90% of phishing attacks, yes, you read that right, incorporate elements of social engineering, revealed Microsoft. Simply, social engineering is the art of manipulating people to give them what they want. So instead of hacking systems, they hack into humans, first by winning their trust, then exploiting it for their purpose, and then clearing their tracks. Given that 95% of security breaches stem from human error, hacking into humans is a pretty efficient technique.
But how can you prevent your employees from succumbing to such social engineering attacks?
That’s precisely what we discuss in this blog. We will break down the science behind social engineering, how attackers use it, and how you can reverse-engineer your defenses to bolster your resilience against it.
TL;DR
| Social engineering exploits elements of human psychology such as trust in authority, reciprocity, and community belonging to manipulate victims. |
| MFA enhances security but remains vulnerable to human-centric tactics like SIM swapping and MFA fatigue, allowing attackers to circumvent these measures. |
| Combating threats requires ongoing, interactive training that addresses psychological vulnerabilities and deploying technical defenses like email filtering and network whitelisting. |
The science behind social engineering attack – How they bypass human defenses
Every social engineering attack starts with one motive—to disrupt the sense of reality. To do that, threat actors deploy techniques ranging from urgency, wielding authority, weaponizing trust, and blackmailing. By understanding each of these, we can create better awareness and training programs and even deploy technical defenses that guard the human links in the first place.
Here’s the anatomy of social engineering attack:
1) Automatic deference to authority
It is a universal truth that people are more likely to comply with requests from figures of authority. Such instances shortcircuit our thought process, and threat actors know it. Thus, they impersonate authority figures to exploit our automatic deference to it.
For example, an attacker can impersonate a high-ranking executive or the CEO of the company they work for and leverage emails, Slack, or even phone calls to request sensitive information like customer data or, worse, make payments on fraudulent links. The employee in question might comply without asking further questions or minimal investigation.
2) Reciprocity
Reciprocity is embedded in all of us as social etiquette, and we should repay people in kind for the favors other people do for us. Seemingly good deeds are reciprocated, and threat actors use this to solicit small favors from unaware victims that turn into an incident. This technique also exploits a common belief – that people who do good to us don’t harm us.
For example, a threat actor might pose as a vendor and offer a free software upgrade or exclusive access to a feature. In return, they would architect the process to have their victims download a malicious asset, run malicious code, or receive sensitive information.
3) Community mirroring
In this classic phishing technique, threat actors build fake profiles on social and professional platforms and then build a following of the same circle as their victims to blend into the environment. When victims see their colleagues and friends in their network, they trust them and lower their guard around them.
Threat actors then build more rapport over time with their victims before finally leveraging it to trigger malicious activity.
For example, an attacker might build a fake LinkedIn profile, connect with the same people as their victim, engage with the same posts as their victims, and build rapport with micro-actions like commenting and complimenting their posts.
4) Exploiting the Good
This is a technique where instead of impersonating a figure of authority or friend, they exploit the rewards of committing good gestures, like helping someone, donating to charity, or receiving seemingly small, harmless favors. They would engage their victims with micro-favors, gradually building towards the exploit.
For example, a threat actor might first ask someone to commit a seemingly innocent action like signing a petition for cybersecurity awareness. Later, they leverage this consistency by asking some of them to participate in a security check, which involves disclosing sensitive details like IP addresses and network keys that they need to advance their attack.
5) Scarcity
This is a type of phishing scam that manipulates human psychology by embedding a sense of urgency and exclusivity around a limited offer. For example, a threat actor that gets access to the email IDs of your employee might receive a phishing email that they are offering a one-time opportunity to sign up for a limited access license of software. The email prompts them to quickly claim the license by entering their login credentials on a malicious website. The urgency and exclusivity of the offer might prompt some people to act hastily, bypassing logic and caution.
But MFA is the silver bullet against such attacks, right?
Yes and no! More than 78% of companies globally have used MFA to protect their critical systems and data. Yet, 28% of them are breached in some way.
MFA is great at bolstering your defenses against such threats, but it is not the silver bullet for security. The same social engineering attacks architectured to compromise user credentials can be tweaked to bypass MFA using techniques like SIM Swapping, leveraging user fatigue, token theft, consent phishing, and more.
Here is how:
MFA fatigue attack
Also known as prompt bombing, it is a well-architected social engineering attack in which adversaries pose as an organization’s IT team or a vendor support official to gain access to a particular system.
The attack pathway commonly feels like this: engineer scenarios where the user is fatigued with repeated MFA prompts until they authenticate the login out of alert fatigue. In some instances, the attack is followed up with emails or phone calls demanding access to stop it. Users with little to no time to spare from work provide the MFA authentication without investigating the scenario to resume their daily tasks.
SIM Hacking
In this attack, cybercriminals manipulate the telecom operator to access the victim’s SIM card. They might use community mirroring to build rapport with the individual, gain their sensitive information like date of birth, name, and address, and then leverage it to authenticate the identity verification process by their telecom operator. When combined with further social engineering tactics like urgency or reciprocity, they might successfully have users unknowingly authenticate the final transfer of SIM by providing their OTP or compelling telecom operators to accelerate the process and bypass specific security measures by citing an emergency.
Once they gain access to the SIM, they can bypass MFA-protected accounts of the individual, such as their emails, work accounts, and more.
Token Theft
Instead of directly demanding users authenticate their MFA bypass, attackers here use a combination of social engineering techniques, such as reciprocity and authority, to gain access to their MFA tokens. Once done, attackers further infiltrate their systems for a full takeover, escalating their privilege with each breach.
Machine-in-the-Middle (MitM) Attacks
In these scenarios, threat actors may use social engineering tactics to win trust and direct users to act on a legitimate vendor or a service portal. However, when done through the link they provide, they get a chance to add an observation layer in between, which enables them to steal any session tokens and cookies that they further exploit to take over the account entirely.
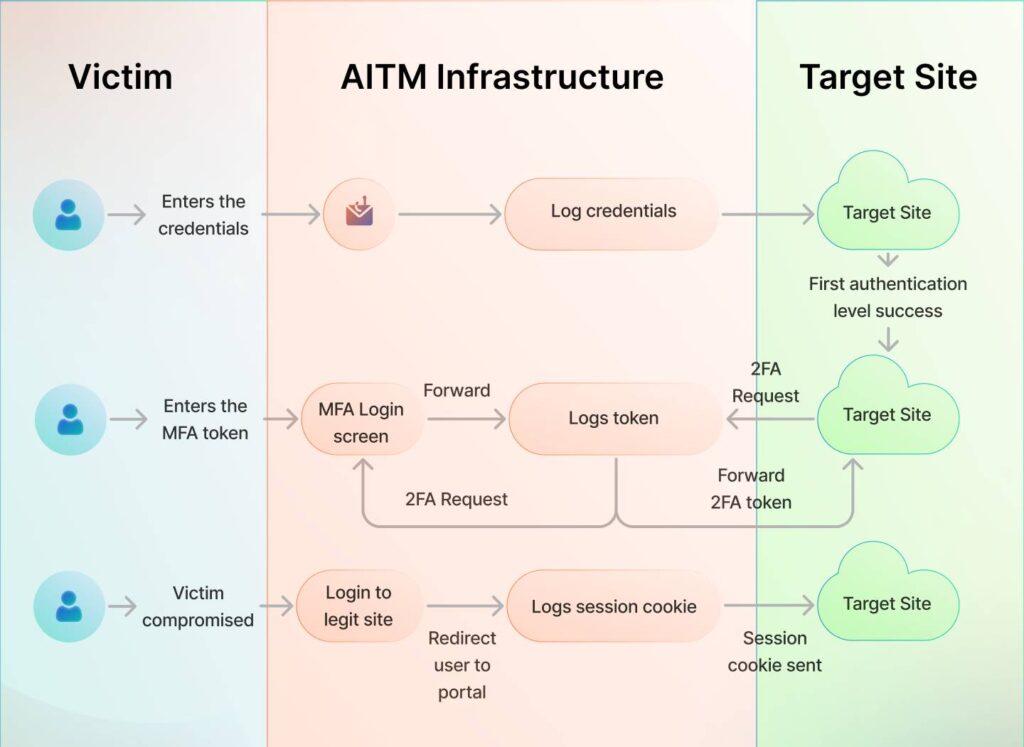
The method has a high success rate as it’s difficult to detect even for a trained eye.
How can you bolster resilience against such social engineering attacks?
To truly mitigate threats, we must enhance our greatest and first line of defense—people—through approaches that go beyond mere technical measures.
We need to approach training the right way. This entails tailored, retention-focused exercises and iterative phishing simulations that identify and target your team’s most probable vulnerabilities.
1) Retention-focused training
One-off, isolated training efforts don’t translate into long-term employee retention of crucial security fundamentals. For example, let’s look at the forgetting curve researched by Hermann Ebbinghaus; we can see how humans quickly pick up concepts and forget without repeated retention-focused reinforcement.
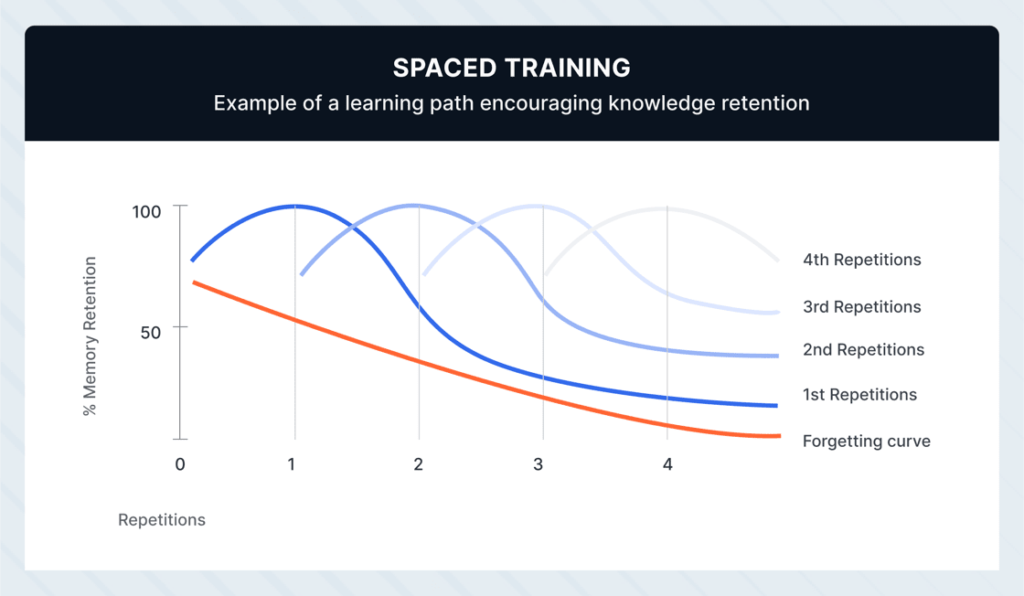
To bolster our first line of defense against such complex phishing attacks, one-off training must replace periodic, interactive training sessions that reinforce concepts over time.
Most of the time, security is about discipline and processes around crucial activities that you do continuously. These include common things such as how you onboard, how well you train them, or how you just push code to production.
Girish Redekar, Co-Founder at Sprinto
2) Targetted phishing simulation
Relying on generic phishing simulations that don’t iterate over scenarios with increasing complexity can skew an organization’s sense of defense. Simulations might observe low click rates, but they might not reveal how well the resilience fares against the complexity of the attack. As social engineering and techniques deployed by threat actors advance, phishing simulations also need to capture the complexity.
To make our phishing simulations more effective, the NIST phish matrix can help make it iteratively challenging.
The matrix takes the characteristics of a social engineering attack and scores a phishing simulation complexity based on it.
Here’s how:
| Premis alignment | Detection difficulty | Complexity of cues | Detection difficulty | Cognitive tactic | Action impulse | Final score |
| Mimics a Workplace Process | High | Spelling and grammar errors | Low | Fear of consequence | High | Medium |
| Has Workplace Relevance | Medium | Lack of signer details | High | Loss of money/reputation | High | High |
| Aligns with other situations or events | High | Generic greeting | Medium | Loss of coupon offer | Low | Medium |
3) Technical controls
Bolstering human defenses against such attacks is a big part of the puzzle. However, technical controls such as implementing SMPTP spoofing or email filtering can complete the loop and enable humans to be more effective at guarding themselves.
Here are some technical controls to bolster resilience against social engineering attacks:
- Email filtering methods such as SPF (Sender Policy Framework,) DKIM (DomainKeys Identified Mail,) and DMARC (Domain-based message authentication) can help secure email domains from unauthorized usage, which is a common tactic in phishing and spoofing attacks as the spoof emails to assume the position of authority or familiarity to build trust.
- Disabling HTML emails for key executives. High-ranking executives and decision-makers are often targets of phishing attacks. Threat actors use HTML emails to appear legit, trustworthy, and visually appealing. Allowing only text-based emails for key accounts or as a company policy can help stop such attacks in their tracks.
- Installing browser-based plugins can control and limit what content gets executed within a browser. These plugins can scan URLs for SSL certificates, trigger warnings to prevent users from revealing credentials on fake websites, and prevent malicious scripts from running in the background.
- Installing organization-wide web proxies and DNS filtering to monitor traffic, detect malicious activities, and block content that does not comply with the organization’s security policy.
- Whitelisting applications and networks (TCP/IP) can enhance resilience against social engineering threats and systems like PoS and terminals by allowing only pre-trusted applications to run or restricting access to trusted network sources. This minimizes the risk of connecting to malicious networks or running scripts that connect to such servers.
- Encrypting backups and sensitive data can help prevent data loss even in a case of active exploit or incident by rendering data captured by threat actors unusable.
Final thoughts…
Even though social engineering attacks have advanced in complexity in their capabilities to exploit nuanced vulnerabilities of human psychology, they can be prevented. However, a blended approach that caters to every link in the chain is required to counteract such attacks effectively. Humans can be the weakest link or the strongest defense, depending upon the security culture and policies an organization develops.
It’s time to move away from checkbox exercises to manage human risks and adopt more nuanced approaches, like reinforced training and targeted phishing simulations, to make employees more capable of identifying and dodging a complex social engineering attack.
By combining human resilience with technical controls like domain filtering, encryption, and anti-malware, we can drastically reduce the chances of such an attack and contain the damage in the event of a breach. Together, these measures fortify organizations against the evolving landscape of social engineering threats.
Bolster your resilience with Sprinto
Sprinto is a GRC automation tool that can quickly help you comply with information security standards and implement technical and non-technical, organization-wide controls that bolster your resilience.
With Sprinto, you can leverage pre-built, customizable policy templates baked into the platform, enabling prompt enforcement of security policies. You can also directly map controls to criteria right from the dashboard and monitor control performance with Sprinto’s automated continuous control monitoring.
Curb security and compliance drifts automated, smart alerts, and launch mitigation workflows from the platform.
With Sprinto, you can take your security program even a step further by prioritizing and right-sizing risks that matter most, enabling you to mitigate threats with focus and precision as you triage risks from an in-built library of industry-benchmarked risks.
To close the loop, Sprinto comes with out-of-the-box, customizable training modules that you can launch at a set frequency to train your teams against the threats that pose the most significant risk to your business.
Comprehensive Risk Monitoring & Mitigation
FAQ
What is social engineering?
Social engineering is the psychological manipulation of people into performing actions or divulging confidential information. It’s a type of confidence trick used for information gathering, fraud, or system access. Unlike traditional hacking, which involves breaking into a system technologically, social engineering exploits human psychology.
What are common types of social engineering attacks?
Phishing involves sending fraudulent emails or messages that mimic reputable sources to trick individuals into revealing personal information or installing malware. On the other hand, Baiting entices users with something appealing, like a free download, which harbors malicious software. Pretexting employs fabricated scenarios to engage targeted victims, increasing the likelihood they will divulge sensitive information or permissions. Lastly, tailgating occurs when someone without proper authentication follows an authorized individual into a restricted area, bypassing security measures.
Virgil
Virgil is a marketer at Sprinto who combines his media savvy with his cybersecurity expertise to craft content that truly resonates. Known for simplifying complex cybersecurity and GRC topics, he brings technical depth and a storyteller’s touch to his work. When he’s not busy writing, he’s likely exploring the latest in cybersecurity trends, debating geopolitics, or unwinding with a good cup of coffee.
Explore more
research & insights curated to help you earn a seat at the table.