Automotive insiders know the drill too well: Scramble all resources to address the stack of security questionnaires with every new partnership. No one is spared if suppliers or OEMs are selling their products in partnerships with another automotive group.
Enter TISAX – one unified attestation to prove your resilience and security practices to new and existing partners. It replaces the evergrowing hassle of addressing individual assessments, resulting in smoother, faster trade within the industry. However, TISAX assessments are extensive and there are multiple steps like scoping, understanding requirements, and the nuances to prepare for a third-party attestation.
In this blog, we walk you through the TISAX participant handbook, detailing everything you need to know to get attested.
So, let’s get started:
Who is a TISAX participant?
A TISAX participant is any organization that has been asked by the partner or voluntarily registered to undertake the standardized TISAX assessment. However, there are two kinds of participants: passive and active.
- Active participants are the organizations that assess and validate their resilience and information security practices. These companies choose to get attested to different levels of TISAX depending on their partner’s request or their voluntary decision. Once attested, active participants can share the details of the assessment with their partners to win trust without needing to fill out individual assessment forms for each partner.
- Passive participants are companies that request a partner company to prove their resilience either by addressing their security questionnaire or through an industry-standard attestation, TISAX. A TISAX attestation streamlines the process of verifying resilience for both the organization that requests proof of resilience and the one that needs to prove it. An active participant can observe the process and findings of the audit.
For further clarity, here’s an infographic on who assumes the active participant role and which company becomes the passive participant.
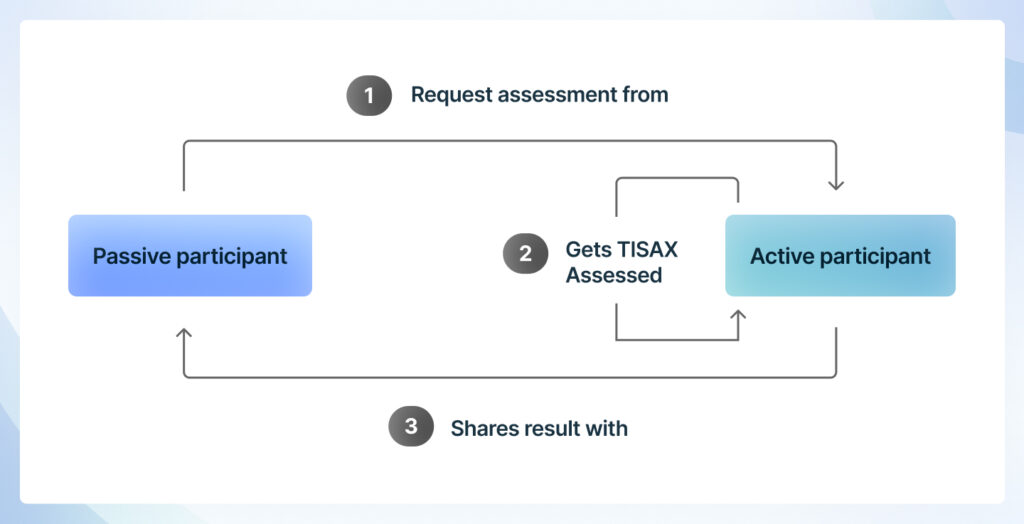
TISAX Participant’s Handbook simplified: The key steps of the attestation process
There are primarily three steps to getting TISAX assessed: navigating through the consuming registration process, assessing your security, and engaging the auditing body to validate your self-assessment. However, there are much more nuances in each step. That’s what we cover moving forward.
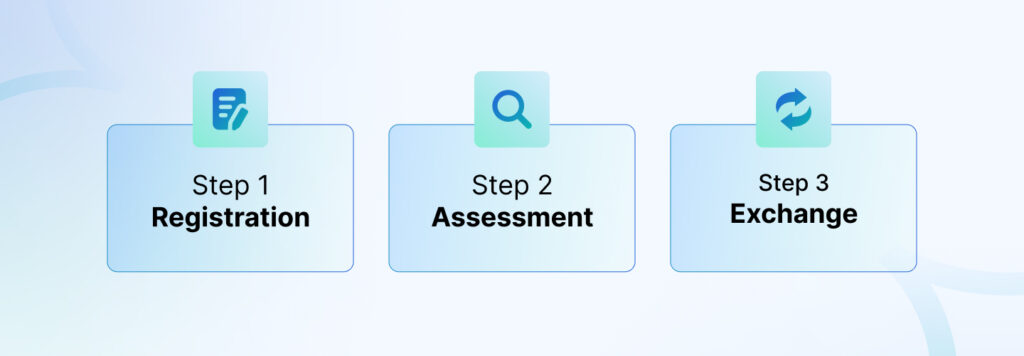
Registration
The registration process begins with signing up at the ENX portal, which asks for basic details about yourself and your company. As per the participant’s handbook, here is the information demanded at the signup:
- Your contact and billing details. This might include the billing address of your company’s office and your organization-provided phone number.
- The signup process will lead you to the terms and conditions page. It’s crucial to read and accept them before proceeding to the next steps.
- They ask you about the scope of your information security assessment.
There are three kinds of information security assessments that you can opt for. We have detailed all of these in our next section on the scope of your assessment.
Scoping
Scoping is where you define the perimeter of your assessment, which further categorizes it into different evaluation levels. Typically, there are three levels: information security assessment, prototype objectives (if that’s applicable to you as a vendor), and data protection category. All of these might have further nuances.
Furthermore, you also need to be clear on which business units or ISMS you want to include for assessment. Typically, the units and parts of your organization that handle or will handle your partner’s information need to be covered in it.
When defining the scope of the assessment, you can either choose the standard scope approach or opt for a custom assessment.
- Standard: The standard scope in the TISAX assessment will cover a predefined yet broad set of criteria generally applicable across the automotive industry. This typically includes evaluating information management processes and data protection of personal, financial, and intellectual property while involving process areas like IT and other business functions that handle sensitive information. A standard scope, by default, includes all physical locations and third-party vendors associated with your organization.
- Custom scope: Sometimes, your industry partners might require additional assessments and tailor the process better to fit their needs or your organization’s circumstances. As a result, it makes room to focus on the areas that matter the most regarding the resilience of business operations and partnerships.
Here’s how you can customize the assessment as per your needs:
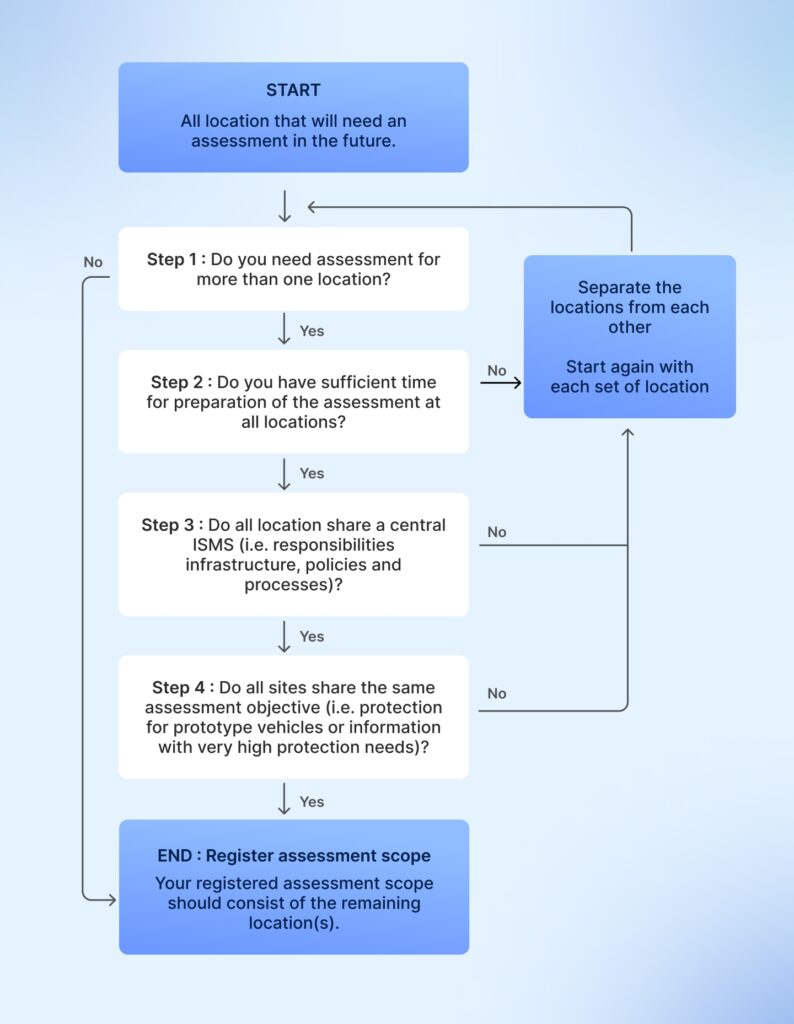
In short, you can reach a conclusion by answering these questions:
- Do you need an assessment for more than one location? If not, you need to separate the locations and get attested again for each location. If yes, proceed ahead.
- Do you have sufficient time to prepare the assessment at all locations? If not, separate the locations. If yes, move ahead.
- Do all sites share the same assessment objective (i.e., protection of prototype vehicles or information with very high protection needs)? If not, separate the locations. If yes, move ahead.
Self-Assessment
Once you’re done with scoping, you come to the self-assessment phase. Here, you will internally audit the assets and business units you declared in the scope and have the report validated by the assessor.
However, the objective of the assessment will decide your path forward, and it depends on the type of data you’re planning to handle for your partner.
For example, here are the different types of data and levels of assessment they require:
Information security assessment
| Type of assessments | Name | Description |
| Information security | High security | Choose this if you need to handle data that require high protection but not very high protection |
| Very high security | Pick this if the data you’ll process and handle will require very high protection | |
| Confidential | Choose this if the information requires very high security and tighter access controls, with privileged access limited to the intended user. | |
| Strictly confidential | Pick this if you’re handling information that requires data protection and strict access controls for high confediantiliy | |
| High availability | Pick this if the information you handle needs to be highly available to the intended stakeholders | |
| Very high availability | Pick this if the information you’re handling must be available to all stakeholders in real-time. | |
| Prototype information | Parts | Pick this if you only work with the prototyping of parts. |
| Proto vehicles | Pick this if you handle information regarding prototypes of the entire vehicle. | |
| Test vehicles | Pick this if your organization also handles test vehicles or if you need information regarding them. | |
| Proto events | Pick this if your organization only handles prototypes during events, expos, etc. | |
| Data | Personal data | Data protection according to Article 28 (“Processor”) of the European General Data Protection Regulation (GDPR) |
| Special data | Data protection according to Article 28 (“Processor”) of the European General Data Protection Regulation (GDPR) with special categories of personal data as specified in Article 9 of the GDPR |
Paying the Fee and registering on the ENX portal
TISAX attestation charges a fee for all businesses. The active participant has to endure the cost for the process.
As the assessment varies based on your assessment level and other factors, the fee for the certification also changes depending on the intensity of the audit and attestation.
Generally, TISAX Attestation can incur the following costs:
- Registration fee: Companies usually pay around 400-700 Euros for ENX registration.
- Assessment fee: This is the major component of the total breakdown. For small to medium-sized businesses, the fee can vary between 5k and 15k Euros. For larger corporations, the pricing could be custom based on size; however, it’s estimated to be around 15000 Euros and more.
- Annual label fee: Companies also need to incur an annual label fee of around 1,000 to 3,000 Euros, depending on their size and other factors.
How to prepare for TISAX Assessments? Notes from the participant’s handbook.
Detailed self-assessment and gap analysis
Before a formal auditor attestation, you must rigorously assess readiness against security guidelines that align with ISO/IEC 27001. It would help you see how your organization is against which controls and where you need to put more work. Assess and revise policies when needed and internally assess until you score high against the requirements.
If you’re already ISO/IEC27001 compliant, you’ll most likely score high on TISAX self-assessments as well.
Fastrack your ISO 27001 compliance
Engage your team
Prepare your team for upcoming assessments. This might include collecting evidence from the stakeholders and functions like HR, procurement, and operations of performance and implementation of security controls. Identify the gaps and train the team on aspects of information security, clearly outlining their role and requirements to meet security standards.
Conduct regular audits and training to help your team understand the requirements for complying with TISAX.
Choose the Right Assessment Partner and Conduct a Pre-Assessment
Consult and engage a TISAX-accredited auditor who understands organizations like yours in terms of size and niche. Work with them to consider pre-assessment and mock runs before the final assessment for attestation. This will help you gauge your preparedness. Once done, you can self-assess or work with an auditor before submitting yourself for validation.
Once you have the scores against all the questions stated for TISAX assessments, you can gauge your readiness with a simple visual:
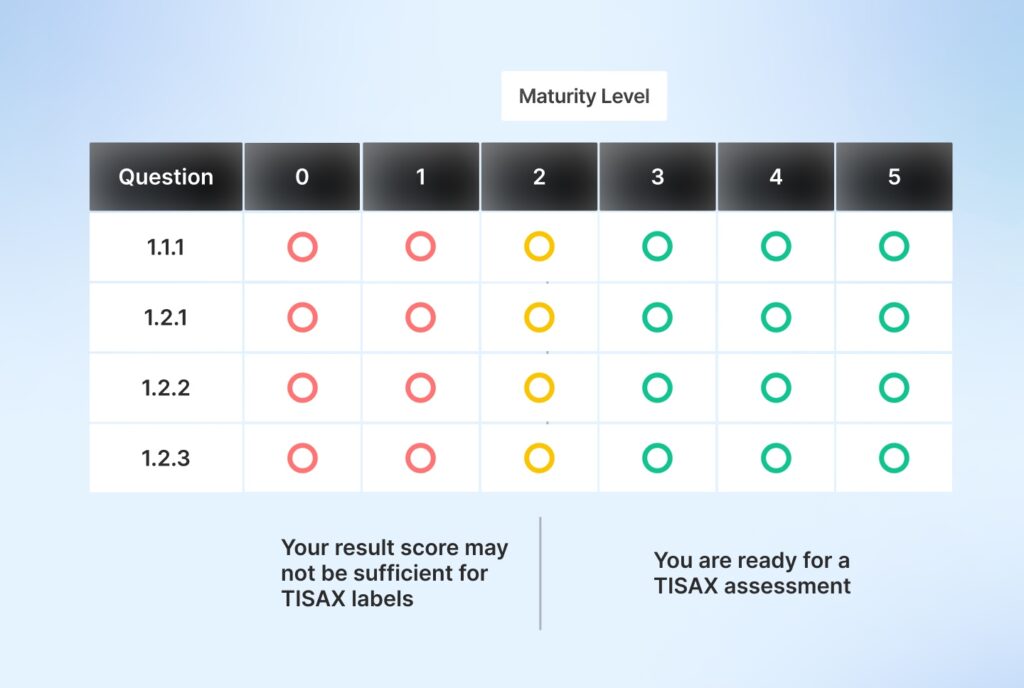
Get TISAX attested
Once you and your partner audit consultant are confident, you can begin the TISAX assessment. The process starts with kick-off meetings with you and the TISAX auditor. The auditor will validate your self-assessment with the documents, policies, and other information you submit. This usually includes on-site inspections, video meetings, and on-site interviews.
Post this; your assessor will provide the findings and an interim TISAX assessment report. You can review your score and offer further clarification and feedback if something has been misinterpreted.
As a final report, your assessor would further validate if the concerns were resolved and communicate the final report.
Get TISAX ready with Sprinto
Automatically map TISAX criteria to controls using Sprinto’s responsive integrations, and monitor these controls continuously to capture audit-ready evidence without impeding your critical bandwidth. Sprinto’s comprehensive controls library and pre-configured policies simplify compliance by ensuring extensive coverage and eliminating the complexity of tracking compliance manually. With continuous control monitoring and automated evidence collection, Sprinto makes your journey to readiness and attestation seamless. Plus, with guidance from our expert compliance advisors, you’ll be well-prepared for your attestation assessment.
From defining processes and policies to getting all employees under compliance, each sufficiently trained, Sprinto was instrumental to our success. The platform would pull all the data, and all l had to do was categorize it: it was all straightforward.
Shreerang Gondegaonkar, CTO, Gift
Get a wingman for your compliance
FAQ
What is the scope of the TISAX assessment, and how does it differ from ISO 27001?
TISAX assessments focus on information security within the automotive industry, aligning with VDA ISA requirements. Unlike ISO 27001, which provides a general framework for information security applicable across various industries, TISAX includes additional criteria for prototype protection and third-party data handling specific to automotive sector needs.
How does TISAX handle data privacy, especially considering varying global regulations like GDPR?
TISAX assessments strongly emphasize data protection to ensure compliance with stringent industry-specific privacy standards, including the GDPR. The assessment evaluates the implementation of necessary controls around personal and sensitive information, particularly in cross-border data exchanges within the automotive supply chain.
Can TISAX certification be extended to subcontractors, and what is the process?
Subcontractors involved in the value chain of TISAX participants must adhere to the same security measures, especially if they handle sensitive information. However, subcontractors must undergo their TISAX assessment rather than being covered under the primary contractor’s certification. This ensures that all parties maintain consistent security standards.
What are TISAX labels, and how are they used?
TISAX labels are the outcomes of a successful TISAX assessment, indicating the level of compliance a company has achieved concerning the specified requirements of the VDA ISA catalog. These labels serve as evidence of compliance and are recognized by all participating companies within the TISAX community, facilitating trust and simplifying the exchange of sensitive information among automotive industry players.
Virgil
Virgil is a marketer at Sprinto who combines his media savvy with his cybersecurity expertise to craft content that truly resonates. Known for simplifying complex cybersecurity and GRC topics, he brings technical depth and a storyteller’s touch to his work. When he’s not busy writing, he’s likely exploring the latest in cybersecurity trends, debating geopolitics, or unwinding with a good cup of coffee.
Explore more
research & insights curated to help you earn a seat at the table.


















