“Murphy’s Law has a way of creeping into things, and it does so in cybersecurity too—’Anything that can go wrong, will go wrong.’ And lately, every marketer and tech vendor has taken this as their cue to sell you their version of ‘Zero Trust.’ Flashy tools, big promises, and buzzwords galore.
Zero Trust isn’t about the depth of your wallet or the fanciest tools you can buy. And while you’ll often hear it described as a ‘cultural shift,’ it’s an oversimplification. Sure, a shift in mindset is necessary, but isn’t that true of almost everything worth doing? Whether it’s committing to a workout routine or rolling out MFA, the point isn’t the shift itself—it’s what happens next.
We won’t shy away from the technicalities because they matter.
TL;DR
| Zero Trust Architecture (ZTA) eliminates implicit trust by continuously verifying users, devices, and applications, enforcing least privilege, and dynamically restricting access to critical assets. |
| A phased approach is key to implementing ZTA – Start with identity and access management, introduce software-defined perimeters, enforce micro-segmentation, and automate policies for real-time adaptability. |
| GRC and cybersecurity work hand in hand – GRC defines the rules and risk tolerance, while cybersecurity tools enforce them, ensuring a resilient and compliant Zero Trust framework. |
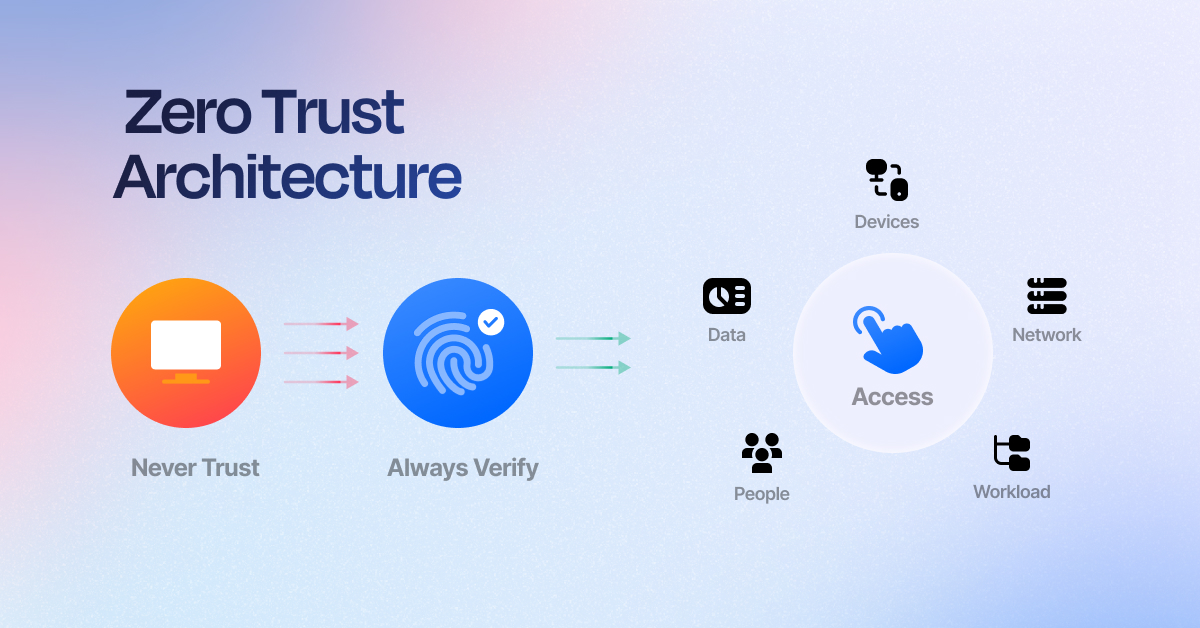
Answering the W’s of Zero Trust
Zero Trust Architecture, ZTA for short, is a security model that challenges the traditional notion of implicit trust within networks. ZTA assumes that security and cyber vulnerabilities or threats can come from anywhere—external attackers or internal actors—and eliminates the outdated reliance on network perimeter-based defenses.
While managed devices—like laptops, servers, and workstations—are monitored and secured, unmanaged assets such as NAS storage, telephony devices, routers, and end-of-life (EOL) systems remain exposed. These gaps form an unseen attack surface, bypassing perimeter defenses and enabling attackers to move laterally across the network.
ZTA is needed now more than ever, as businesses face a growing attack surface fueled by remote work, IoT proliferation, and multi-cloud strategies. The implementation begins with granular identity-based policies that enforce least-privilege access, ensuring users and devices only interact with resources they are explicitly authorized for.
Continuous authentication, device posture checks, and dynamic session monitoring form the backbone of how ZTA functions, creating an adaptive security environment that evolves with real-time risk. By combining advanced technologies like micro-segmentation, encrypted communication, and behavior analytics, ZTA achieves a fine balance between usability and protection.
Before we get to the meat of the matter, Meeta, our PMM at Sprinto has something to say about ZTA.
Zero Trust isn’t about turning developers into security experts or passing the burden of security down like a relay baton. It’s about weaving security into the fabric of daily workflows—from system access to code pushes—so it becomes a natural part of the process. By introducing just enough friction at key points, Zero Trust ensures that only the right people and systems interact with critical infrastructure and data, without disrupting the pace of development.
Meeta Sharma, ISC2 certified.
Great advice adds up. Get more from the brightest minds in GRC — join now
Building a Zero Trust Architecture
Building a Zero Trust Architecture (ZTA) involves a phased approach—starting with identity management, moving through network segmentation, continuous monitoring, and finally automating policies for real-time adaptability.
The result is a security framework that minimizes risks, limits lateral movement, and ensures dynamic protection for critical assets.
Phase 1 – Establish identity and access management
It starts off pretty simple. You essentially need to implement Identity and Access Management (IAM). The focus is; Who and what is allowed to access resources.
- Zero Trust starts with identity verification—you can’t protect what you don’t identify or authenticate.
- IAM ensures every user, device, or service is authenticated and authorized before accessing any resource
IAM isn’t just a gatekeeper — it’s the architect of digital trust within an organization. It ensures that access to sensitive data is managed wisely, aligning security with usability so that business can flow seamlessly, while security and compliance stay intact.
Rajiv Rajan — ISO Lead Auditor
Here’s what you need to do:
- Implement Multi-Factor Authentication (MFA)—biometrics, OTPs, etc.
- Set up Single Sign-On (SSO) to allow users to get secure access across platforms.
- Automate Identity Governance to manage user access automatically by provisioning and de-provisioning accounts.
- Secure admin accounts and privileged accounts.
- Enable continuous authentication to verify users and devices even after they log in by monitoring for unusual behavior or security anomalies.
Phase 2 – Deploy software-defined perimeters
After establishing who can access your systems with Identity and Access Management (IAM), the next step is ensuring how they access these systems is just as secure. Software-defined Perimeters (SDPs) are security models that rely on static firewalls and expose IP addresses.
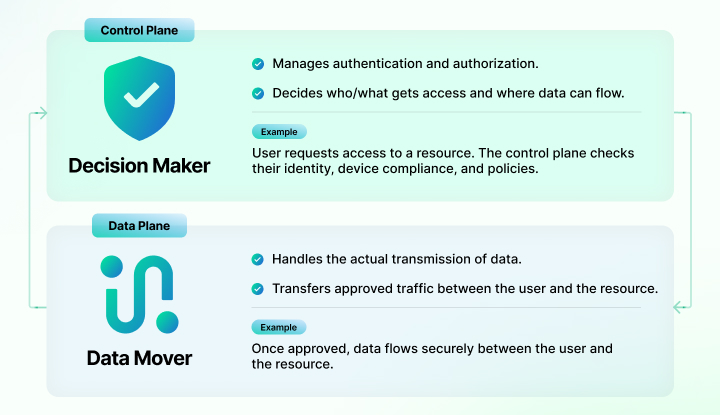
SDP separates control and data planes, creating an architecture where resources remain invisible until authenticated and authorized.
In case you were wondering The data plane handles the actual transmission of data between systems, while the control plane manages the decisions about how and where that data should flow, including authentication and access enforcement.
The tech behind SDP
- SPA or single packet authorization acts as the first line of defense. Before a resource (like a server or application) can even respond to a connection request, a cryptographically validated packet must be sent to the SDP Controller. Think of this as a digital handshake that occurs before any network port opens.
- Once SPA is successful, Mutual TLS (mTLS) takes over to ensure both endpoints—client and resource—authenticate each other. Unlike traditional TLS, which only validates the server, mTLS requires certificates for both sides. This prevents man-in-the-middle attacks and guarantees encrypted communication.
- SDP doesn’t just verify identities—it also validates devices attempting to access resources. This ensures that endpoints meet your security baseline, reducing the risk of compromised devices introducing threats.
- Traditional firewalls leave ports and protocols open indefinitely, creating opportunities for exploitation. SDP replaces this with dynamic firewall policies that open ports only when required for an authorized session.
- SDP goes beyond network access by binding user permissions directly to specific applications or services. This ensures that even authenticated users can only interact with the resources they are explicitly authorized to access.
In short;
Before: SPA ensures that unauthorized users or devices can’t even see the resource.
During: mTLS encrypts traffic, while device validation ensures the endpoint is compliant.
Within: Dynamic firewalls and application binding restrict communication to what’s necessary, reducing lateral movement and data exposure.
Phase 3 – Implement micro-segmentation
Restrict lateral movement and secure workloads by creating tightly controlled network zones. In a traditional network, once an attacker gains access to a single point—whether through a compromised device, stolen credentials, or an overlooked vulnerability—they can move laterally across the network to access other systems or data.
Micro-segmentation addresses this vulnerability by dividing your network into isolated zones. This ensures that even if one segment is breached, attackers are unable to extend their reach to other parts of the network.
To enforce this segmentation, granular policies are defined based on several factors, such as the roles of the systems, the applications they support, and the communication protocols they require. These policies dictate what each segment can communicate with and under what conditions.

For example, a web server may only communicate with a database server over a specific port, and all other access is blocked.
Software-based firewalls, deployed within each segment to enforce rules dynamically, back these policies. Unlike traditional firewalls that protect the network perimeter, these virtual firewalls operate at the segment level, continuously monitoring and controlling traffic between workloads.
Phase 4 – Continuously monitor
Monitor, assess, and respond to threats in real-time to maintain Zero Trust compliance. Continuous monitoring ensures that every interaction, device behavior, and network flow is scrutinized for anomalies, policy violations, or potential threats.
A key component of this phase is behavioral analytics, powered by AI and machine learning (ML). These systems learn the typical patterns of user, device, and network behavior and flag deviations that may indicate malicious activity, such as an unusual login location or an unexpected spike in data transfers.
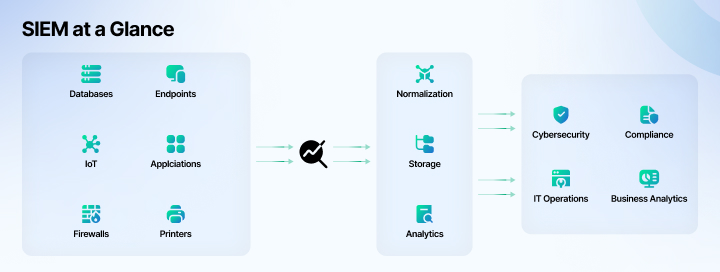
This process is supported by Security Information and Event Management (SIEM) platforms, which aggregate and correlate data from across the network.
Telemetry data collection is essential to making all this possible. By continuously gathering information from endpoints, network flows, and user activities, organizations build a rich dataset for analysis. This data forms the backbone of all monitoring systems, enabling a detailed understanding of what is happening across the network at any moment.
Phase 5 – Secure data and applications
Protect critical data and applications while automating policies to ensure real-time adaptability and scalability. Securing the data and application layer becomes paramount. Data is the ultimate target of cyberattacks, and its protection is non-negotiable. Organizations can safeguard sensitive information from interception or misuse by ensuring that all data—whether at rest or in transit—is encrypted using robust standards like AES-256.
But encryption alone isn’t enough. Tools like Data Loss Prevention (DLP) monitor data movement, ensuring sensitive information isn’t shared, exfiltrated, or misused without explicit authorization.
Applications, which serve as the interface between users and data, also require stringent security controls. Applying least privilege principles to applications and APIs ensures they operate with minimal access, reducing the risk of exploitation. Moreover, Software-Defined Perimeter (SDP) technologies like application binding further refine access control by restricting interactions to authorized users and devices.
Phase 6 – Automate policies and orchestration
Once data and applications are protected, the focus shifts to automation and orchestration to sustain and scale the Zero Trust model. As networks grow and threats evolve, manually managing security policies becomes impractical. Automating the creation, enforcement, and updating of these policies across systems like IAM, SDP, and network segmentation ensures consistent security across all layers.
Policy orchestration platforms centralize this process, allowing administrators to implement changes seamlessly.
Zero Trust Gateways, often comprising Policy Decision Points (PDPs) and Policy Enforcement Points (PEPs), streamline decision-making by automating access approvals based on pre-defined policies and risk scores. Real-time automation further enhances this by adapting dynamically to threats—whether by restricting permissions, isolating devices, or escalating suspicious activities.
When something breaks or deviates, controls act as a feedback loop, guiding you to exactly where vulnerabilities exist. And when done right, Zero Trust isn’t manual. Automation becomes the linchpin, ensuring security decisions are accurate, scalable, and consistent—without slowing down the pace of innovation.
Zero Trust doesn’t disrupt engineering; it enables it to move faster, with confidence that security is always running quietly in the background.
Sounds like a lot, doesn’t it? That’s because it is. But let me simplify it for you.
Working in cohesion with tech
Here’s a breakdown of how responsibilities are divided—what you need to take care of and what the software or technology you choose will handle for you:
| What will the company do | What will you do |
| Authenticate users and devices via SPA and mTLS | Define access policies and least privilege rules |
| Encrypt traffic and isolate resources | Maintain device compliance (patches, updates) |
| Automatically enforce dynamic firewalls and access rules | Train employees in secure practices |
| Monitor and log all activities | Regularly review and refine security policies |
| Black-box critical resources from unauthorized users | Collaborate with vendors and integrate tools |
Mixing GRC practices with cybersecurity
GRC practices and cybersecurity strategies are the backbone of a robust Zero Trust Architecture (ZTA). They’re essential for ensuring Zero Trust works effectively.
GRC lays the foundation by defining governance frameworks, risk tolerance levels, and compliance requirements. This provides the “why” and “what” behind ZTA policies—establishing rules for access, defining acceptable risk, and ensuring regulatory compliance. Without these guiding principles, ZTA would lack direction or alignment with organizational goals.
Cybersecurity practices, on the other hand, handle the “how”—implementing the technology that enforces these rules. IAM systems ensure the right people access the right resources, micro-segmentation limits lateral movement, and continuous monitoring detects potential risks in real time. These practices operationalize the policies and controls established by GRC, turning them into actionable safeguards.
Here’s Mathew Webster, CISO, Cyvergence explaining cybersecurity resilience
We’ve found you a GRC solution
If you’re looking for a GRC software solution that can help you align your organization’s governance, risk, and compliance practices with the principles of Zero Trust Architecture (ZTA), Sprinto is built to meet your needs.
While ZTA relies on cybersecurity tools to enforce least privilege access, micro-segmentation, and continuous monitoring, your GRC framework provides the foundation for these controls. Sprinto simplifies the management of governance policies, risk assessments, and compliance audits, ensuring that your ZTA implementation is not only secure but also aligned with regulatory standards and business objectives.
By automating key compliance tasks, Sprinto helps you stay audit-ready while giving you the clarity to refine and strengthen your Zero Trust policies.
With Sprinto, you can bridge the gap between compliance mandates and security execution, ensuring your Zero Trust framework is supported by a solid GRC foundation that’s easy to manage and scale.
FAQs
What is Zero Trust Architecture (ZTA)?
Zero Trust Architecture (ZTA) is a security model that assumes no user, device, or system should be trusted by default—even if they’re inside the network perimeter. Instead of relying on firewalls or VPNs to keep threats out, Zero Trust continuously verifies who is trying to access what, from where, and under what conditions. Every interaction is authenticated, authorized, and monitored in real time, minimizing the chance of unauthorized access or lateral movement within the network.
What are the 7 Core Pillars of Zero Trust Architecture?
Zero Trust isn’t just about one tool or solution—it’s a framework built around seven key pillars:
- User Identity
- Device security
- Network segmentation
- Application security
- Data security
- Visibility and analytics
- Automation and orchestration
What is the Zero Trust Architecture Pattern?
The Zero Trust Architecture (ZTA) pattern is designed to introduce just enough friction at critical points to secure systems without disrupting workflows. It ensures that every request, connection, and action is verified and authorized—not just at the perimeter, but throughout the network and application layers.
Rather than relying on traditional defenses like firewalls, Zero Trust bakes security into processes such as system access, code deployment, and data interactions. This pattern operates under three core principles:
- Verify – Every access request is authenticated based on multiple data points—user identity, device health, location, and more. This validation happens continuously, not just at login.
- Enforce – Users and systems are granted only the minimum access needed to perform their tasks, reducing the risk of lateral movement or privilege escalation. Access is temporary and dynamically adjusted.
- Assume – Zero Trust treats the entire environment as potentially compromised, segmenting resources and constantly monitoring for unusual behavior. If something seems off, the system responds immediately, preventing threats from spreading.
Heer Chheda
Heer is a content marketer at Sprinto. With a degree in Media, she has a knack for crafting words that drive results. When she’s not breaking down complex cyber topics, you can find her swimming or relaxing by cooking a meal. A fan of geopolitics, she’s always ready for a debate.
Explore more
research & insights curated to help you earn a seat at the table.