Gartner’s study reveals that 80% of compliance leaders uncover third-party risks post-initial onboarding and due diligence processes; this finding underscores the escalating complexity within vendor relationships. It emphasizes the necessity for risk management strategies when dealing with vendors.
Investing in vendor risk assessment procedures—such as enhancing procurement processes, bolstering supervision, and mitigating associated risks with vendors—can yield organizations substantial benefits; the advantages are not limited to these. To delve further into this crucial practice of vendor risk assessment, read our blog for an in-depth exploration of its significance and effective conducting methods.
Vendor Risk Assessment: A structured process to evaluate, monitor, and mitigate risks introduced by third-party vendors and partners.
Purpose: To reduce cybersecurity, operational, legal, financial, and reputational risks associated with third-party engagements.
Key Phases:
1. Selection – Initial screening based on risk
2. Onboarding – Vetting vendor controls before access
3. Monitoring – Ongoing evaluation during relationship
4. Termination – Secure offboarding and data handling
5. Incident Response – Breach impact analysis and mitigation
6-Step Vendor Risk Assessment Process:
1. Assign roles across teams
2. Define risk tolerance (risk matrix)
3. Set up tiered assessment frameworks
4. Distribute vendor questionnaires
5. Implement continuous monitoring
6. Categorize/remediate risks
When to Assess Vendor Risks?
• Onboarding
• Audits
• Periodic evaluations
• Contract renewals
• Post-incidents
• Termination
Best Practices to Assess Vendor Risks
• Define scope and tailor assessments
• Set clear response standards
• Build remediation plans
• Use real-time, continuous monitoring
• Leverage vendor risk assessment automation tools like Sprinto
Why Sprinto?
Sprinto automates vendor risk assessment by bringing structure to disorganized processes.
What is vendor risk assessment?
Vendor risk assessment refers to the process of evaluating risks that may arise from outsourcing business to third-party vendors, suppliers, and contractors. Vendor risk assessments allow businesses to understand the exposure levels associated with these third-party entities and help them gain insights into security, privacy, and other threats that could emerge when vendors are involved in handling data, business operations, or customer interactions. It gives you a comprehensive overview of potential threats that could impact the organization.
What is a vendor risk assessment process?
A vendor risk assessment reviews potential threats when engaging external partners.

The process involves five key stages:
- Selection – Initially screening to shortlist vendors with low-risk levels.
- Onboarding – Vetting vendor controls before allowing access.
- Monitoring – Regularly checking performance, contracts, and compliance.
- Termination – Securing data protection when relationships end.
- Incident Response – Determining breach impacts and developing mitigation plans.
A vendor risk assessment typically involves issuing questionnaires for vendors to detail their information security controls, data protection policies, compliance frameworks, subcontracting practices, and more. Companies may also gather financial, legal, and operational information to gauge broader business risks.
Vendor assessments help organizations assess risks that originate from vendor exposure. Security teams are able to assign risk scores and determine potential impacts across issues like data breaches, service disruptions, audits, regulations, and reputation. Initial assessments occur during vendor screening and selection. Follow-up assessments help uphold regulatory standards, meet compliance, and elude unexpected vendor-introduced threats.
Types of Vendor Risks With Examples
Vendor risks are multifaceted and can impact your operations, compliance and brand trust. Understanding the risk categories is crucial for you to build a resilient security program.
Here are the six types of vendor risks, along with examples.
1. Information Security Risk
Third-party vendors often integrate directly into your infrastructure, creating potential backdoors for attackers. A single misconfigured endpoint or delayed patch on their side can compromise your entire environment.
For example, a cloud storage provider that fails to address a known vulnerability could expose your customer database to unauthorized access.
2. Compliance Risk
Even if a vendor handles part of your business, you’re still responsible for making sure they follow the rules. If they aren’t compliant with key regulations, it could impact your own compliance which means audit failures, fines, or legal trouble.
For example, using a healthcare software vendor that isn’t HIPAA-compliant can put your entire certification at risk, no matter how secure your internal systems are.
3. Operational Risk
Vendors often power critical operations such as payroll or product delivery. If they fail, it can directly impact your ability to serve customers or meet deadlines.
For example, if a support platform goes offline during a product launch, response times may drop and customer trust can take a hit.
4. Reputational Risk
When a vendor makes a mistake, your customers may hold you responsible. If a marketing agency leaks customer data or sends the wrong message, it reflects poorly on your brand.
5. Financial Risk
If a vendor has financial problems or goes out of business suddenly, it can disrupt your operations. For example, if your analytics provider shuts down without notice, your reporting and decision-making could be affected.
6. Strategic Risk
Over time, a vendor’s goals or direction may no longer align with yours. They might shift focus to a different market or stop supporting features you rely on. This kind of misalignment can slow you down or force costly changes.
Why Vendor Risk Assessment is Important?
Vendor risk assessments are essential for managing potential threats posed by third-party service providers. Conducting vendor risk assessments enables careful risk management when outsourcing services, sharing data, or allowing supplier network access.
With vendors taking on more sensitive functions, the regulatory landscape also emphasizes the need for effective third-party risk assessment. Assessments provide continuous visibility into vendor performance and policy changes. They help confirm that vendors uphold security and privacy standards throughout the business relationship and enable organizations to be better positioned to reduce impacts from security incidents.
Identifying and addressing risks early can protect you from financial losses associated with security breaches or operational disruptions. Hence, a proactive third-party risk assessment process is vital to promote operational resilience, business continuity, compliance with standards, data security across the vendor ecosystem, and the effective governance of third-party relationships.
Conducting vendor security assessments goes beyond spotting vulnerabilities. It presents an opportunity to initiate meaningful dialogues with vendors regarding security measures, compliance issues, and mutual expectations. By actively collaborating to mitigate the risks at hand, you fortify partnerships. This results in enhanced security and stability.
Also, check: Best vendor risk management tools in 2024
When to perform a vendor risk assessment?
Conducting regular vendor risk assessments is essential to sustain security, privacy, resilience, and compliance across all vendor relationships. These assessments provide visibility into the levels of risk over time and allow for holistic governance and tailored oversight of each individual provider. Some crucial stages that organizations should perform these risk evaluations are listed below:

During the onboarding process:
Initially, conduct a risk assessment rigorously vet inherent risks before considering bringing new vendors on board–all while maintaining alignment with your predetermined risk tolerance.
Before audits
Whether internal or external, preparing for audits warrants a vendor risk assessment to ensure compliance with regulatory requirements and align with audit expectations.
Periodic assessments
Conduct regular risk assessments throughout the lifecycle of the vendor relationships. These periodic evaluations ensure ongoing compliance, evaluate alterations in risk status—and validate adherence to agreed-upon standards.
Upon contract renewals
Before renewing contracts, it is essential to reevaluate the risk profile of your vendors. This process ensures that your vendors’ risk aligns with your evolving business needs and standards before contract renewal.
During incidents
In the event of security incidents or breaches, it is essential to perform a risk assessment. This allows you to understand the violation’s scope and determine its impact on your organization— crucial steps towards developing effective incident response plans.
During termination
When terminating a vendor relationship, it is important to conduct a final assessment. This ensures proper migration or secure disposal of sensitive data confirming adherence to contract terms.
Read more: Vendor Selection For Cloud Businesses: The Complete Handbook
Ace Vendor Risk Assessment with Sprinto
A Step-by-step Guide to Vendor Risk Assessment
It is crucial for businesses to conduct a vendor risk assessment in order to establish an assessment strategy. This ensures an understanding of vulnerabilities related to vendors. Enables organizations to create effective plans for addressing them.
Here are the 6 steps to conduct vendor risk assessment:

Step 1: Assign roles
Begin by forming a cross-functional team that includes stakeholders from various areas: risk management, procurement, IT compliance, and security operations. Each role introduces specific priorities, unifying perspectives, and expertise in the vendor risk assessment process. This collaborative strategy guarantees comprehensive coverage of potential risks tied to third-party relationships while fostering an understanding of the multifaceted aspects of vendor risk assessment.
Step 2: Define your risk tolerance
After assembling your team, thoroughly assess and define the organization’s acceptable level of risk. This critical step requires a comprehensive evaluation of different risk types: data security, financial risks, and operational risks. Implementing a risk matrix method streamlines this process.
- Calculating your risk matrix
This matrix helps you categorize critical risks: anything scoring above a 6 on our 10-point scale signals an imminent danger. It further assists in identifying risk thresholds once we establish some remediation plans, thus enabling us to assess with precision and clarity. This way, we can weigh if the benefits are worth the risks we’re taking.
Step 3: Establish vendor risk assessment process
Now that we know what risks we’re okay with, it’s time to set up our game plan for checking out potential vendors. Develop a structured and standardized vendor risk assessment process. Tailor the process to suit different vendors based on their criticality, access to sensitive data, or susceptibility to continuity events. Initiate the process with an internal profiling and tiering assessment to categorize vendors and define the type, scope, and frequency of assessment required for each group.
Step 4: Conduct vendor risk assessment questionnaires
Following this step, we distribute comprehensive questionnaires to our vendors or groups of vendors. These security questionnaires aim to gather crucial information about the vendors’ internal controls, information security practices, compliance requirements, financial stability, and third-party supplier data.
For instance, questions might revolve around the encryption methods used to safeguard data, access control measures, adherence to specific regulatory standards (such as GDPR or HIPAA), financial health indicators, and the extent of oversight on their supply chain. The choice between standardized or proprietary questionnaires relies on the organization’s preferences and prevailing industry standards.
Step 5: Implement continuous risk monitoring
Continuous risk monitoring helps you track evolving cybersecurity vulnerabilities, regulatory compliance requirements, credential risk exposures, data breaches, operational disruptions, financial instabilities, or reputational risks associated with the vendor ecosystem.
Struggling to keep up with continuous vendor monitoring? Download “The CISO’s Guide to Scaling Vendor Risk Management” for practical steps to tier vendors, automate assessments, and keep your VRM program running on autopilot—minus the manual overload.
Step 6: Categorize and remediate risks
Categorize identified risks as acceptable or unacceptable based on the organization’s risk tolerance levels. Unacceptable risks must undergo remediation before engaging with the vendor. Remediation strategies may include requesting security certifications, discontinuing relationships with associated vendors, or modifying business practices to mitigate risks.
Vendor Risk Assessment Template
A structured vendor risk assessment helps you spot red flags early and make informed decisions. Start with this ready-to-use template that covers all critical risk areas to ensure your vendors meet your standards.
Next, based on the sensitivity of information shared with the vendor, classify them as high, medium and low risk vendors.
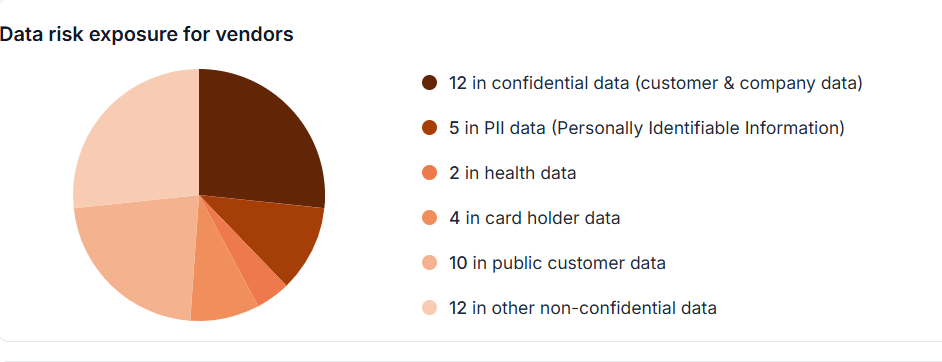
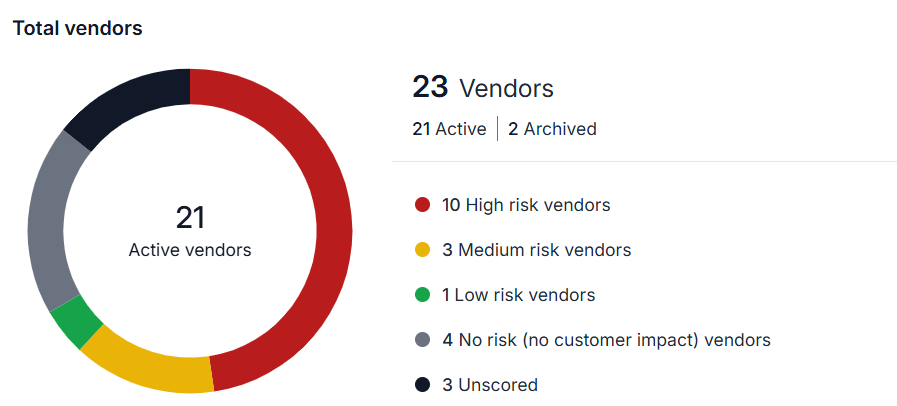
Five Best Practices for Effective Vendor Risk Assessment
Managing thirty-party vendor risks is paramount in today’s business landscape. To proactively assess and mitigate potential risks posed by vendors, implementing these five essential best practices in vendor risk assessments is crucial:

Define the scope of the assessment
- Start by recognizing the inherent risks to kick off assessments.
- Tailor assessments to focus on key areas without unnecessary scrutiny.
- For instance, concentrate on data security assessments only for vendors requiring access.
Establish guidelines and standards
- Develop questionnaires with specific answer expectations.
- Set clear standards guiding how vendors should respond.
- Make risk identification easier by providing expected answer guidelines.
Develop remediation plans
- Create a catalog of suggested actions tied to identified risks.
- Offer predefined guidance for swift and effective risk resolution.
- Simplify the risk resolution process with ready-made solutions.
Conduct real-time assessments
- Blend due diligence questionnaires with continuous monitoring for detailed insights.
- Evaluate vendors using their self-reported data and ongoing external insights.
- Gain a comprehensive view of vendor risks by adopting a holistic assessment strategy.
Leverage Technology
- Use automation tools to streamline security risk assessments, data collection, and risk management.
- Explore reliable software partners to ensure a comprehensive oversight of vendor risks.
Build an effective vendor risk management program with Sprinto
Vendor risk assessment is essential for businesses to gain insights into the potential risks associated with third parties and how best to mitigate them while saving time and money. However, maintaining a vendor list, understanding the type of data accessed by vendors, and keeping a repository of due diligence reports are arduous tasks.
Sprinto enables an efficient vendor risk management strategy.
A compliance automation solution like Sprinto helps you create a robust third-party risk assessment process while helping you swiftly expedite audit readiness to comply with relevant security frameworks. You can add vendors to the platform directly and choose the type of data the vendor has access to, and the level of risk will automatically be calculated. Due diligence reports and risk reviews can be added and maintained from a centralized dashboard.
Speak to our compliance experts today to make vendor management more efficient and tied to security compliance.
FAQs
Vendor risk assessments act as safety measures for your business partnerships. They are vital in identifying risks and vulnerabilities that may impact your operations, data security, and overall reputation. By comprehending and effectively managing these risks, you can protect your business from disruptions and financial losses.
We recommend regular assessments, particularly during new vendor onboarding and periodically throughout a vendor relationship lifecycle. Factors such as your business’s nature, the criticality of vendor relationships, and changes in the business environment can influence the frequency at which you conduct vendor risk assessments. Utilizing an automation tool like Sprinto streamlines this process, automating assessments, continuously monitoring changes, and ensuring an up-to-date understanding of vendor risks.
Here are a few questions for effective vendor risk assessment:
1. Can the vendor provide evidence of financial stability?
2. How does the vendor safeguard sensitive data through encryption and access controls?
3. Does the vendor comply with GDPR, HIPAA, or industry-specific regulations?
4. What plans does the vendor have for business continuity and disaster recovery?
5. How does the vendor handle security incidents, and do they have a response plan?
In the process of conducting vendor risk assessments, one often collects details about a vendor’s operations, security practices, compliance measures, financial stability, and subcontractor relationships. This information proves instrumental in evaluating the potential risks associated with that particular vendor. Moreover, it not only ensures alignment with your business standards but also allows for a more strategic decision-making approach towards partnerships and collaborations.
Yes. Specialized vendor risk management software and tools indeed exist. These tools enable you to automate tasks, manage data, and offer comprehensive insights into risks; these tools streamline the process of third-party risk management.
Gowsika
Gowsika is an avid reader and storyteller who untangles the knotty world of compliance and cybersecurity with a dash of charming wit! While she’s not decoding cryptic compliance jargon, she’s oceanside, melody in ears, pondering life’s big (and small) questions. Your guide through cyber jungles, with a serene soul and a sharp pen!
Explore more
research & insights curated to help you earn a seat at the table.






















