Ransomware is no longer a fringe cybercrime—it’s a multi-billion-dollar industry growing alarmingly. With Ransomware-as-a-Service (RaaS) lowering the barrier to entry for cybercriminals, even less sophisticated actors can launch high-impact attacks that paralyze businesses overnight.
The ransomware prevention market is expanding just as rapidly. In 2023, it was valued at $28.49 billion, growing to $32.25 billion in 2024, and is projected to reach $69.88 billion by 2030 at a CAGR of 13.67%.
The response? Soaring cybersecurity investments. Gartner predicts cybersecurity spending will jump 15% in 2025, from $183.9 billion to $212 billion. Despite the growing spending, ransomware continues to evolve, bypassing traditional defenses with double and triple extortion tactics.
TL;DR
| Ransomware is malicious software that encrypts files, locking businesses out of their data until a decryption key is provided—often for a hefty ransom. Paying doesn’t guarantee recovery and can lead to repeat attacks. |
| Ransomware detection is critical, as modern attacks bypass traditional antivirus. Organizations need real-time monitoring, anomaly detection, and strict access controls to spot and stop threats before encryption begins. |
| A ransomware incident can cause severe financial, legal, and reputational damage. Compliance frameworks help set security baselines, but resilience requires proactive defenses, employee training, and automated security practices to minimize risk. |
What is ransomware?
Ransomware is malware designed to encrypt files or lock systems, rendering them inaccessible until the victim pays a ransom. It is among the most disruptive and financially damaging cyber threats, often targeting businesses, critical infrastructure, and government entities. Ransomware attackers typically demand payment in cryptocurrency, making transactions difficult to trace.
How does ransomware happen?
Ransomware doesn’t strike at random—it exploits weaknesses in your operating systems, processes, and people. Attackers leverage a combination of human error, unpatched vulnerabilities, and misconfigurations to gain entry, execute malicious payloads, and encrypt critical data.
Phishing and social engineering
Most ransomware attacks start with you or your employees receiving a malicious email. Phishing emails are designed to look legitimate, often impersonating vendors, executives, or IT teams, and contain links or malicious attachments.
How does it work?
- You click a link or download an attachment.
- A hidden script (macro, JavaScript, or PowerShell) runs in the background.
- The ransomware payload is downloaded and executed.
- Files are encrypted, and your system is locked.
Exploiting unpatched vulnerabilities
Ransomware groups scan for outdated software, misconfigured servers, and exposed services to break into networks. If you haven’t patched a known vulnerability, attackers can exploit it to gain full system access and deploy ransomware remotely.
How does it work?
- Attackers scan your systems using tools like Shodan.
- If they find an unpatched vulnerability (e.g., EternalBlue for SMB), they exploit it to gain entry.
- The ransomware payload is delivered, and your network is compromised.
Compromised credentials and RDP attacks
If your Remote Desktop Protocol (RDP) is exposed to the internet, it’s a prime target for ransomware gangs. Weak passwords and leaked credentials make it easy for attackers to gain unauthorized access.
How does it work?
- Attackers brute-force or use stolen credentials to log in to your RDP.
- Once inside, they escalate privileges, disable security tools, and deploy ransomware.
- Your entire system is encrypted before you realize what’s happening.
The reason it works is because many RDP instances lack Multi-factor authentication or MFA and passwords are often weak or reused.
“We have seen the success of attacks against MFA-protected accounts increasing over the past couple of years.”
The National Cybersecurity Centre
Great advice adds up. Get more from the brightest minds in GRC — join now
Supply chain attack
Even if your security is strong, your vendors and software providers might be the weak link. Attackers compromise trusted software updates to distribute ransomware without raising alarms.
How does it work?
- Attackers infiltrate a software vendor’s system.
- They inject ransomware into a legitimate software update.
- When you install the update, ransomware spreads across your network.
Malvertising and drive-by downloads
Sometimes, all it takes is visiting the wrong website. Attackers use compromised ad networks to deliver ransomware payloads through legitimate-looking ads.
How does it work?
- You visit a website with an infected ad.
- The ad executes hidden JavaScript or exploits a browser vulnerability.
- Ransomware is downloaded in the background without your knowledge.
Here’s where things get a little scary because no interaction is needed—just loading the page is enough.
Compromised managed service providers or MSPs
If your business relies on an IT service provider, their systems could become a ransomware entry point. Attackers compromise MSPs to infect multiple clients at once.
How does it work?
- Attackers gain access to an MSP’s remote management tools.
- They push ransomware to all connected client systems simultaneously.
- The attack spreads across multiple businesses in one move.
The consequences of ransomware extend far beyond data encryption and ransom demands, affecting your organization’s bottom line, reputation, and legal standing.
The Impact of ransomware on businesses: Financial, reputational, and legal consequences
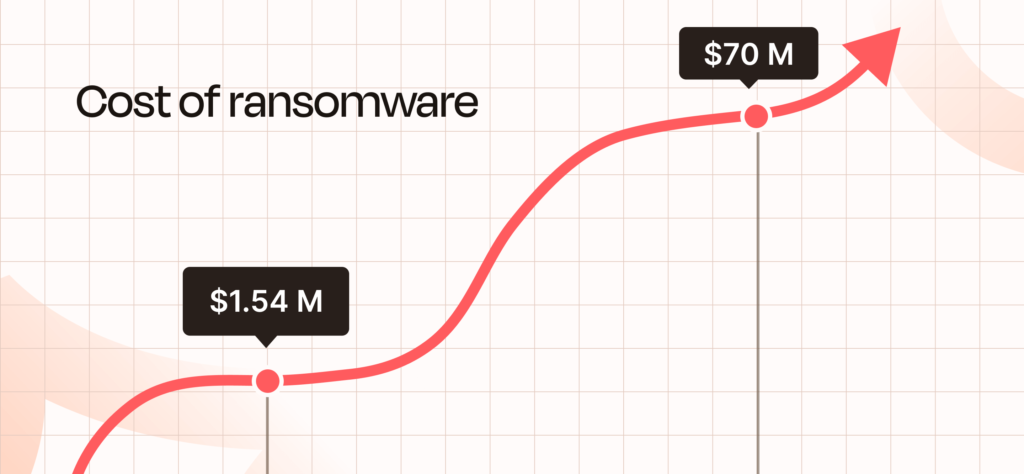
Ransomware attacks are financial black holes, with costs piling up long after the breach. IBM’s 2023 Cost of a Data Breach Report estimates the average total cost of a ransomware attack at $4.45 million—even when no ransom is paid. When payments are made, the numbers are staggering: the average ransom in 2023 was $1.54 million, with some exceeding $10 million. The Kaseya VSA attack set a record with a $70 million ransom demand.
Few incidents underscore this impact better than the Colonial Pipeline attack. In May 2021, a single ransomware infection led to fuel shortages across the U.S. East Coast, triggering panic-buying, price surges, and federal emergency declarations. The attack exposed how ransomware can cripple economies and threaten national security.
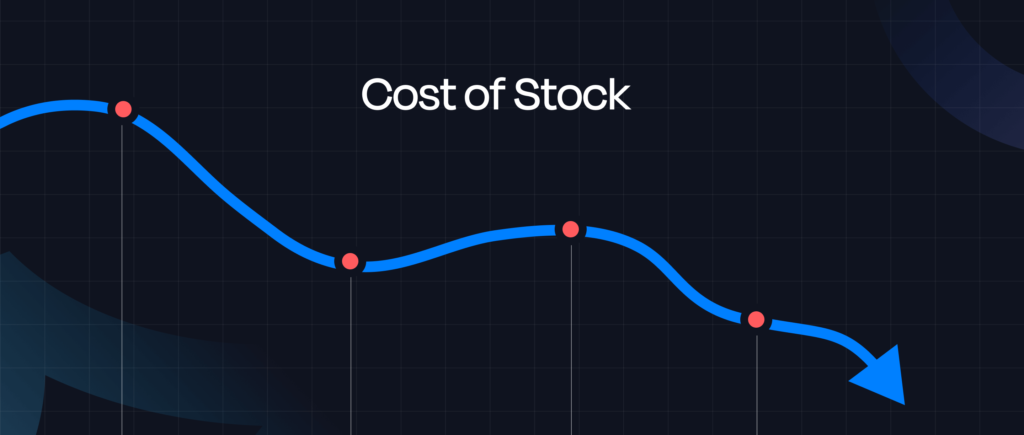
For publicly traded companies, ransomware often wipes out market value. The Equifax breach caused a 60% stock drop, erasing billions, while Maersk lost $300 million after NotPetya disrupted global shipping. Companies also face regulatory fines—British Airways paid $25 million for exposing 400,000 records, while Marriott International paid $23.8 million after a $339 million record breach.
The Colonial Pipeline attack was a turning point, prompting the U.S. government to launch stopransomware.gov and establish the Joint Ransomware Task Force with the FBI. These efforts aim to improve federal response, enhance information sharing, and strengthen cybersecurity across critical sectors.
The question that remains, is it possible to not be attacked? Yes, and No. You see, preventing ransomware is a mix of technology, processes, and human vigilance. Firewalls, endpoint detection, and offline backups are essential, but they won’t help if an employee falls for a phishing email or an unpatched system remains exposed.
How to prevent a ransomware attack?
The best defense for ransomware prevention is layered security, combining technical safeguards, strict access controls, and employee awareness to reduce the attack surface.
Patch management
Many ransomware attacks don’t rely on tricking users—they exploit unpatched vulnerabilities to gain access. Attackers scan for outdated software, weak remote access configurations, and exposed services to find an entry point.
Best practices:
- Automate patching for OS, applications, and firmware to eliminate known vulnerabilities.
- Prioritize high-risk CVEs (Common Vulnerabilities and Exposures) used in ransomware attacks.
- Monitor threat intelligence feeds to stay ahead of emerging exploits.
Backups
If ransomware does get in, your ability to recover without paying depends on reliable, protected backups. Attackers know this, which is why modern ransomware actively targets backups first.
Best practices:
- Follow the 3-2-1 backup rule (3 copies, 2 different media, 1 offsite).
- Use immutable storage to prevent ransomware from modifying or deleting backups.
- Regularly test restoration processes—a backup is worthless if it can’t be restored quickly.
Access controls
Ransomware spreads faster when users have excessive access. If an attacker compromises an admin account, they can encrypt everything. Implementing least privilege access and network segmentation limits the damage.
Best practices:
- Enforce least privilege – Users should only have the access necessary for their role.
- Restrict admin rights – Remove local admin privileges from endpoints.
- Segment networks – Keep critical systems isolated from general workstations.
Endpoint and network security
Traditional antivirus alone won’t prevent a ransomware. Modern attacks use fileless execution, obfuscation, and encryption to evade detection. Businesses need advanced security solutions that detect suspicious activity in real time.
Best practices:
- Deploy Endpoint Detection and Response (EDR/XDR) to monitor and stop ransomware before execution.
- Use DNS and web filtering to block malicious phishing and payload delivery sites.
- Enable network segmentation to prevent ransomware from spreading laterally.
Employee training
Even the best security tech won’t stop ransomware if an employee clicks the wrong link. Phishing remains the #1 initial attack vector for ransomware, meaning human error is often the weak link.
Best practices:
- Conduct regular phishing simulations – Employees should practice spotting fake emails.
- Train staff on suspicious activity – Employees should report unusual login requests, unrecognized file encryptions, or sudden system slowdowns.
- Enforce security hygiene – Require strong passwords, MFA, and strict access policies.
Zero Trust
No system is 100% secure. A zero-trust architecture assumes that attackers are already inside and enforces continuous authentication and strict access control. Ransomware operators often use stolen credentials to access networks without triggering alarms. Zero Trust shifts security from “trust but verify” to “never trust, always verify.”
Compliance and ransomware; a baseline not a shield
Compliance isn’t security, but it ensures you have the foundational measures needed to build real security on top of it. Regulations like GDPR, CCPA, HIPAA, and PCI DSS don’t stop ransomware—they set minimum standards for data protection, access controls, and incident response.
Take GDPR, for example—it mandates encryption, breach notifications, and data minimization, but it doesn’t actively prevent ransomware infections. Similarly, HIPAA requires healthcare organizations to secure patient records, but without proactive threat detection and ransomware-specific controls, compliance alone won’t stop a breach.
Where compliance helps is in forcing businesses to implement structured security measures—like regular risk assessments, access controls, and backup strategies—that reduce ransomware’s impact. A company that follows NIST CSF or ISO 27001 is better positioned to detect, contain, and recover from an attack than one that only meets the bare minimum legal requirements.
To be fair, security is never-ending. You cannot let your guard down, so it is best to automate tasks like compliance so your humans can take care of the bigger picture.
How can Sprinto help with cybersecurity and compliance?
Sprinto helps businesses achieve continuous compliance with frameworks like ISO 27001, SOC 2, GDPR, HIPAA, PCI DSS, and more. It ensures that key security controls are in place to mitigate risks, including those posed by ransomware.
With automated monitoring, real-time alerts, and policy enforcement, Sprinto helps organizations move from a compliance-driven mindset to a security-first approach that proactively addresses vulnerabilities.
- Automated risk assessments
- Real-time threat monitoring
- Access control and least privilege enforcement
- Data backup and recovery
- Employee training and awareness
- Continuous compliance monitoring
Wrapping up
Ransomware attacks are growing in scale and impact, costing businesses millions in ransom payments, downtime, and legal penalties. While compliance frameworks like GDPR, CCPA, and HIPAA help establish security baselines, they don’t stop attacks. Proper protection requires layered defenses, including patch management, backups, access controls, employee training, and continuous monitoring.
Frequently Asked Questions
What are the most common ransomware variants, and how do they work?
Ransomware variants come in many forms, but they all aim to encrypt data and demand payment. Locker ransomware locks users out of their entire system, while crypto ransomware encrypts files and demands a decryption key. More advanced versions use double or triple extortion, threatening to leak stolen data if the ransom isn’t paid. The best defense is a proactive approach, including security software, access controls, and regular security patches to reduce vulnerabilities.
What should I do if I receive a ransom note after a successful attack?
If you’re the victim of ransomware, do not immediately pay the ransom. Disconnect infected systems to prevent further spread, notify law enforcement, and report the malware infection to cybersecurity experts. Investigate ransomware detection tools that may help recover encrypted files and assess if backups are available. Paying the ransom does not guarantee access to your data and can encourage further attacks.
How can businesses improve their security posture to prevent ransomware incidents?
A strong security posture requires a multi-layered defense. This includes security software for threat detection, continuous monitoring, strict access controls, and endpoint protection. Organizations should also focus on employee training to prevent a phishing attempt from leading to a ransomware infection. Regularly applying security patches ensures that attackers don’t exploit known vulnerabilities.
Can law enforcement help after a ransomware incident, and should businesses report attacks?
Yes, reporting ransomware incidents to law enforcement is crucial. Agencies like CISA, the FBI, and Interpol track ransomware groups and may assist in recovering encrypted data or disrupting attacker operations. Even if a successful attack occurs, reporting it helps authorities identify ransomware variants and prevent further damage. Businesses should also have a proactive approach, such as ransomware detection tools and incident response plans, to minimize downtime and losses.
Heer Chheda
Heer is a content marketer at Sprinto. With a degree in Media, she has a knack for crafting words that drive results. When she’s not breaking down complex cyber topics, you can find her swimming or relaxing by cooking a meal. A fan of geopolitics, she’s always ready for a debate.
Explore more
research & insights curated to help you earn a seat at the table.