliance requirements against which the vendor shall be assessed and lists the items that will fall under the assessment scope.
Vendor’s risk management practices, security controls, incident management plans, business continuity plans, technical capabilities etc. are some examples of scope items.
2. Identify high and low risk vendors
The next step is to list down all your vendors along with the type and level of services provided. The idea is to use this inventory to categorize high, medium and low-risk vendors. The following questions will help you identify the critical ones:
- Which vendor has the most access to sensitive information?
- The loss of which vendor disrupts my business functions the most?
- Does my vendor comply with all relevant regulations and standards?
- How mature is the security infrastructure of the vendor?
Your immediate focus should be the high-risk vendors but the segregation can be presented to the auditor to demonstrate that the due diligence was performed.
3. Assessment methodology
The surefire way to assess critical vendors and understand the nature, impact and likelihood of risks involves a combination of these approaches:
Evidence from vendor: This approach relies on documentation submitted by the vendor like security policies, incident response plans, certifications like SOC 2, ISO 27001 etc. Additionally, it also comprises responses to vendor security questionnaires that provide further insights.
Security Ratings: These ratings are generated by independent platforms and provide a quantitative measurement of the risk.
Security ratings are calculated with extracted data from multiple sources like public information, threat intelligence feeds etc. and analyzed using algorithms and other methodologies.
Relying solely on vendor documentation and security questionnaires is not a good practice because there can be limited visibility, biased self-evaluations, and time-specific snapshots. Security ratings are the best way to testify the security posture of the vendor yourself and with precision.
Third-party evidence:This approach involves considering publicly available information, independent audits or assessments to help validate vendor’s security stance further.
4. Evaluate risks involved and define tolerance levels
After gathering the assessment data, refine your analysis with the following steps to add clarity and make informed decisions:
- Identify the risk types: Operational, data security, financial etc.
- Have a risk matrix for clarity: Risk=Likelihood X Impact
- Analyze the severity levels (On a scale of 1-10, anything beyond 6 is high risk)
- Define acceptable residual risk: The risk that the organization is willing to take after implementing mitigation plans because the benefits outweigh the costs.
Using a risk matrix is a useful practice for visually understanding the likelihood and impact of risks.
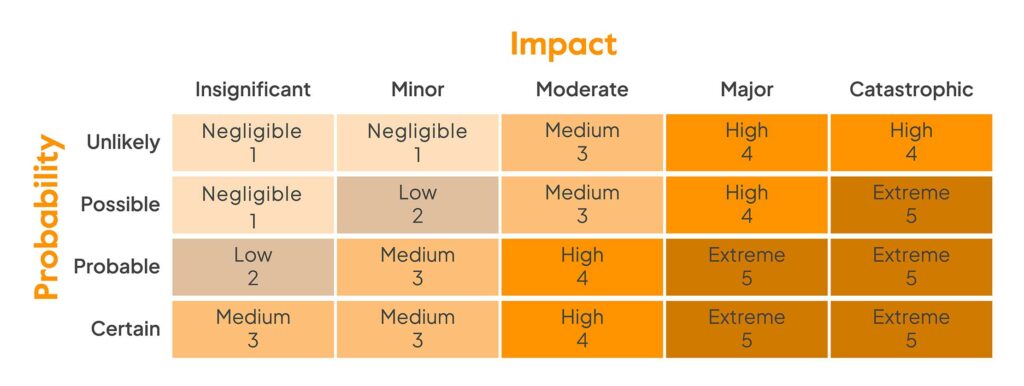
5. Develop Risk Mitigation plans
Based on the vendor risk profiles and the acceptable residual risk scores, you can pursue two options. You can terminate partnership and seek new vendors for the ones exceeding the residual risk score.
A tactical mitigation plan should serve as the cornerstone of further communication for the remaining vendors falling under the acceptable bracket. The plan must include specific actions for identified risks like enabling MFA, backup mechanisms, encryption measures and like.
6. Monitor and re-assess periodically
The residual risk scores keep evolving because of the complex interconnected business landscape. So do the vendor’s stability and viability. It’s therefore crucial to monitor the progress on mitigation plans and identify if any changes are required in the security practices.
Vendor security assessments should be a periodic exercise for addressing issues and strengthening relationships.
Vendor security assessments with Sprinto
While vendor security assessments are a critical component of the overall risk management strategy, these are challenging in practice. Maintaining a list of vendors in excel sheets, understanding the type of data accessed by vendors, keeping a repository of due diligence reports is an arduous task.
Sprinto aims to ease the burden out when managing vendor security.
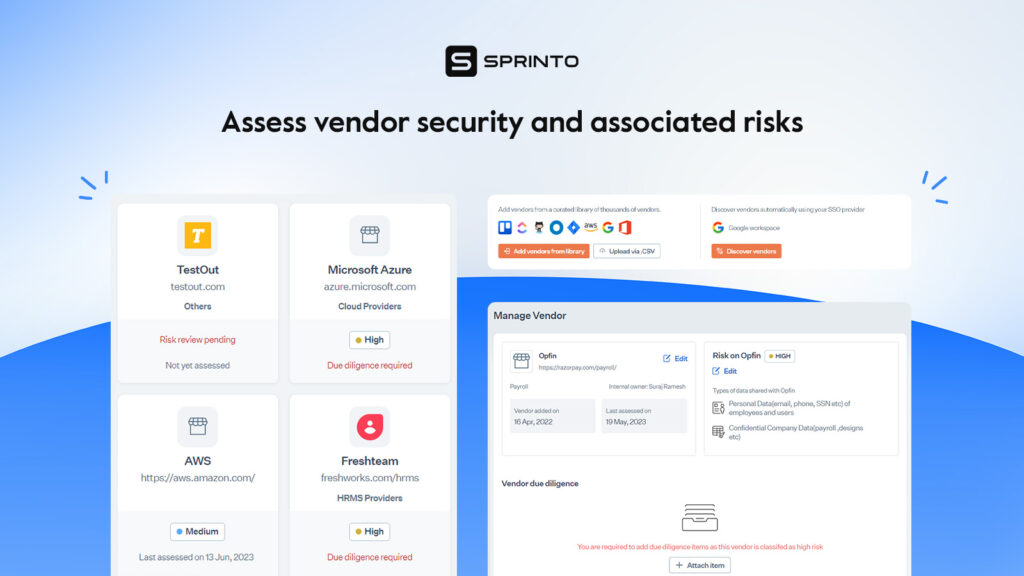
You can discover and add vendors to the platform directly from a curated list of thousands or add your own files. Next, you can choose the type of data that the vendor has access to from various options and the level of risk will automatically be calculated. Due diligence reports and risk reviews can be added and maintained at a centralized place.
Speak to our compliance experts today to make vendor management more efficient and tied to security compliance.
FAQs
Who performs vendor security assessment?
Vendor security assessments can be performed by security teams, IT departments, compliance teams, partnerships/ procurement teams or by third-party assessors. This will depend on the nature and size of the organization as well as the resources available.
What is the purpose of a vendor security assessment?
The purpose of a vendor security assessment is to protect an organization’s information assets by understanding and mitigating the risks involved to enhance incident preparedness.
What are the different types of vendor assessment processes?
Different types of vendor assessment processes include Request for Proposal (RFP), Request for Information (RFI), vendor security questionnaires, vendor demos/presentations, security ratings and third-party assessments.
How often should you conduct vendor security assessments?
Vendor security assessments should be conducted depending on the risk involved with vendor association or the compliance requirement mandates. While conducting vendor security assessment at least once a year is a common practice, this can even be a quarterly exercise for high-risk vendors.


Use Sprinto to centralize security compliance management – so nothing
gets in the way of your moving up and winning big.

























