82% incident rate. 10.3 Billion dollars in losses. 30% uptick in phishing attempts. Need we say more? Phishing is more prevalent and harmful than we think. Yet, our attempts to curb it stay limited to one-off training and tracking vanity metrics to gauge phishing resilience.
Enter the NIST Phish scale — a simple yet effective approach to understanding why some employees fall for phishing attacks, why some don’t, and how you, as a security leader, can use these learnings to make better training programs, track the right metrics to measure org-wide resilience against phishing attacks and deploy effective playbooks to stop phishing in their tracks.
Excited? So are we. Let’s get started:
TL;DR
| The NIST Phishing Scale upgrades phishing defenses by integrating complex criteria like context and difficulty, optimizing training programs and resilience metrics. |
| The scale focuses on psychological influences and contextual triggers, helping identify why sophisticated phishing attacks deceive even vigilant employees. |
| It encourages a strategic, real-world approach to phishing simulations and continuous security training enhancements, improving organizational phishing resilience. |
What is the NIST Phish scale?
Unlike the rudimentary “click-rate” approach most organizations rely on to track the success of their security training, the NIST Phish Scale introduces critical dimensions – context and difficulty. It helps you rate your phishing simulations against factors like technical cues, social engineering, and the reality of your employees. It also helps you correctly identify what kind of phishing attacks your organization is most vulnerable to and exactly where to plug the gaps in training.
“The way most organizations measure phishing awareness is fundamentally broken. If your security team is still chasing low click rates instead of meaningful behavioral insights, you’re doing more harm than good. The NIST Phish Scale is the wake-up call the industry needs, and yet, few are listening. Let’s cut through the noise and talk about why your phishing metrics need a revolution.“
Rachna Dutta, Infosecurity Consultant, Sprinto
Why does the NIST Phish Scale matter now?
A study that surveyed 1,400 organizations revealed that 26% experienced an uptick in phishing attempts over the last year, and 88% of these organizations fell victim to ransomware in some capacity—underscoring a relation between phishing and dire consequences for the business.
The common denominator? Phishing training that operates in a vacuum. Not all phishing emails are created equal. Some are brilliantly engineered and tailored for a particular group of people, while others are generic and easy to spot. Tracking success rates of simulations without testing against complex techniques like social engineering and contextual traps that threat actors use builds a false sense of resilience.
Here’s an example: A poorly crafted phishing email with obvious spelling errors might fool only a handful of users. Meanwhile, a polished, highly contextual email that mimics legitimate internal communication might trip up even your most security-aware employees. Both click rates could be the same, but the lessons learned are vastly different.
The Phish Scale isn’t just about measuring user performance and contextualizing it. It forces organizations to ask tougher questions:
- Was the email truly challenging?
- Did users fall for it because of its sophistication or gaps in training?
- How do environmental factors, like timing or stress, play into their decision-making?
The science of the NIST Phish Scale
Phishing is not just a vulnerability — it’s a human problem. And, like all human problems, the issue stems from psychological factors. Every click on a phishing link is most likely driven by a combination of cognitive biases, stress levels, emotional triggers, and the tendency to make snap-second decisions under pressure.
It’s less of an intelligence problem and more about the external factors that shape human decisions.
So what are these factors?
These factors can be divided into four categories: premise alignment, perceived legitimacy, urgency, and diligence.
Let’s discuss them in detail:
1) Premise alignment
Premise alignment is a technique threat actors use to exploit the recipient’s routine, a recent project, a trusted contact, or job-to-do to win trust and lower their defenses. By aligning the context of the email with familiar cues, they mimic their reality to appear more legitimate and evade suspicion. This tactic uses a typical human trait–trusting what seems familiar.
For example, a threat actor targets a project manager at a construction company. The domain of the email mimics a supplier, and the email quotes the project the project manager is currently working on or details the list of items supplied for the project. The actor then brings up an urgent issue with the non-payment of the due amount and threatens to hold back the delivery of the rest of the material until the payment is made.
The detailed and urgent context of the email directly targets the project manager. It makes him act quickly without giving him the time to confirm the invoice or the sender’s legitimacy. The project manager can open an infected invoice file attached to the email or initiate a payment using the link.
2) Complexity of Cueus
Not all phishing emails are created equal. Some are easier to spot, and some require an eye for detail to observe even the smallest anomalies in the email.
When dissecting the anatomy of a phishing email, it’s imperative that every professional—not just the IT security team—understands and reacts to the subtler cues that distinguish a genuine message from a malicious attempt.
In a study conducted by researchers at NIST, they found that people who clicked on phishing emails and those who didn’t perceive cues differently. The ones who did not click sensed suspicion when even the smallest of things were unaligned. For example, an email mentioning an attached PDF, while the actual attachment was Docx.
3) Urgency and consequences
In professional settings, where job performance is closely related to job security, the fear of a situation escalating, an oversight coming to light, or negative feedback can particularly motivate specific actions. Especially when they embody an authoritative tone
Such phishing attacks exploit a basic emotion – fear of consequences.
Imagine receiving an email that mimics your manager, sternly asking you why a critical report hasn’t been submitted to the client. Your details of the oversight are skipped and left to your curiosity. The email then suggests you look at the report you missed in the attached file, or worse, provide them with your login credentials to verify the work you have done so far.
In this scenario, the phisher is not only mimicking an email address – but they are also creating a scenario that creates urgency and anxiety.
4) Diligence
Researchers at NIST realize that malicious tactics could be stopped in their tracks if a person is trained to assess the reality of the situation. Take the previous example: If the receiver is sure that no tasks were skipped or remembers that no such reports were demanded, then they can circumvent the element of urgency and fact-check the information through more secure and private channels like Slack or Microsoft Teams.
So now you understand what makes a Phishing attack more effective. What’s next?
With these learnings, security leaders can return to the drawing board to chalk out better phishing training programs, define more meaningful metrics to track, and understand how their resilience fares against phishing attacks.
For instance, if you were to plot Detection difficulty on the Y-axis and cues on the axis
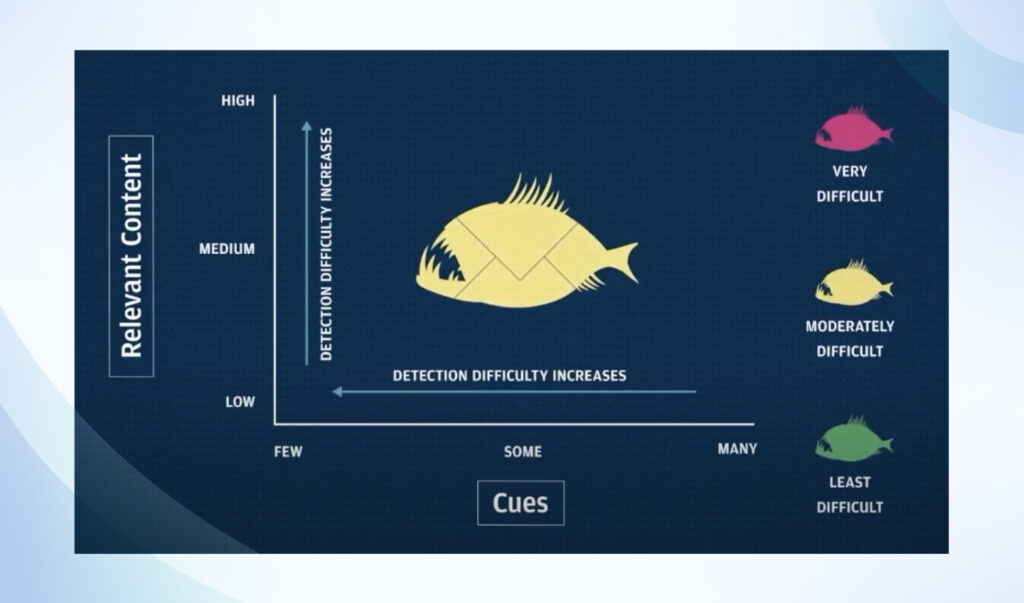
Or you can modify it to include cognitive nudges like urgency, authority, and more, using a table to create a matrix.
| Premis alignment | Detection difficulty | Complexity of cues | Detection difficulty | Cognitive tactic | Action impulse | Final score |
| Mimics a Workplace Process | High | Spelling and grammar errors | Low | Fear of consequence | High | Medium |
| Has Workplace Relevance | Medium | Lack of signer details | High | Loss of money/reputation | High | High |
| Aligns with other situations or events | High | Generic greeting | Medium | Loss of coupon offer | Low | Medium |
Once you have the matrix, you can start creating better phishing simulations by tracking:
1) Click rates vs. Phishing Complexity Score
Measuring click rates against the complexity of phishing attacks helps you gauge exactly where your organization falters. With this understanding, you can tailor your phishing training programs and track their progress, thereby measuring their effectiveness.
For instance, if click rates are high on emails with high premise alignment but low action impulse, you can tailor your training to assess such emails.
2) Repeat clickers
Identifying repeat clickers can help you direct focus on the employees needing additional training, tightening your weakest link in the chain. This targeted approach not only helps reduce the vulnerabilities but also turns the weak links into champions of security once they grasp the full concept of their trigger points and points of failure
3) Identifying security champions
Identifying and empowering security champions within an organization can significantly bolster phishing prevention programs, especially when security teams are stretched thin. These champions act as proxies for the central security team, extending their reach and influence throughout the organization. By leveraging knowledgeable and passionate employees, companies can ensure that security awareness and best practices are continuously promoted at all levels, even in areas where the security team cannot be physically present.
4) Gamify security across the board
These metrics can also be used to gamify good behavior and resilient security practices across the board. Organizations can easily introduce a tiered reward system, track employee progress, and assign badges to employees as they progress toward becoming security champions.
Train teams, and be on top of your security posture with Sprinto
Compliance automation tools like Sprinto significantly enhance an organization’s ability to maintain a robust security posture against threats through features like continuous control monitoring and automated training deployment. By automating the scheduling and delivery of phishing awareness training, Sprinto ensures that employees regularly receive up-to-date training, keeping security awareness high and enabling staff to recognize better and respond to phishing attempts. Moreover, Sprinto’s continuous control monitoring ensures that security measures such as phishing filters, email gateways, and other technical controls consistently function correctly. This persistent oversight helps quickly identify and rectify deviations from expected security settings, preventing potential breaches and keeping the organization’s defenses strong against sophisticated phishing attacks.
Get a real-time view of risk
FAQ
What criteria does the NIST Phishing Scale use to assess phishing email sophistication?
The NIST Phishing Scale evaluates phishing emails based on several key criteria, including the context of the message, the quality of the deception (such as the use of personalized information or reputable company logos), and the apparent legitimacy of the requested action (like clicking a link or downloading an attachment). This scale helps organizations gauge the sophistication level of phishing attempts and tailor their security training accordingly.
How can organizations use the NIST Phishing Scale to improve cybersecurity training programs?
Organizations can use the NIST Phishing Scale to identify specific vulnerabilities within their workforce’s ability to recognize phishing attempts. By mapping training scenarios to various complexity levels on the scale, they can ensure that employees are equipped to handle phishing attacks of differing sophistication, from basic to highly deceptive techniques. This targeted approach allows for more effective training and a stronger defense against phishing.
What role does the NIST Phishing Scale play in compliance and regulatory frameworks?
While the NIST Phishing Scale is not a compliance requirement, it aligns with broader NIST guidelines and frameworks that advocate for comprehensive cybersecurity measures. Organizations can leverage this scale to demonstrate a proactive approach to phishing defense, potentially aiding compliance with regulations that require evidence of practical cybersecurity training and phishing awareness among employees.
Can the NIST Phishing Scale be integrated into existing security tools and platforms?
Yes, the NIST Phishing Scale can be integrated into various security awareness platforms and simulation tools to enhance the realism and relevance of phishing tests. By embedding this scale into routine security assessments, organizations can continuously evaluate and adapt their phishing defense strategies, ensuring they remain effective against evolving phishing tactics and techniques. This integration helps maintain an up-to-date security posture and reinforces ongoing employee training efforts.
Virgil
Virgil is a marketer at Sprinto who combines his media savvy with his cybersecurity expertise to craft content that truly resonates. Known for simplifying complex cybersecurity and GRC topics, he brings technical depth and a storyteller’s touch to his work. When he’s not busy writing, he’s likely exploring the latest in cybersecurity trends, debating geopolitics, or unwinding with a good cup of coffee.
Explore more
research & insights curated to help you earn a seat at the table.


















